
Hey Folks, in this tutorial we will introduce an multi-tool web application scanner called “RapidScan”. The ultimate goal of this program is to solve this problem through automation; viz. running multiple scanning tools to discover vulnerabilities, effectively judge false-positives, collectively correlate results and saves precious time; all these under one roof. Now you can read some of the key features of this tool from below.
Key Features
- Only one-step installation
- Checks vulnerabilities with multiple tools
- Association with OWASP Top 10
- Classification of vulnerabilities.
- Remediations
Let’s take a look 😛 !!
RapidScan Tool Installation
As we told you that to install this tool all you need to do is follow a step. Download this tool from gtihub using the git command, go to the directory, give executable permission and that’s all 😛 !! Now you can boot up this tool by using the following command.
1 2 3 4 | git clone https://github.com/skavngr/rapidscan.git cd rapidscan chmod +x rapidscan.py ./rapidscan.py |
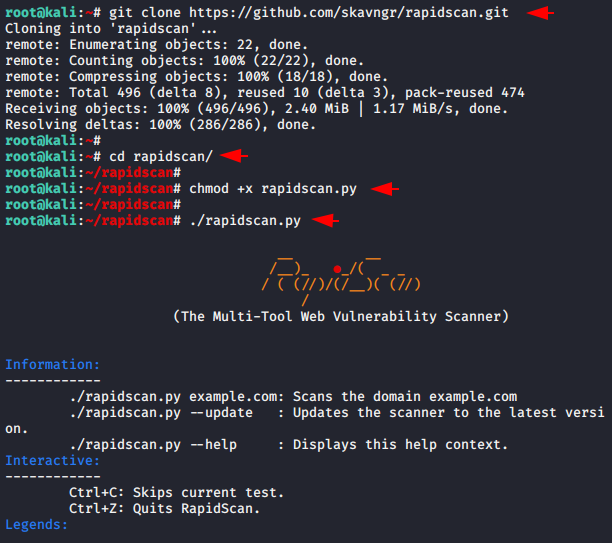
Everything in this tool is classified, so you can read all the specifications of this tool one by one.

Test Vulnerability
When you scan any target, it will first find the necessary equipment and if any is missing then you have to download it yourself. Let’s move on to the results.
1 | ./rapidscan.py example.com |

Service Detected
As you can see it has detected the services available on the web server and also classified the severity.

Hmm 🙁 !! RDP server is discoverable with UDP packets, causing the attacker to either crash the service or even perform brute force attacks using ncrack type tools.

Firewall Detected
We think this can be a helpful tool to detect if a firewall is active or not.

Likewise, it performs almost 80 tasks at the same time to get deeper information about the target.





