Hey Folks, in this tutorial we are going to talk about an interesting tool called “GHunt“. GHunt is an OSINT tool to extract information from any Google Account using an email address. It can extract the following details using a specific email address.
Possible Extract Details
- Owner’s name
- Last time the profile was edited
- Google ID
- Activated Google services (YouTube, Photos, Maps, News360, Hangouts, etc.)
- Installed softwares (P)
- Google Maps reviews (M)
- Possible physical location (M)
- Events from Google Calendar (C)
- Possible YouTube channel
- Possible other usernames
- Public photos (P)
- Phones firmwares (P)
Let’s take a look 🙂 !!
Install Dependencies
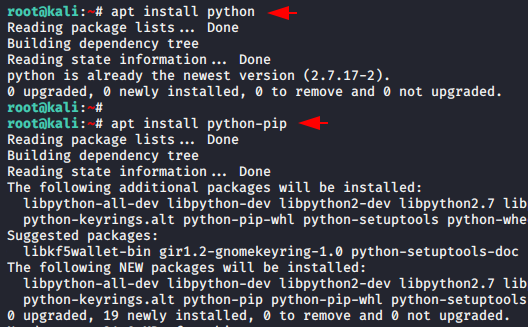
It is necessary to install all dependencies in order to use each tool and any type of tool, especially in your system it must have pre-installed.
1 2 | apt install python apt install python-pip |
Tool Installation
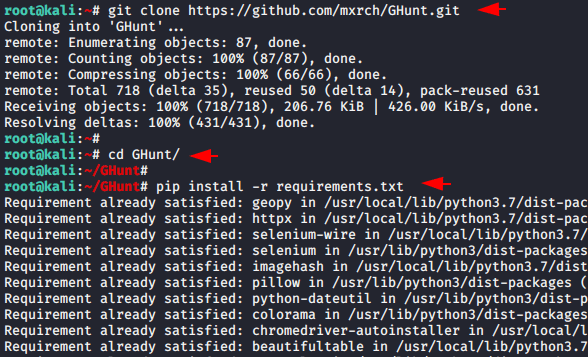
Now the time has come to configure this tool on the system for which we will first download it from github, go to the directory of this tool and install the remaining dependencies using the pipe command.
1 2 3 | git clone https://github.com/mxrch/GHunt.git cd GHunt pip install -r requirements.txt |
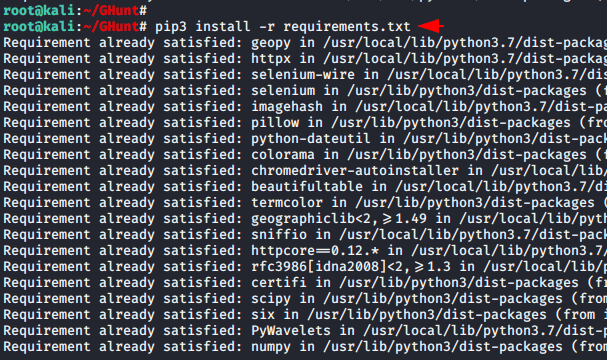
Once again we will execute the given command to establish the remaining dependencies.
1 | pip3 install -r requirements.txt |
Check Cookie Validation
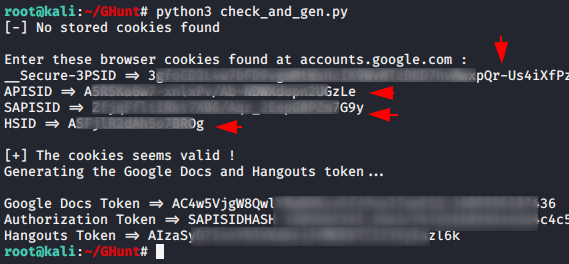
Now we will check the validity of your cookies by using the following command. Let’s follow the steps.
1 | python3 check_and_gen.py |
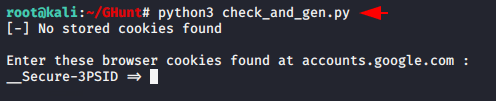
Just login to any gmail account but we would suggest you to create a new account for this or use an account where you never login.
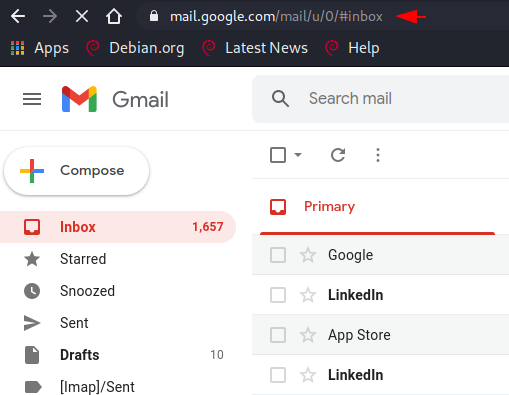
After login to any gmail account we will use the developer console using Inspect feature of browsers. To do this we will right click on the gmail web page and select inspect option.
After that we will go to the applications tab in which we will open the cookie section and click on google account.
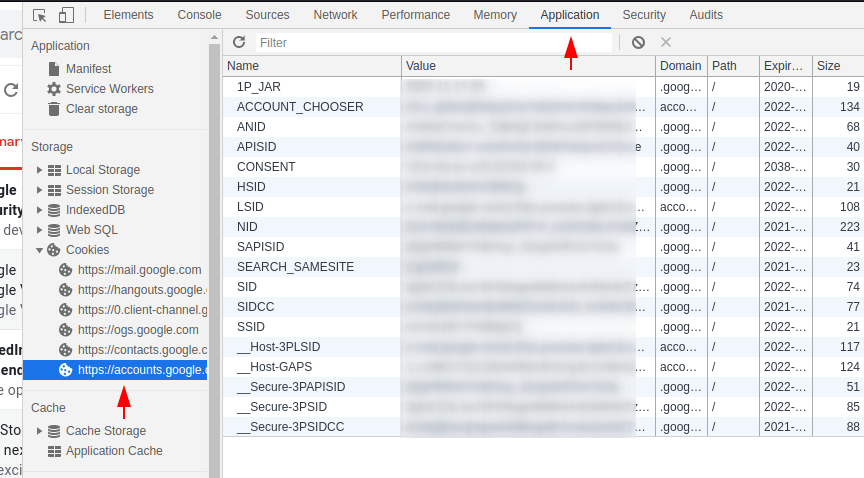
Now to authentication the google account with ghunt tool, we will entered the values of the highlighted names on the terminal one by one.
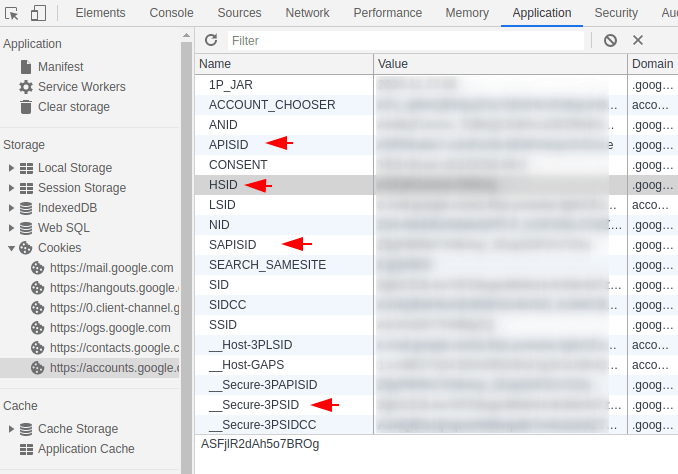
After entering all the requirements it shows that “cookies seem to be valid” which means that the google account has been successfully connected to this tool.
Start Hunting
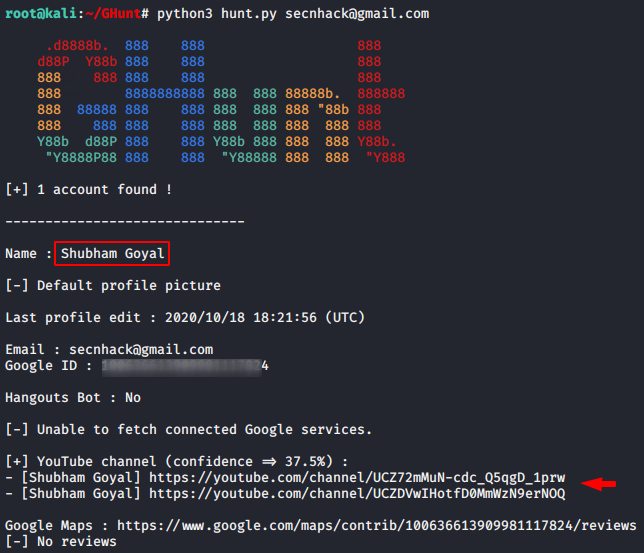
Configuration was quite difficult but using this tool is quite simple. Just you need to enter the target gmail address you want to track and then it will dump all the sensitive information it will be able to find. As you can see what kind of results come after giving the gmail address of the target.
1 | python3 hunt.py < email address > |
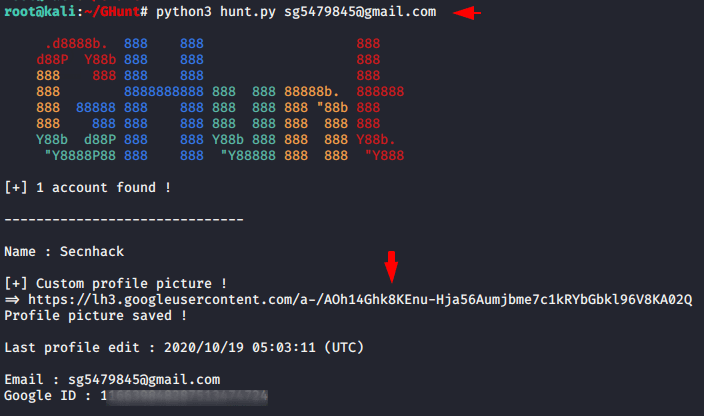
Great 🙂 !! As you can see we have got the user profile of the following gmail address.

Also, if any other user writes any review on the target google Map profile then it will appear here.
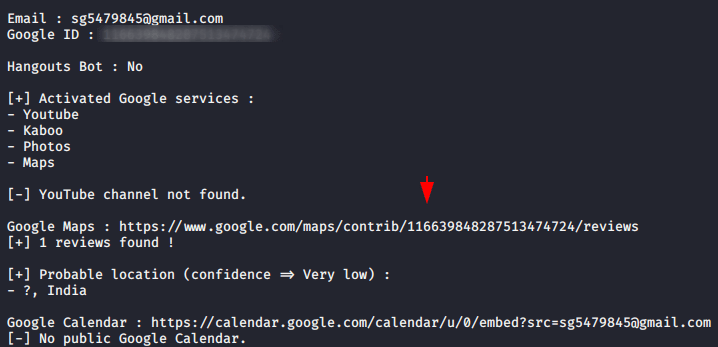
Hm 🙂 !! We are able to see the location of the reviewers on the target profile.
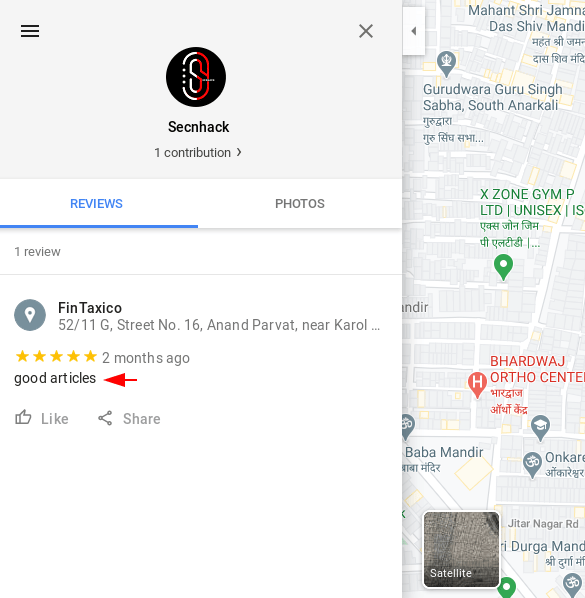
Last one 🙂 !! Similarly, you can use this tool and get a lot of useful information about the target using its gmail address.