
Hey Folks, in this tutorial, we have brought a system protection tool for you, which is called “ThreatMapper“. The Deepfence Runtime Threat Mapper is a subset of the Deepfence cloud native workload protection platform, released as a community edition. You can read about this tool completely from here.
Let’s take a look 😛 !!
Install Docker
To install this tool in any server or system, we must first install the docker. Installing Docker anywhere is not a difficult task as you can easily install it using the following command.
1 | apt install docker.io docker-compose |

Installation of Threat Mapper
Like every time, this time also we have to download the community edition of this tool from github using the git clone command. Once downloaded, we go to the directory of tool named “file” and execute the docker command to run the multi-container docker applications at the same time.
1 2 3 4 | git clone https://github.com/deepfence/ThreatMapper.git cd ThreatMapper/ cd files/ docker-compose -f docker-compose.yml up -d |

Hmm 😛 !! Suppose if the command executes, but the application does not start then in that case you can check all the activated application by using the “ps” command.
1 | docker ps |

Alright 😛 !! Now we forcefully open our local address with “https” on the browser. We do not already have an account, so we have to register ourselves first.
1 | https://localhost |

Now we have to enter some necessary details to create a new account.

Topologies
Good 😛 !! Once the account is created, we redirect to the management console of this tool. The interface of this tool is beautiful and easy that anyone can control easily. In the topology section of this tool, we find all the devices connected to this network.

OK 😛 !! You can choose any host according to you but in our case we will select our machine and start a vulnerability scan on it. It will take a long time to detect all types of vulnerabilities in the host machine.

Vulnerabilities Detect
After the scanning is complete, you can find all the details by going to the vulnerability section of this tool. As you can see in the image below it describes all vulnerabilities according to the risk situation.

We just go down a bit and get more clarity on the results.

As you can see all the vulnerabilities have been described with CVE which can give developers the benefit of fixing these errors.

Nice 😛 !! We can get deep knowledge of any vulnerability by clicking on it.
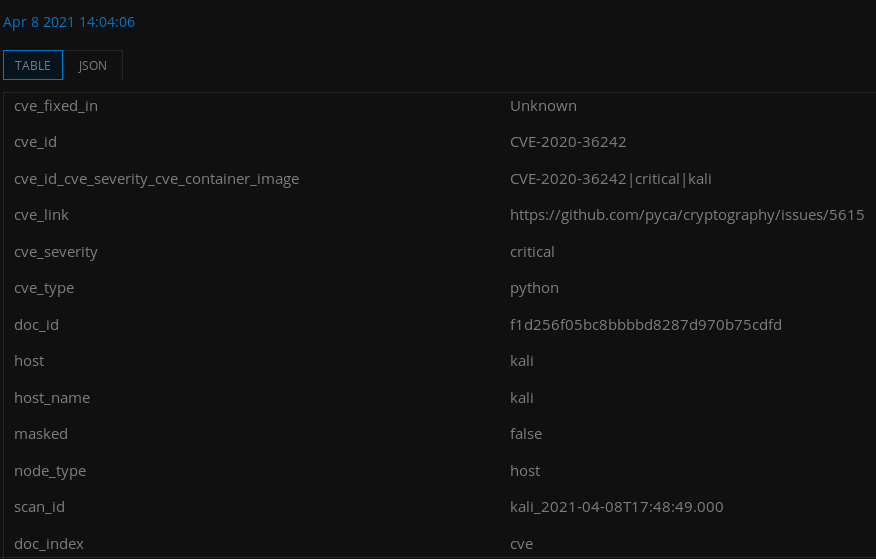
Opps 😛 !! We have highlighted some features that we could not access due to not have premium version but you can buy it according to yourself and easily audit any system.





