
Hey Folks, in this tutorial we are going to talk about an web application security scanner tool called “WAScan“. WAScan ((W)eb (A)pplication (Scan)ner) is a Open Source web application security scanner. It is designed to find various vulnerabilities using “black-box” method, that means it won’t study the source code of web applications but will work like a fuzzer, scanning the pages of the deployed web application, extracting links and forms and attacking the scripts, sending payloads and looking for error messages,..etc. WAScan is built on python2.7 and it can run on any platform which has a Python environment.
Credit : github.com
Let’s take a look 🙂 !!
Installation
To successfully configure this tool we have to follow the given steps consecutively. After executing the git command the tool will be automatically downloaded to our system after which we can go to the directory and boot this tool using python command.
|
1 2 3 |
git clone https://github.com/m4ll0k/WAScan.git cd WAScan python wascan.py |
Features
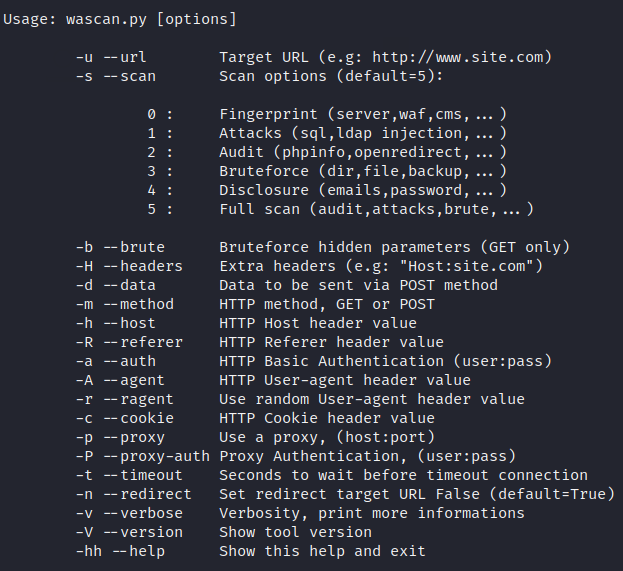
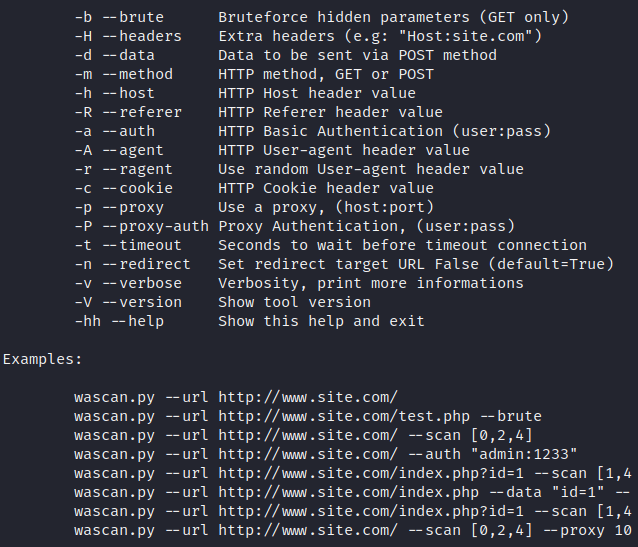
You can see all the available features in this tool by executing the following command. But you don’t have to be so nervous to use this tool as it gives us all examples to use the features of this tool.
|
1 |
python wascan.py |
Basic Scan – Fingerprint
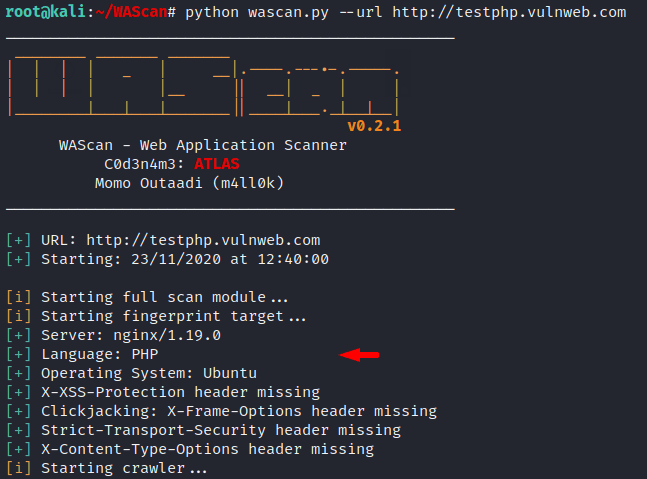
Just after giving the “–url” argument to the command, we have to enter our target details. As you can see in the image above there are six levels of scans in this tool where by default it runs at level 0. We get the same result after executing the command which is mentioned in the tool such as header, server version, waf, technology etc.
|
1 |
python wascan.py --url http://testphp.vulnweb.com |
Disclosure – Email and Passwords
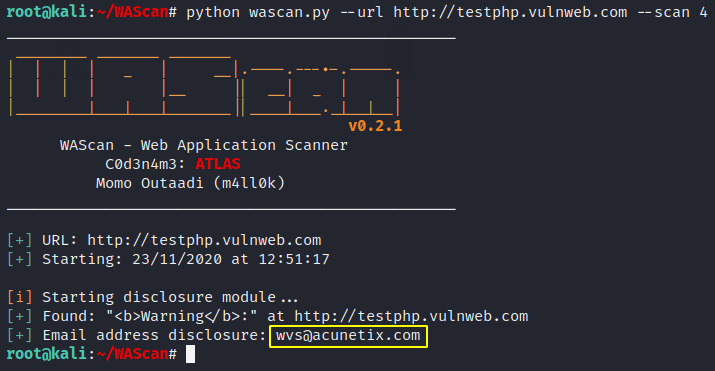
By using the disclosure option we can get sensitive data available on target web application.
|
1 |
python wascan.py --url http://testphp.vulnweb.com --scan 4 |
Full Scan
Through the following command we can do all the things at the same time like brute forcing, crawling, weakness, audit, attack etc. So we will add “–scan 5” to our command to activate full scan mode.
|
1 |
python wascan.py --url http://testphp.vulnweb.com/listproducts.php?cat=1 --scan 5 |
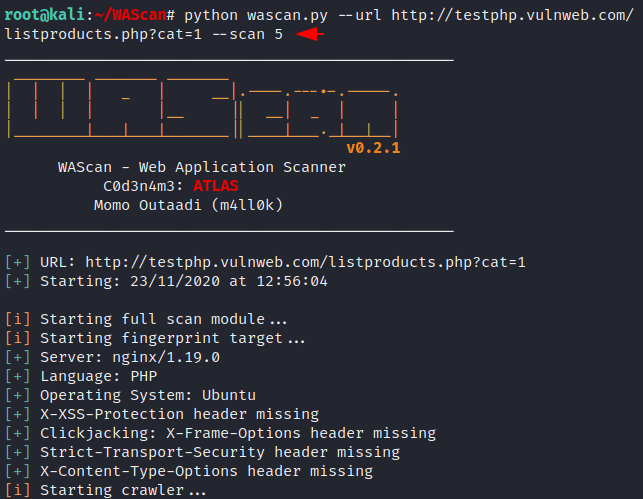
Great 🙂 !! It will first crawl the entire web application and try to find vulnerabilities in the web application by adding several combinations of payloads. As you can see how important vulnerabilities have been found in web applications.
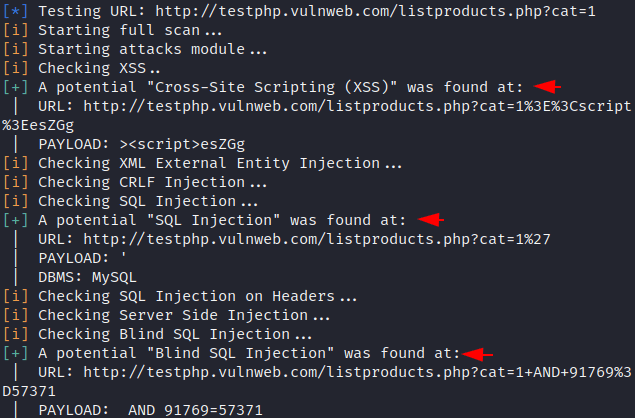
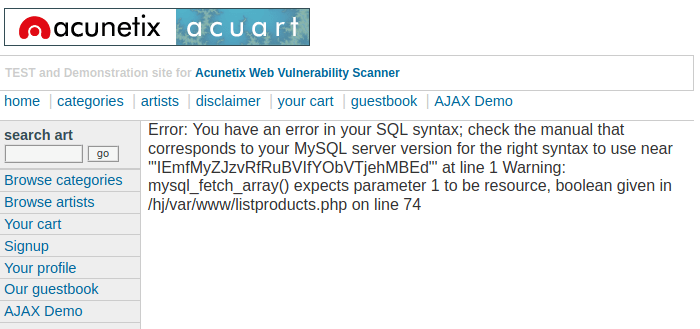
Hmm 🙂 !! You can see as proof that web application is vulnerable to the SQL injection vulnerability.
As you can see how many vulnerabilities it tries to detect in a web application.
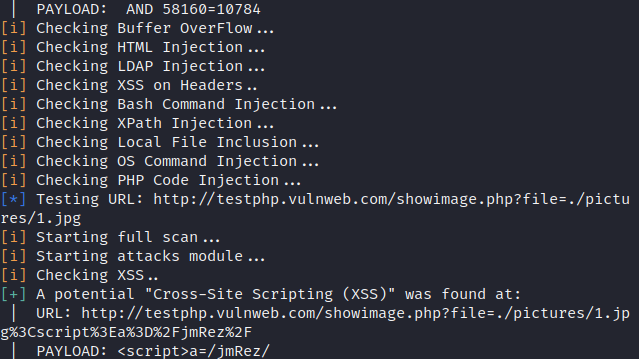
Done 🙂 !! Similarly, you can use the all these features available in this tools one by one and obtains some hidden files or vulnerabilities in the web application.

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.




