CVE-2020-13432
- Credits: John Page (aka hyp3rlinx)
- Website: hyp3rlinx.altervista.org
- Source: http://hyp3rlinx.altervista.org/advisories/HFS-HTTP-FILE-SERVER-v2.3-REMOTE-BUFFER-OVERFLOW-DoS.txt
- twitter.com/hyp3rlinx
- ISR: ApparitionSec
- Exploit Author: hyp3rlinx
- Vendor – www.rejetto.com
Security Issue
This vulnerability allows an remote attackers to trigger an invalid-pointer write access violation via concurrent HTTP requests with a long URI or long HTTP headers like Cookie, User-Agent etc. Remote unauthenticated attackers can send concurrent HTTP requests using an incrementing or specific payload range of junk characters for values in the URL parameters or HTTP headers sent to the server. This results in hfs.exe server crash from an invalid pointer write access violation.
Download Vulnerable Software
1 | https://sourceforge.net/projects/hfs/ |
Full Proof of Concept
Step -1
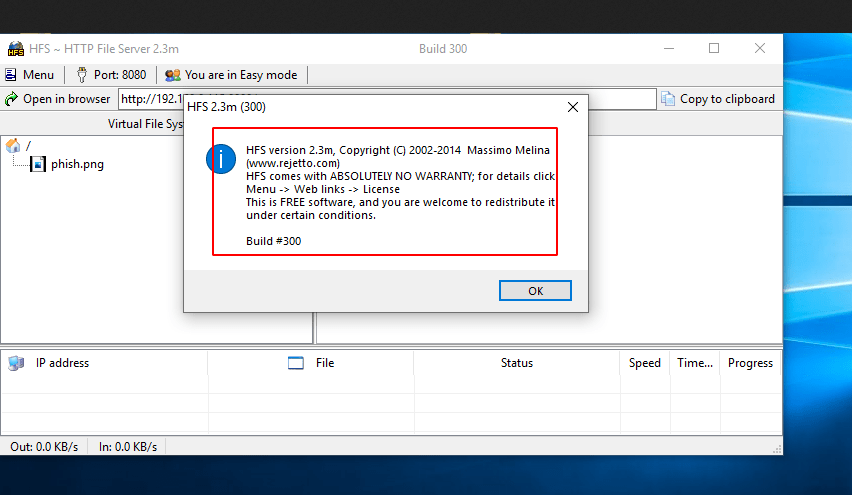
Step -2
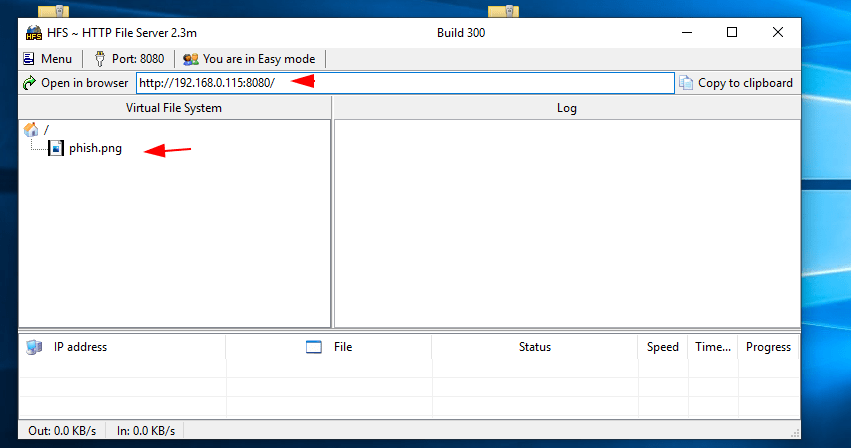
Step -3
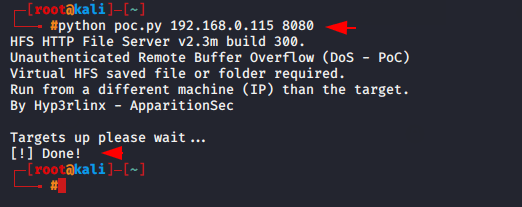
Step -4
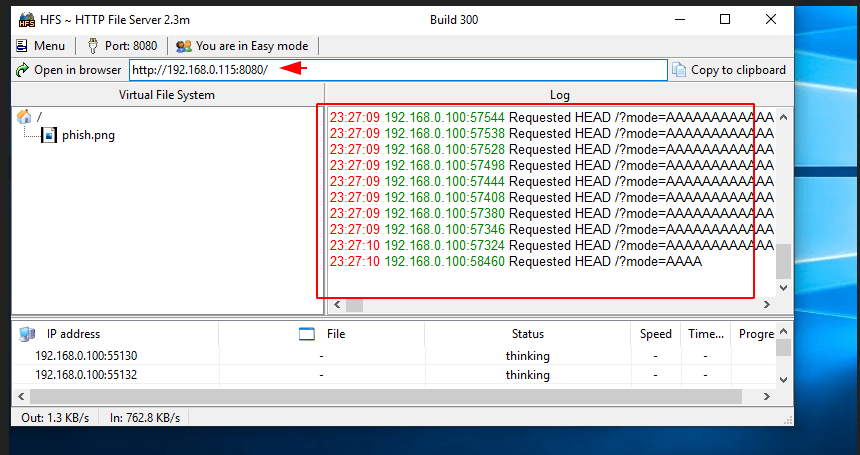
Great !! The vulnerable software is crashed.
About the Author
Virat Sharma Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.