Mobile Platform Hacking (WAN) Through Google Cloud Shell
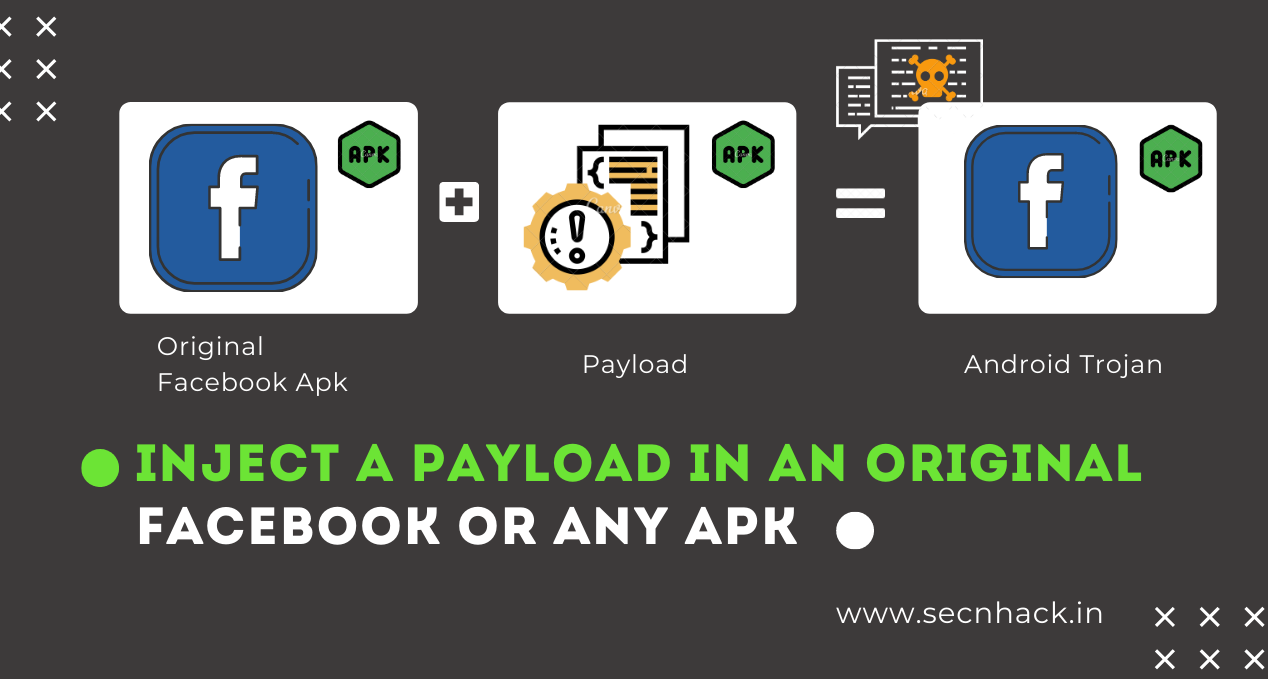
Hey Folks, in this tutorial we are going to discuss about another topic related to google cloud shell. Let’s talk straight away 🙂 !! As you know that to access any android device, we need to take meterpreter session through the kali Linux operating system or any other. But suppose […]
Continue Reading