
Hey Folks, today’s article is going to be very interesting and important for bug bounty hunters because in this article we will tell you about a tool by which you can easily find cross site scripting (XSS) vulnerability in any web application through waybackurls.
Let’s take a look at it 🙂 !!
Installation of Golang
First of all we have to install GO in our system and set the GOPATH environment variables one by one. We are pretty sure that you will not get any error after executing the given commands carefully commands.
1 2 3 4 5 | sudo apt install -y golang export GOROOT=/usr/lib/go export GOPATH=$HOME/go export PATH=$GOPATH/bin:$GOROOT/bin:$PATH source .bashrc |

QuickXSS Tool Installation
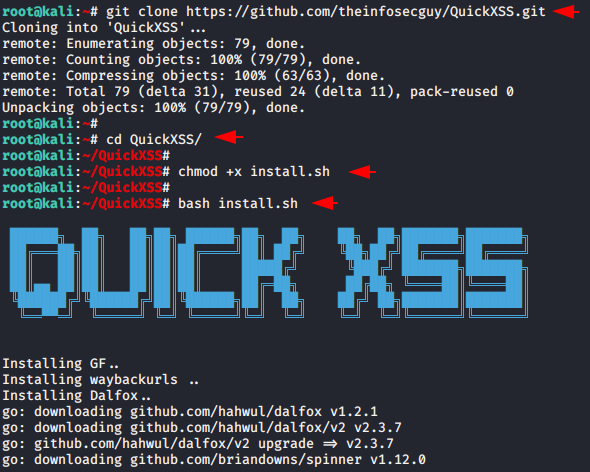
Now let us move to the second part of this article where we have to install this tool using the command given below. After waiting few seconds you will automatically exit from the installation part and then you can run this tool.
1 2 3 4 | git clone https://github.com/theinfosecguy/QuickXSS.git cd QuickXSS chmod +x install.sh ./install.sh |
Triggered XSS Vulnerability
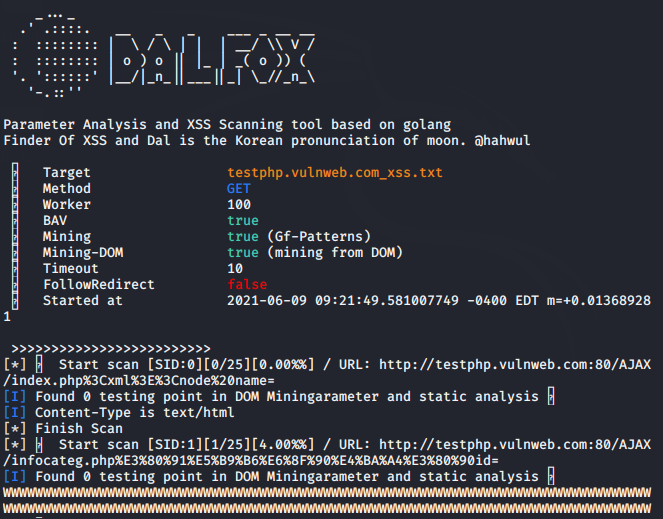
Now it’s time to demonstrate an example of this tool. You just need to give the domain name you want to hunt and it will automatically find the working “params” first and then exploit on them to find XSS vulnerabilities. In addition, it generates a complete report of the domain that you have given it with the exploited “params” too.
1 | bash QuickXSS.sh -d testphp.vulnweb.com |

Good 🙂 !! After executing the command it gives us all the details about the target and the mode of attack.
Nice 🙂 !! In addition, it is also capable of finding other vulnerabilities as you can see in the image below that it has successfully detected the “SQL Injection” vulnerability in the web application.

Done 🙂 !! As you can see the vulnerable “parameter” is found successfully and even it gave us complete command with payload to exploit directly.

Work :O !! But we check once and get the result like you can see in the image below. s you can see how quickly we found critical vulnerability on web application.

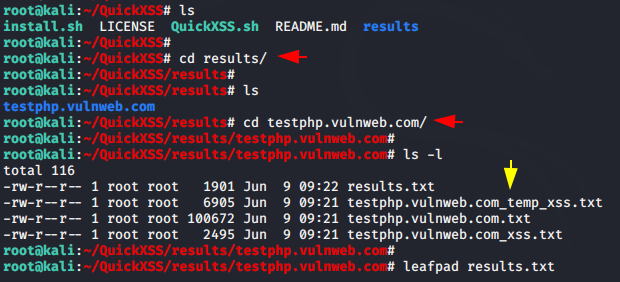
Great 😛 !! As we told you earlier that it saves all exploited placed along with payload which you can easily check later by going to the directory of the domain exactly which you gave it.





\[\e]0;\u@\h: \w\a\]\[\033[;94m\]┌──(\[\033[1;31m\]\u💀\h\[\033[;94m\])-[\[\033[0;1m\]\w\[\033[;94m\]]\n\[\033[;94m\]└─\[\033[1;31m\]$\[\033[0m\]
its is my [root💀kali]–# when i’m running source .bashrc
yes i am getting the same error
what kind of error comes ?