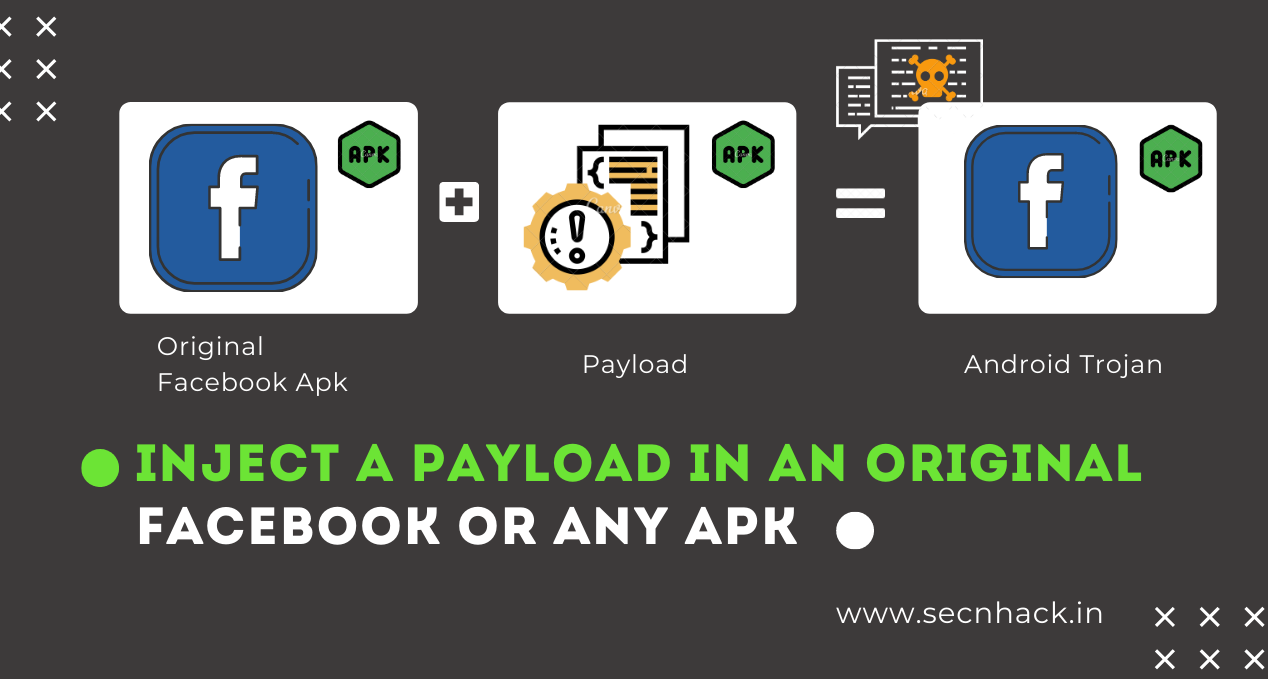
Multiple Ways to Embed a Payload in an Original APK File
Hey Folks, as we know beginners try to find the best ways that they can embed the payload into the original APK, But it takes their long time to do research on it. So in this article we will give you all the working methods, with the help of which […]
Continue Reading