
Hey Folks, Most of the time we find offensive tools on github separately that take much time, hence we come back with an interesting tool called “PowerSharpPack” which has Offensive CSharp Projects that can help for the red teaming or offensive security purposes. As we know the most recent innovative security projects or tools are written in C# language and it compiles all projects into one tool such as :
- Seatbelt
- SharpUp
- winPEAS
- Lockless
- SharpChromium
All projects work separately and this tool is designed for PowerShell because all the project are wrapped into powershell because of easy usage.
Lets take a look 🙂 !!
Installation
This project is open source that available on the github page. We do not need to download or configure the collection of projects differently, just we will using the below command which will download the “.ps1” extension file from the github page and configured it automatically.
|
1 |
iex(new-object net.webclient).downloadstring('https://raw.githubusercontent.com/S3cur3Th1sSh1t/PowerSharpPack/master/PowerSharpPack.ps1') |
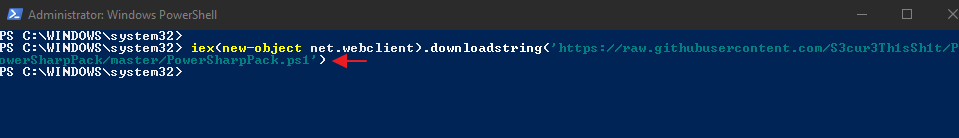
After successfully executing the above command we can use this tool by entering the name on the terminal.
|
1 |
PowerSharpPack |
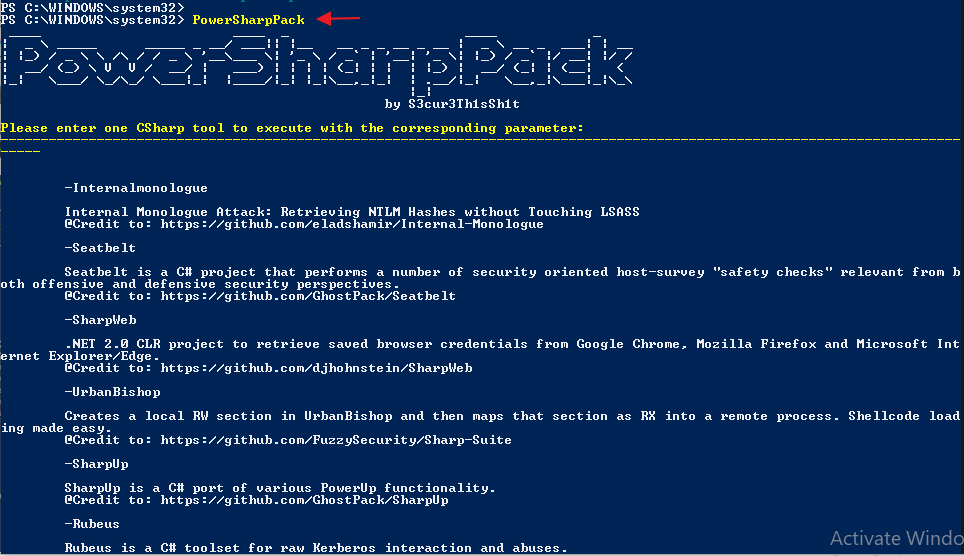
As we have already mentioned that this tool contains a collection of projects that we cannot perform separately, so in this tutorial we will show you some examples, after which you will connect with this tool and do itself. In addition, we have mentioned all the projects through the image that are in it.
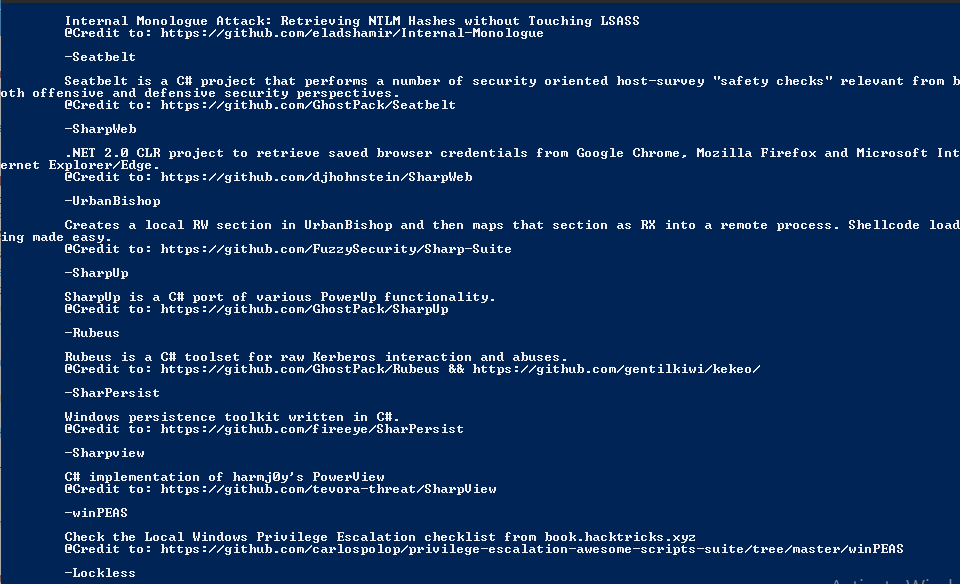
Read More …
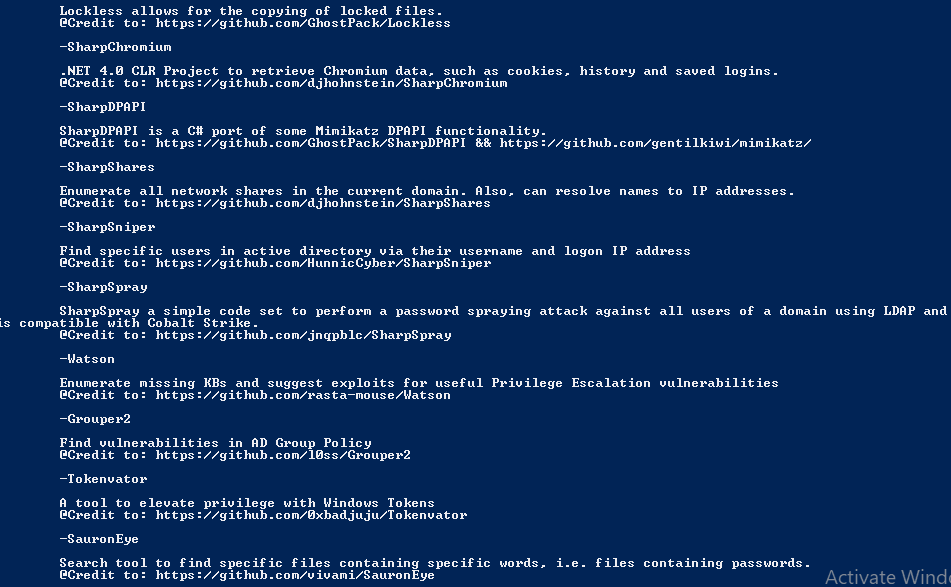
We can investigate the use and function of these all tools by going separately.
Usage
We have mentioned the full usage guide of this tool through an image to which we can add our module and execute its command.
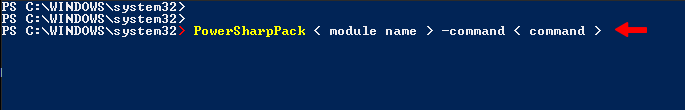
SauronEye
It is a search tool designed for Red Teamers to find hidden directories, drives, files with specific keywords. There are many such tools available, but they take longer to scan disk files and give us details. But we don’t need to configure it, just we have to execute the below command. As you can see the result it gives us all the directories and files because we did not add any filter.
|
1 |
PowerSharpPack -SauronEye |
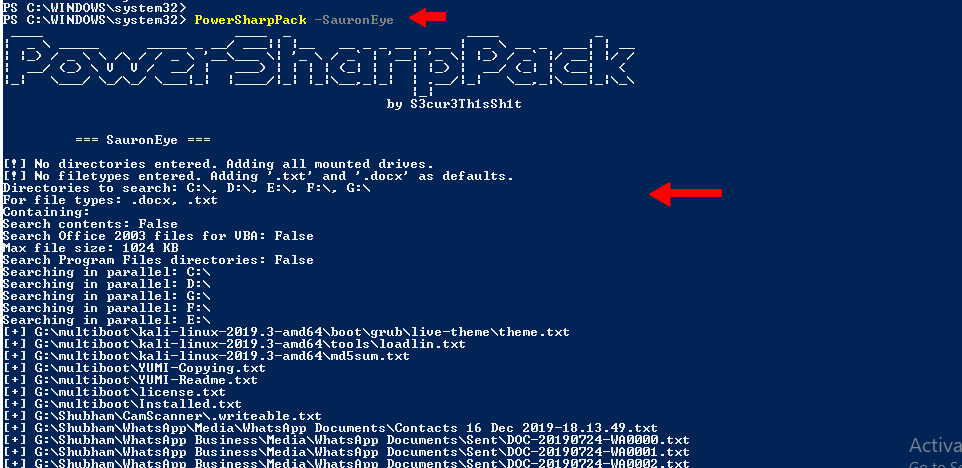
SharpView
This module can be helpful to identify the available method by which we can get information about the domain and also related to it. But we do not need to do this, just we will execute the below command and it will display all the methods and from which we can further processing.
|
1 |
PowerSharpPack -Sharpview |
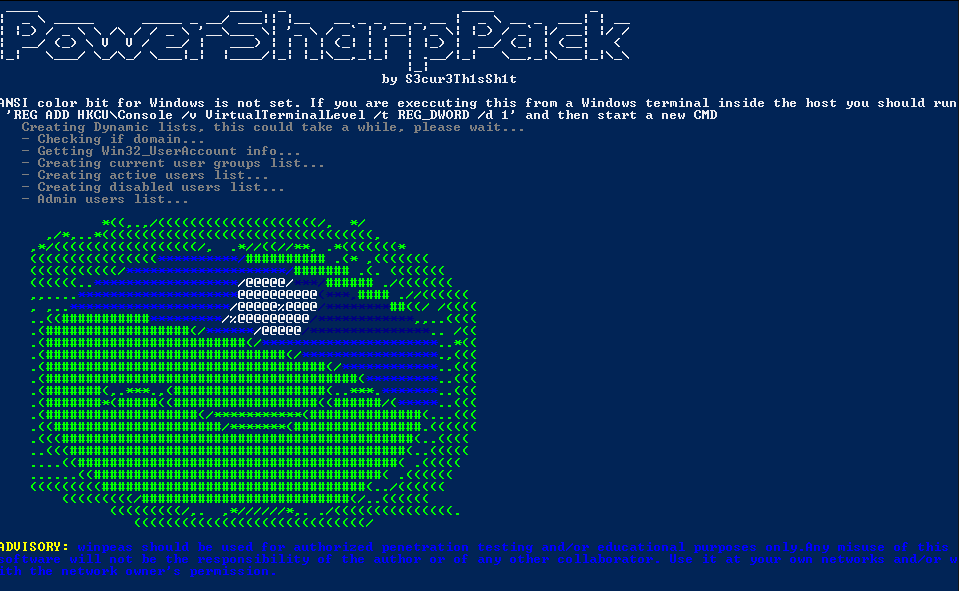
WinPEAS
This project is specifically designed to explore a possible privilege escalation path in a Windows environment. It will take few seconds to execute almost all the checks and some seconds/minutes during the lasts checks searching for known filenames that could contain passwords. We will execute the following command.
|
1 |
PowerSharpPack -winPEAS |
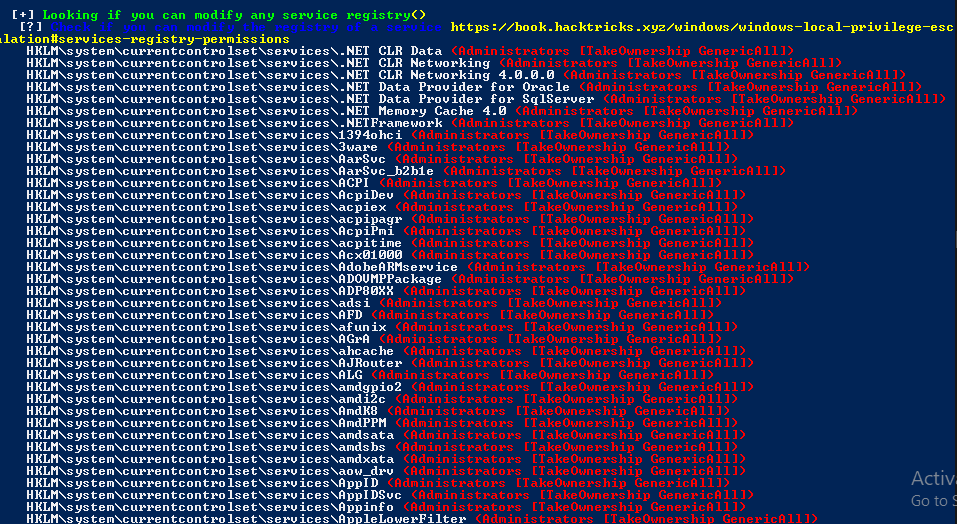
Registry
Here you can see that it is trying to lookup the registry services in which we can easily modify.
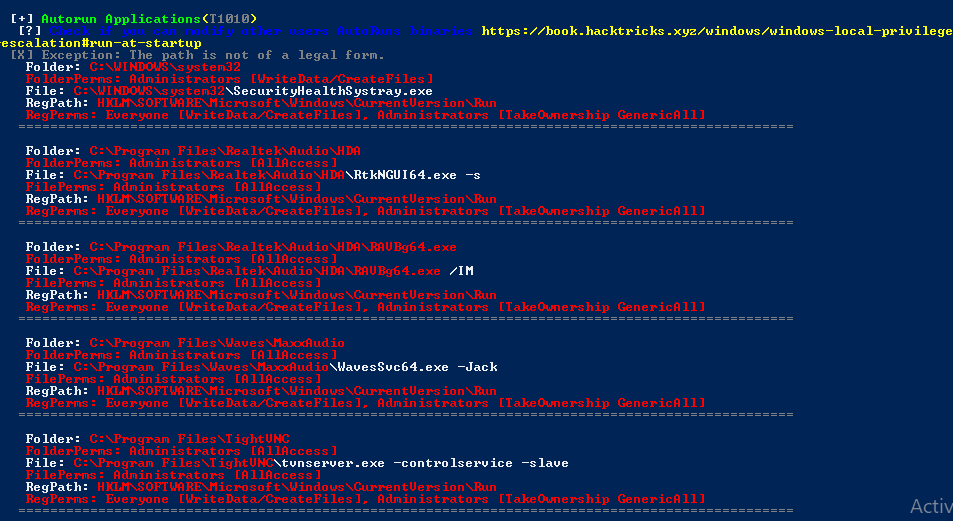
Autorun Binaries
A window operating system contains autorum.exe that is designed to automatically run a program from a CD-ROM, as you can see below it tries to find autorun binaries from which we can create a persistence service.
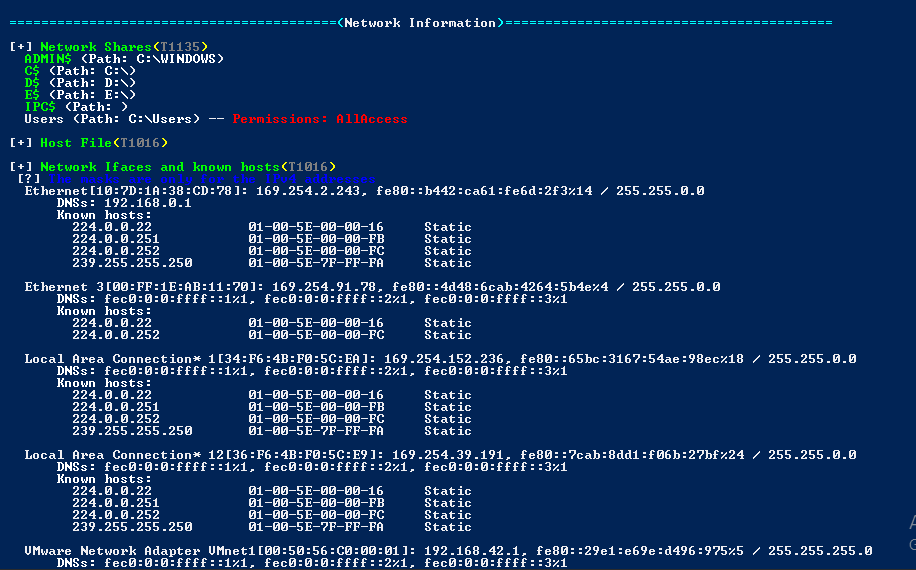
Network Information
Here we can get some useful information like drive access and network configuration and based on which we can take our next step.
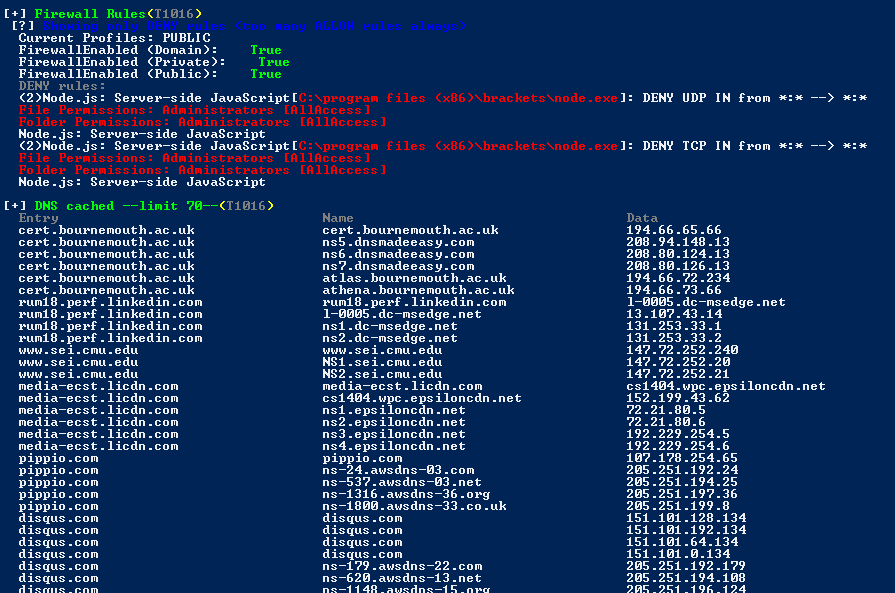
Firewall and DNS
Of all the information, this can be useful information for us. If we know about firewall rules then we can easily break the security of the system.
Listening Ports
Here you can see that all the listening address and service which is restricted from outside.
This is not enough because it gives us a lot of information and we cannot show you everything but we hope you have got an idea of how important and useful this tool is.

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.





When someone writes an article he/she maintains the idea of a
user in his/her mind that how a user can be aware of it.
Thus that’s why this article is great. Thanks!