Hey Folks, in the tutorial we are going to introduce you with an interesting tool called “TIDoS-Framework” . TIDoS is provided as an offensive web application audit framework. It has built-in modules which can reveal potential misconfigurations and vulnerabilities in web applications which could possibly be exploited maliciously. We have mashed up some interesting features which you can read below.
Availability
- Has 5 main phases, subdivided into 14 sub-phases consisting a total of 108 modules.
- Scanning & Enumeration Phase has got 16 modules.
- Vulnerability Analysis Phase has 37 module.
- Exploits Castle has only 1 exploit.
- And finally, Auxiliaries have got 4 modules.
Key Features
- the programming language: TIDoS is fully ported to Python3
- Parallelisation: TIDoS uses multiprocessing to speed up attacks
- Anonymity: Attacking through Tor is possible (95% done)
- Some new modules: arpscan
- A Graphical User Interface for easier interaction with the toolkit
Let’s take a look 😛 !!
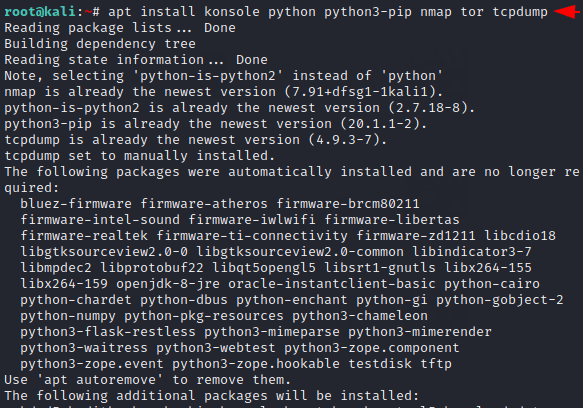
Install Dependencies
Before jumping directly to the installation we have to install some necessary dependencies which we have given below.
1 | apt install konsole python python3-pip nmap tor tcpdump |
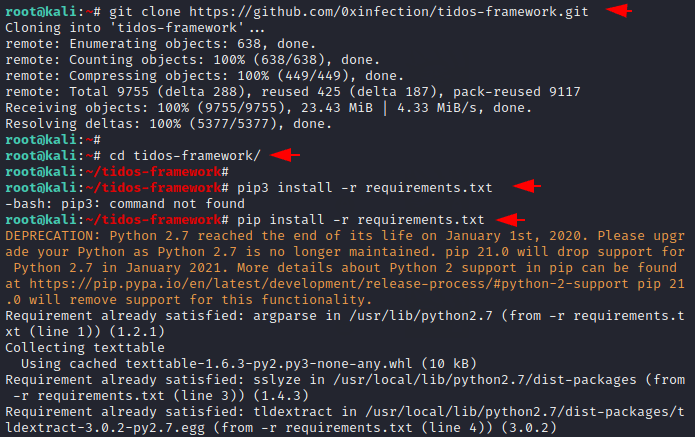
Tool Installation
After downloading all those things we are able to configure this tool in our system. To get the latest version of this tool we have to download it directly from github using git command. After that we will move to the install folder and execute the pip command to install the rest dependencies.
1 2 3 4 | git clone https://github.com/0xinfection/tidos-framework.git cd tidos-framework pip3 install -r requirements.txt pip install -r requirements.txt |
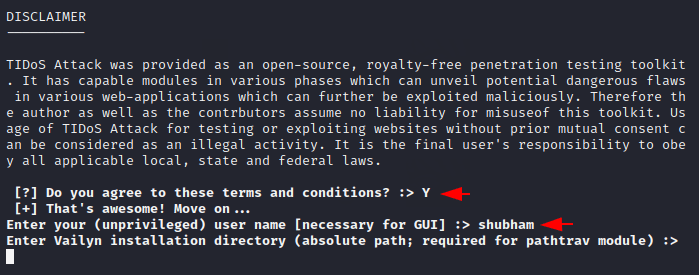
Done 🙂 !! TIDoS-Framework has been completely installed and now we can boot it by using the following command. As soon as we boot this tool, it asks us the name of the unprivileged user. The TIDoS-Framework will be fully started after entering all the required details.
1 | python3 tidconsole.py |
Usage Guide
We can see all the main features available in the tool using the help command.
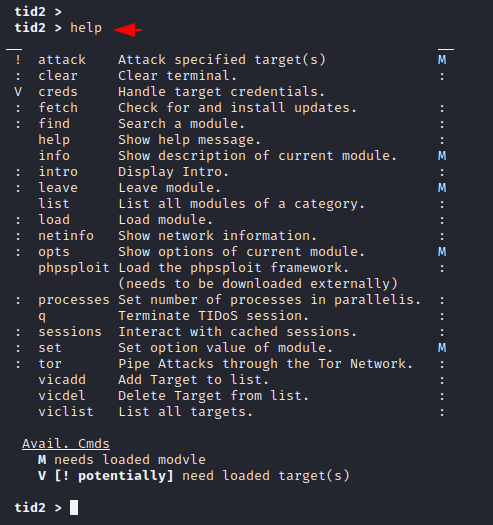
NetInfo
The following command is given to show a brief description about the current network as well as the operating system.
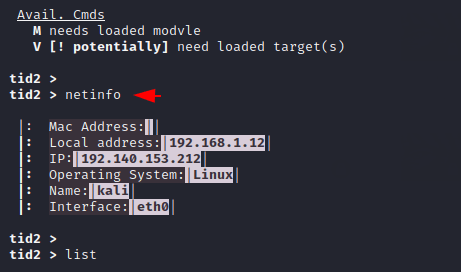
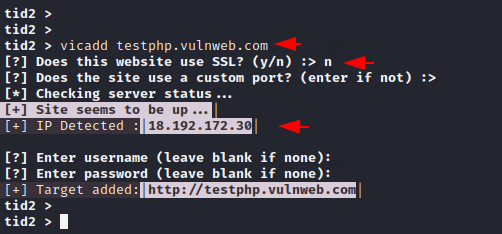
Vicadd – Add Victim
We will add the target description to this tool using the following command after which we can do footprints, reconnaissance and calculations on it.
1 | vicadd < target / domain name > |
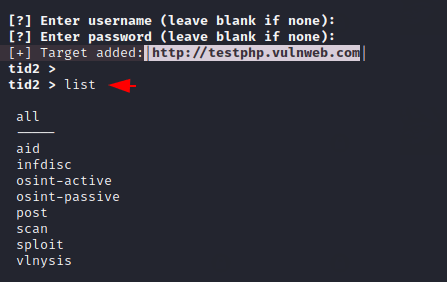
List ALL Modules
It comes with the following types of modules, inside which there are different types of categories. First let’s see all the available modules by using the list command.
1 | list |
List of Categories Inside Modules
If we want to check the available categories in a particular module then we can add the name of that module after the list command.
1 | list < module name > |
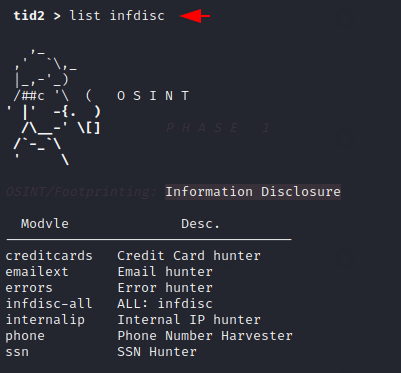
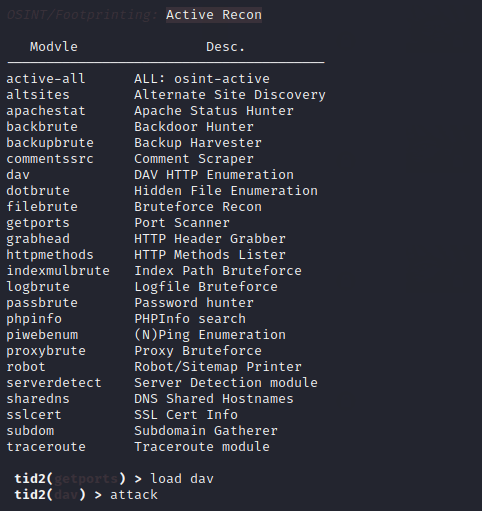
Infodisc – Email Hunter
Now we will choose the email hunting option from the information disclosure module. To use any of the options available in the module we have to use the “load” command. After that we can check complete description of the current module by using the “info” command. Just we need execute the “attack” command to activate any module.
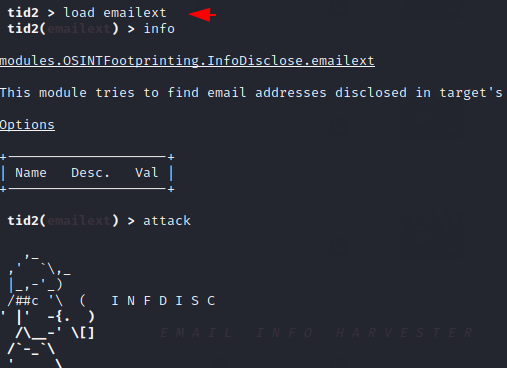
Great 🙂 !! The tools look beautiful and at the same time give us the right information which is actually publicly available on the targeted web application.
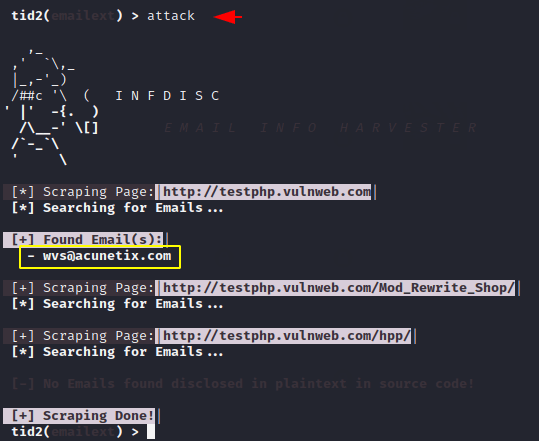
Active OSINT
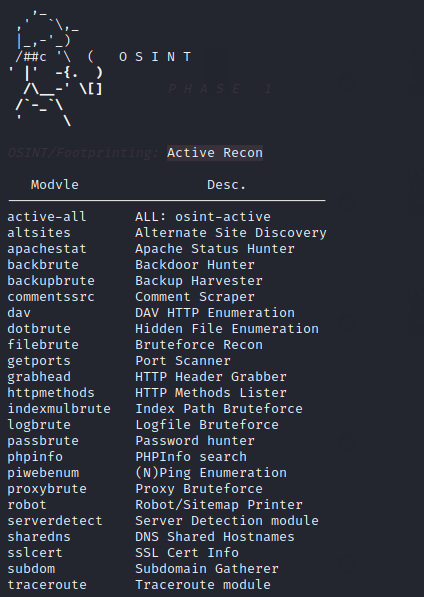
Again we will use the list command to see all the available modules and select one of them that is “osint-active“.
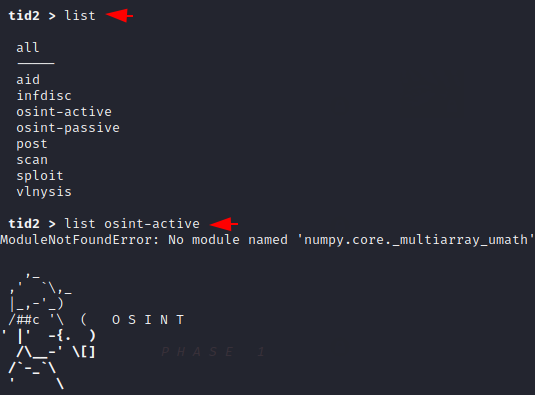
OMG 🙂 !! As you can see below how many options do we get in this tool to do active OSINT on target web application.
Activate All
We will execute the following command to use all available features at the same time.
1 2 | load active-all attack |
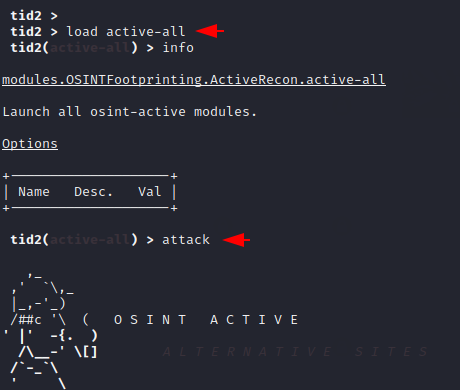
Setting Custom User Agent
To keep yourself anonymous it will randomly set the user agent first and then communicate with the target web server.
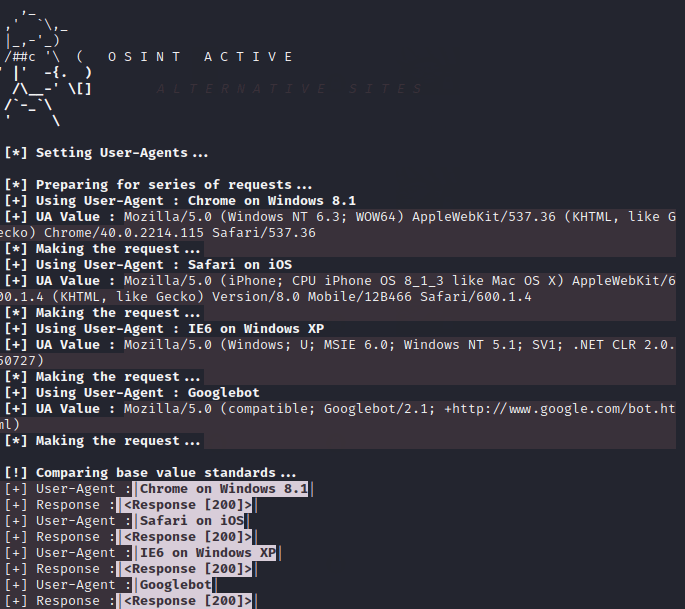
Fuzzing – Apache Status
If the target is hosted on the apache web server then it will try to find out its status.
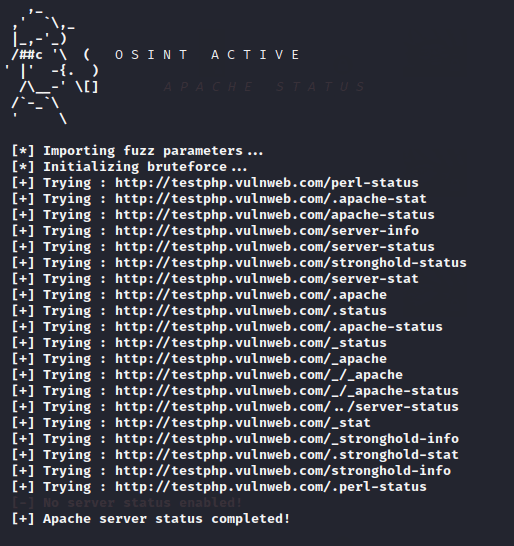
Backdoor Brute forcing
Sometimes we upload our malicious backdoor to the target web server to gain access but after uploading we are unable to find the uploaded backdoor location so through this tool we try to find all available backdoor on the target web server.
Backup Brute force
Some web applications save their previous data or records as a backup to the particular location that it will find through brute forcing.
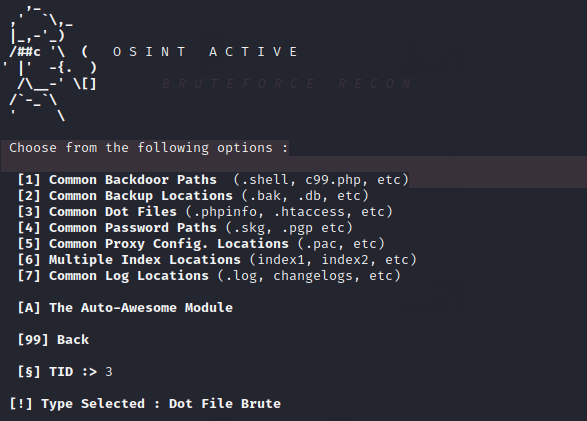
Brute force Recon
At the end of the scan you will get all the options through which you can get some important things through the brute force technique.
Port Scan
Now we will load the following module to find all the open, filters and closed services on the target web server.
1 2 | load getports attack |
Results 🙂 !! As you can see how beautifully it is shown that only two ports are open on the target web server.
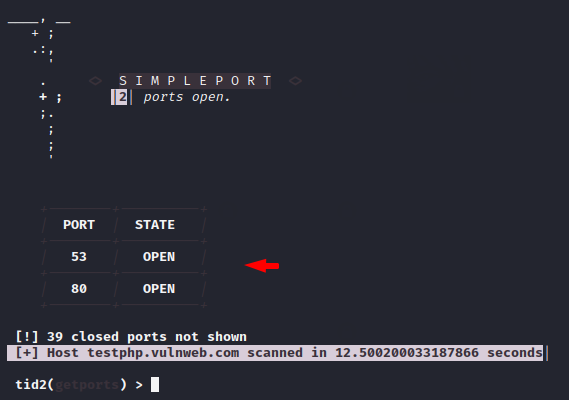
Done 🙂 !! We have covered only the useful options of this module but you can try all the options one by one.
Passive OSINT
Once more we execute the list command to see all the available modules and then check all the options available in this module.
1 2 | list list passive-osint |
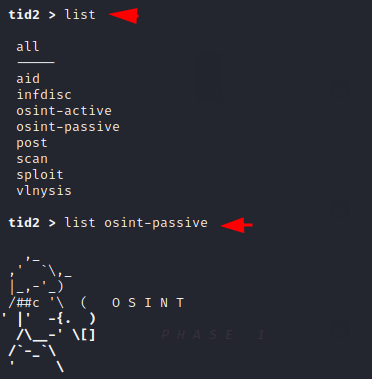
Hmm 🙂 !! Look at in given image below that how many more useful options we find in the passive Osint module.
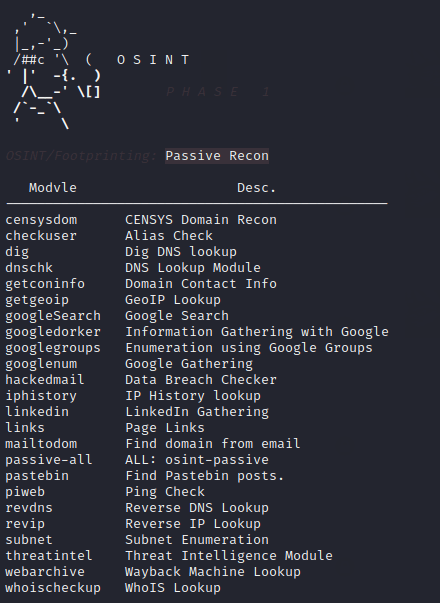
Linkedin Gathering
First of all just load this tool as given in the image below. After that execute “attack” command to activate this feature.
1 2 | load linkedin attack |
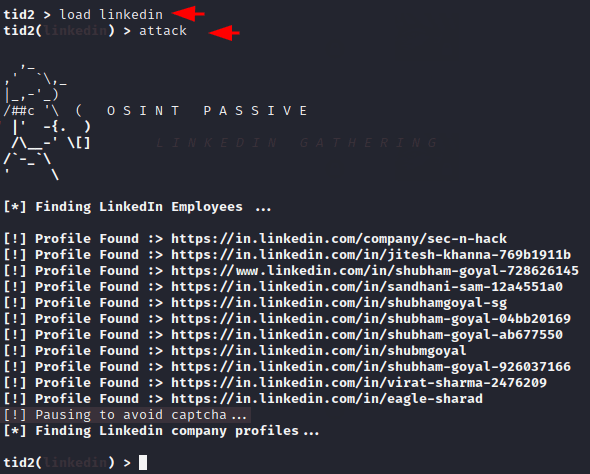
Great 😛 !! The following module will dump all LinkedIn profiles associated with this website. Thus, you can use all the passive osint option one by one yourself.
Scan Module
Now we will select another module called “scan” and check all the options available inside it.
1 2 | list list scan |
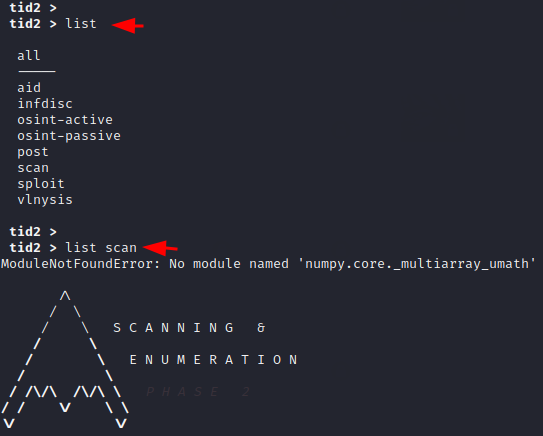
Nice 🙂 !! We feel that this module has everything related to scanning as it comes with almost all the useful tools which is essential for every hacker or cyber security expert.
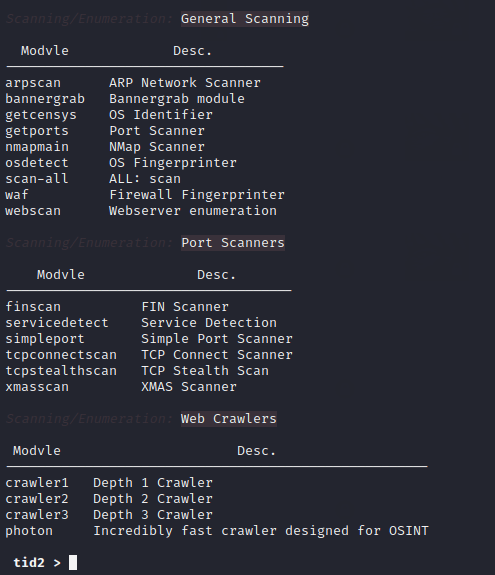
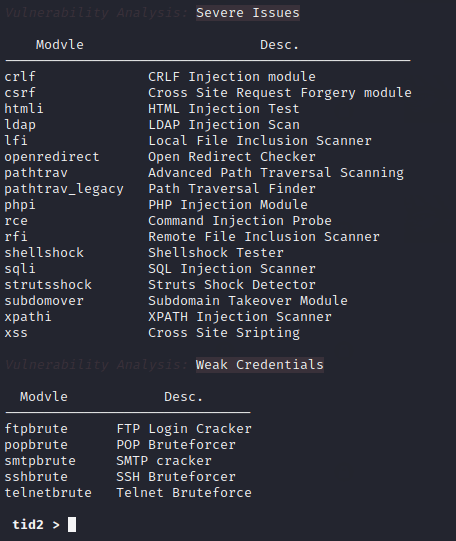
Vulnerability Module
Here are the most awaited things that can be more useful for bug bounty hunters because through this module of the tool we can easily find all available vulnerabilities in web application.
1 2 | list list vlnysis |
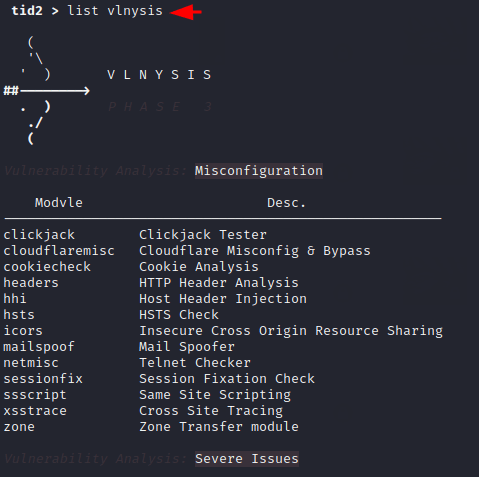
Alright 😛 !! The following types of vulnerabilities can be detected in web applications through this modules of this tool.
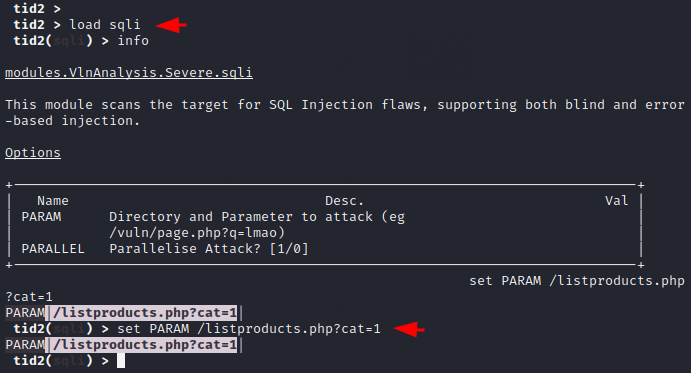
Just we take an example to demonstrate the usage of this module. First we load the SQL module and then set the value of PARAM in which we give parameters where the vulnerability of SQL injection is likely to be found.
1 2 3 | load sql set PARAM < paramter > attack |
Hmm 🙂 !! It will try several combinations of payloads to detect SQL injection in the web application and after successful detection it will result on the terminal.
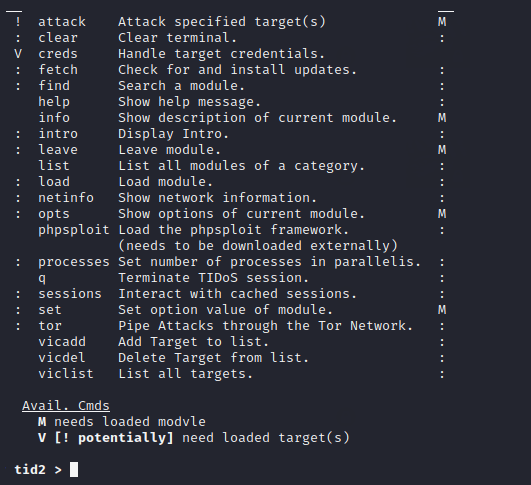
Done 🙂 !! This tutorial is just that and we have covered only useful and few options of this tool, but definitely you will like it when you use it.




