
Hey Folks, in this tutorial we are going to talk about an interesting tool that will help us during solve the CTF challenge. Once the target is compromised we can collect data and a lot of information called privilege escalation. But the good thing is that we don’t have to do anything, just execute the command it will get all the information and give it to us.
Lets take a look 🙂 !!
Installation
In this case we will run this tool with non privileged user as you can see below because as we know that the privilege escalation are used for getting the privileges of accounts.
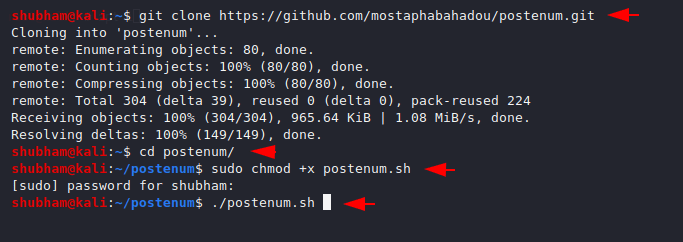
First we will download it from the github page using the following command. After installed we will going into the directory and give some chmod permission.
|
1 2 3 4 |
git clone https://github.com/mostaphabahadou/postenum.git cd postenum/ sudo chmod +x postenum.sh ./postenum.sh |
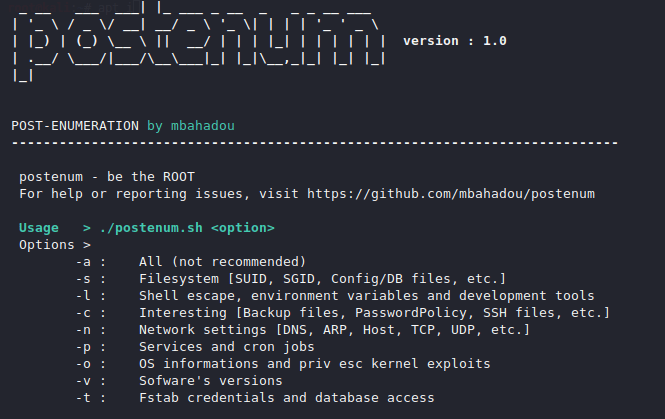
You can see the features of this tool by execute the above commands.
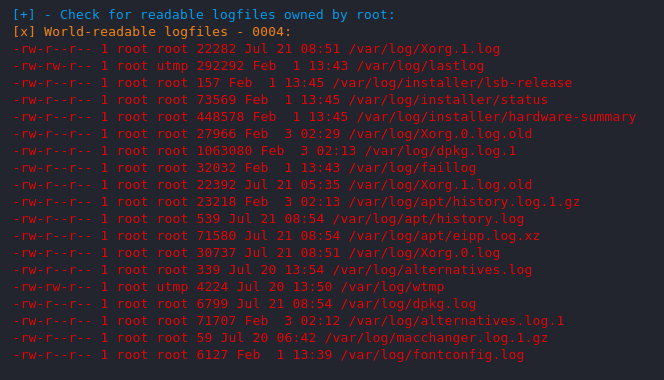
File System
We check the permission and ownership of file and directory by executing separate-2 command but this feature can give us complete information about the file system such as where the file is kept and what its permission.
|
1 |
./postenum.sh -s |
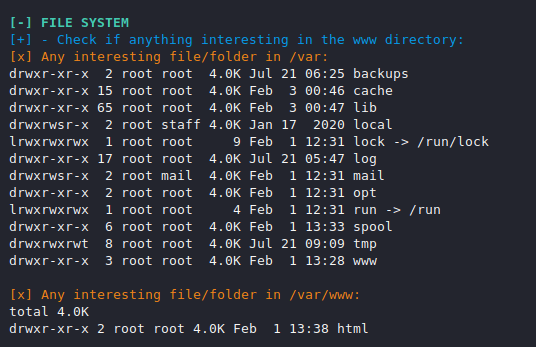
You can see the file read by other users which can be helpful for lfi with log poising attack.
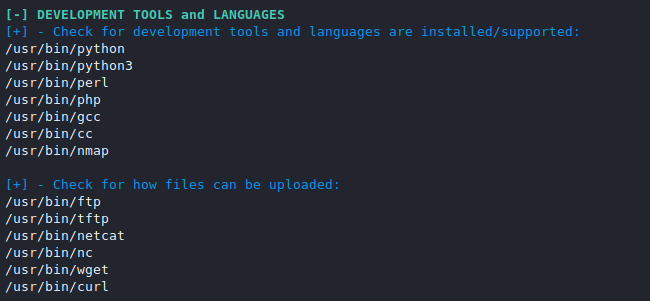
Shell Escape and Tools
With the help of this command we can check the development tools and languages which are installed and supported.
|
1 |
./postenum.sh -l |
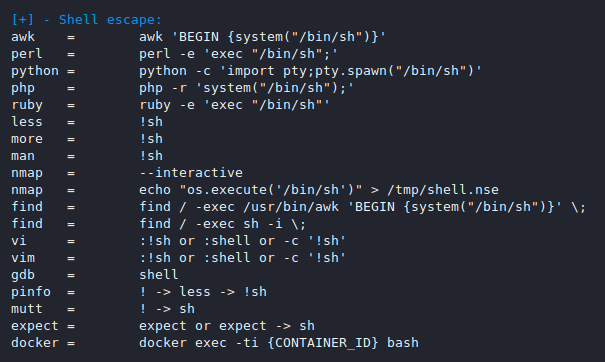
Even we can also identify the shell escape that is the most useful feature for CTF player.
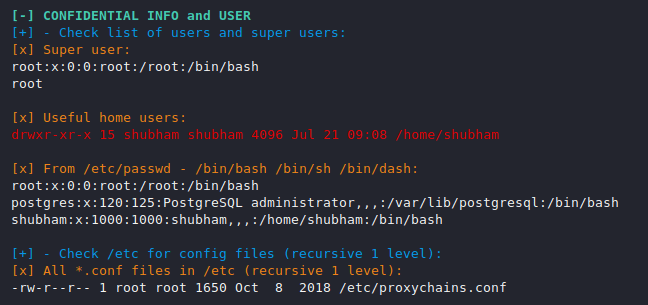
Credentials Info and Users
Linux user knows how to check user and what is permissions but if you have limited time and want to get more details then you can use it.
|
1 |
./postenum.sh -c |
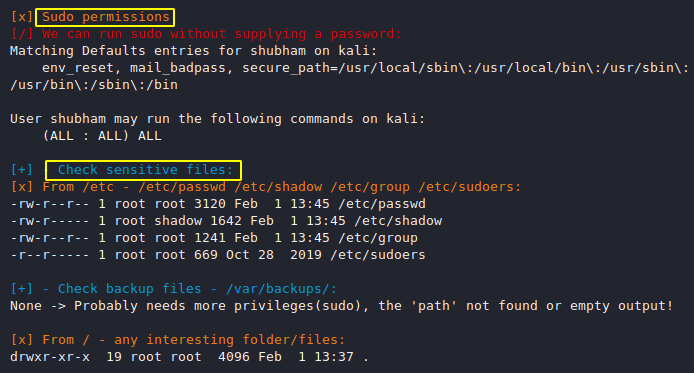
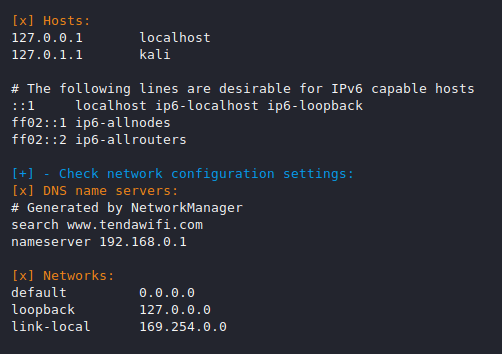
Network
This feature provide us the network configuration of the target machine.
|
1 |
./postenum.sh -n |
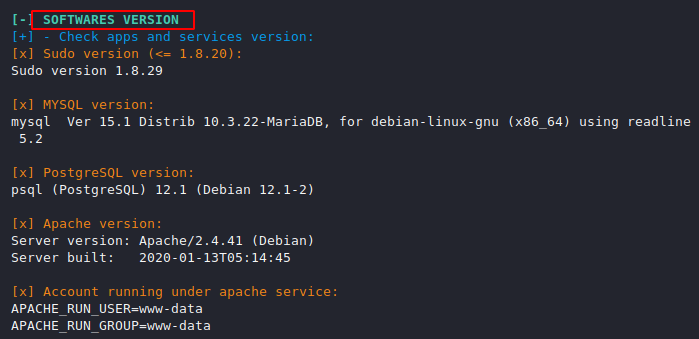
Software Vulnerability
Its will provide us the version details of the protocols.
|
1 |
./postenum.sh -v |
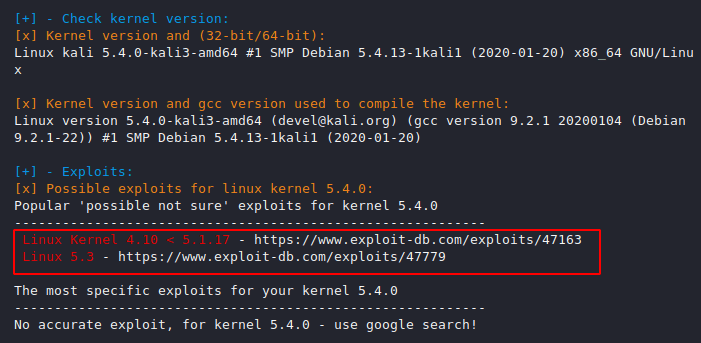
Exploits
This feature can be the leader of this tool as it will provide us with OS information and privilege escalation kernel exploits.
|
1 |
./postenum.sh -o |

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.




