
Hey guys, in this tutorial we will show that how we can decrypt or crack the password of any PDF format file using “John the Ripper” tool. John the Ripper is a free password cracking software tool. Originally developed for the Unix operating system, it can run on fifteen different platforms. John the Ripper is a fast password cracker, currently available for many distributions of Unix, macOS, Windows, DOS, BeOS, and OpenVMS (the latter requires a contributed patch). Its primary purpose is to detect weak Unix passwords.
Let’s take a look 🙂 !!
Protect PDF File
There are many ways to secure your PDF files, which means that you can protect your file with both software or online service. But in our case we will choose an online service to protect our PDF file and we think it can be suitable for anyone.
1 | https://smallpdf.com/protect-pdf |
As you can see, we have successfully protect our PDF file which is currently in the root folder.
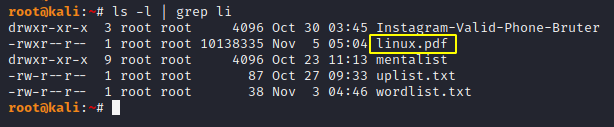
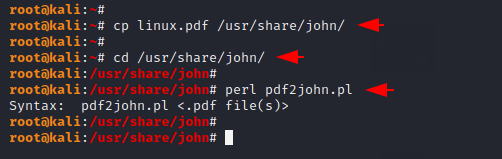
Basically we will first get hashes of the PDF file and then crack the password using those hashes. So we have to transfer our password-protected PDF file to the given location. After reaching the following location we can use the “pdf2john” tool.
1 2 3 | cp linux.pdf /usr/share/john/ cd /usr/share/john/ perl pdf2john.pl |
Get Hashes of PDF File
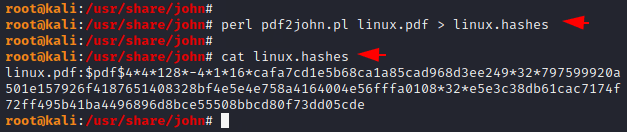
We cannot directly crack the password of a PDF file through the “john the ripper” tool, so we have to get hashes of the PDF file. Just give us the location of the PDF file and the location where we want to save. After executing the command the hash will be automatically saved on your file which you can read by the cat command.
1 2 | perl pdf2john.pl linux.pdf > linux.hashes cat linux.hashes |
Crack Password
Finally the time has come where we will try to crack the password of PDF file through “John the Ripper” tool. Just we need to provide the hashes of pdf file.
1 | john linux.hashes |
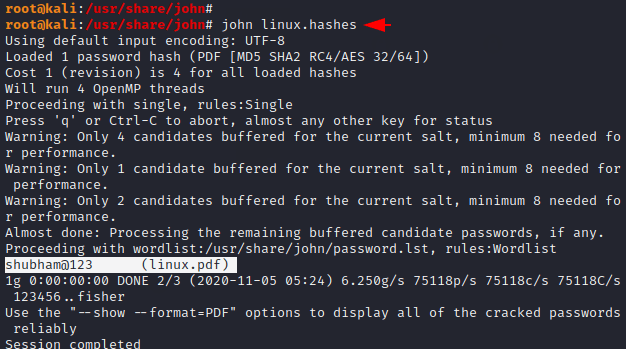
Great 🙂 !! As you can see, we have successfully obtained a valid password to unlock the PDF file.




