
Hey Folks, this article can be valuable for bug bounty hunters and CTF players because in this tutorial we will talk about the best hidden directory finder tools that will help you do enumeration.
What do you get ?
- gobuster
- dirb
- dirsearch
- Wfuzz
- konan
- dirhunt
- Metasploit
- disbuster
Lets take a look 🙂 !!
Gobuster
Gobuster is an open source tool designed to force URI (files and directories) and DNS subdomains. The Gobuster tool provides a command line interface (CLI) that is built into the Go programming language. Downloading this tool is not difficult, just let us execute the following command.
|
1 |
apt-get install gobuster |
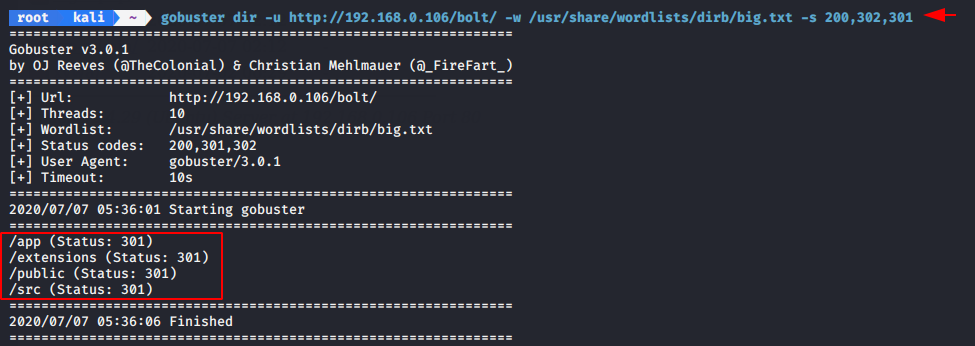
After completing the download we can launch bruteforce attack to find the hidden directory in the web directory.
- -u –url string
- -w –wordlist string
- -s –statuscodes string
|
1 |
gobuster dir -u http://192.168.0.106/bolt/ -w /usr/share/wordlists/dirb/big.txt -s 200,302,301 |
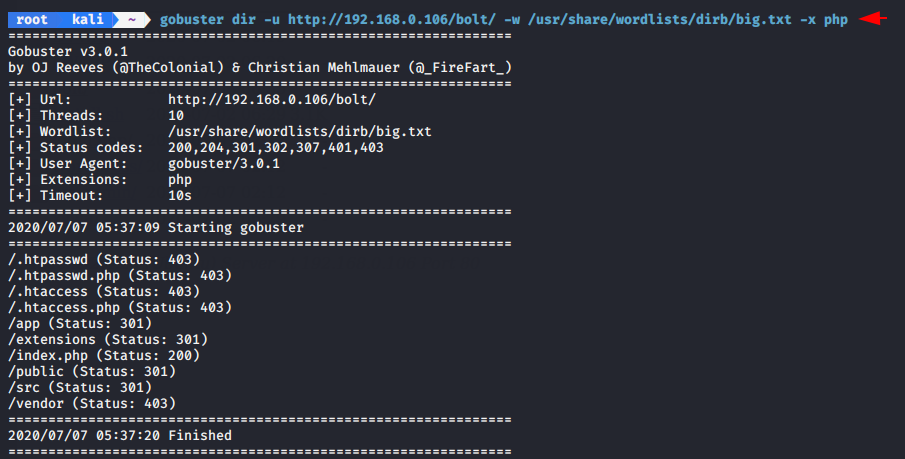
We can use the “-x” syntax to find the specifics extension files.
- -x –extensions string
|
1 |
gobuster dir -u http://192.168.0.106/bolt/ -w /usr/share/wordlists/dirb/big.txt -x php |
DIRB
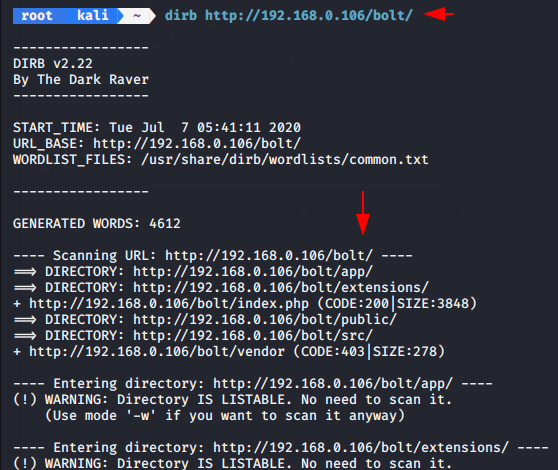
DIRB is a Web Content Scanner. It is in-built kali linux tool and works by launching a dictionary based attack against a web server and analyzing the response but remember is a content scanner not a vulnerability scanner.
When we will exeute the following command it will start the brute force attack and dumps the all hidden directory.
|
1 |
dirb http://192.168.0.106/bolt/ |
Similary we can use the given syntax to find the specifics files or directory.
- -X = extensions
|
1 |
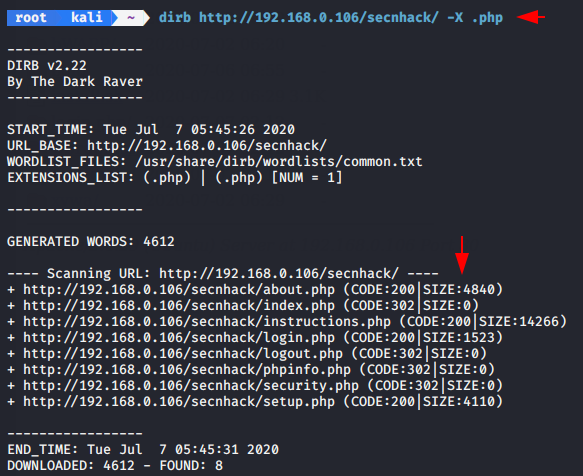
dirb http://192.168.0.106/secnhack/ -X .php |
Dirsearch
Dirsearch is a brute-force tool that is written in Python and used for find hidden web directories and files. It can run on Windows, Linux, and macOS, and it offers a simple, yet powerful command-line interface.
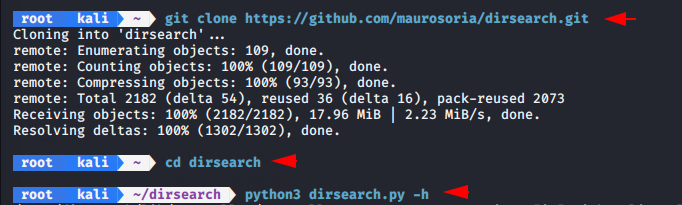
Download this tool from github page and when the downloaded is complete the directory will be automatically created on terminal after then we can start this tool by using the python tool.
|
1 2 3 |
git clone https://github.com/maurosoria/dirsearch.git cd dirsearch python3 dirsearch.py -h |
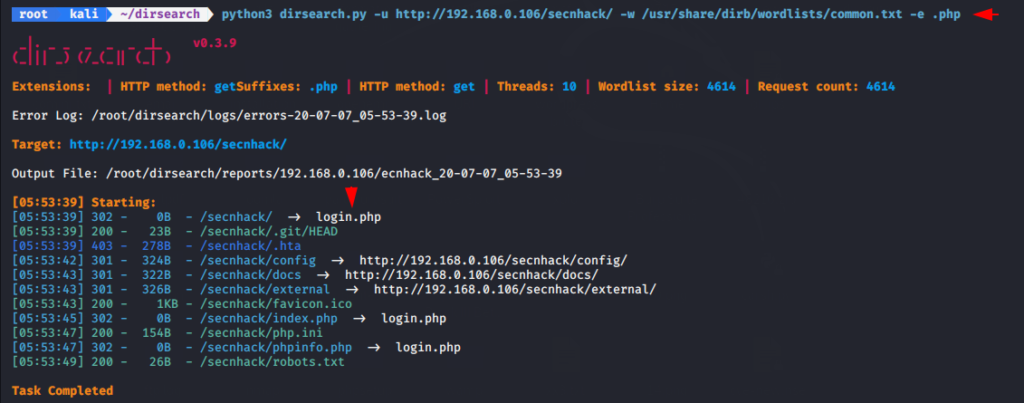
Now we will launch brute force attack with extension facility.
- -u = url
- -w = wordlist
- -e = specifics extensions
|
1 |
python3 dirsearch.py -u http://192.168.0.106/secnhack/ -w /usr/share/dirb/wordlists/common.txt -e .php |
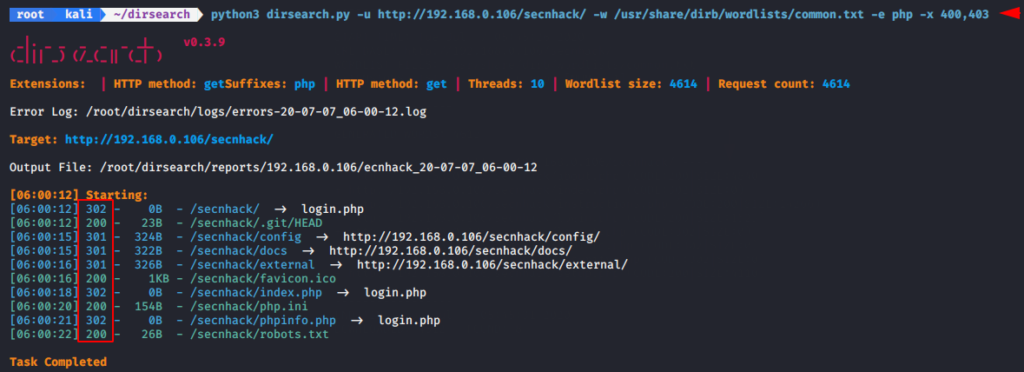
Lets move on further and try to dump the results with specific status code.
- -x = hide response
|
1 |
python3 dirsearch.py -u http://192.168.0.106/secnhack/ -w /usr/share/dirb/wordlists/common.txt -e php -x 400,403 |
Wfuzz
Wfuzz is a open source tool designed for brute forcing Web Applications, it can be used for finding resources such as brute force GET and POST parameters for checking different kind of injections (SQL, XSS, LDAP,etc), bruteforce Forms parameters (User/Password), Fuzzing,etc.
Wfuzz is in-built in Kali Linux, hence we can start this by type “wfuzz” on terminal. Keep in mind we have to mention the “FUZZ” word after the URLs.
- –hc = status
- -u = url
- -w = wordlist
|
1 |
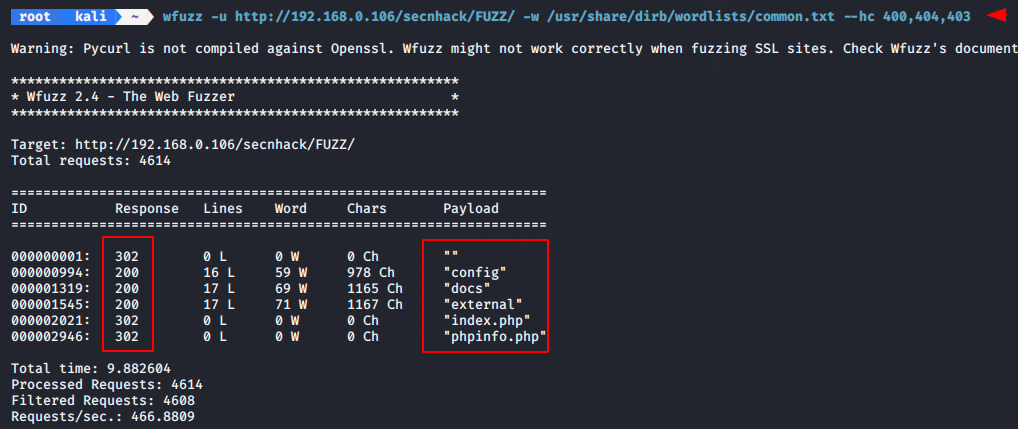
wfuzz -u http://192.168.0.106/secnhack/FUZZ/ -w /usr/share/dirb/wordlists/common.txt --hc 400,404,403 |
Konan
Konan is an another open source tool that is hosted on github page and designed to brute force directories and files names on web/application servers.
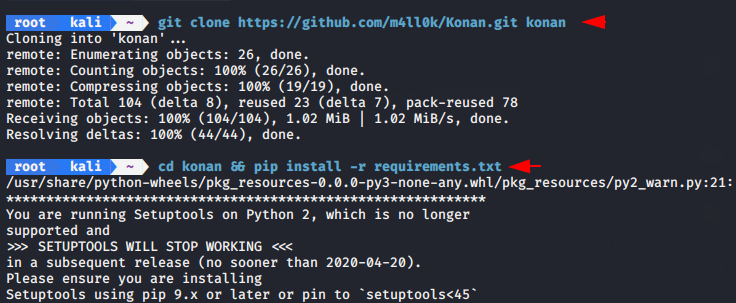
First we will download this tool from Gitub and after that we will have to fulfill some requirements of this tool by executing the following command.
|
1 2 |
git clone https://github.com/m4ll0k/Konan.git konan cd konan && pip install -r requirements.txt |
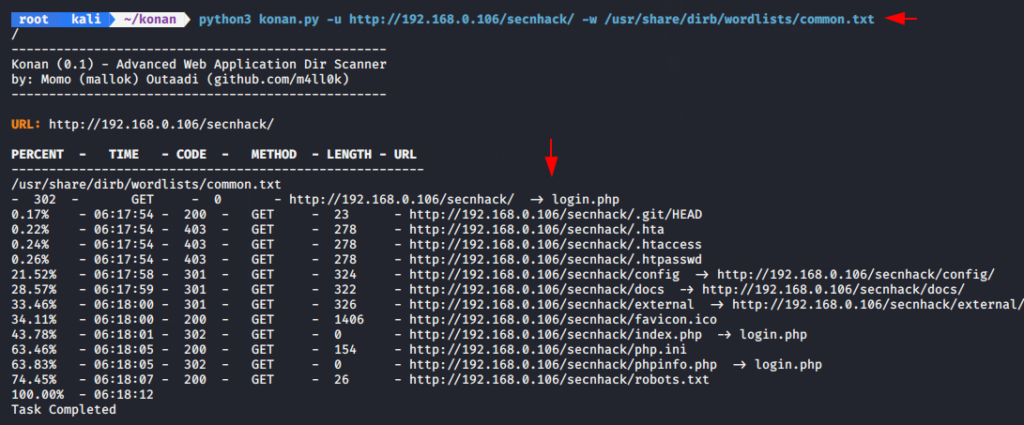
Lets take a example and try to dump the directory list.
|
1 |
python3 konan.py -u http://192.168.0.106/secnhack/ -w /usr/share/dirb/wordlists/common.txt |
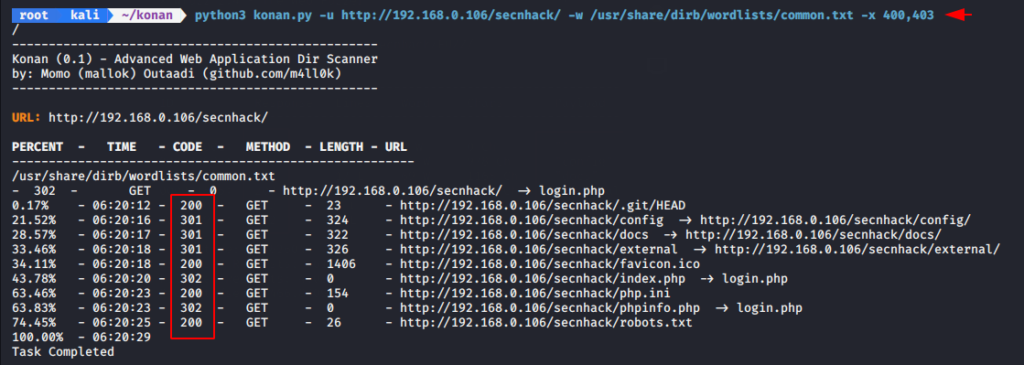
Now we will uses the exclude feature of this tool to skip the some status code.
- -x = –exclude
|
1 |
python3 konan.py -u http://192.168.0.106/secnhack/ -w /usr/share/dirb/wordlists/common.txt -x 400,403 |
Dirhunt
Dirhunt is a web crawler or hidden directory finder. This tool can find interesting things if the server has the “index of” mode enabled. Dirhunt is also useful if the directory listing is not enabled because it can dumps the hidden directory.
We do not have to make much effort to download this tool, we can download it by pip tool.
|
1 |
sudo pip3 install dirhunt |
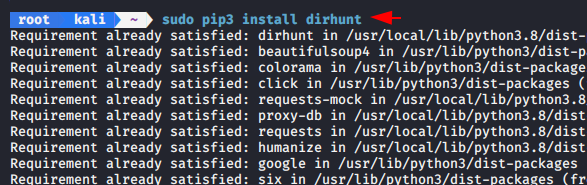
Dirhunt can be a useful tool to find hidden directories of live websites.
- -x = exclude
|
1 |
dirhunt http://192.168.0.106/secnhack/ -x 400,402 |
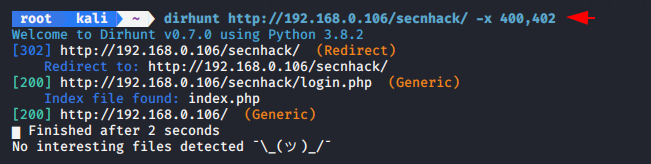
Metasploit
If you know about the metasploit framework then you will understand batter about this tool because this module identifies the existence of interesting directories in a given directory path.
Start the metasploit framework by type “msfconsole” on terminal and then enter the following command. After execute the following
command it will gives the result such as below given image.
|
1 2 3 4 5 |
msf5 exploit(multi/handler) > use auxiliary/scanner/http/dir_scanner msf5 auxiliary(scanner/http/dir_scanner) > set rhosts 192.168.0.106 msf5 auxiliary(scanner/http/dir_scanner) > set path secnhack/ msf5 auxiliary(scanner/http/dir_scanner) > set dictionary /usr/share/dirb/wordlists/common.txt msf5 auxiliary(scanner/http/dir_scanner) > run |
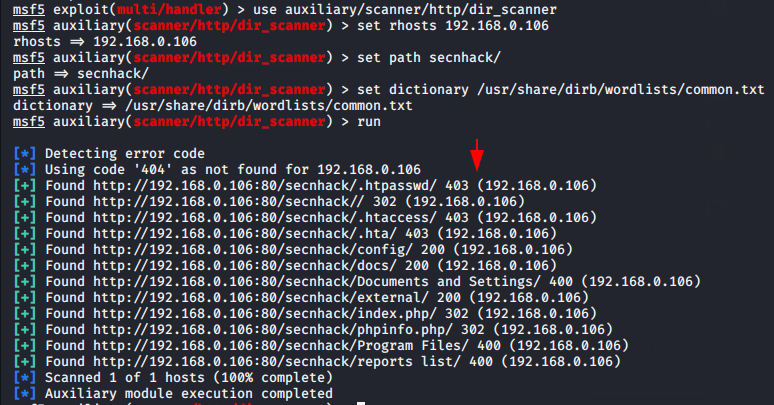
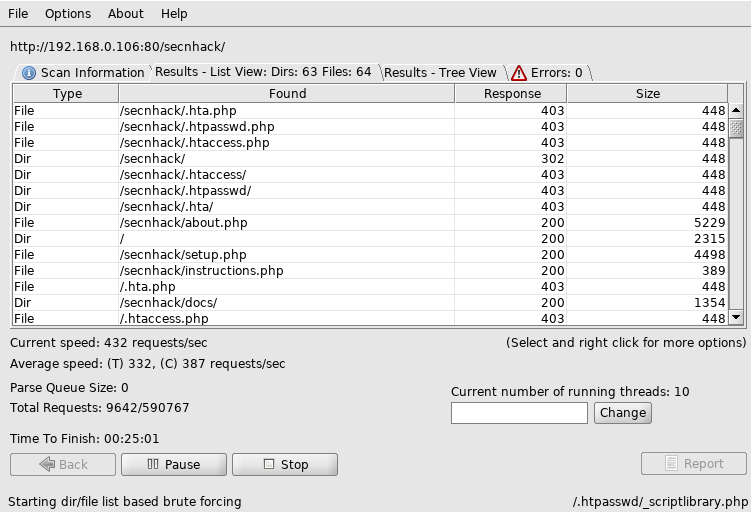
Disbuster
DirBuster is especially designed to brute force directories and files names on web/application servers which is GUI based tool . Often is the case now of what looks like a web server in a state of default installation is actually not, and has pages and applications hidden within therefore we are using the multiple tool to find that directory’s.
When we enter the “dirbuster” it will automatically opened in our terminal and in which we need to submit the target details as shown given below.
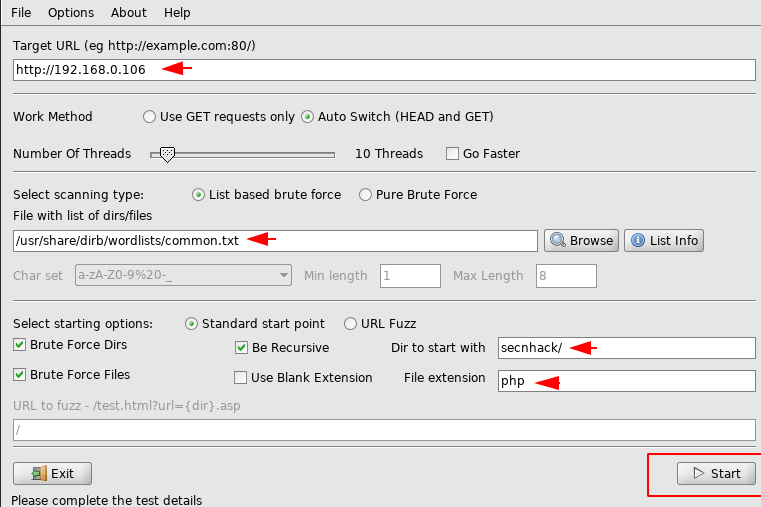
As you can see it has dumped all the hidden directories.

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.





After looking at a number of the blog posts on your site, I truly appreciate
your technique of writing a blog. I saved it to
my bookmark webpage list and will be checking back in the near future.
Please check out my web site as well and tell me how you feel.