
Hey folks, today we are going to talk about an interesting tool called “HawkScan” which can help us in information gathering and reconnaissance of any website. HawkScan is an open source tool that is available on github. It is automated tool which is designed for gather the information about the website such as : cms version, header details, hideen direcotry, vulnerability etc. First we will install this tool and after that test.
Lets take a look 🙂 !!
Installation
First download it from github page using the following command. After installation go to the directory and execute the given command to fulfill the requirements.
1 2 3 | git clone https://github.com/c0dejump/HawkScan.git cd HawkScan pip3 install -r requirements.txt |
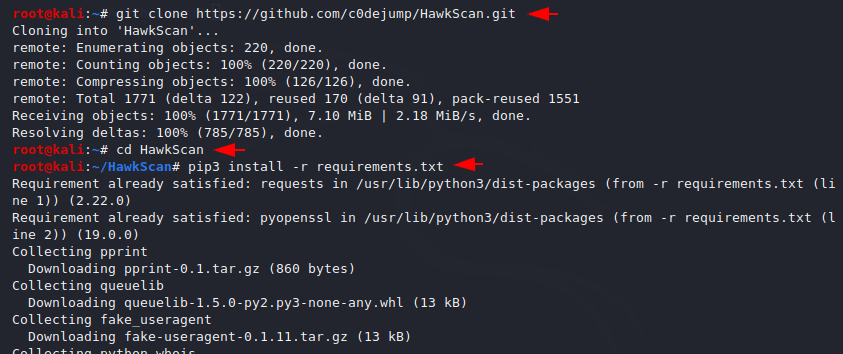
You can see the key features of this tool by execute the help command.
1 | python3 hawkscan.py -h |
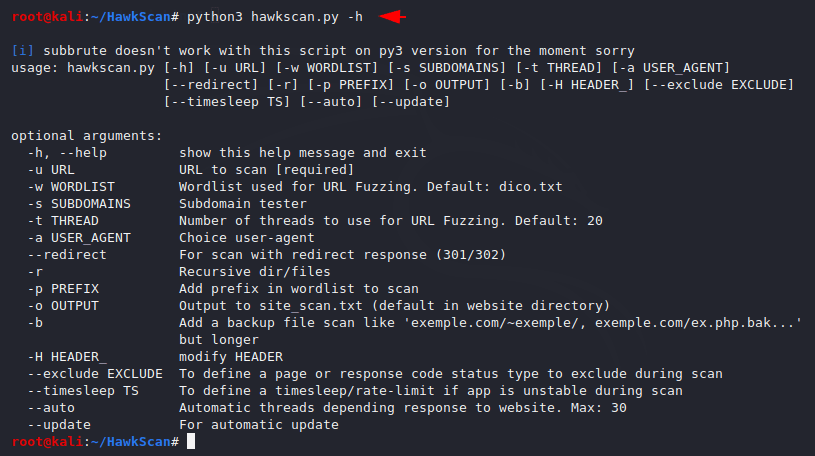
Example
Now first we will take a simple example giving the URL and see the result.
Usage 🙂 python3 hawkscan.py -u
1 | python3 hawkscan.py -u http://testphp.vulnweb.com/ |
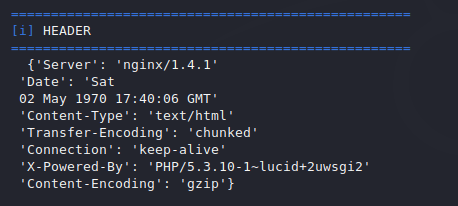
Header
It gives us a lot of information about the website as soon as executing the above command. In the image below you can see the header details that contain information from both the web server and the client.
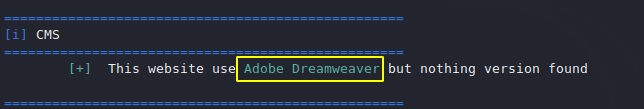
CMS
We can see the cms details of the website and if the version is vulnerable then we can take advantage of it.
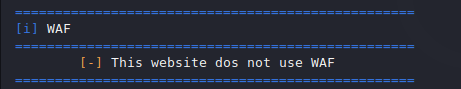
WAF – Web Application Firewall
We can check the firewall is enable or not on the web application.
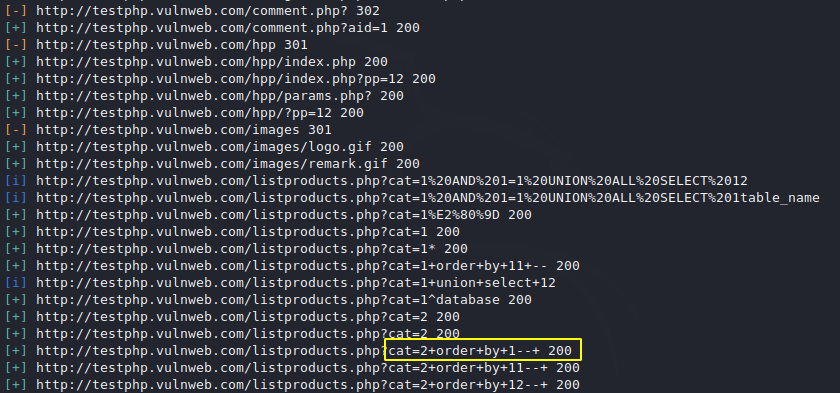
SQL Injection Vulnerability
You can see that it has automatically detected the vulnerability to SQL injection on the web site which we can exploit using sql map.
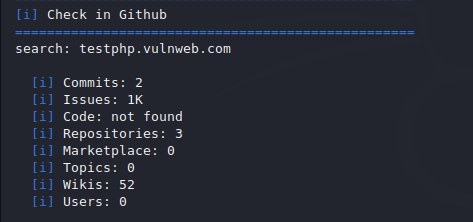
Github Repo
If a repository related to the site is available, it will find out.
Fuzzing
We will use the fuzzing technique to find the hidden directory in the web server.
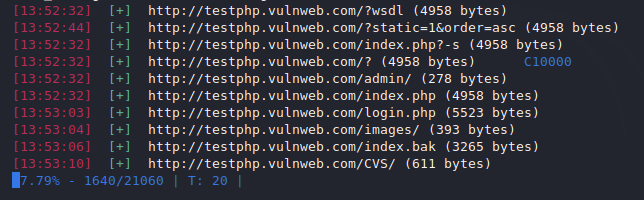
As you can see, on giving a command it will perform all these types of attacks on the web application to detect vulnerabilities and information. Likewise you can use some more features that can help you in reconnaissance.




