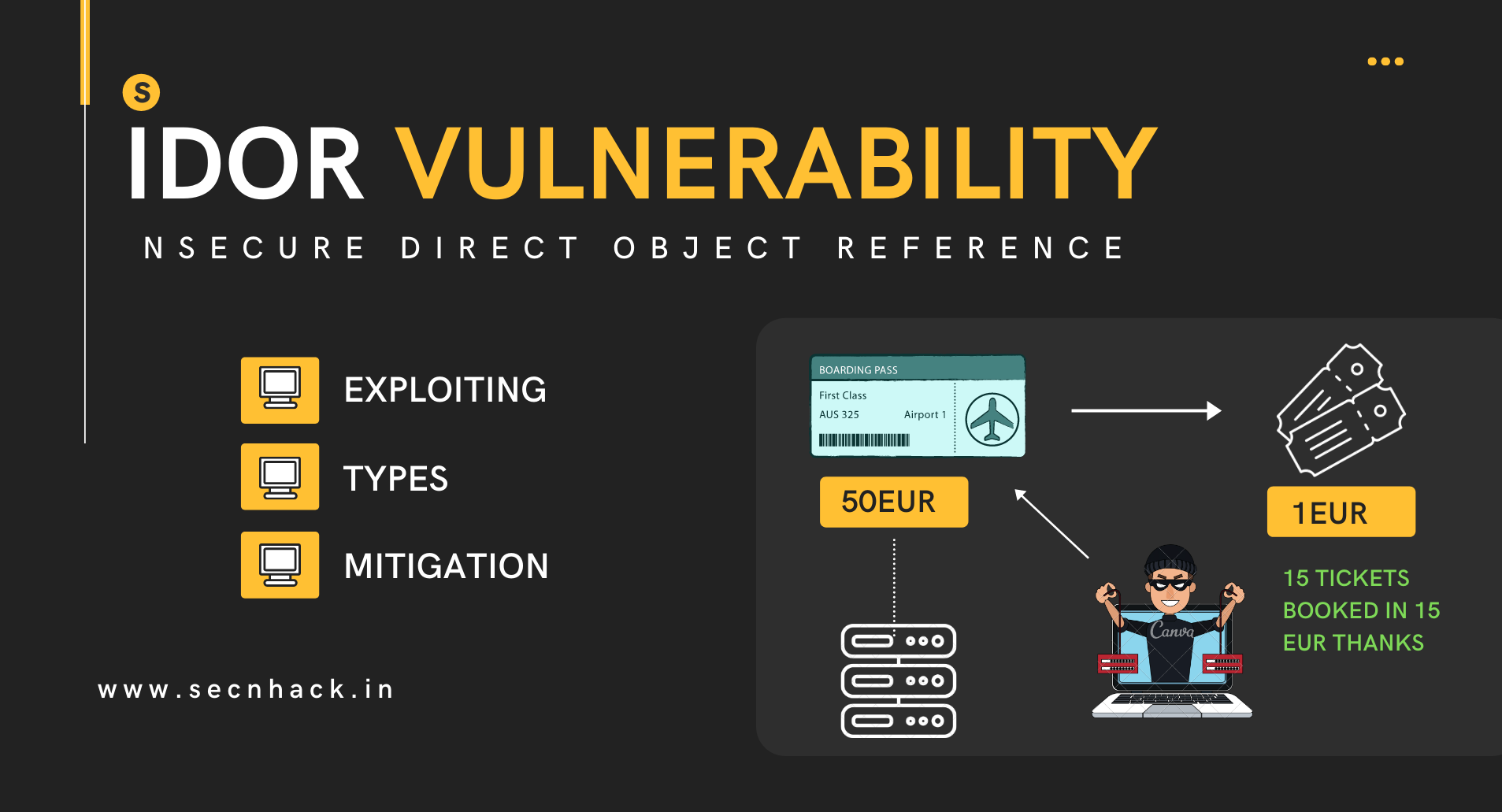
IDOR Vulnerability – Exploit, Types and Mitigation
Hey guys, in this tutorial, we are going to move towards the next vulnerability of OWASP TOP 10 which is IDOR “Insecure direct object references“vulnerability. Insecure direct object references are a type of access control vulnerability that occurs when an application uses user supplied input to access object (server), such […]
Continue Reading