
Hey Folks, in this tutorial we are going to talk about an window based web application vulnerability scanner called “vooki“. It is a free web application vulnerability scanner which gives us a perfect scan report about the scanned networks, applications. It is a user-friendly tool that you can easily scan any web application and find security vulnerabilities. Vooki scanner helps in finding such vulnerability in web application.
Vulnerability
- SQL Injection.
- Command Injection.
- Header Injection.
- Cross-site scripting – reflected.
- Cross-site scripting – stored.
- Cross-site scripting – dom based.
- Missing security headers.
- More.
Let’s take a look 😛 !!
Installation
If you are looking for a web application scanner for a window or mac operating system then you can go with it as it is available for both which you can download from here.
The installation of this tool in both operating systems is quite simple as you can easily configure it in your system by pressing enter 3 to 4 times.
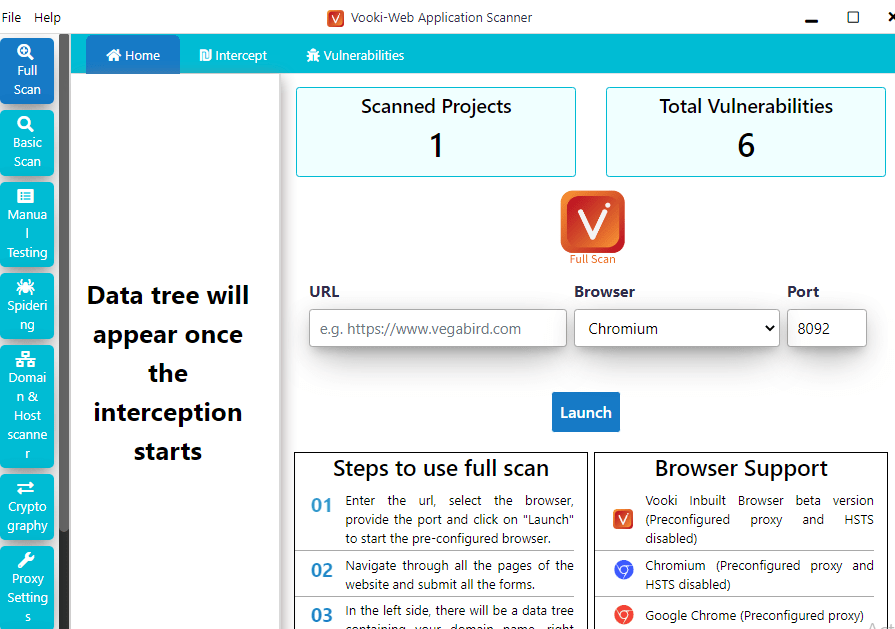
In this tool you get the following options out of which we will try with basic scan first.
Here we have to enter the URL of the target web application that we want to scan.
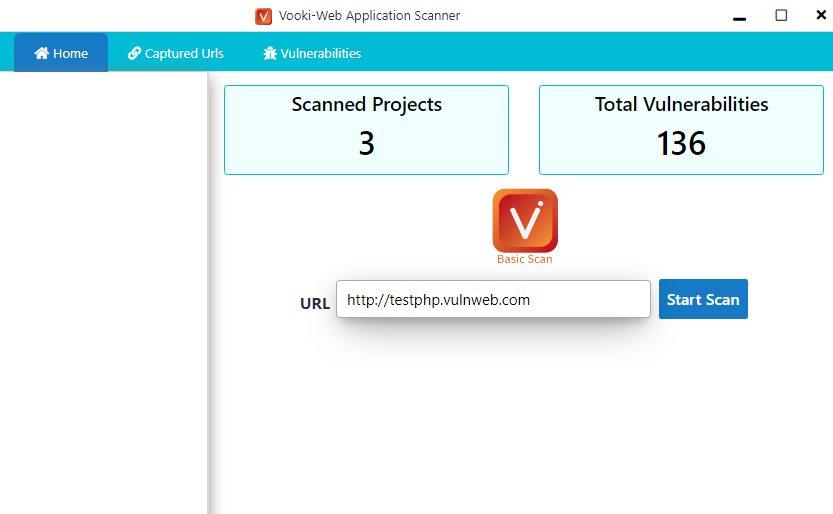
Hmm 🙂 !! After clicking on “start Scan” button the vooki bar will be activated in which we can see all the details that it has found.
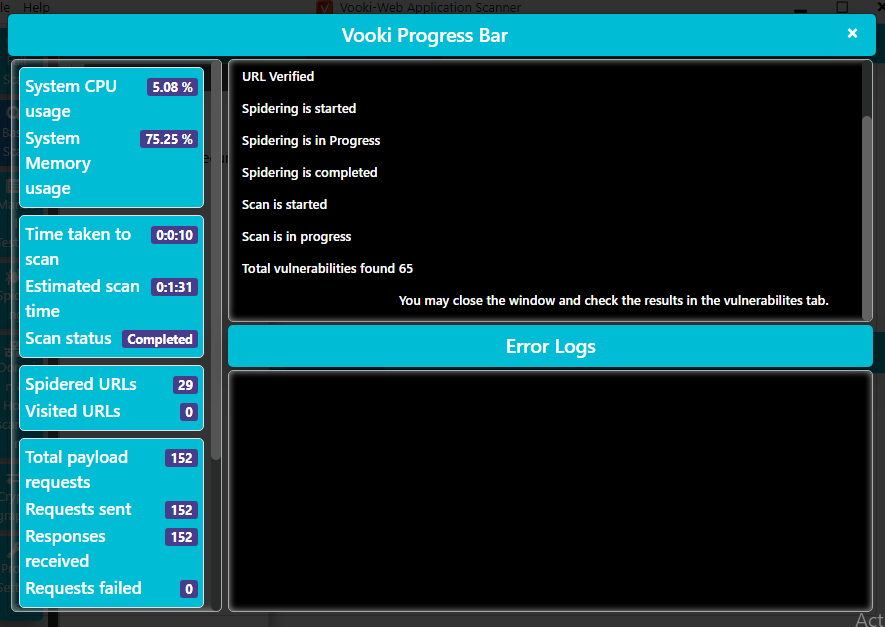
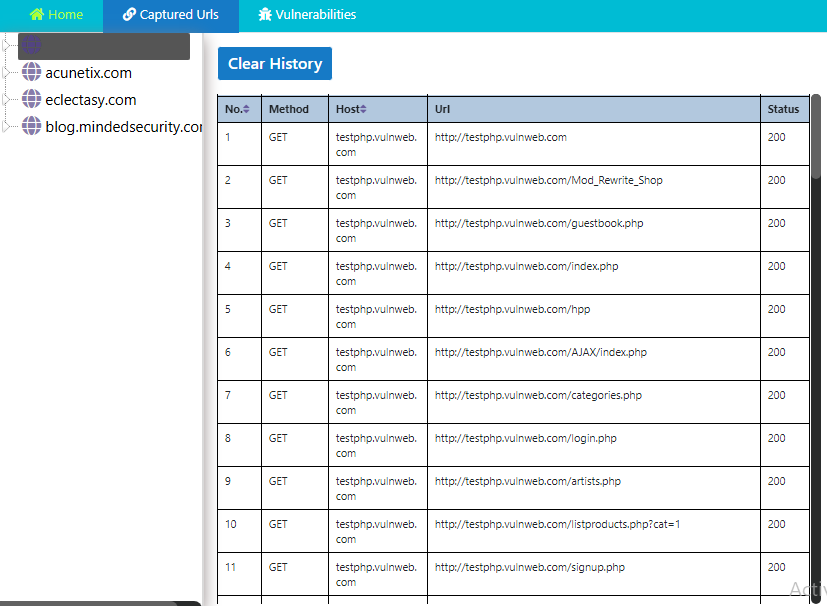
Results 🙂 !! After closing the vooki bar you will redirect to the results page where you can see all the results of the current or previous scans. In this tab we find some sensitive locations of web application.
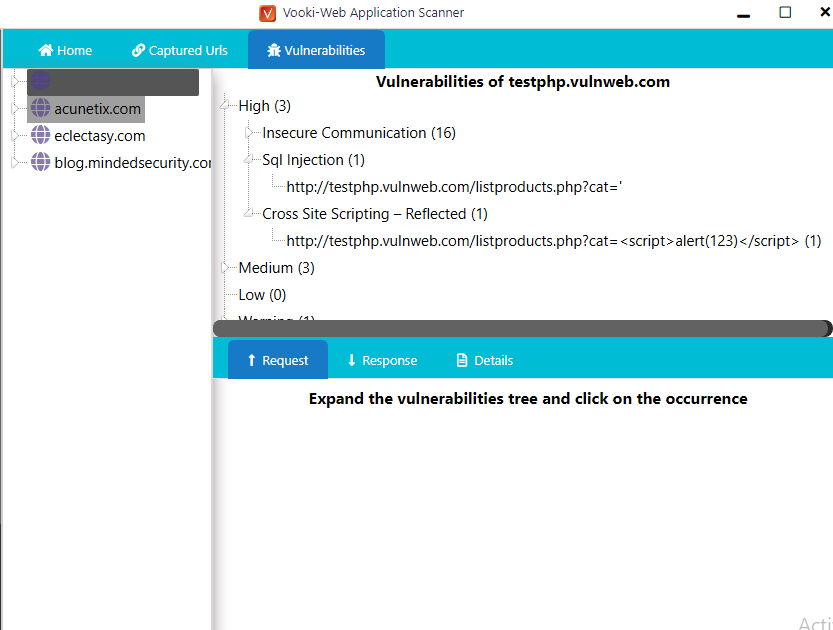
Great 🙂 !! It looks impressive as you can see that it automatically finds all the vulnerabilities available in the web application as well as it classifies them based on the impact.
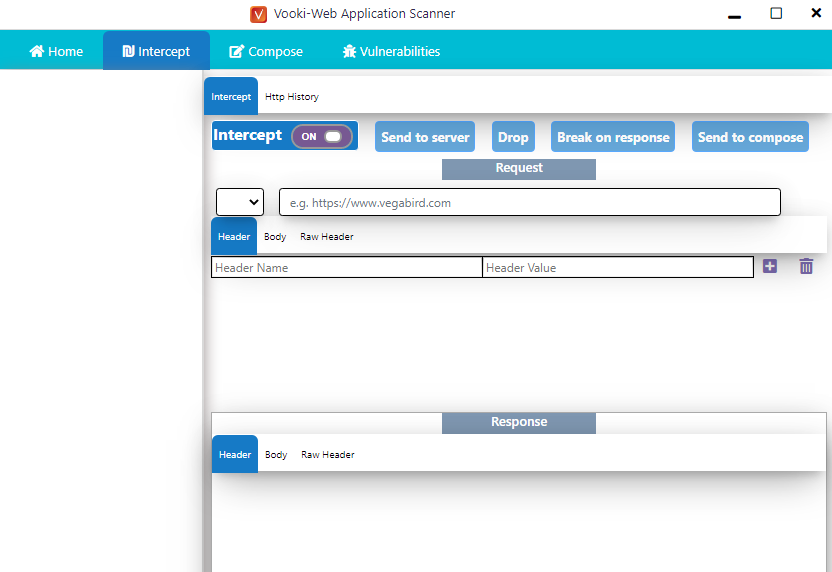
You can also intercept the request and response which is the same feature that we find in the burpsuite tool. Amazing :p !!
Also we can crawl any web application to get some sensitive files or locations.
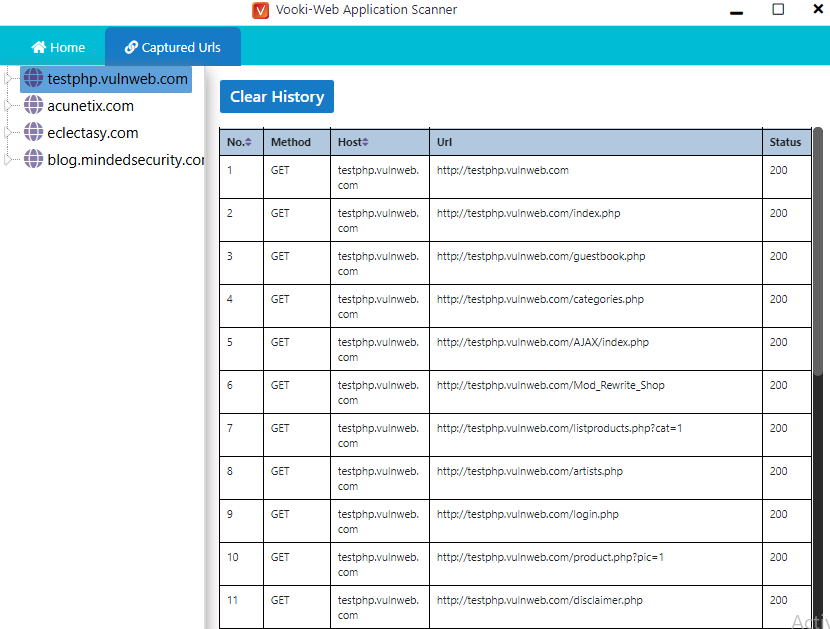
Domain and Host Scanner
Through this feature we can get different information about the target such as whois information, open port, DNS etc. for which we need to enter the domain name or host address.

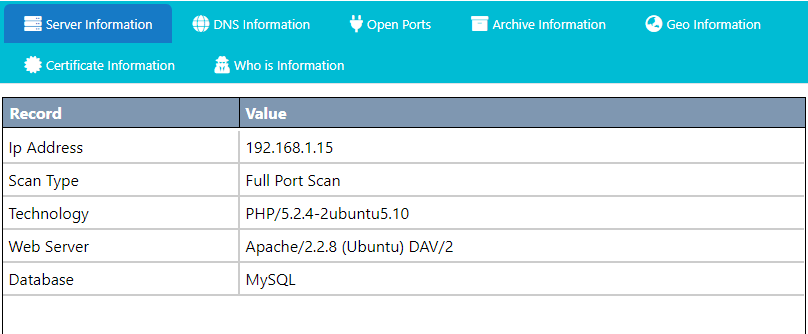
You can see almost all the necessary details about the target web server.
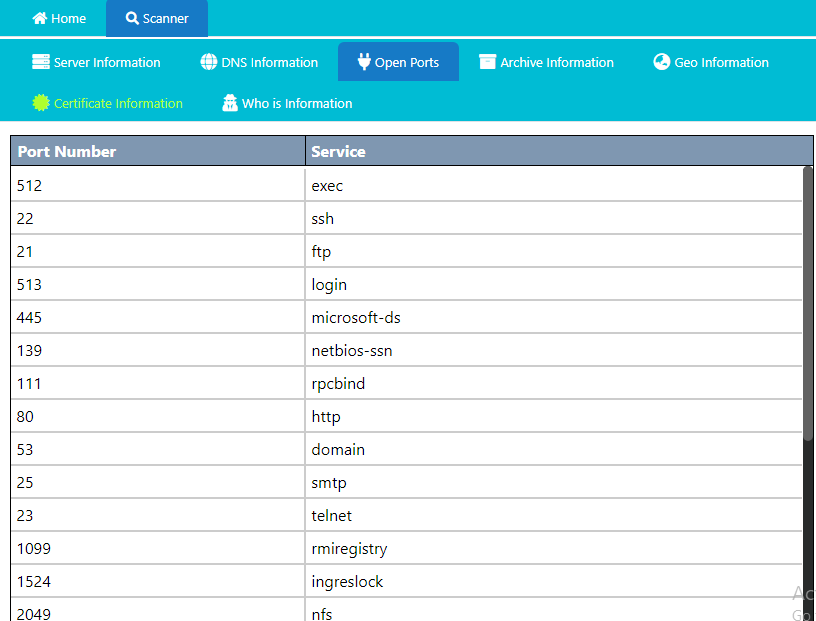
Also we can see all the services running on the target web server but not in depth.
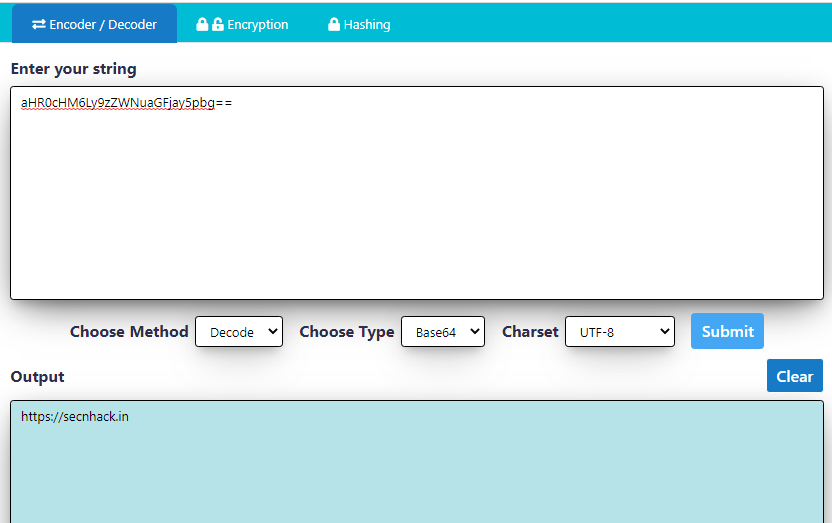
This tool has another interesting encoding / decoding feature through which we can easily decode our hashes and encode plain text during penetration testing.
That’s all in this tutorial and we hope that now after reading this article from top to bottom you can control this tool very easily.




