
Hey Folks, In the tutorial we are going to talk about an OSINT tool that will help us gather information on phone numbers. Sometimes we get some fake numbers or calls asking about our account details or personal details even most people give details of them, as a result of which they have to compromise their account. After that we start that browse and no one site can be found that can give details about fake calls. Hence in this tutorial we will learn how we can information gathering through the “PhoneInfoga” tool and get the exact details against the target.
Lets do it 🙂 !!
Installation
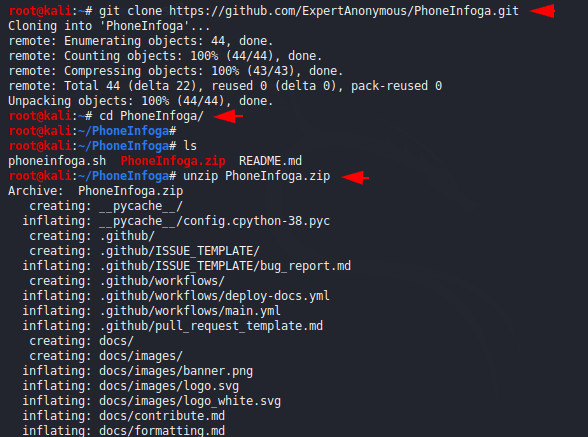
Installation is quite simple, but we will make it quite difficult due to the docker installation 🙂 because it is not possible that you already have a docker. But first we will download it from the github page and after the installation we will got zip file that we have to unzip by using the following command.
1 2 3 4 | wget https://github.com/sundowndev/PhoneInfoga/archive/v2.0.10.zip unzip v2.0.10.zip cd PhoneInfoga-2.0.10/ |
Docker
Docker is a set of platform and as a service products which use OS-level virtualization to deliver software in packages.
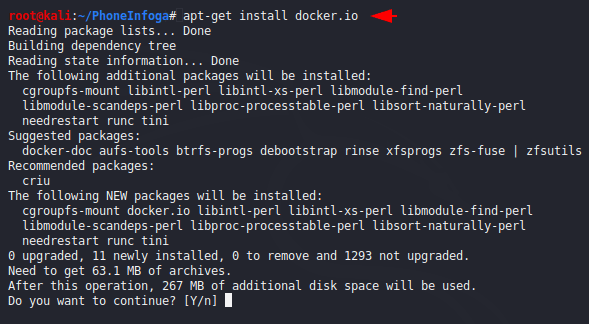
We will download the docker service on the terminal by using the following command.
1 | ap-get install docker.io |
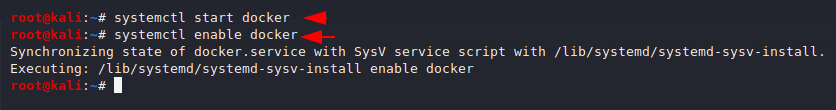
Enable and start the docker service by using the following command.
1 2 | systemctl start docker systemctl enable docker |
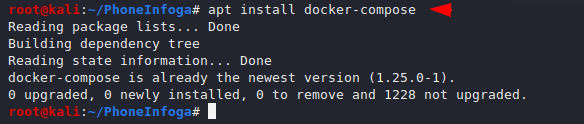
Compose has to be downloaded as it will configure the application with the help of “.YML” file.
1 | apt install docker-compose |
Now just we will execute the following command and it will automatically complete all the process like compiling, creation and hosting of application on Apache server
1 | docker-compose up -d |
Complete 🙂 Here you can see that the application is successfully hosted with bind address. Now we will browse the following location.
1 2 | docker ps localhost:80 |
Test time !! Here we have to give the number we want to find out. It is not mandatory to provide the number with the country code, just you can enter the number. As soon as we enter the number on it we got lot of information about the target such as : social media profiles, country code location etc. with the help of google dork.
Note : We are sorry but we cannot show everything, showing someone’s number can be against the security conditions.
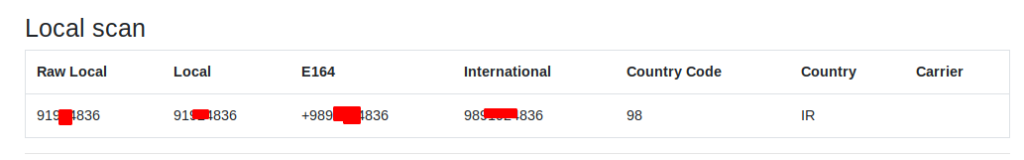
Local Scan
In this result we get important details, but we think it may not be that much usage data. Let’s move on
Google Search – Dork
As we know how important Google dork is if we are Footprinting, so it also uses this technique to get more information about the target. Lets open the links.
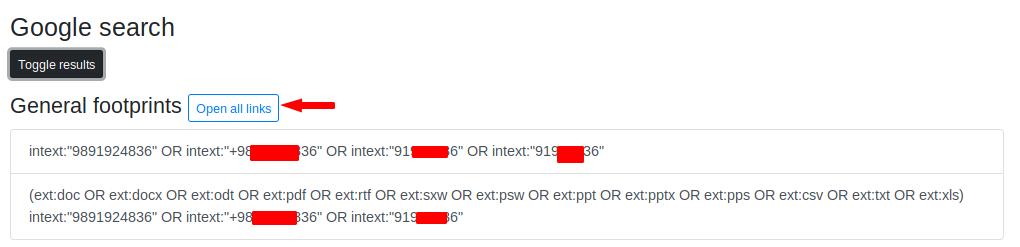
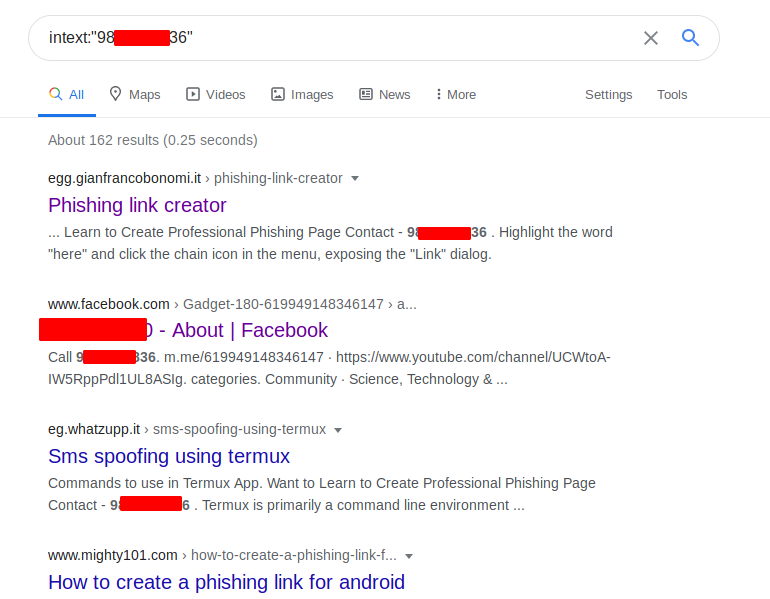
Nice 🙂 As we can see that if the target number would be associated with a social media handler or website, it would definitely indicate the results.
Social Network Footprinting
The best part of this tool comes from here because now it will give all the results separately. Here you can get profile information if the target is available on social media then it will catch it.
Individual Footprinting
Now it will separately execute the dork on Google and give us the result.
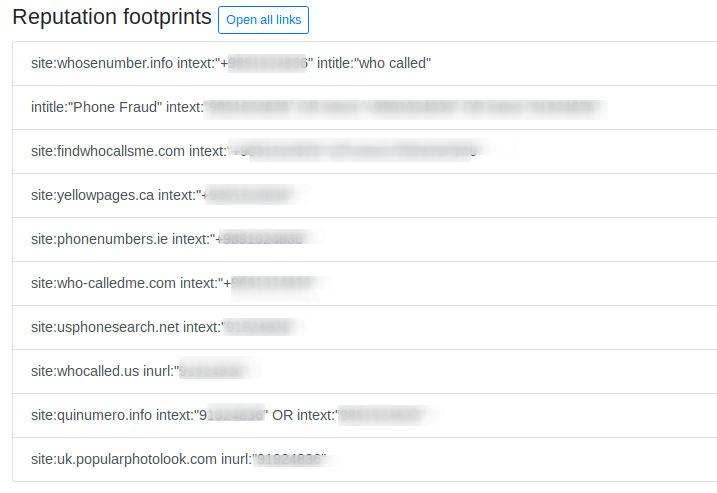
Repuatation Footprinting
It will get the details about the target through the reputed website where footprinting can be done manually.
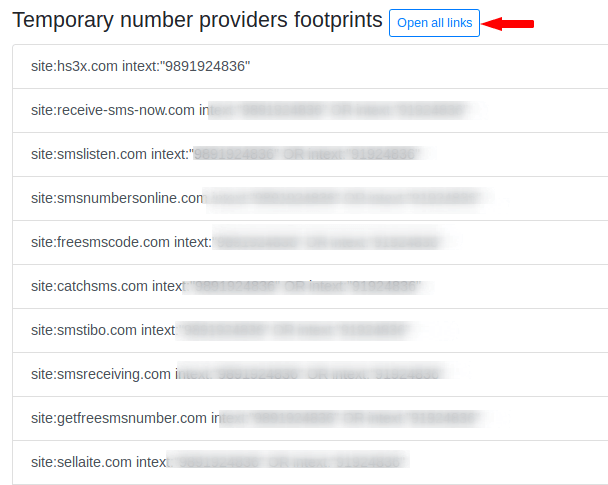
Temporary number providers
Most of the time attackers take temporary numbers to deceived the people so it also gets details from the following services.





I like the valuable information you provide on your articles.
I will bookmark your weblog and test again here regularly.
I am relatively certain I’ll be informed many new stuff
proper right here! Good luck for the next!
Thanks for your valuable comment 🙂 !!
Best view i have ever seen !