
Hey folks, in this article we will going to talk about “ Top 20 Recon, Passive Enumeration and Information Gathering Tool “ for bug bounty hunters. We have selected these tools after extensive research. Basically this article based on “Information Gathering” which is the part of bug bounty.
What is Information Gathering ?
Information Gathering is a phase in which we attempt to gather information against the target, victim or system. The information can be open ports, government docs, services running, applications like unauthenticated administrative consoles or those with default passwords. Suppose we are working on web application assessment, we need to explore all the possibilities of breaking into the web application, because the more information we can gather about the target, the greater chance we can penetrate it. There are two types of Information Gathering.
- Active Techniques
- Passive Techniques
Table of Content 🐛
Active Techniques
- Fierce
- Dig
- Skipfish
- DIRB
- Gobuster
- Final Recon
- Subfinder
- Crunch
- WhatWeb
- Domained
Passive Techniques 🐛
- Zomeeye
- Shodan
- Wolfram Alpha
- Reverse IP Lookup using YouGetSignal
- Pentest-Tools
- Google Advance Search
Lets get started 🙂 !!
Active Techniques
1. Fierce
Fierce is a scanner that helps locate non-contiguous IP space and host name against specified domains. This tool is hosted on github page that is designed especially for locate the target inside and outside a corporate network. We will install this tool on our kali linux operating system using the following command.
|
1 2 3 |
git clone https://github.com/mschwager/fierce.git cd fierce python -m pip install -r requirements.txt |
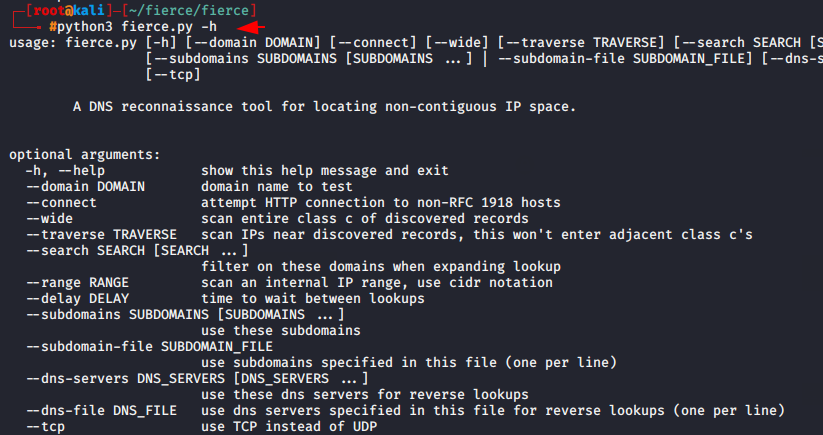
Now we can start this tool just executing the command from given below.
|
1 |
python3 fierce/fierce.py -h |
It uses DNS primarily so we will take a example of our website.
|
1 |
python3 fierce.py --domain secnhack.in |
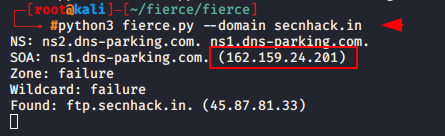
As you can see above it has provide the name server and IP address of our website.
2 . Dig
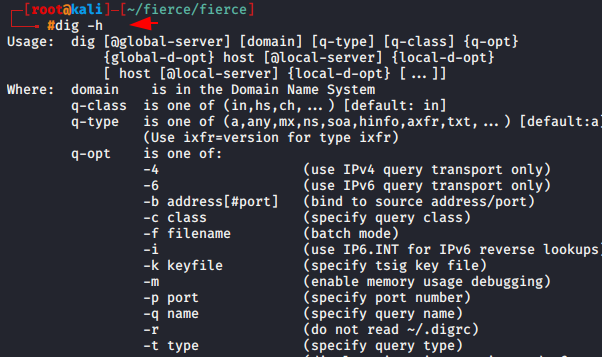
Dig is a pre-installed tool in kali linux operating system that can be operate through command line option. It is useful for querying the Domain Name System. Dig can be used in order to network troubleshooting and for educational purposes. We can start this tool using the following command.
|
1 |
dig -h |
We will perform full DNS enumeration using the default command.
|
1 |
dig secnhack.in |
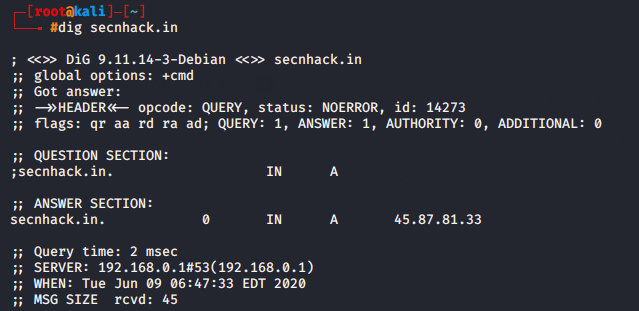
Now we try to get only name servers from the target website.
Usage 🙂 dig < target domain >
|
1 |
dig secnhack.in ns |
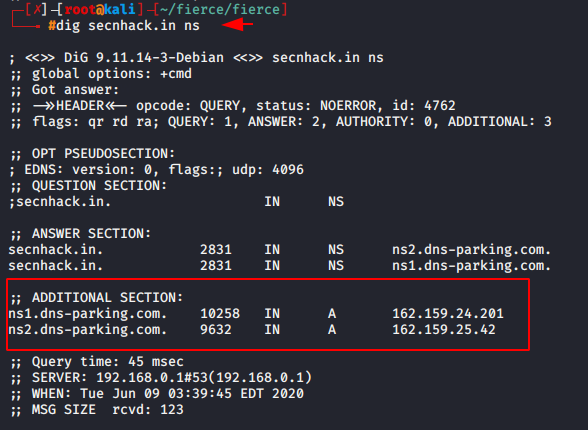
Similarly we can add multiple filters :
- +comments: Show comment lines.
- +authority: Show the authority section.
- +additional: Show the additional section.
- +stats: Show the stats section.
- +answer: Show the answer section.
- +all: Show everything.
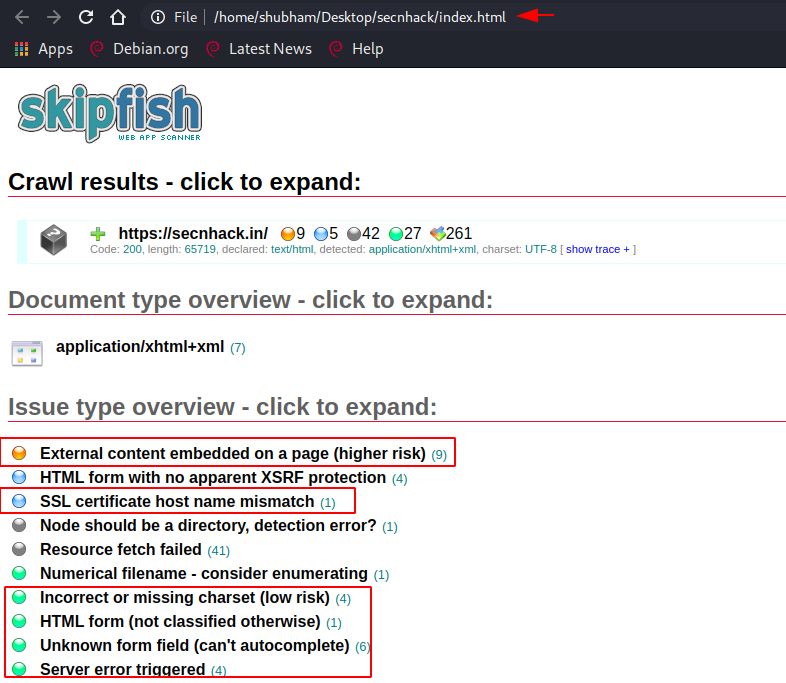
3. Skipfish
Skipfish is a pre-installed reconnaissance tool for active web application security . It is uses the sitemap of the target site for detecting the risk and uses crawling method to fetch invalid URL as it can affect website. As you know that skipfish is the pre-installed tool hence we can start this tool by following command.
|
1 |
skipfish -h |
Now we will take a example of our website and try to find the vulnerability and redundant links.
Usage 🙂 skipfish -o < name of result file > < website >
|
1 |
skipfish -o secnhack https://secnhack.in |
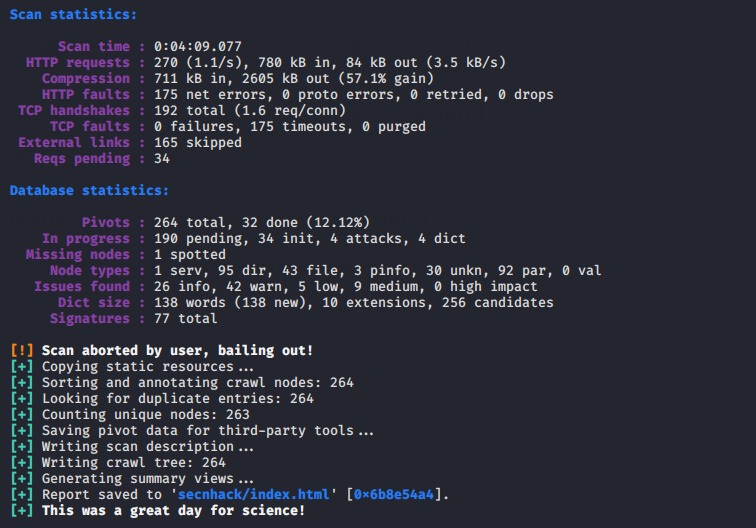
After the scanning is complete it gives all the details that we can easily see through the GUI interface.
4. DIRB
DIRB is a web content or index scanner. DIRB is a web content or index scanner. It is usually used in most CTF challenges because it allows us to find hidden directories on the web server by using the brute force technique. Keep in mind it is a content scanner not a vulnerability scanner also dirb sometimes can be used as a classic CGI scanner. We can start this tool using the following command.
|
1 |
dirb |
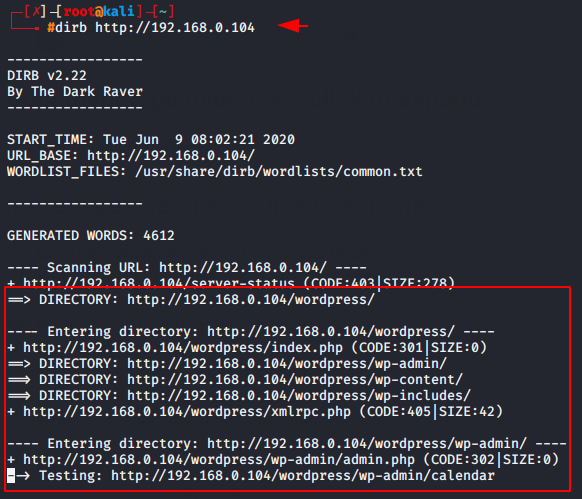
Now we will try to obtain the hidden directory on the web server.
Usage 🙂 dirb < target ip or url >
|
1 |
dirb http://192.168.0.104 |
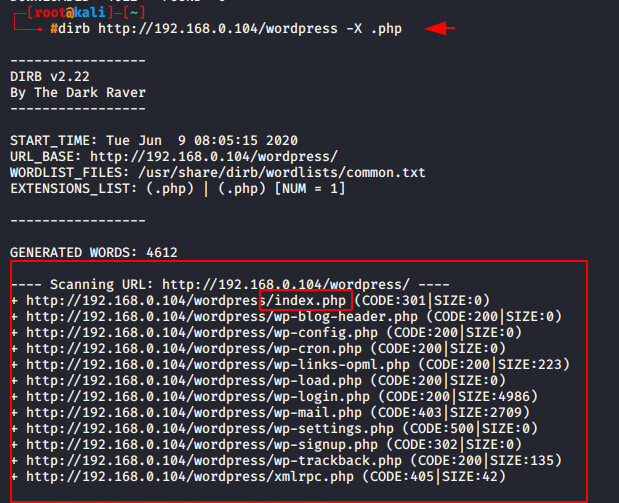
If we want to find only those files whose extension is .php then we will add the following filter to our command.
Usage 🙂 dirb < target ip or url > -X < extension want to fetch >
|
1 |
dirb http://192.168.0.104/wordpress -X .php |
Add the output filter which will create the file of result.
Usage 🙂 dirb < target ip or url > -X < extension want to fetch > -o < file name >
|
1 |
dirb http://192.168.0.104/wordpress -X .php -o res.txt |
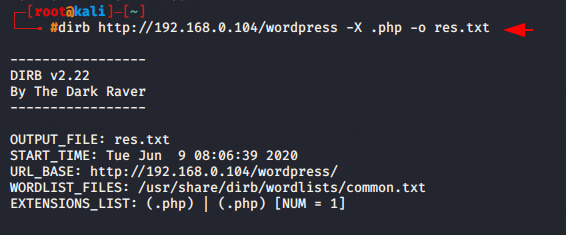
Similarly we can get the data of the website by adding many filters.
5. Gobuster
Gobuster Alternative directory and file busting tool which is written in Go programming language. We can easily install this tool using the following command.
|
1 |
apt-get install gobuster |
To check the all features we will use the help command.
|
1 |
gobuster -h |
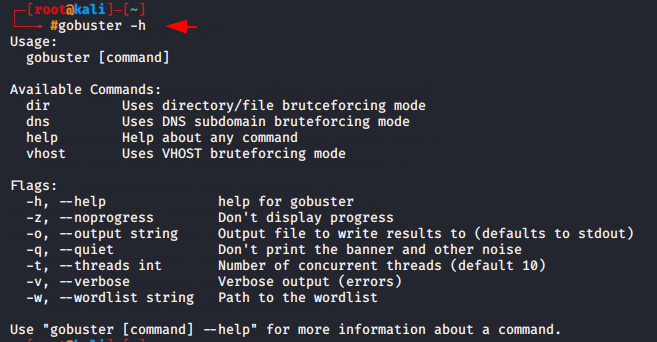
- gobuster dir -h
- gobuster dns -h
- gobuster vhost -h
Lets take a example of wordpress website that is hosted on our localhost and try to obtain the hidden directory.
Usage 🙂 gobuster dir -u < url > -w < wordlist >
|
1 |
gobuster dir -u http://192.168.0.104/wordpress -w /usr/share/wordlists/dirb/big.txt |
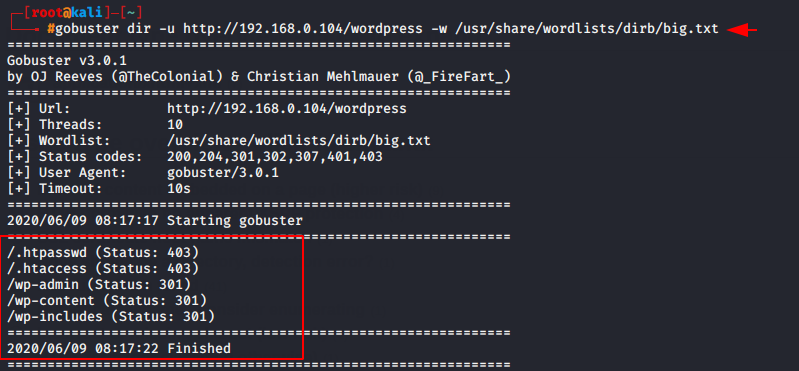
Similarly we can add given filters to find out the better results.
- -n = ” No Status Mode “
- -e = ” Significant Result “
- -v = ” Verbose Mode “
- -q = “Disable Banner “
6. FinalRecon
FinalRecon tool are hosted on Github page and made in python language. FinalRecon tool used to web reconnaissance such as scanning, enumeration and footprinting.
Read out the features of this tool by given below.
- Headers – check server, content-tye, xff and encoding.
- SSLinfo – check security of site.
- WHOIS – lookup information about the domain
- Crawl – fetching the web pages or link from website.
- Dns – check Dns A, AAA and more records.
- Sub – find the sub domain
- Trace – can be used in order for debugging purposes
- Dir – grab the hidden directory.
- Port Scan (PS) – find the open ports.
- Full Scan – contains all above scan
Now we will download this tool from github page using the following command.
|
1 2 3 |
git clone https://github.com/thewhiteh4t/FinalRecon.git cd FinalRecon pip3 install -r requirements.txt |
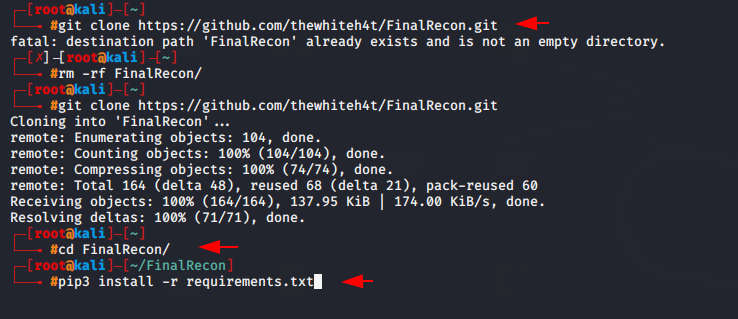
Lets start this tool using the following command.
|
1 |
python3 finalrecon.py |
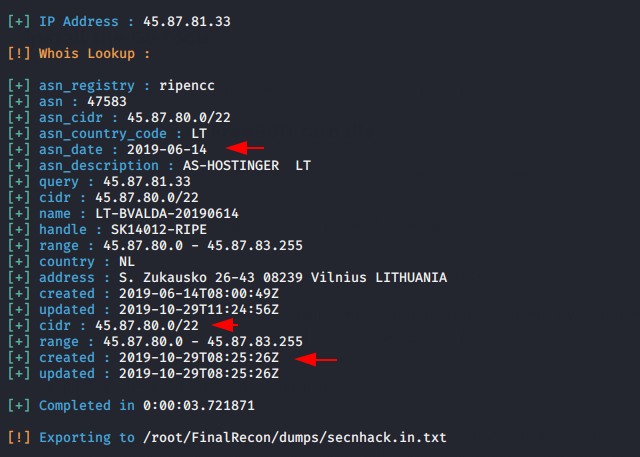
As you know that whenever person or organization register a new domian then the registration information becomes available for everyone. Hence whois is used to grab the information about the website.
|
1 |
python3 finalrecon.py --whois https://secnhack.in |
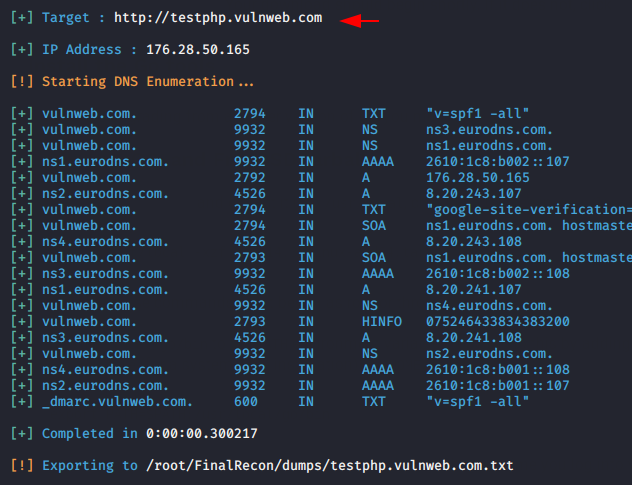
DNS Footprinting is the process to collecting information about DNS zone data, DNS records and much more.
|
1 |
python3 finalrecon.py --dns http://testphp.vulnweb.com/ |
Similarly we can use this tool for multiple features.
- python3 finalrecon.py –headers http://testphp.vulnweb.com
- python3 finalrecon.py –sslinfo https://secnhack.in
- python3 finalrecon.py –crawl https://secnhack.in
- python3 finalrecon.py –trace http://testphp.vulnweb.com
You can checkout the complete article from it here.
7. Subfinder
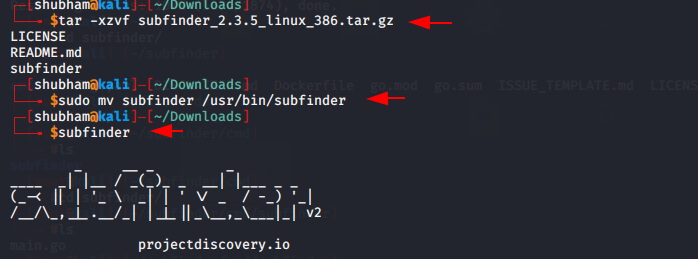
From the github : Subfinder is a subdomain discovery tool that discovers valid subdomains for websites. Designed as a passive framework to be useful for bug bounties and safe for penetration testing. First we will download this tool from here.
Now unzip the file and execute the following command.
|
1 2 3 |
tar -xzvf subfinder-linux-amd64.tar.gz mv subfinder /usr/bin/subfinder subfinder |
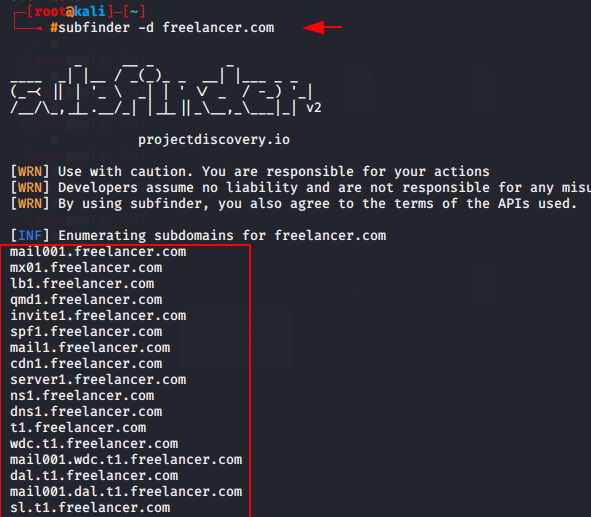
Here we will obtain the subdomain using the following command.
|
1 |
subfinder -d freelancer.com |
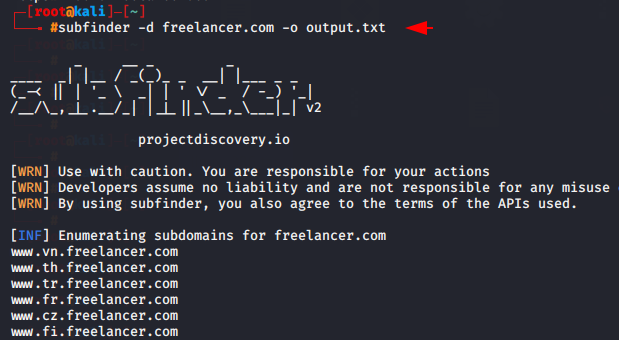
This tool also provide the output feature which we can use using the following command.
|
1 |
subfinder -d freelancer.com -o output.txt |
Similarly we can use the more filters.
Filters :
- -oJ -nW = JSON format
- -v = verbose
8. Crunch
Crunch is a pre-installed tool in kali linux that is used for generate a powerful wordlist. where you can specify a standard character set or a character set you specify. Crunch can generate all possible combinations and permutations.
|
1 |
crunch |
Now we will create a directory that contains six minimum words, eight maximum words and the specific string is “shubham“.
Usage 🙂 crunch output < location >
|
1 |
crunch 6 8 shubham –o /root/secnhack.txt |
Here you can see that the file has successfully created.
|
1 |
cat secnhack.txt |
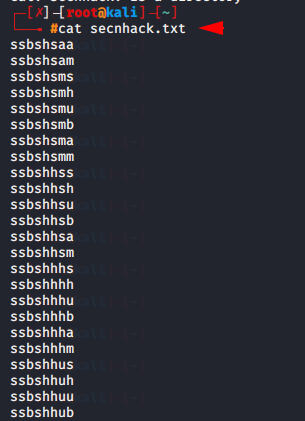
After that we can create the wordlist as our need using the help command.
9. Whatweb
The WhatWeb tool is used to identify different web technologies used by the website. It is pre-installed tool in kali linux hence we can start this tool using the following command.
|
1 |
whatweb -h |
Now simply execute the command for check the web technology ⚙.
|
1 |
whatweb secnhack.in |
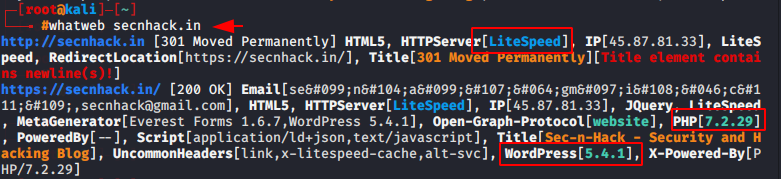
We can use the following filters.
- AGGRESSION = –aggression, -a=LEVEL
- HTTP OPTIONS = –user-agent
- AUTHENTICATION = –user
- PROXY = –proxy-user
- PLUGINS = –list-plugins
- OUTPUT = –verbose
10. Domained
From the Github : Domained uses several subdomain enumeration tools and wordlists to create a unique list of subdomains that are passed to EyeWitness for reporting with categorized screenshots, server response headers and signature based default credential checking. It contains the multiple tool such as :
- Massdns
- Subbrute
- Sublist3r
- Amass
- Enumall
- SubFinder
- Knockpy
- Virus Total
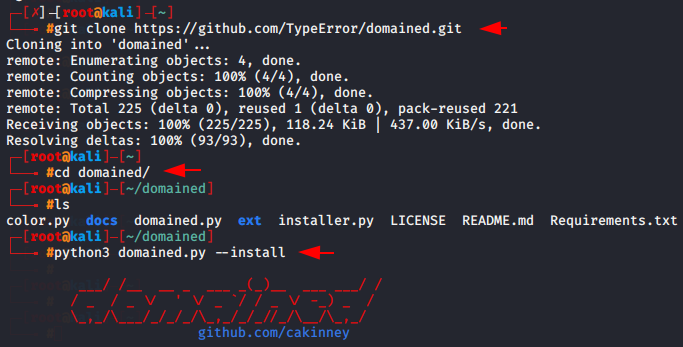
For configure this tool in kali linux we have to execute the following command.
|
1 2 3 |
git clone https://github.com/TypeError/domained.git cd domained/ python3 domained.py --install |
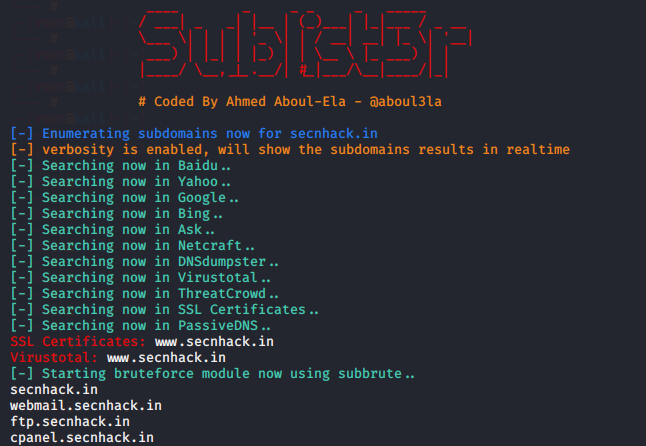
Lets take one example of this tool so that you get an idea
|
1 |
python3 domained.py -d secnhack.in |
Fillters 🙂
- –vpn = Check if you are on VPN (update with your provider)
- –quick = Use ONLY Amass and SubFinder
- –bruteall = Bruteforce with JHaddix All.txt List instead of SecList
- –fresh = Delete old data from output folder
- –notify = Send Pushover or Gmail Notifications
- –active = EyeWitness Active Scan
Passive Techniques
11. ZoomEye
ZoomEye is a cyberspace search engine tool used to grab the data of devices, websites, services and components etc. With the help of this tool user can easliy find the target details such as IP, open services etc. We can find the details 🥫 from it here.
We can obtain the details by type the targeted URL on zoomeye.
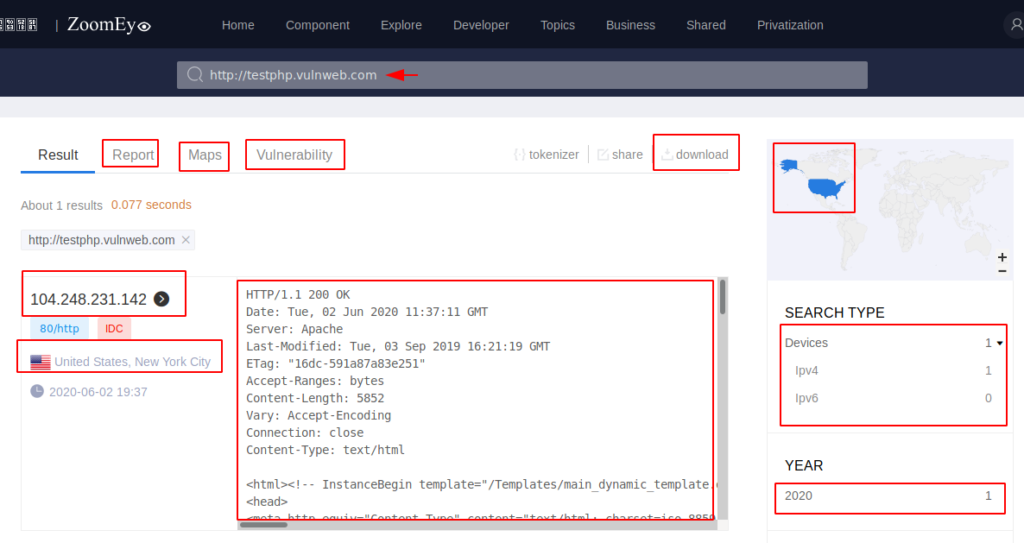
After the results it provide the vulnerability of that website that can be downloaded.
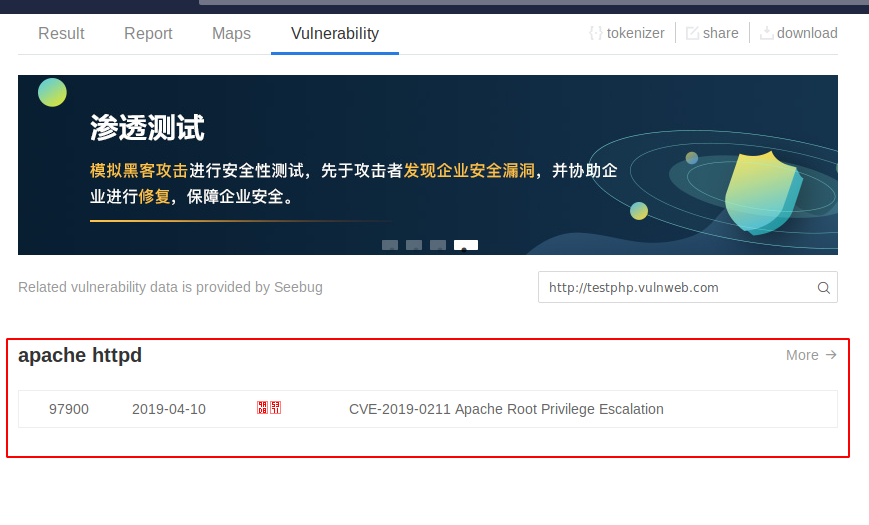
12. Shodan
Shodan is a search engine which lets the user to find various types of computers connected to the internet using a variety of filters. Shodan provide completely legal service that collects data that was already available to the public. The metadata for various IOT devices is already broadcast online, and Shodan simply reports what it finds.
First we have to find the IP address of that website.
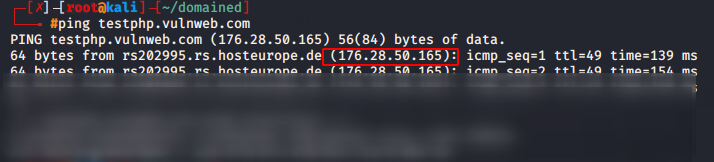
Now we can collect the data of this website that is available to the public.
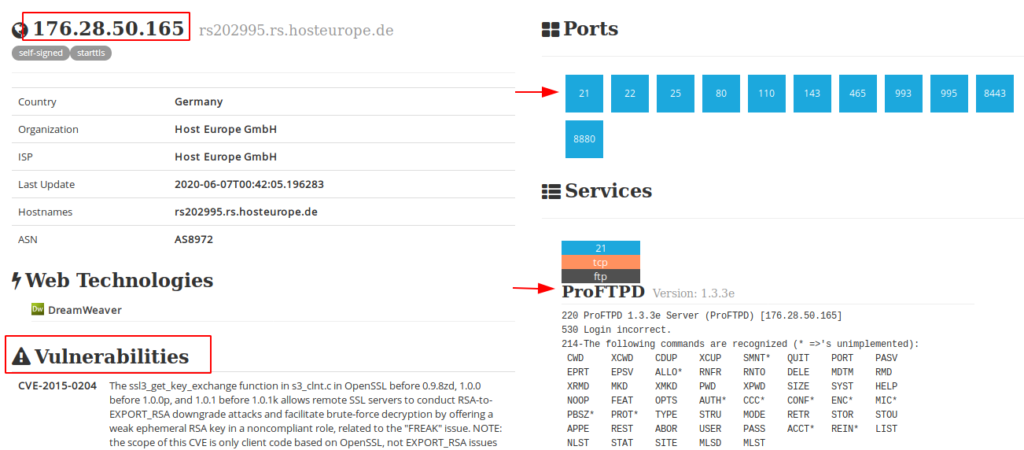
Lets try to find the Apache Server.
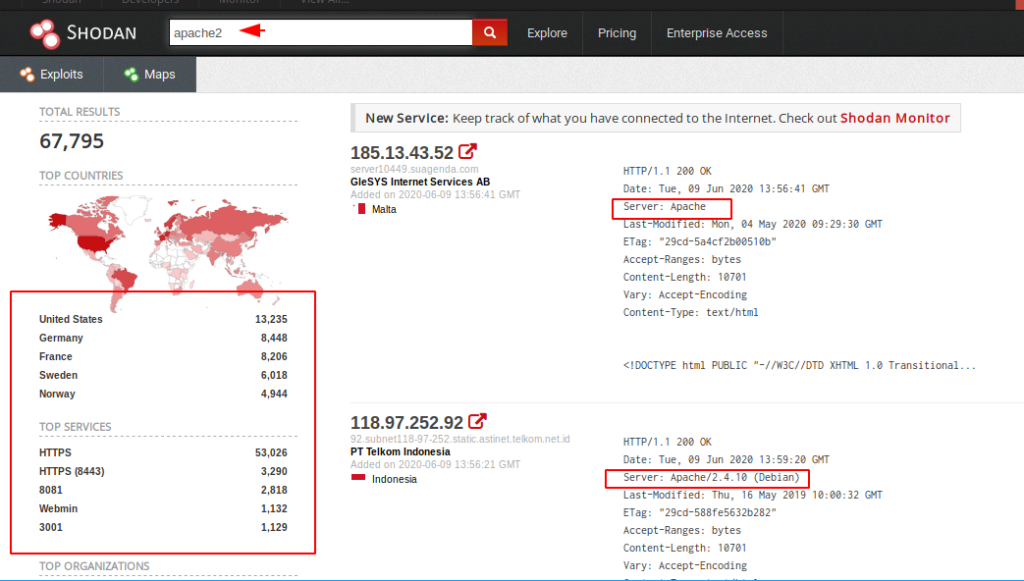
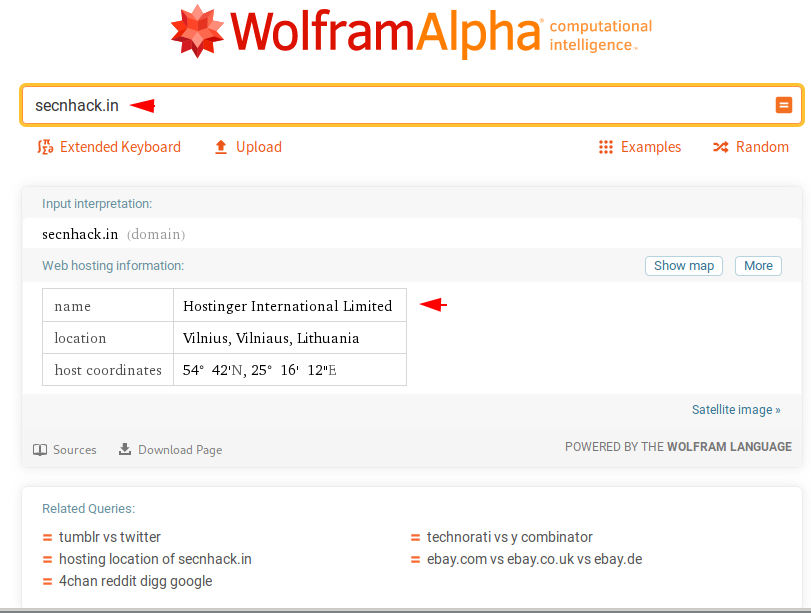
13. Wolfram Alpha
Wolfram Alpha is the another Advance Search Engine tool but it is a unique engine for computing answers and providing knowledge. According the Google : It works by using its vast store of expert-level knowledge and algorithms to automatically answer questions.
Here you can see that what kind of results come on searching
14. YouGetSignal
YouGetSignal is the collection of network tools that is helpful for domain enumeration. In this website we can find lot of features such as :
- Reverse IP Domain Check
- Remote Address
- Domain or IP address
Here you can visit this website and checkout the features.
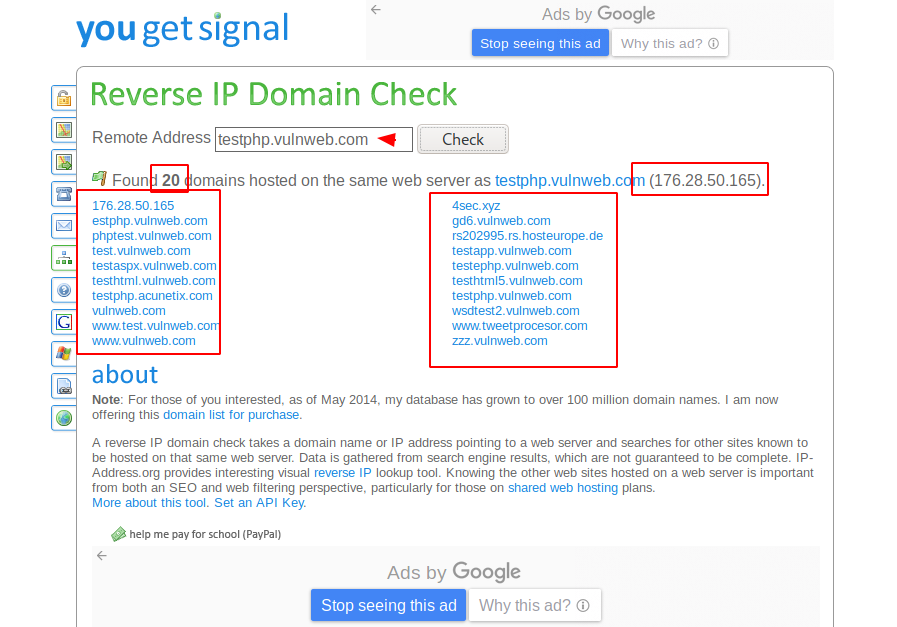
After entering the URL it gives the much details about the website as possible.
15. Pentest-Tools
From Google : Pentest-Tools.com allows you to quickly discover and report vulnerabilities in websites and network infrastructures.
As you can see that it provides the CVE details, Vulnerability and High Risk Issues of the website.
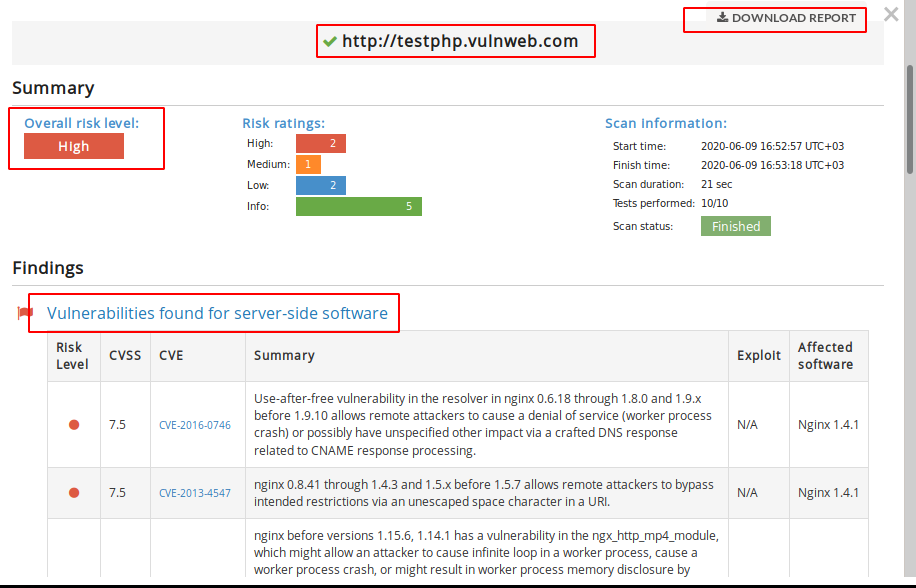
Here we can see that the web technology’s servers and software details.
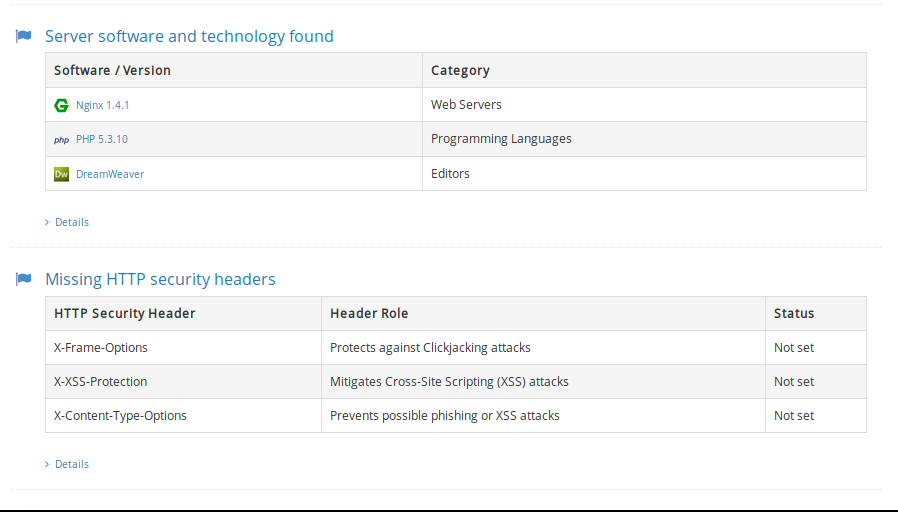
There are some paid tools that we highly recommend for vulnerabilities scanning.

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.




