Hey Folks, in this tutorial we are going to talk about an open source “Open Redirection” vulnerability finder tool called “OpenRedireX“. Simply tool takes the URL from the user and then it constantly tries to find open redirect issues using its own wordlist that called as “FUZZING“. If you want to get deeper information about this vulnerability then you can go here.
Key Features
- You can specify your own payloads in ‘payloads.txt’
- Shows Location header history (if any)
- Fast (as it is Asynchronous)
- Takes a url or list of urls and fuzzes them for Open redirect issues
Installation
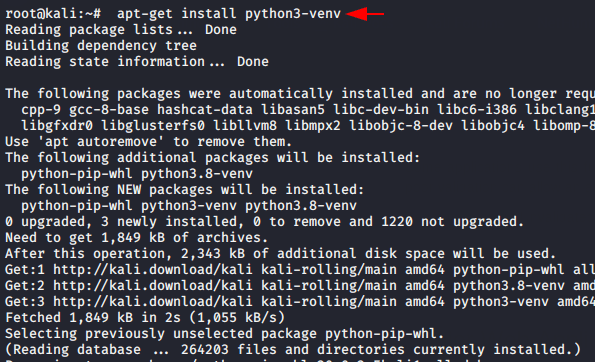
The tool is available on github as it is an open source tool. The installation is quite simple but as we know that dependence is the most important factor during the installation of any type of tool. So we will download the dependency before starting the tool.
|
1 |
apt-get install python3-venv |
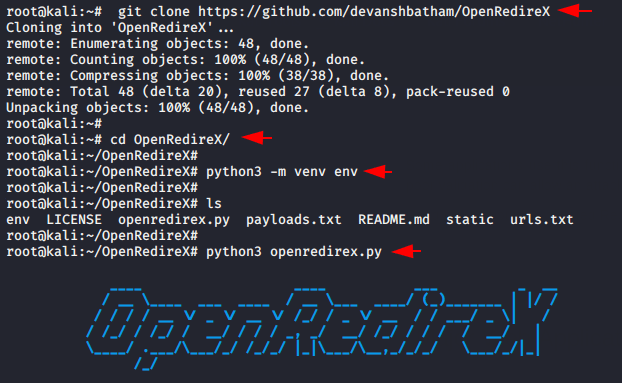
Now we will configure this tool in our terminal but first we have to download it from the github and then go the directory. It’s not enough as we have to execute one more python command at the end.
|
1 2 3 4 |
git clone https://github.com/devanshbatham/OpenRedireX cd OpenRedireX python3 -m venv env python3 openredirex.py |
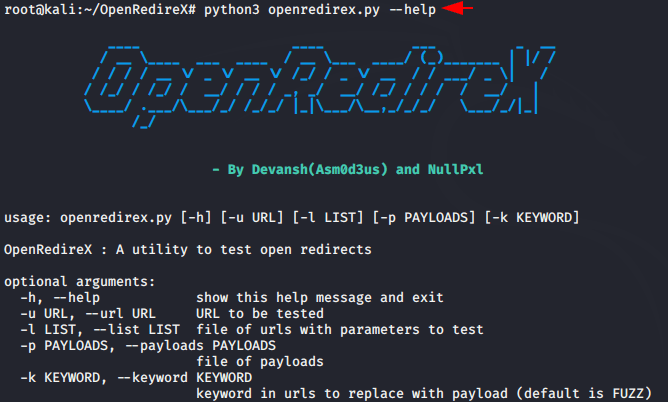
The installation has been completed and now we will show you the features of this tool through given image. Use the given command to launch this tool.
|
1 |
python3 openredirex.py --help |
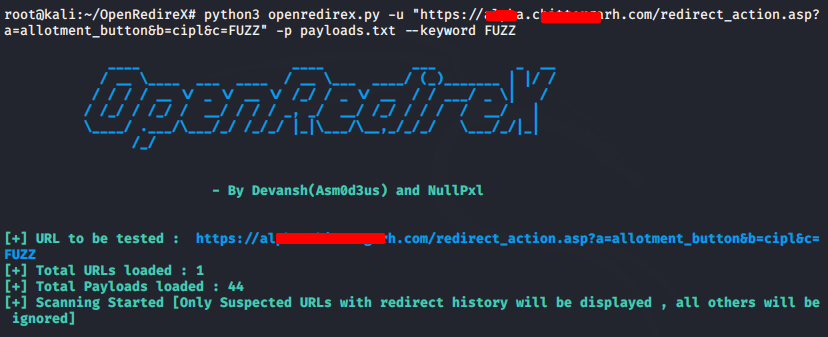
live Website
Here you can see that we got open redirection vulnerability in live website through this tool, but due to security policy we can show you everything.
Demo
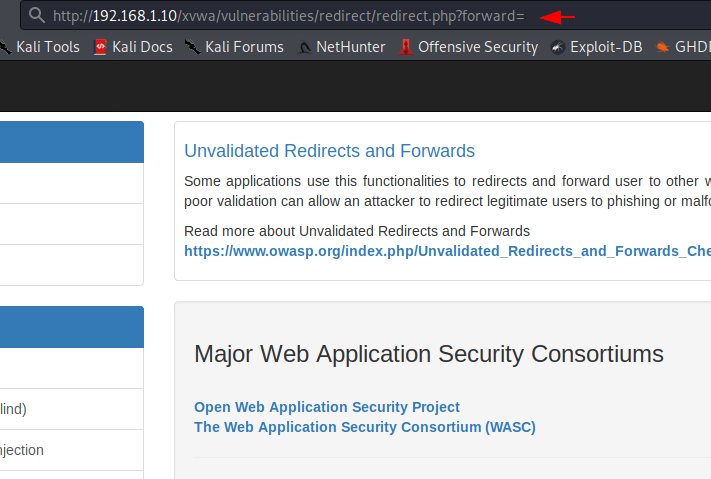
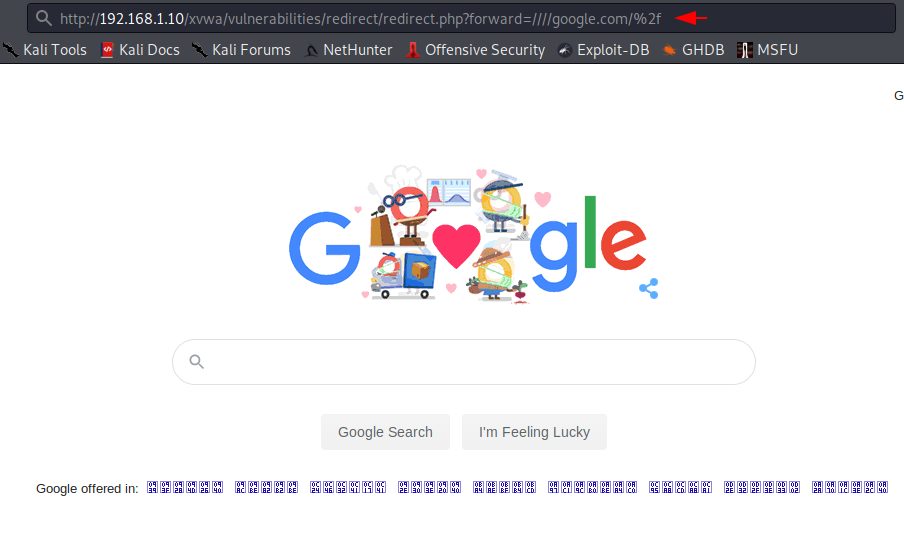
Here you can see that we are using XVWA vulnerabale application for demonstration. If you want to do same lab setup in your localhost machine then you can go here.
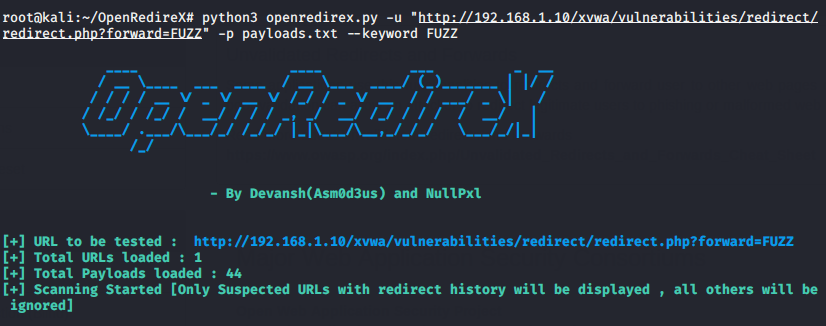
Just look at the command that we mentioned below and only manipulate the URL parameter according to yourself. You can also see that the command below mentions the FUZZ keyword which is instructing the vulnerable parameter.
Usage 🙂 python3 openredirex.py -u < URL > -p < payload file > –keyword FUZZ
|
1 |
python3 openredirex.py -u "http://192.168.1.10/xvwa/vulnerabilities/redirect/redirect.php?forward=FUZZ" -p payloads.txt --keyword FUZZ |
As you can clearly see it gives us many combinations of results from which we can exploit this vulnerability.
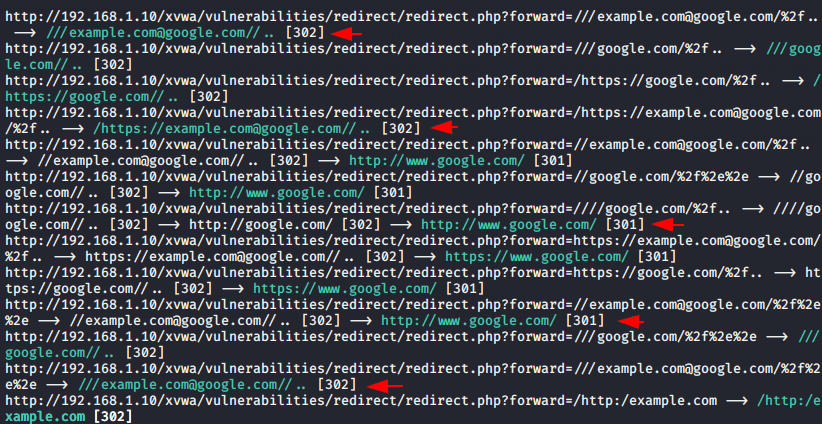
Don 🙂 !! We get success when we take a URL from the results and execute it on the browser and as you can see we have successfully redirected to “google.com“.

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.




