Hey Folks, In this tutorial we will learn how we can configure the vulnerable web application on docker. As we know that docker gives us the ability to run multiple containers simultaneously on a given host and even we can run containers within host machines that are actually virtual machines. So with the help of this great technology we will install our vulnerable web application for testing purposes.
What shall we do ?
Docker
- WebGoat & WebWolf
- Juice-Shop
- bWAAP
- DVWA
- Mutillidae
- Sqli-Labs
- XVWA
Lets do it 🙂 !!
Docker
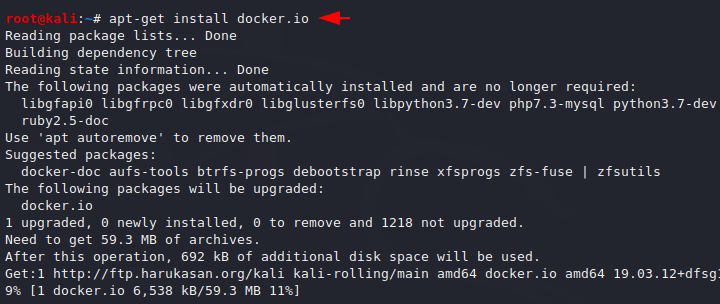
First we have to download the docker on our terminal which are quite simple just we need to execute the below command and it will be automatically downloaded.
|
1 |
apt-get install docker.io |
We need to execute the following command to start the docker service.
|
1 2 |
systemctl enable docker systemctl start docker |
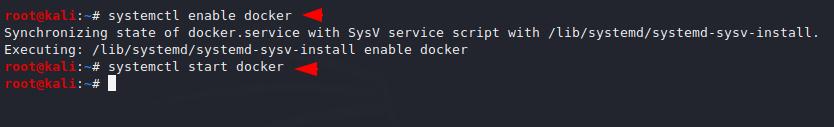
Now the docker is successfully configured on the web server and now we can host our web applicaitons.
WebGoat & WebWolf
WebGoat and WebWolf both are insecure application that allows interested developers just like you to test vulnerabilities commonly found in Java-based applications that use common and popular open source components.
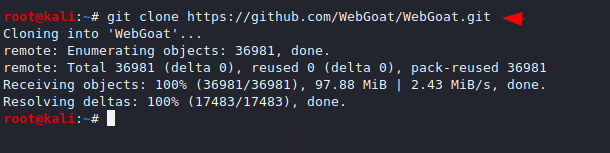
We need to download it from the github page in which we will get the docker configuration file and we will be able to host it on the docker.
|
1 |
git clone https://github.com/WebGoat/WebGoat.git |
The downloaded directory contains the configuration file to which we will go. Now we only need to execute the last command which will automatically host this vulnerable web application on the web server.
Usage 🙂 docker run -p < Any Port >:8080 -p < Any Port >:9090 -e Image
|
1 2 |
cd WebGoat/ docker run -p 8080:8080 -p 9090:9090 -e TZ=Europe/Amsterdam webgoat/goatandwolf |
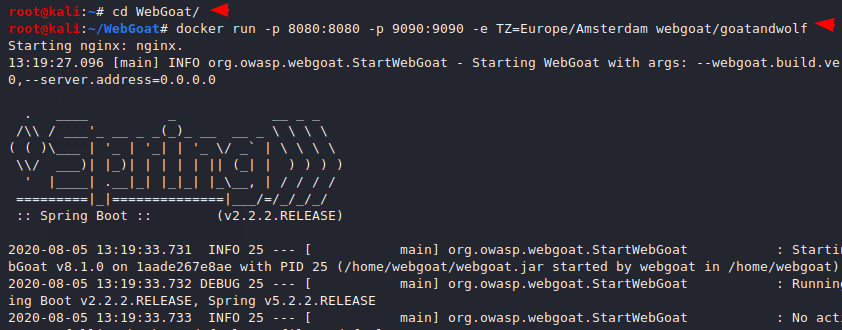
Next step to browse the following location and click on “register new user” option.
|
1 |
http://127.0.0.1:8080/WebGoat |
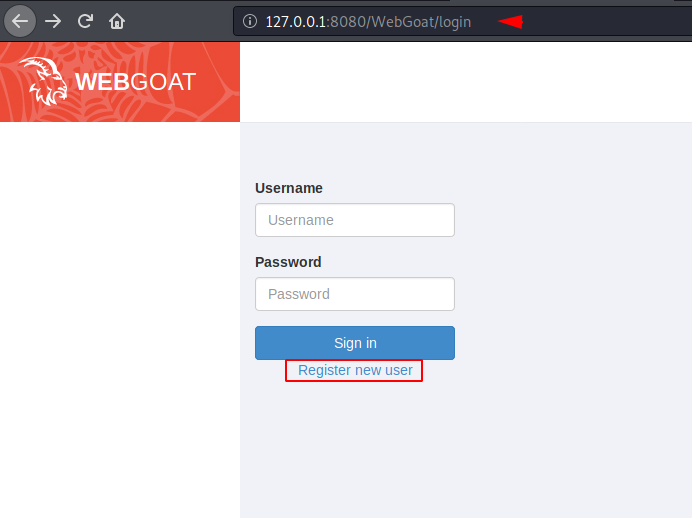
We can set user and password as required.
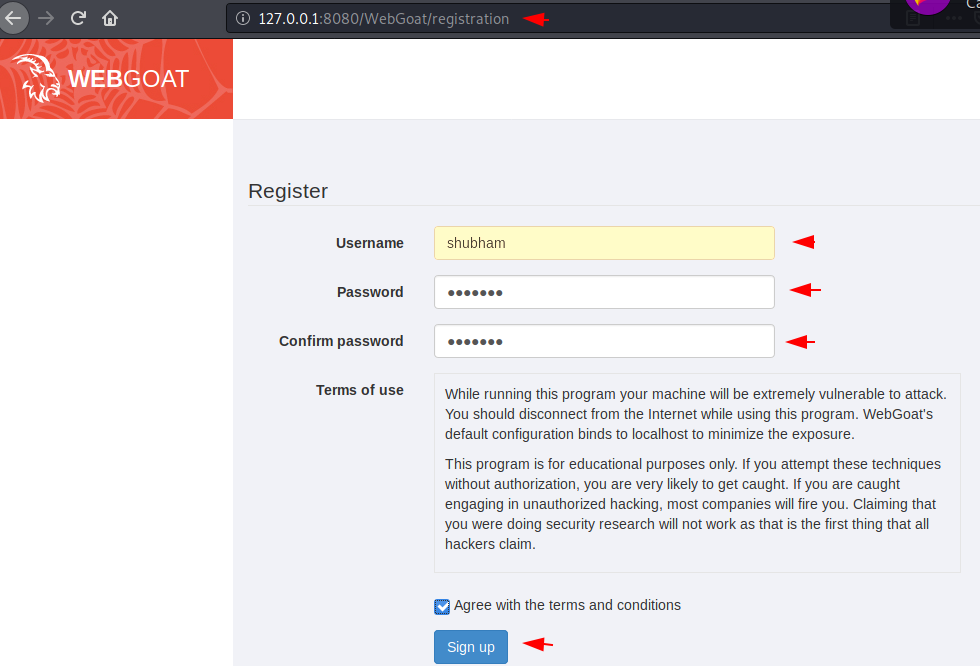
Thats it 🙂 here you can see that our first vulnerable web application is successfully hosted on the docker.
After Browse the following location you will get your WebWolf vulnerable web application.
|
1 |
http://127.0.0.1:9090/WebWolf |
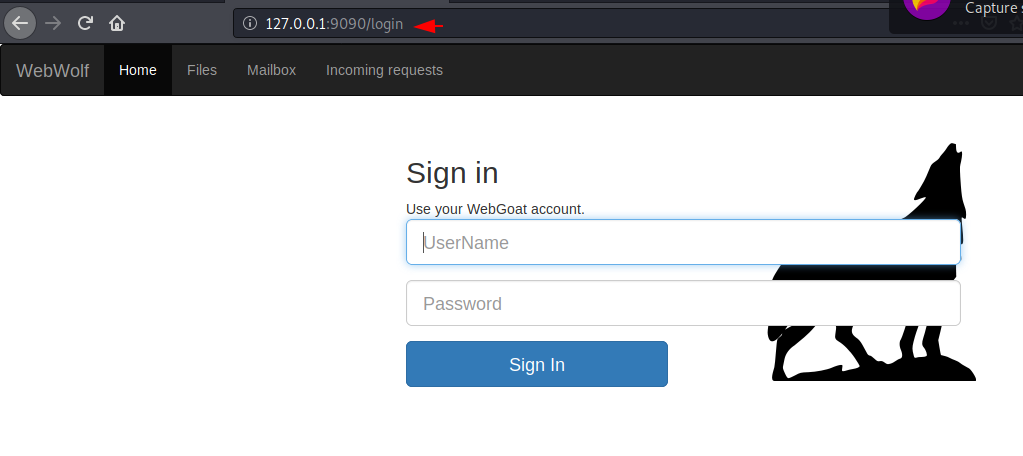
Without much effort, we have successfully hosted our first vulnerable web application on Docker.
Juice-Shop
Juice Shop is written in Node.js, Express and Angular. It was the first application written entirely in JavaScript listed in the OWASP XVWA Directory. The application contains a vast number of hacking challenges of varying difficulty where the user is supposed to exploit the underlying vulnerabilities.
Source : OWASP
For this project we do not need to put a lot of effort as the docker provides this service to download the terminal to the project. Now we will execute the “pull” command which will automatically download the docker’s image.
|
1 |
docker pull bkimminich/juice-shop |
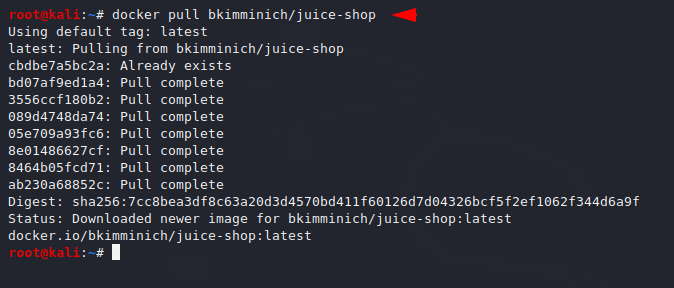
After executing the above command we will host it on the docker using the following command.
|
1 |
docker run --rm -p 3000:3000 bkimminich/juice-shop |
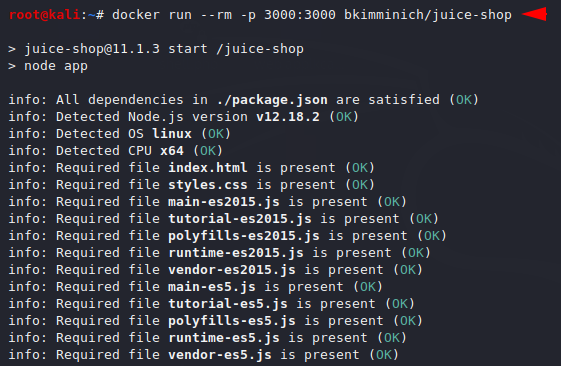
This will take some time and after doing this you can use the following URL to see your juicy web application.
|
1 |
http://localhost:3000 |
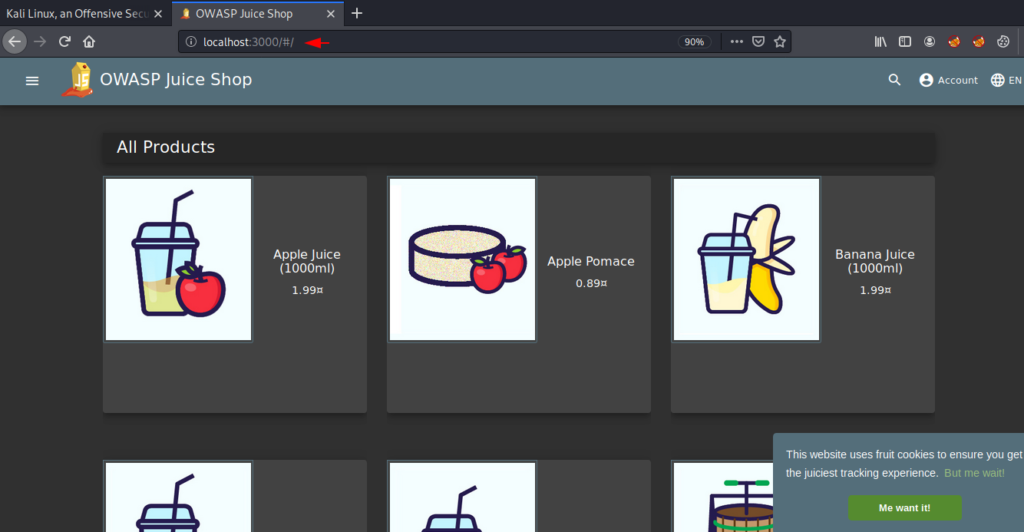
bWAAP
bWAPP is a vulnerable web application which is a free and open source. bWAPP is a PHP application that uses a MySQL database. It can be hosted on Linux/Windows with Apache/IIS and MySQL. prepares one to conduct successful penetration testing and ethical hacking projects.
We have to download the following image by using the pull command.
|
1 |
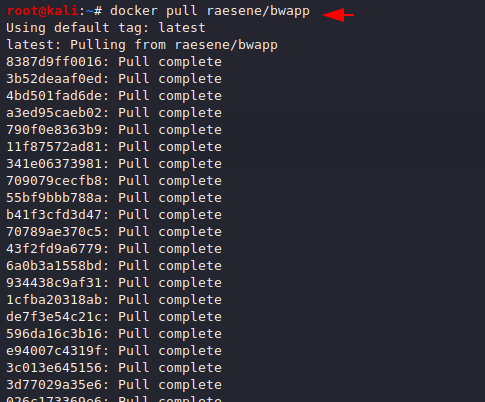
docker pull raesene/bwapp |
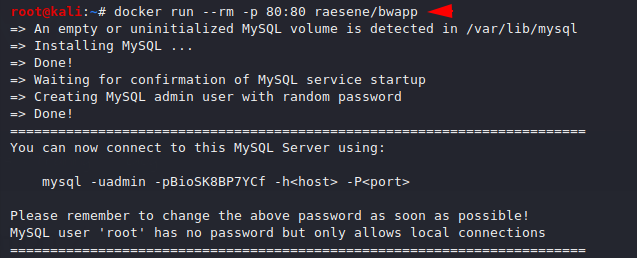
Just host the web application on port 80 by using the following command.
|
1 |
docker run --rm -p 80:80 raesene/bwapp |
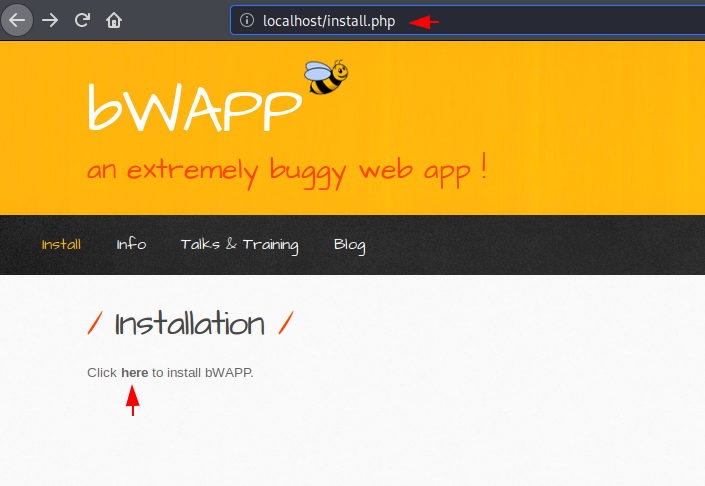
Now we will open the given link in which we have to click on highlighted hyperlink that will establish mysql database.
|
1 |
http://localhost/install.php |
After doing all this we can login into the web application by using the bee and bug credentials.

Here you can see that we have successfully hosted it and now we can start out penetration testing.

DVWA
DVWA is an vulnerable web application which coded in PHP/MYSQL. Seriously it is too vulnerable. With the help of this application ethical hackers can test their skills and run this tools in a legal environment. The aim of DVWA is to practice most common web vulnerability, which contains different types of level.
Now we will execute the following command and it will download the DVWA image from the docker hub.
|
1 |
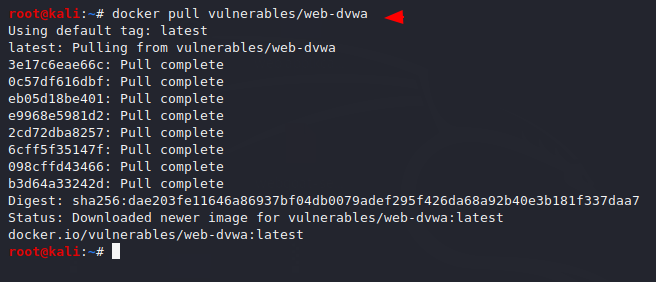
docker pull vulnerables/web-dvwa |
Keep in mind it may be give you error of bind address hence you can use the different port number in your case. But anyway just execute the following command.
|
1 |
docker run --rm -p 80:80 vulnerables/web-dvwa |
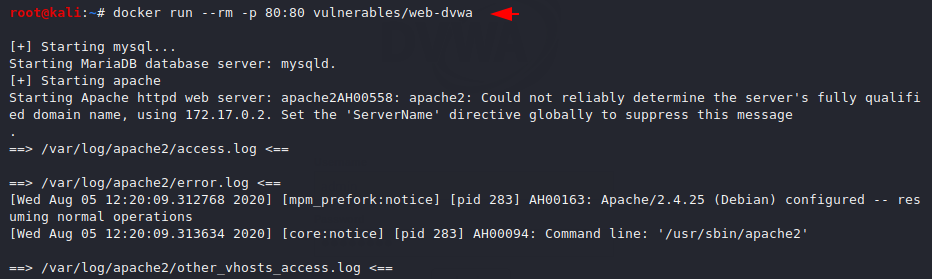
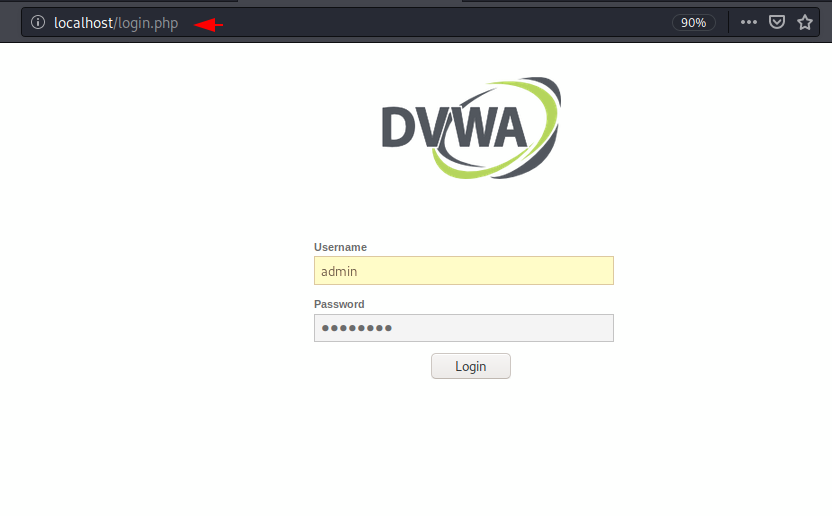
Browse the following location and you will find the login page where you have to enter admin and password in the input field to login to the web application.
|
1 |
http://localhost/setup.php |
Click on reset database and after that it will give us location of login in which we have to click.
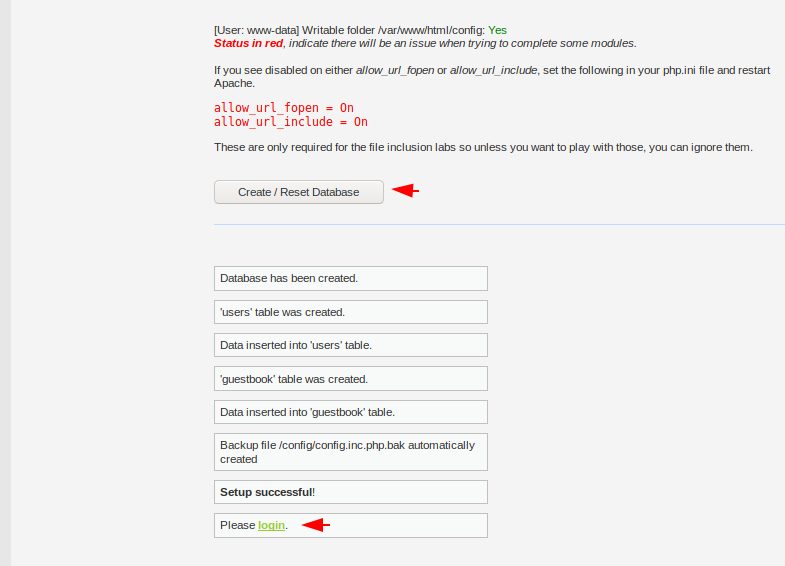
Thats it 🙂 Again we have successfully configured our web application.
Mutillidae
Mutillidae is a another pen source web application provided to perform pen-test and hack a web application. Mutillidae can be installed on Linux, Windows XP, and Windows 7 using XAMMP making It easy to install, only we need to configure the linux, apache, mysql and php on web server.
|
1 |
docker pull citizenstig/nowasp |
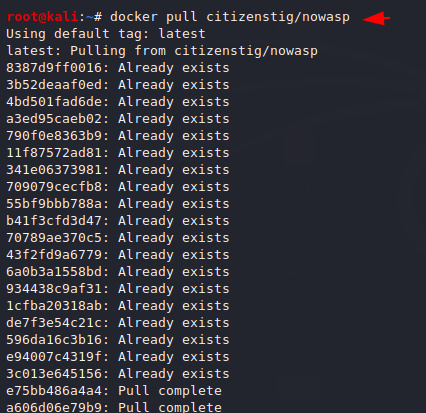
Execute the following command pull command which will automatically download Docker images from a registry.
|
1 |
docker run -d -p 82:80 citizenstig/nowasp |
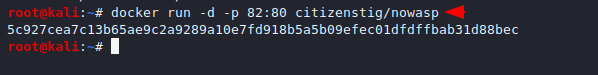
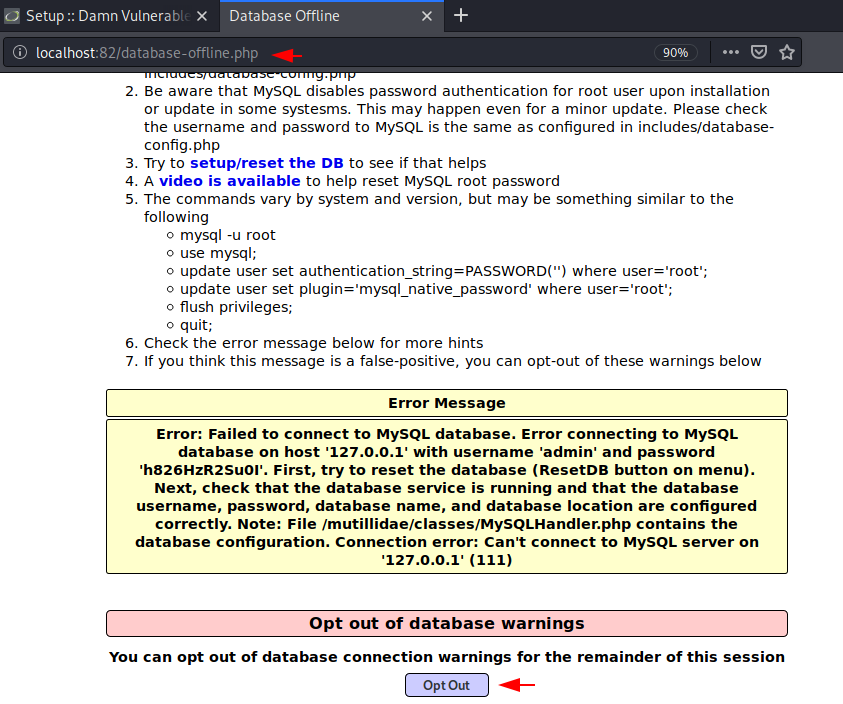
We need to open the following location on our browser where the web application is hosted. Then we will click on the “opt-out” option which will appear at the end of the page.
|
1 |
http://localhost:82 |
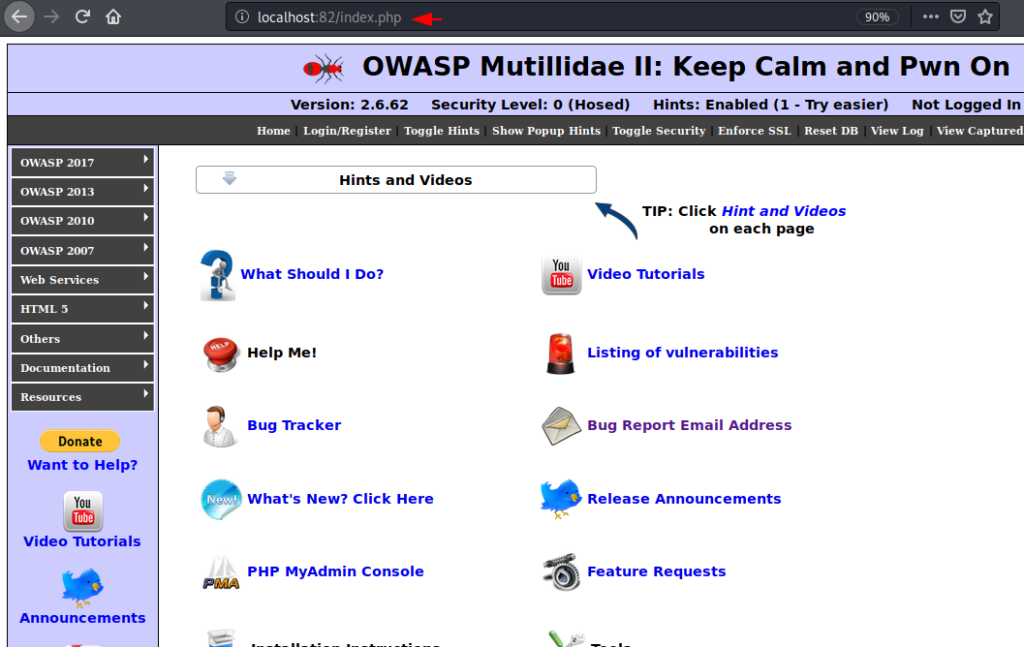
Congratulations 🎊 ! our vulnerable web application is successfully configured on the docker.
SQli-Labs
SQLI-LABS is a platform to learn SQLI Following labs are covered for GET and POST scenarios. It is an open source that is hosted on github page and especially designed to learn sql injection.
Like every time, this time also we will execute the pull command to download this project from the docker hub.
|
1 |
docker pull acgpiano/sqli-labs:latest |
Now we will run the following command that will help us to host our web application without much effort.
|
1 |
docker run -d -p 83:80 acgpiano/sqli-labs:latest |
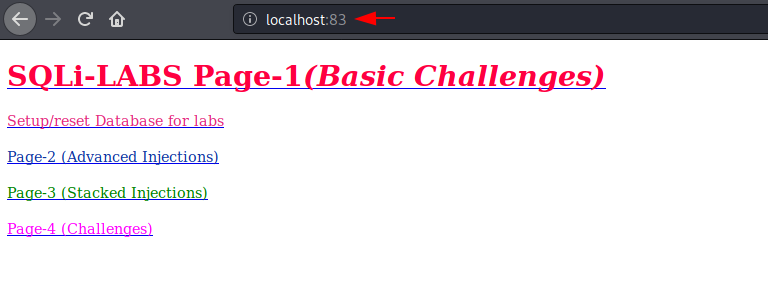
Again open the given URL on browser and now we donot need to do more thing.
|
1 |
http://localhost:83 |
XVWA
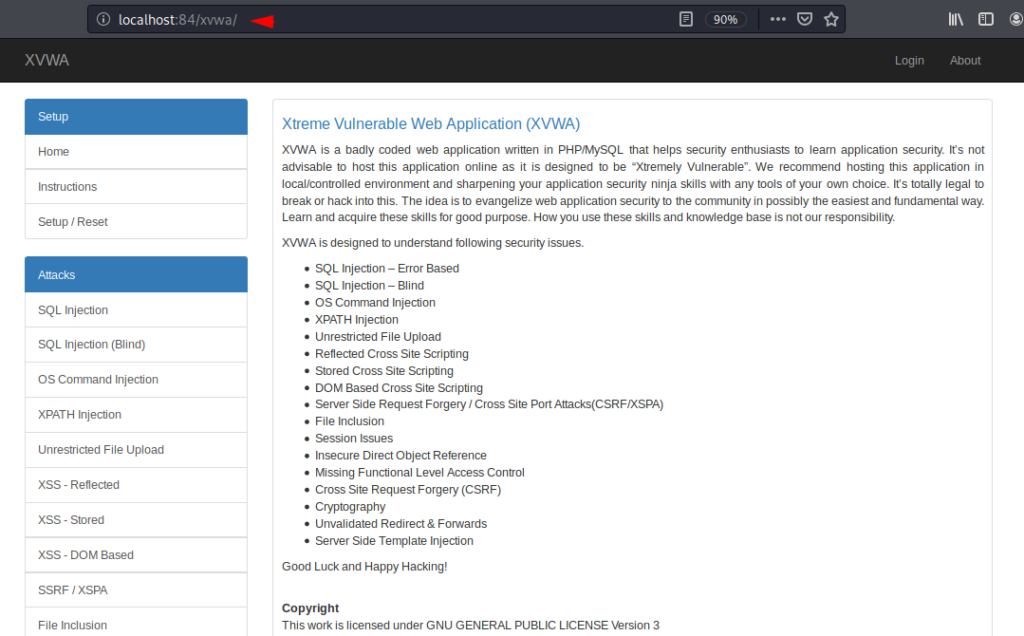
XVWA is an another vulnerable web application written in PHP/MySQL that helps security enthusiasts to learn application security. XVWA is designed to understand following security issues and with the help of this vulnerable application we can enhance our penetration testing skills.
We will first download it as Github page and then we need to go inside the directory of the tool where we will get the docker file. After receiving it, I think you already know what our next step is 🙂 ! just execute the following command.
|
1 2 3 |
git clone https://github.com/tuxotron/xvwa_lamp_container.git cd xvwa_lamp_container/ sudo docker run --name xvwa -d -p 84:80 tuxotron/xvwa |
This configuration is quite easy from all web applications as we do not need to do much, just browse the following location and start testing.
|
1 |
http://localhost:84/xvwa/ |
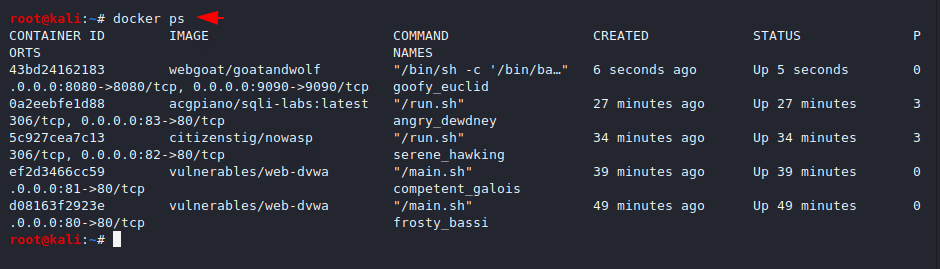
After configured all the vulnerable web application we can see all the location of the web application by using the “ps” command.
|
1 |
docker ps |
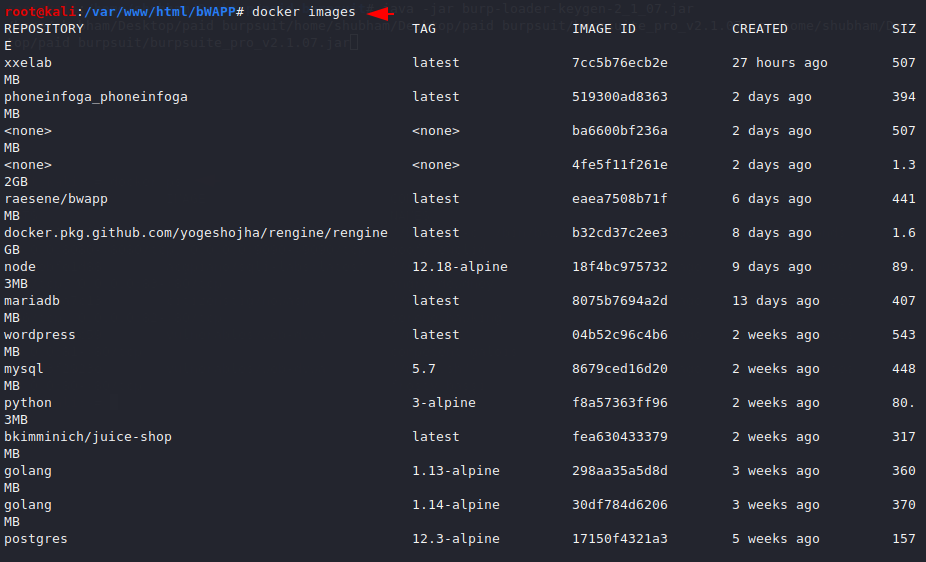
Done 🙂 If we want to check how many images we have on our docker then we can use the following command.
|
1 |
docker images |

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.




