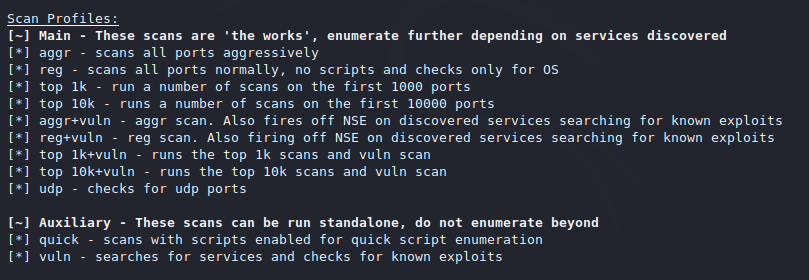
If you are a CTF player or bug bounty hunter then you will know about enumeration how important it is and we waste our time executing commands, But in this tutorial we will talk about a tool that will save our time by executing the command automatically and will give us the result. It will automatically detect web applications’ service, vulnerabilities, hidden directories as well as their exploits, which we can use to take advantage of them. The tool is named “autoenum” which is available on Github.
Requirements
Kali Linux
Lets take a look 🙂 !!
Installation
First we will download it from the github page and install on our terminal. Then we will go to the directory and give some important permission of this tool.
1 2 3 | git clone https://github.com/thatonetester/autoenum.git cd autoenum chmod +x autoenum.sh |
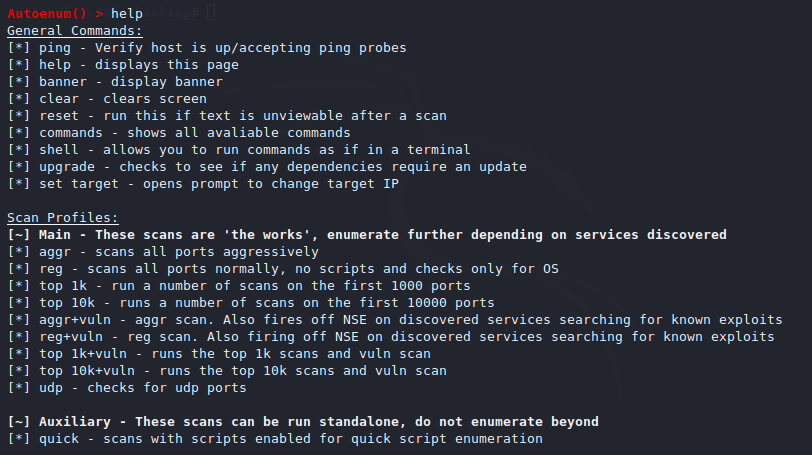
All thing is complete ! we can start this tool using the bash command. After start the tool the “autoenum” will apear on terminal in which we can use the help command to see the features of this tool.
1 | bash autoenum.sh |
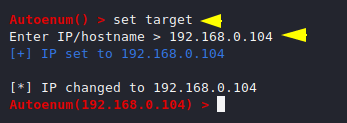
First we have to enter the IP address of the target machine that we want to enumerate. Keep in mind we have to give only the IP address.
Aggressive Scan
Now we can enumerate the services one by one. First we will use this aggressive scan feature.
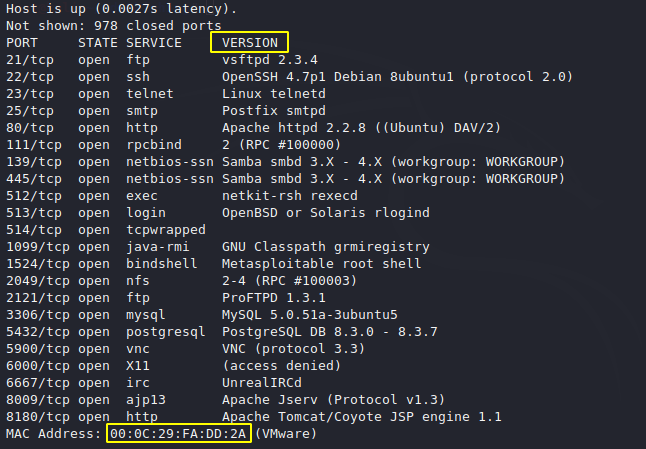
As you can see it has given details of open ports and their versions.
Without execute the more command it will automatically find the NSE vulnerable script for open ports.
Aggressive Scan and Vulnerability
Now it is time to find the vulnerability on the host machine, for this we will use the following command. It will take some time but we will get complete information about the target machine.
Results – Ports Scan with Version
Always first it will enumerate the services because some time port exploitation depend on the version of the ports.
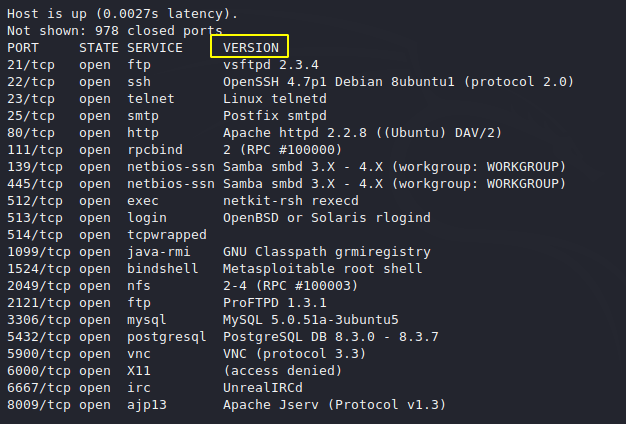
Ports Enumeration
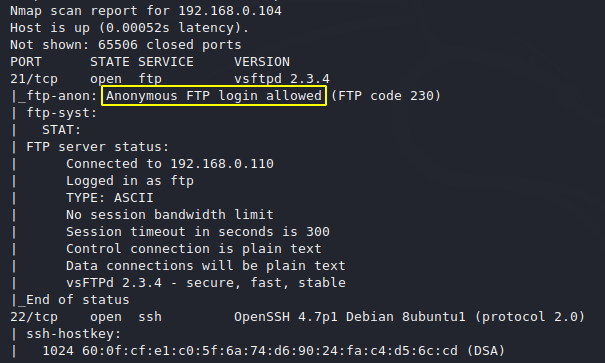
As you can see, anonymous login details of ftp port have been found in it.
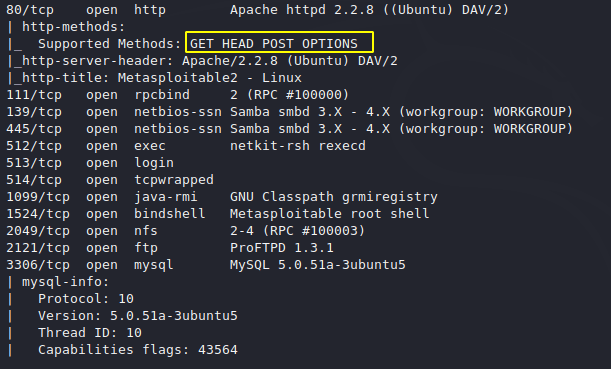
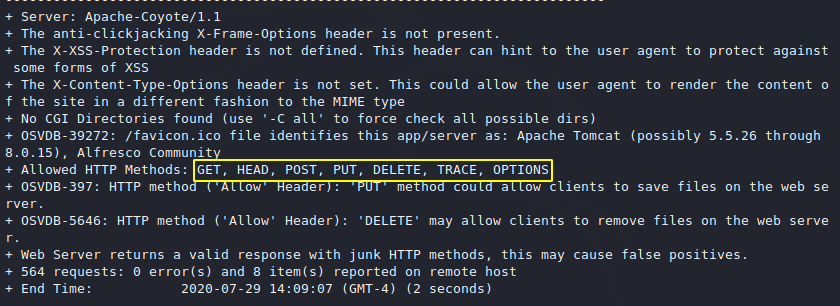
HTTP Methods
We can use the following method to send the request to the server.
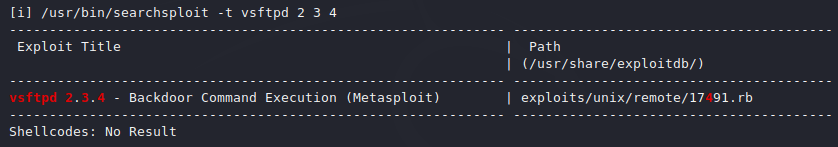
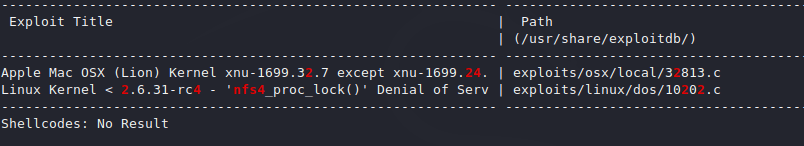
Exploits
As you can see, with the help of port enumeration, we came to know the exploits of the port which can give us control of the web server.
Continue Reading…..
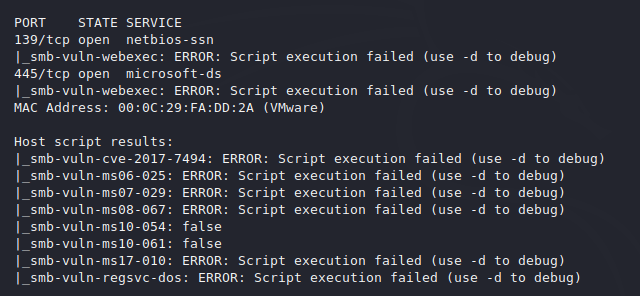
SMB Enumeration
As you can see that it tries to find the well known smb vulnerability by execute the nmap scripts.
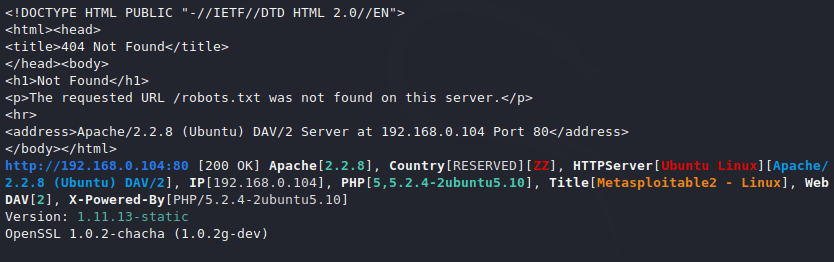
Web Technology’s
We can see the details of the front page of the web application in the CLI interface.
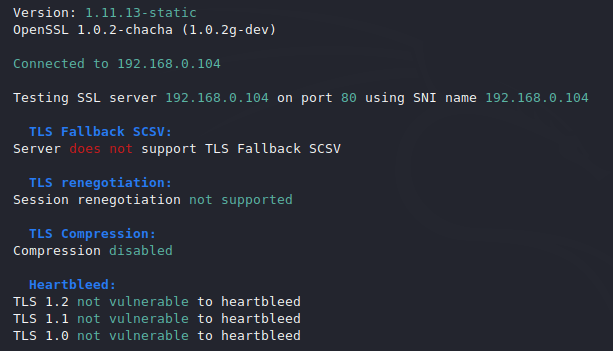
SSL Testing
It is testing well-known ssl vulnerabilities on the target machine such as heartbleed etc.
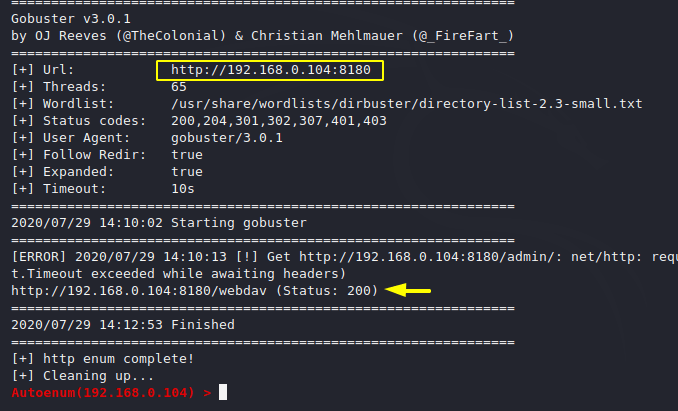
Fuzzing
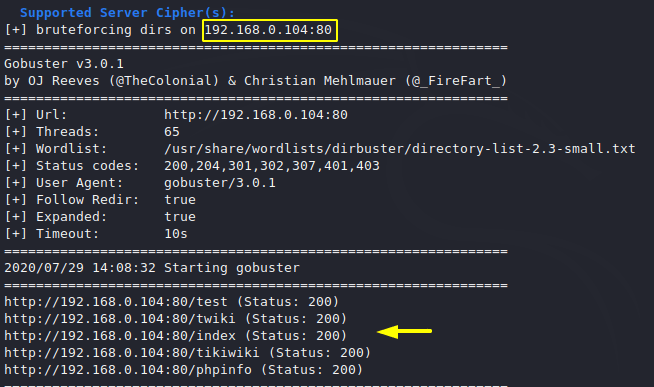
It is trying to find the hidden directory using the Go buster tool.
HTTP Methods with Nikto
As you can see that it has provide us the deep details of port 80 with uses the nikto tool.
It will continuously tries fuzzing on every web application protocol.
Done !! As you can see it gives us all these details by executing only one command. So it can be used when we are playing CTF challenges so that we can save our time. Also, you can check more features of this tool and get more information.